Abstract
A robust watermarking scheme using an optimization-based image reconstruction technique is presented in this paper. In the proposed scheme, the cover image (CI) and watermark image (WI) are decomposed using Hessenberg decomposition (HD) and singular value decomposition (SVD) with discrete wavelet transformation (DWT). Following the use of SVD, each singular value of the watermark is immediately incorporated into the singular component of the CI using the best scaling factor. Considering the scenario of different attacks on the WI, the optimization-based robust image reconstruction technique is developed and applied to the attacked WI to reproduce its attack-free good quality version. The proposed technique splits the low-quality attacked WI into several small patches processed in raster scan order. Moreover, it also employs some database images of the same domain for computing the reconstruction coefficients and producing the high-quality counterpart of the extracted attacked watermark. Simulation results calculated in terms of different performance metrics, namely Normalized Cross-Correlation (NC), Bit Error Rate (BER), Normalized Absolute Error (NAE), Peak Signal to Noise Ratio (PSNR), and Structure Similarity Index (SSIM) suggest that the proposed watermarking scheme is more robust to different attacks as compared to several existing competent techniques.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Multimedia has evolved into the information storage technology of the modern world. Image has features such as intuitive images and rich content as a significant way of transmitting a piece of information. Due to the growing importance of scientific visualization and the requirement for adequate information receiving and transferring, image processing techniques have garnered a lot of attention and scope [12, 29]. However, security issues are becoming more prominent due to the image’s widespread use and distribution, which has raised serious concerns about copyright infringement, manipulation, data authentication, and integrity [22]. Digital watermarking [5, 26, 27, 37] is a well-known technique for protecting intellectual property rights and authenticating the validity of data by concealing secret information in digital products. To safeguard ownership and integrity, copyright violations can be avoided by obscuring information in the image via digital image watermarking. Digital watermarking consists of two processes: embedding and extraction, which are mutually exclusive but connected. Watermarking is differentiated into two categories based on the embedding domain: spatial domain and transform domain. As the spatial domain methods are straightforward, they are more vulnerable to attacks. Transform domain methods, on the other hand, are more resistant and durable to numerous attacks, but they are slightly more sophisticated [41]. The time-frequency domain aspect of the wavelet transform domain allows it to be utilized as a multi-resolution wavelet analysis approach [24]. The most extensively used transform domain techniques for developing robust watermarking algorithms are the discrete Fourier transform (DFT), DWT, discrete cosine transform (DCT), integer wavelet transform (IWT), and redundant wavelet transform (RWT). Attacks on watermarked images wipe off both the host image and the applied watermark. As a result, the watermark becomes distorted, and the image’s quality suffers. Wavelet transforms frequently used with different decompositions to improve resilience. Because of its geometric feature and strong stability even at minor disturbances, SVD is commonly used with transform domain algorithms [13].
All the above-discussed techniques are fundamental, and they suffer heavily when attacks are complicated. Therefore, to enhance the robustness of existing watermarking methods against various attacks, especially noise, filtering, and scaling, a new watermarking scheme (WMS) using an optimization-based image reconstruction technique is proposed in this paper. The proposed image reconstruction technique allows our watermarking scheme to efficiently produce the attack-free WI from the extracted attacked WI as compared to other competing methods. Moreover, it makes the WMS more robust to noise, filtering and scaling.
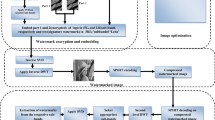
The rest of this paper is arranged as follows: Section 2- literature review; Section 3- the proposed watermarking scheme; Section 4- experimental results; and Section 5- conclusions.
2 Related works
As the focus of this paper is to develop a robust WMS using image reconstruction (IR) techniques, hence in this section, the works related to both WMS and IR are discussed one by one.
2.1 Image watermarking methods
Ebrahimnejad et al. [7] have presented a window-based approach for removing high-density salt-and-pepper noise from brain Magnetic Resonance Imaging (MRI) pictures for optimal Region of Interest (ROI) recognition. In this method, an adaptive n × n window in the neighborhood of each pixel of the noisy input image is considered. This window’s pixels are weighted according to their distance from the target pixel if they are not noisy, and the weighted sum of the nearby pixels is averaged. The result is then used to replace the noisy pixel. Before and after the addition of noise, the ROI obtained is the same. This approach produces an intermediate image with varied noise densities.
Sakthivel et al. [34] proposed a large-scale integration (VLSI) image watermarking system with increased robustness and performance. The use of integer DCT reduces computing complexity, while the development of a four-stage pipeline architecture improves throughput. Integrating the torus automorphism procedure against invertibility threats improves security. Using a mean adaptive threshold value, secret watermark bits are injected into the DCT low-frequency coefficient [15, 16]. The least damage to the host image quality enhances the suggested algorithm’s robustness. The PSNR reported of the suggested method was greater than 50db. The major goal of Zermi et al. [40] is to effectively integrate the watermark into the host medical image with minimum possible distortion so that the information content of the image is normally retained. The host image is transformed using DWT, and transformed using SVD. Authors claim that the method assures integrity, the confidentiality of patient data during transmission, and robustness against a variety of traditional threats.
Using matrix decomposition and the Gyrator transform created in the invariant integer wavelet (IIW) domain, Zhang et al. [42] suggested a watermarking algorithm. The authors proposed the redistributed IIW transform, which is reversible and can convert an image into an invariant domain. A new singular value determination approach is also presented in this study. While compared to SVD, it has lesser time complexity. They further, proposed a new dual encryption system [23]. Hu and Xiang [11] proposed a lossless robust watermarking method using polar harmonic transform. This method is capable of retrieving the original image losslessly if no attacks happen. The WI can be immediately extracted for copyright authentication in the event of an assault.
The majority of extant color image watermarking systems [9] is designed to mark each color channel separately, ignoring color channel correlation and synchronous watermark embedding. In this direction, Chen et al. [4] presented a resilient blind watermarking system for color image copyright protection using quaternion QR-decomposition (QQRD) with an algebraic structure-preserving strategy to reduce computing cost. In the embedding phase, QQRD is used for the entirety of non-overlapping 4 × 4 watermark fragments, after which three strong coefficient pairs are calculated using the NC method and are changed to embed color watermarks within factorized matrices. This eliminates layered processing, which leads to an exaggerated sensitivity to attacks and less correlation, which leads to excessive coefficient value alteration.
Using the Paillier cryptosystem (PC), Liang et al. [17] presented a resilient and reversible WM method for encrypted images. The plain-text image is divided into 8 × 8 non-overlapping blocks, and the PC is used to encrypt [25] each block. To begin, a data hider can use the modular multiplicative inverse (MMI) method to determine the statistical values of encrypted blocks while searching for a mapping table. The shifted histogram is produced from both the encrypted and decrypted images on the receiver side [23]. In addition, the shifted histogram is used to extract the embedded watermark. The encrypted image is restored via inverse histogram shifting procedures. The original image is then restored via a decryption procedure.
To achieve the correct balance between imperceptibility, robustness, and payload, Wang et al. [39] used statistical model-based multiplicative watermarking with local Radial Harmonic Fourier Moments (RHFMs). The CI is spitted into non-overlapping blocks during the embedding process, and the local RHFMs of image blocks are computed before the watermark signal is inserted. Robust local RHFMs magnitudes are initially modeled using the Beta exponential distribution in the extraction phase. The suggested technique is more imperceptible to local geometrical attacks and conventional image processing attacks, and it is more resistant to them. However, there are certain flaws in this method, such as the extraction accuracy not being as good as it should be in strong signal processing.
Based on the Walsh Hadamard Transform (WHT), Prabha and Sam [28] proposed a blind color image WMS. The method splits an image into four 4 × 4 non-overlapping blocks, which are then processed with WHT. This technique embeds the color image watermark in the third and fourth-row WHT coefficients since a little alteration in those rows may not have a significant impact on the image’s visual quality. The difference between the watermarked image’s third and fourth-row WHT coefficients is then calculated. The obtained difference value is used to extract the watermark information. The suggested system surpasses existing watermarking methods in terms of embedding capacity, PSNR, Weighted PSNR, NC, and SSIM. This strategy is more resistant to a variety of manipulations and lossy attacks.
A QR-based digital watermarking approach that can incorporate color images is proposed by Hsu, and Tu [10]. Each bit of the strong watermark is duplicated four times and hidden in several image blocks. The sinusoidal function is used to create the embedding rule, and the wavelength of the sinusoidal function determines the trade-off between imperceptibility and resilience.
Mohammed et al. [21] proposed an approach for an effective embedding technique to create a semi-blind WMS based on the transform domain DWT-SVD. The WI is first transformed using the DWT technique for one pass during the embedding procedure. The SVD technique is then used to alter the LL-band values. For inserting into the CIs, a diagonal matrix with S-values is prepared. DWT, on the other hand, transforms the CIs for two degrees of deconstruction. The watermark bits are embedded into the HL2 and HH2 bands of the CI using the zigzag approach.
In [13], the lifting wavelet transform (LWT) based scheme with the support vector machine (SVM) technique is presented by Islam et al. After applying a 3-level LWT decomposition on the host image, several different sub-bands are selected for the embedding process. The process of training and testing using SVM is used as a detector of the watermark bit during extraction. This scheme provides better robustness against a variety of attacks in addition to noise attacks. Ansari et al. [1] proposed an integer wavelet transform (IWT) based method for protecting copyrighted material using SVD and Ant Bee Colony (ABC) algorithm. ABC algorithm helps to find optimized scaling factors to achieve high robustness, but it does not give good results against deep geometric attacks. On another side, Liu et al. [19] also proposed a similar technique in which HD and SVD-based optimized watermarking method has been proposed in the DWT domain. The Fruit Fly Optimization (FOA) algorithm is used to find the optimal scaling factor. The robustness of this algorithm against various types of attacks is good due to the optimal scaling factor, but increasing the robustness against rotation and crop attacks also needs attention. In [2], an intelligent watermarking method using SVD and HVS in the DWT domain is presented by Ahmadi et al. After applying the DWT, embedding regions are selected with the help of HVS to enhance the visual quality. In this method, the scaling factor is automatically chosen by using the PSO algorithm. By selecting the appropriate area, the robustness against various attacks is high, but still, the robustness against scaling and noise needs to be strengthened. Recently, a robust WMS is proposed by Salehnia et al. [35] with a combination of SVD and lifting wavelet transform along with the three Module Redundancy approach. Most recently, the JA-fi algorithm has been developed in [6] for getting better robustness against different attacks.
2.2 Image reconstruction methods
The study of different image reconstruction techniques is presented here. As in real-world scenarios, the captured images are often destroyed by various noises, blur, etc., and hence, image IR methods are developed to restore the lost information in the captured images [8, 36]. Initially, these methods focused on reconstructing only clean low-size images to generate corresponding higher-dimension images [20]. Thereafter, these techniques are explored by many authors to make them robust to different noises, blurs, etc. [18, 30, 32]. Most of them used the least square representation-based optimization approach [20] for generating high-resolution clean images from the captured low-resolution, noisy, and blurry captured images.
3 Motivation and contributions
As insight derived from the above discussion, the handling of different attacks, especially noise and down-scaling, is still challenging for the current watermarking schemes. Hence, this paper presents the new image-reconstruction-based watermarking schemes which provide better robustness against various attacks as compared to the different competitive methods. The major contributions of this work are as follows:
-
A new optimization-based IR technique is developed that succors the proposed WMS to generate the high-quality watermark image from the extracted attacked one.
-
The objective function developed for IR is optimized statistically to get the maximum benefit of the proposed IR technique.
-
IR technique is coupled with the extraction process to develop the robust WMS.
4 The proposed algorithm
In many circumstances, watermarks are degraded and become noisy due to channel noise and different kinds of image-processing attacks. To overcome this problem, a robust WMS using a DWT-HD-SVD and optimization-based IR technique is presented in this section. The proposed WMS is described in three parts, namely (i) the embedding process, (ii) the extraction process, and (iii) the proposed IR technique. All three sections are discussed briefly in the following subsections.
4.1 Embedding Process (EP)
The EP happens in the transform domain to achieve greater robustness against various attacks. In this work, a CI and WI of size N × N and M × M, respectively, are used as inputs. The process of embedding the watermark is shown in Fig. 1. There are three steps to hide a watermark in a CI. In the first step, a 1-level DWT is performed on the CI that divides it into four sub-bands LL, HL, LH, and HH of size \(\frac {N}{2}\times \frac {N}{2}\). In the next step, the LL sub-band is further decomposed by HD to extract the matrix H. Finally, SVD is performed to extract singular values on the matrix H and the WI. Thereafter, the embedded singular value is computed with the optimal scaling factor α. The detailed embedding steps are shown in Algorithm 1.
4.2 Extraction process
The extraction process is the reverse of the embedding process. In the watermark extraction algorithm, a WI of size M × M is used as the input. The extraction process is based on DWT, HD, and SVD, which is similar to the embedding process. The procedure of the watermarking extraction is shown in Fig. 2. First, the watermarked image is decomposed into four non-overlapping sub-bands using 1-level DWT, then HD is performed on the LL sub-bands. The SVD is applied to the Hessenberg matrix H (which is the output of the previous step) to extract the singular value of H. By taking the singular value, \(HS_{w}^{ext}\) and the singular value of the CI, HSw, a reconstructed singular value \(S_{w}^{ext}\) is generated which is used in the reverse SVD to obtain the extracted watermark. The detailed extracting steps are shown in Algorithm 2.
4.3 Image reconstruction (IR) technique
In this paper, an optimization-based IR technique is proposed to make the WI robust to various attacks (especially to different digital image processing noise, filtering, and scaling). The proposed IR technique helps in generating a high-quality (HQ) version of the extracted low-quality (LQ) attacked WI. Inspired by the advantages of patch-based IR [14, 31,32,33] over the other kinds of IR techniques, this paper employs the patch-based IR concept for the reconstruction of extracted LQ WI. In addition to the input image, the proposed technique also requires some database images of the same domain.
As the proposed IR is the patch-oriented approach, we first divide the input image (extracted attacked LQ WI) into small overlapping patches, which are processed in raster scan order. Then, each input patch is expressed as a weighted linear combination of same-positioned patches in database images. From this process, a vector of weights (or coefficients) is obtained. After this, the optimization approach is applied to optimize the weights. Further, the same weights are again associated with the same database patches with generating the HQ attack-free patch. All patches of the input image follow this process. And at last, all the HQ attack-free patches are merged to form a complete image. An average value is utilized for overlapping image portions during the merge operation. The overall working of the proposed IR technique is illustrated in Fig. 3.
Illustrates the working of the proposed IR technique. Here, each patch of the extracted attacked watermark image is represented as a weighted linear combination of some patches from database images of the same domain. The weight vector (ω) obtained from this representation is optimized statistically. After this, the optimized weights are applied to the same database patches to reconstruct the high-quality watermark patch, which is free from several artifacts. All reconstructed patches are merged to form the complete image
The reconstruction process discussed above is mathematically formulated as follows:Footnote 1
where \(W^{NS}_{E}\) is the noise-suppressed watermark calculated using Algorithm 3; Dn and ωn are the nth database image and its associated coefficient, respectively; λ is the tunable parameter that balances the contribution of both terms, and M is the diagonal matrix whose elements are calculated as follows:
Equation (1) is the optimization (minimization) problem that needs to be minimized efficiently to generate optimal reconstruction coefficients. For this purpose, the (1) is re-written in matrix form as follows:
here, D is the matrix in which each column represents one database image.
Following [3], (3) can analytically be solved as follows:
In (4), \(\overrightarrow {N}\) is the N size column vector which holds value 1 and “∖” symbolize left matrix division operator; and term Q(r,c) express covariance matrix for \(W^{NS}_{E}(p,q)\). Where,
In (5), A is calculated as follows:
Further, the coefficients are re-scaled to satisfy the constraint \({\sum \limits _{n}^{N}} \omega _{n}(r,c) = 1\).
After optimization, the obtained reconstruction weights are again associated with the same set of database patches to generate an attack-free HQ output patch (WAF(r,c)). Mathematically, it is calculated as follows:
Finally, all reconstructed patches are merged to form the complete image, i.e., WAF. The above IR process in the form of pseudo-code is given in the Algorithm 4.
5 Experiments
5.1 Experimental setup and performance metrics
Several experiments and comparisons have been executed to investigate the proposed WMS’s effectiveness. The performance of the proposed watermarking scheme in terms of robustness and imperceptibility is evaluated based on five metrics, namely Normalized Cross-Correlation (NC), Bit Error Rate (BER), Normalized Absolute Error (NAE), Peak Signal to Noise Ratio (PSNR), and Structure Similarity Index (SSIM). In experiments, the most commonly used grayscale images, ‘Lena,’ ‘Man’, and ‘Sailboat’ of size 512 × 512 pixels, are picked as host images (or CI). A facial image of size 256 × 256 pixels are taken from the FEI [38] database as the WI. As the proposed IR technique also needs some images which should be of the same domain as the WI to generate the attack-free HQ watermark, therefore, the 360 images are randomly chosen from the FEI database.
As parameter tuning also plays a vital role in the performance of the proposed WMS, hence, the optimal settings of all parameters are derived experimentally in this paper. For the embedding and extraction process, the optimal value of scaling factor α is experimentally set to 0.01. Figure 4 presents the experimental results used for finding the optimal value of α. These results are computed on CI for different α values under no attack. It can be analyzed from these results that the PSNR value is more significant at 0.006, but the NC value is less at this point. However, the NC value at α = 0.013 is very good, but PSNR is average. Therefore, the value of α is set to 0.01 as it gives good PSNR and NC values which maintain a better trade-off between these performance metrics. Similarly, based on experiments, the value of τ and λ is set to 160 and 10, respectively. The PSNR and SSIM results, as shown in Figs. 5 and 6, are considered to find the optimal settings of τ and λ. These results are computed for WI under Gaussian noise = 0.001. Patch size and overlap between patches are taken as 16 × 16, and 12 pixels, respectively.
5.2 Performance analysis
To validate the effectiveness of the proposed algorithm, its performance is compared with several existing watermarking algorithms including Ansari et al. [1], Islam et al. [13], Ahmadi et al. [2], Zhang et al. [42], Liu et al. [19], Salehnia et al. [35] and Jyothsna et al. [6]. Detailed analysis is given below:
5.2.1 Robustness analysis
Normalized cross-correlation (NC) is a metric to measure the robustness of the algorithm. It compares the similarity between original WI and extracted WI. It is computed as follows:
where, W and WE represent original watermark and extracted watermark, respectively; I × J is the dimension of watermarks; and (i,j) denotes pixel in the image.
The range of NC is [-1, + 1], where, value -1 represents negative similarity and + 1 indicates that the extracted watermark and original watermark are the same. A value of NC close to or greater than 0.75 is considered acceptable. We evaluated the robustness of the proposed scheme by analyzing the NC value between the original watermark and the extracted watermark without attack, which is near 1. In experiments, the watermarked image becomes distorted under a variety of geometric and image processing attacks such as filtering, noise, rotation, cropping, scaling, JPEG-Compression, and histogram equalization. Table 2 shows the experimental results in terms of NC under different attacks with different degrees. These results show that the robustness of the watermark before applying the IR technique is poor under many attacks but after applying the proposed IR technique the image quality gets enhanced and the NC value become excellent. We can see in the table that the NC values of the Gaussian, Average, and Median filters are above 0.99 at window size 3 × 3. Similarly, the proposed scheme has strong robustness at different densities of noise as well as at different degrees of JPEG-Compression. Besides rotation at 15 degrees, all attacks have an NC value greater than 0.94.
Further, for performing the comparative analysis, NC values of the proposed scheme and several competitive methods including [1, 2, 13], and [19] under various types of benchmark attacks for different CIs are illustrated in Tables 3, 4 and 5. Using the same CI, WI, and same scaling factor the proposed scheme showed stronger robustness than [19]. We can see in Table 3, especially, against a scaling coefficient 0.125, salt & pepper noise, and speckle noise with an intensity of 0.03 the proposed scheme showed great results compared to this work. Another comparison with [13] which carried the same CI but with the binary logo as a watermark for the embedding. The proposed scheme outperformed the method [13] under filters (median and average) and Gaussian noise at 0.005 variance. Moreover, [1, 2] performed satisfactorily under various types of attacks but not better than the proposed scheme. Using the JA-fi algorithm, [6] generates an optimized scaling factor that performs well against noise but not better than the proposed algorithm. Additionally [6] exhibits limited robustness against rotating and scaling
In addition, BER and NAE are other parameters used to measure the robustness of an algorithm. BER is the error rate between the original watermark and the extracted watermark. The error rate can be defined as the ratio of the number of watermark bits that are manipulated during watermarking to the total number of bits of the watermark. The range value in BER is between 0 and 1. If the BER value is close to 0 then the error rate will be very low hence the algorithm’s robustness will be high. Calculation of BER is as follows:
Another parameter to measure the robustness of algorithm is normalised absolute error (NAE). The algorithm with a higher value of NAE is of poor quality, whereas the algorithm with a lower value is of great quality. Calculation of NAE is as follows:
Tables 6 and 7 illustrate that the proposed WMS performed better in comparison of [19] and one can conclude that the scheme proposed in this paper has outperformed in terms of robustness against geometric and image processing attacks on a various types of host images.
5.2.2 Imperceptibility analysis
Imperceptibility is a performance metric that assesses how closely the WI and the CI are the same. It is measured using two parameters: PSNR and SSIM. PSNR is a popular metric that determines how close a WI is to CI and is derived using Mean Square Error (MSE). MSE is used to find out how much of a difference is between CI and WI. A lower MSE value indicates that the CI and WI are more similar, implying that the images have a high PSNR value. It is formulated as:
The PSNR is primarily concerned with the transparency of the image but does not take into account the visual quality. The visual quality of a watermarked image is measured by SSIM. It is another metric of imperceptibility that calculates the structural similarity of a WI. Its value varies between [0,1] and if a value is close to 1 it means that it is almost the same as the original image. Following is the formula for SSIM calculation
As the proposed WMS mainly focused on robustness and image quality, therefore, in this work, the PSNR and SSIM are computed between the original WI and extracted WI rather than CI and WI. From Tables 8 and 9, it can be analyzed that the proposed WMS performs better than [19] for different images under various.
5.2.3 Visual analysis
In the visual perceptibly of the watermark or any change on the watermarked image due to the watermarking process is tested by human eyes. The visual analysis results are presented in Fig. 7. Three random cover images in Fig. 7(a), (d) and (g) are chosen and three different watermark images Fig. 7(b), (e) and (h) are embedded on them respectively. The resulted watermarked images are presented in Fig. 7(c), (f) and (i) in which the there are no visual trace of watermarks. Hence, the proposed scheme is capable to sustain the visual quality of the watermarked images.
6 Conclusions
A new robust image watermarking scheme based on the transform domain DWT-HD-SVD using an image reconstruction (IR) technique is presented in this paper for producing a high-quality watermark image (WI) from the extracted attacked one. Simulation results computed in terms of PSNR, NC, BER, SSIM, and NAE metrics confirm that the proposed watermarking scheme has stronger robustness than the other compared algorithms. These results also illustrate that the proposed scheme shows remarkable robustness against various image processing and geometric attacks especially noise, filtering, histogram equalization, and scaling.
Data Availability
Data sharing not applicable to this article as no datasets were generated or analyzed during the current study.
Notes
Note: the below formulations would be more convent to understand by referring to the notations and abbreviations given in Table 1.
References
Ansari IA, Pant M, Ahn CW (2016) Robust and false positive free watermarking in iwt domain using svd and abc. Eng Appl Artif Intell 49:114. https://doi.org/10.1016/j.engappai.2015.12.004
Bagheri Baba Ahmadi S, Zhang G, Wei S, Boukela L (2021) An intelligent and blind image watermarking scheme based on hybrid svd transforms using human visual system characteristics. Vis Comput 37(2):385. https://doi.org/10.1007/s00371-020-01808-6
Chang H, Yeung DY, Xiong Y (2004). In: Proceedings of the 2004 IEEE computer society conference on computer vision and pattern recognition, 2004. CVPR 2004., vol 1, pp I–I. https://doi.org/10.1109/CVPR.2004.1315043
Chen Y, Jia ZG, Peng Y, Peng YX, Zhang D (2021) A new structure-preserving quaternion qr decomposition method for color image blind watermarking. Sig Process 185:108088
Chopra J, Kumar A, Aggarwal AK, Marwaha A (2018). In: 2018 5th international conference on signal processing and integrated networks (SPIN), pp 413–418. https://doi.org/10.1109/SPIN.2018.8474269
Devi KJ, Singh P, Thakkar HK, Kumar N (2022) Robust and secured watermarking using Ja-Fi optimization for digital image transmission in social media. Applied Soft Computing 131:109781. https://doi.org/10.1016/j.asoc.2022.109781
Ebrahimnejad J, Naghsh A (2021) Adaptive removal of high-density salt-and-pepper noise (arspn) for robust roi detection used in watermarking of mri images of the brain. Comput Biol Med 137:104831
Elad M, Feuer A (1999) Super-resolution reconstruction of image sequences. IEEE Trans Pattern Anal Mach Intell 21(9):817. https://doi.org/10.1109/34.790425
Gakkhar D, Samant S, Sharma V, Singh SK (2010). In: 2010 international conference on signal and image processing, pp 23–28. https://doi.org/10.1109/ICSIP.2010.5697435
Hsu CS, Tu SF (2020) Enhancing the robustness of image watermarking against cropping attacks with dual watermarks. Multimed Tools Appl 79(17):11297
Hu R, Xiang S (2021) Lossless robust image watermarking by using polar harmonic transform. Sig Process 179:107833
Hu R, Xiang S (2021) Cover-lossless robust image watermarking against geometric deformations. IEEE Trans Image Process 30:318. https://doi.org/10.1109/TIP.2020.3036727
Islam M, Roy A, Laskar RH (2020) Svm-based robust image watermarking technique in lwt domain using different sub-bands. Neural Comput Appl 32(5):1379. https://doi.org/10.1007/s00521-018-3647-2
Jiang J, Yu Y, Tang S, Ma J, Aizawa A, Aizawa K (2020) Context-patch face hallucination based on thresholding locality-constrained representation and reproducing learning. IEEE Trans Cybern 50(1):324
Leng L, Li M, Kim C, Bi X (2017) Dual-source discrimination power analysis for multi-instance contactless palmprint recognition. Multimed Tools Appl 76(1):333
Leng L, Zhang J, Xu J, Khan MK, Alghathbar K (2010). In: 2010 international conference on information and communication technology convergence (ICTC), pp 467–471. https://doi.org/10.1109/ICTC.2010.5674791
Liang X, Xiang S, Yang L, Li J (2021) Robust and reversible image watermarking in homomorphic encrypted domain. Sig Process Image Commun 99:116462
Liu L, Chen CLP, Li S, Tang YY, Chen L (2017) Robust face hallucination via locality-constrained bi-layer representation. IEEE Trans on Cybern PP(99):1
Liu J, Huang J, Luo Y, Cao L, Yang S, Wei D, Zhou R (2019) An optimized image watermarking method based on hd and svd in dwt domain. IEEE Access 7:80849. https://doi.org/10.1109/ACCESS.2019.2915596
Ma X, Zhang J, Qi C (2010) Hallucinating face by position-patch. Pattern Recogn 43(6):2224
Mohammed AA, Salih DA, Saeed AM, Kheder MQ (2020) An imperceptible semi-blind image watermarking scheme in dwt-svd domain using a zigzag embedding technique. Multimed Tools Appl 79(43):32095
Mondal B, Kumar D, Mandal T (2015) Security challenges in internet of things, Int J Softw Web Sci, pp 8–12
Mondal B, Mandal T, Choudhury T, Khan D A (2019) Use of’a light weight secure image encryption scheme based on chaos and dna computing’for encrypted audio watermarking. Int J of Adv Intell Paradigms 13(1-2):67
Mondal B, Mandal T, Khan DA, Choudhury T (2018) A secure image encryption scheme using chaos and wavelet transformations. Recent Patents Eng 12(1):5
Mondal B, Singh JP (2022) A lightweight image encryption scheme based on chaos and diffusion circuit. Multimed Tools Appl pp 1–25
Pandey P, Kumar S, Singh SK (2014) A robust logo watermarking technique in divisive normalization transform domain. Multimed Tools Appl 72:2653
Pandey P, Kumar S, Singh SK (2014) Rightful ownership through image adaptive dwt-svd watermarking algorithm and perceptual tweaking. Multimed Tools Appl 72:273
Prabha K, Sam I S (2020) An effective robust and imperceptible blind color image watermarking using wht. Journal of King Saud University-Computer and Information Sciences
Qi W, Guo S, Hu W (2022) Generic reversible visible watermarking via regularized graph fourier transform coding. IEEE Trans Image Process 31:691. https://doi.org/10.1109/TIP.2021.3134466
Rai D, Rajput S S (2022) Robust face hallucination algorithm using motion blur embedded nearest proximate patch representation. IEEE Trans Instrum Meas, pp 1–1. https://doi.org/10.1109/TIM.2022.3223141
Rajput SS, Arya KV (2019) Square, noise robust face hallucination via outlier regularized least representation, neighbor. IEEE Transactions on Biometrics, Behavior, and Identity Science 1(4):252
Rajput SS, Arya K, Singh V (2018) Robust face super-resolution via iterative sparsity and locality-constrained representation. Inf Sci 463–464:227
Rajput S S, Singh A, Arya K, Jiang J (2018) Noise robust face hallucination algorithm using local content prior based error shrunk nearest neighbors representation. Sig Process 147:233
Sakthivel S, Sankar A R (2020) Computation-efficient image watermarking architecture with improved performance. Comput Electr Eng 84:106649
Salehnia T, Fathi A (2021) Fault tolerance in lwt-svd based image watermarking systems using three module redundancy technique. Expert Syst Appl 179:115058
Sheppard D, Panchapakesan K, Bilgin A, Hunt B, Marcellin M (2000) Lapped nonlinear interpolative vector quantization and image super-resolution. IEEE Trans Image Process 9(2):295. https://doi.org/10.1109/83.821746
Singh SK, Kumar S, Srivastava M, Chandra A, Srivastava S (2009). In: 2009 third UKSim European symposium on computer modeling and simulation, pp 241–244. https://doi.org/10.1109/EMS.2009.114
Thomaz CE, Giraldi GA (2010) A new ranking method for principal components analysis and its application to face image analysis. Image Vis Comput 28(6):902
Wang XY, Tian J, Tian JL, Niu PP, Yang HY (2021) Magnitudes, statistical image watermarking using local rhfms distribution, beta exponential. J Vis Commun Image Represent 77:103123
Zermi N, Khaldi A, Kafi MR, Kahlessenane F, Euschi S (2021) Robust svd-based schemes for medical image watermarking. Microprocess Microsyst 84:104134
Zhang L, Wei D (2020) Robust and reliable image copyright protection scheme using downsampling and block transform in integer wavelet domain. Digit Sig Process 102805:106
Zhang L, Wei D (2020) Image watermarking based on matrix decomposition and gyrator transform in invariant integer wavelet domain. Sig Process 169:107421
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interests
We state that there is no conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Rajput, S.S., Mondal, B. & Warsi, F.Q. A robust watermarking scheme via optimization-based image reconstruction technique. Multimed Tools Appl 82, 25039–25060 (2023). https://doi.org/10.1007/s11042-023-14363-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-14363-8