Abstract
Communication networks, play a major role in keeping us connected and sharing the details of our lives with each other. The main driver of multimedia data transmission is to enhance security protection of this multimedia data (speech, image and video). In this paper we addresses the synchronization problem of the masterslave type via a static error feedback. Sufficient conditions expressed by means of linear matrix inequalities (LMI) for the synchronization of fractional-order hyperchaotic systems with a known time delay between them is presented. The delay-dependent criterion is given based upon a Lyapunov function. We take the fractional-order hyperchaotic Liu system as an illustrative example to demonstrate the effectiveness of the proposed synchronization scheme. Moreover, as an application an images cryptosystem is presented. We considered two scenarios corresponding to the transmission channel, under occlusion attack and under noisse addition respectively. Results for the studied scenarios are presented and compared. The extensive simulation results prove that proposed cryptosystem has clear advantage over other proposed in the litterature.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
The dynamic response of a chaotic system with its broadband power spectra that is very similar to noise, is an ideal candidate for combating narrow-band disturbances in communication systems [38]. The dependence of the initial conditions is another intersting feature of chaotic signals, which makes it very difficult to know the structure of the generator and predict the signal over the distant future. Moreover, they are aperiodic, in that the same state is never repeated twice which make them very suitable for image encryption [1, 19]. A chaotic system can caracterized by one positive Lyapunov exponent, on the other hand a hyperchaotic system have more than one positve Lyapunov exponent, in fact higher dimensional chaotic systems with more one Lyapunov exponent clearly exhibit more complex dynamics[57]. One of the major problems in implementing chaotic based communication systems is the synchronization [4, 27, 34, 48].For this last decade, numerous contributions on the chaos synchronization have been made by researchers from different disciplines. In 2000 [8] was the first report on propagation delay in master-slave configurations. The authors called this a phase sensitivity and the existence of it can destroy the synchronization. On the other hand, in the area of control theory time-delay systems have been investigated and the delays often affect the stabilities. Therfore investigating time-delay systems stability becomes an important subject [49].
On the other hand, it is worthy noticing that the propagation delay may exist in the remote communication systems. For the time-delay chaotic systems, the propagation delay might not be equal to the system time delay. The propagation delay problem was reported and studied theoretically in [7, 29, 49]. In [49] the authors initiated the master-slave synchronization scheme for Lur’e type chaotic systems with propagation delay. The same problem was further investigated in [29] where some improving results were presented. In [7], the authors recast it as a more general synchronization problem based on the delayed feedback control scheme where the controller time delay is the propagation delay.
Fractional calculus, are powerful mathematical tools that handles with the differentiation and integration of noninteger orders. In past decades, fractional-order systems have represented an emerging research because of their capability to better exemplify real-world applications. In fact fractional-order systems are feature by an innite memory. Many literatures have demonstrated that some fractional order systems can have a chaotic regime. Several fractional-order chaotic systems have been reported in many studies [16,17,18]. More recently, the synchronization problems of fractional-order chaotic systems becomes an attractive challenge, and many schemes have been proposed [12, 33, 35, 50]. In [35] fractional-order chaos synchronization is investigated where the authors applied a linear controller to the slave system. The authors in [50] based on the comparaison principales studied a lag projective synchronization of fractional-order chaotic systems with time delay. In [12] a function cascade synchronization method for achieving complete synchronization, modified projective synchronization and anti-phase synchronization of two fractional-order hyperchaotic systems was proposed.
These days, one can easily transmit countless of informations through communication network. However, because of the openness of the network, there is a higher concerns of concealment of the informations. The digital image is an important information vector of multimedia communication, thus how to protect the image information becomes high a concern problem, and fascinate a lot of researchers. Cryptosystems have been developed for such reasons to prevent the information from the attackers. However, most conventional cryptosystems such as DES, IDEA and AES are not suitable for image transmission in a noissy channel, because of the inherent features of image such as the strong correlation among adjacent pixels. To cater this problem and due of the features chaotic signals have a lot of chaos-based cryptosystems have been developed up to now [10, 13, 21, 30, 39,40,41, 43, 51, 53]. The main objective of the cryptosystem proposed in [43], is to improve the permutation efficiency and reduce the computation cost, the authors use a heterogeneous bit-permutation and then use a XOR operation. By DNA sequences operation, the authors in [53] shuffled the pixels value of the plain image, and by using the generated sequences from a fractional order hyperchaotic system a pemutation operation on the pixels position is performed. In [40], a cryptosystem is presented, which a SHA-2 function is used to generate the initial conditions for the chaotic systems, after a DNA exclusive-OR is perform for pixel substitution. In [30], based on the region of interest the authors propose a multidimensional chaotic image cryptosystem. The region is messed up by using the improved Henon and Joseph sequences and diffused it using the unified chaotic sequence to hide the sensitive information in the image. Furthermore, they used the improved logistic map to hide the edge information of the target image to achieve a balance between the secrecy of information and the complexity of the encryption. A cryptosystem based on fractional-order chaotic systems has a higher security level, in addition has an improvement on the encryption key space [24, 47, 48, 56]. More recently, many images cryptosystems built from fractional-order chaotic systems have been proposed [20, 28, 32, 33, 46, 52]. An anti-synchronization scheme for fractional order reverse butterfly- shaped hyperchaotic systems is investigated via active control technique, then a cryptosystem is presented in [33].
Motivated by the above discussions, in this paper a synchronization scheme between two identical fractional-order hyperchaotic systems via a static error feedback is presented. In an application point of view, the synchronized systems are applied in a new images cryptosystem. In the confusion (scrambling) stage, two permutations processes are designed to break inter-intra correlation of the plain image. The first is done by cyclic shift operations and according to the selected chaotic sequences indexes we perform the other one. In the diffusion stage, we performs the XOR and expanded XOR operations for each components of the scrambled image, to obtain the encrypted image. Compared with the existing works in the literature, the principal contributions of this study can be summarized as:
-
Propagation time-delay has been considered.
-
The derived criterion is a sufficient condition for the stability of the error dynamics between the master and the slave systems.
-
A new cryptosystem for color images.
The rest of this paper is organized as follows: Section 2 is devoted to present some basic preliminaries. In Section 3, we present the master-slave synchronization scheme of fractional-order hyperchaotic systems and a delay-dependent criterion for the asymptotic stability based on a Lyapunov function is derived. A new cryptosystem is illustrated in Section 4. In Section 5 simulations results for images encryption and decryption with some robustness analysis are presented and discussed. Finally we provide conclusions in Section 6.
2 Preliminaries
The most used definitions for fractional differential equations, given by the first pioneers Grünwald—Letnikov, Riemann–Liouville and Caputo are detailled [37]. As compared with the Caputo fractional operator, the main advantage of the Riemann—Liouville fractional operator lies in the composition properties of its fractional derivatives and integrals. Therefore, our consideration in this paper is the fractional-order systems with the Riemann—Liouville fractional operator.
Definition 1
The Riemann—Liouville fractional integral of a function f(t) with respect to time is defined as follows [37],
and the fractional derivative also defined as,
where m = [α] + 1 and [α] is the integer part of α and \({\varGamma }(S)={\int \limits }_{0}^{\infty } t^{S-1}e^{-t}dt\), with Γ(S + 1) = S Γ(S) is the well-known Euler’s gamma function.
Property 1 [37].
Lemma 1
[9]
Let v1 and v2 be real vectors of appropriate dimensions. For any positive scalar μ, we have:
Lemma 2
[25]
If α > β > 0, then the following property
holds for sufficiently good functions x(t). In particular, this relation holds if x(t) is integrable.
Lemma 3
[31]
Let \( x(t): R^{n} \rightarrow R^{n}\), be a vector of differentiable function. Then for any time instant t ≥ t0, the following relationship holds,
where P ∈ Rn×n is a constant, square, symmetric and positive definite matrix.
Lemma 4
(Barbalat’s lemma) [23]
Assume that f(t) is a function of time and has a limit when \(t \rightarrow \infty \), if \(\dot {f}(t)\)is uniformly continuous (\(\ddot {f}(t)\)is bounded), then \(\dot {f}(t) \rightarrow \infty \) as \(t \rightarrow \infty \).
Lemma 5
For any positive definite matrix R > 0, a scalar τ > 0, vector function, \(f(.):[0,\tau ]\rightarrow R^{n}\) such that the integrations concerned are well defined, the following inequality holds :
Definition 2
(improved expanded XOR operation) [6, 42]
The improved expanded XOR operation introduce an enhancement on the overall security level of the proposed scheme. For two inputs \(r1={\sum }_{i=0}^{7} r1_{i}\) and \(r2= {\sum }_{i=0}^{8} r2_{i}\), the operator can be described as,
where not(r1) flips a single bit r1. The operator has the following property: if eXOR(r1, r2) = t, then eXOR(t,r2) = r1. This property can be deduced from Table 1 as,
3 Synchronization scheme
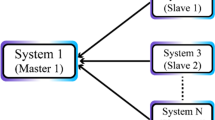
Consider the following master—slave synchronization scheme with a time delay τ:
The state vectors of the master and slave systems are x ∈ Rn and y ∈ Rn, respectively. The matrices A ∈ Rn×n, \(B\in R^{n \times n_{h}}\), \(C \in R^{n_{h} \times n}\) and H ∈ Rl×n are known real constant matrices. and q(t) ∈ Rm are the outputs of the master and the slave systems, respectively. The main objective of this scheme is to synchronize the master system \({\mathscr{M}}\) and the slave system S by applying a linear state error feedback to the slave system with control signal u(t) ∈ Rn with feedback matrix F ∈ Rn×l. Defining the synchronization error as e(t) = x(t) − y(t), the error dynamic can be obtained as,
Assumption 1
For robustness, we will assume that f(x(t)) satisfy the following Lipschitz property:
where le is an appropriate positive constants. We note that the Lipschitz properties are satisfied locally if f(x(t)), is differentiable with the respect of x(t).
3.1 Delay-dependent synchronization criteria
In this section, the stability of the error system \(\mathcal {E}\) given in (10) is explored in order to obtain a synchronization criteria.
Theorem 1
for a given τ > 0 and le > 0, the error system described as (10) is asymptoticly stable if there exists the matrices P = PT > 0, \(R_{1}={R}_{1}^{T}>0\), \(R_{2}={R}_{2}^{T} >0\) and \(R_{3}={R}_{3}^{T} >0\), a matrix F with appropriate dimensions and constant positive scalars μ1 and μ2 there is a solution of the following optimization problem:
where F = P− 1X, I is the n × n identity matrix and ϕmax is the maximum eigenvalue function.
Remark 1
The matrix inequalites (12) include information on the delay. Therefore this result is a delay–dependent stability criterion for synchronization.
Proof Proof of theorem
Let us construct a Lyapunov function in the following form:
where in case α = 1, this function is reduced to a classical Lyapunov-Krasovskii function in the integer-order calculus (see Property 1), and in the case when 1 > α > 0, the term \(D_{t}^{-(1-\alpha )}\left [e^{T}(t) P e(t)\right ]\) is constructed as a Rieman-Liouville fractional integral, thus according to Definition 1 and integral property the positive defitiveness is guaranted. □
An application of Property 1 and Lemma 2, we get the time derivative of (13) as,
Applying Lemma 3 to the right side of (14) results we get,
Substituting (10) in (15) yields to,
In view of Assumption 1 and Lemma 1, we obtain,
and
where \(\phi _{max}\left (\bullet \right )\) represnt the maximum eigenvalue of a matrix.
By using the inequality (7) we obtain the following :
and
Thus, we have
Therefore,
where \(\xi (t)=\left [e(t);e(t-\tau );{\int \limits }_{t-\tau }^{t} e(\sigma ) d\sigma \right ]\) and Z =
with X = PF. Then if Z < 0, then \(\dot {V}(t)\le 0\). To derive asymptotical stability we use the Barbalat’s lemma. Form \(\dot {V}(t)<0\) it is obtain that V (t) < V (0). To verify the boudennes of \(\ddot {V}(t)\), it needs to show that ξ(t) ∈ ℓ2. Note that V is a non-increasing and positive definite function then:
then
where λmin(−Z) represent the minimum eigenvalues of − Z. From (25), it is concluded that ξ(t) ∈ ℓ2. Then it is derived that \(\lim _{t\rightarrow \infty }\dot {V}(t)=0\), the asymptotic stability is concluded. This completes the proof.
3.2 Illustrative example
In this subsection, we will numerically verify the effectiveness of the proposed synchronization scheme between two identical fractional-order hyper-chaotic Liu systems [16].
The master system is given by
and the slave system as
where η1 = 10, η2 = 40, η3 = 0.5, η4 = 2.5 and η5 = 10/15.
Thus the systems matrices in (9) are \(A=\left [ \begin {array}{cccc} -\eta _{1}&\eta _{1}&0&1\\ \eta _{2}&0&0&\eta _{3}\\ 0&0&\eta _{4}&-1\\ 0&-\eta _{5}&0&-1 \end {array} \right ]\), \(B=\left [ \begin {array}{ccc} 0&0\\ 1&0\\ 0&1\\ 0&0 \end {array} \right ]\), \(f(x(t))=\left [ \begin {array}{lr} -x_{1}(t)x_{3}(t)\\ 4{x}_{1}^{2}(t) \end {array} \right ]\) and \(f(y(t))=\left [ \begin {array}{lr} -y_{1}(t)y_{3}(t)\\ 4{y}_{1}^{2}(t) \end {array} \right ].\)
Initial conditions are selected as: x(0) = [2, − 1, 0.8, 0.8]T and y(0) = [5, 3, 2, 1]T respectively. We choose \(C=\left [ \begin {array}{cccc}1&~ 0 &~ 0 &~1 \end {array}\right ] \) (it can be easily verified that \(\left (C,A \right )\) is an observable pair). The matrices P, X and Ri= 1,2,3 and the scalares μj= 1, 2 are found using Matlab LMI optimization toolbox with łe = 5 and τ = 0.163 as :
\(R_{1}=10^{-4} \times \left [ \begin {array}{cccc} 0.6403 &~ -0.1115 &~ -0.0701 &~ -0.0761\\ -0.1115 &~ 0.7144 &~ -0.0725 &~ -0.1025\\ -0.0701 &~ -0.0725 &~ 0.6827 &~ -0.1333\\ -0.0761 &~ -0.1025 &~ -0.1333 &~ 0.6584 \end {array} \right ]\), \(R_{2}= 10^{-3} \times \\\left [ \begin {array}{cccc} 0.1486 &~ -0.0018 &~ -0.0025 &~ -0.0031\\ -0.0018 &~ 0.1484 &~ -0.0024 &~ -0.0022\\ -0.0025 &~ -0.0024 &~ 0.1486 &~ -0.0021\\ -0.0031 &~ -0.0022 &~ -0.0021 &~ 0.1479 \end {array} \right ]\), \(R_{3}=10^{-4} \times \\ \left [ \begin {array}{cccc} 0.6832 &~~~~~~~ -0.0746 &~~~~~~~ -0.0463 &~~~~~~~ -0.0475\\ -0.0746 &~~~~~~~ 0.7393 &~~~~~~~ -0.0454 &~~~~~~~ -0.0691\\ -0.0463 &~~~~~~~ -0.0454 &~~~~~~~ 0.7153 &~~~~~~~ -0.0891\\ -0.0475 &~~~~~~~ -0.0691 &~~~~~~~ -0.0891 &~~~~~~~ 0.6959 \end {array} \right ]\), μ1 = 2.1032 × 10− 5, μ2 = 5.0017 × 10− 6, \(X=10^{-4} \times \left [ \begin {array}{cc} -0.1535 \\ 0.2944 \\ -0.0626\\ 0.0719 \end {array} \right ]\), \(P=10^{-5} \times \left [ \begin {array}{cccc} 0.1144 &~ -0.0344 &~ 0.0014 &~ 0.0047\\ -0.0344 &~ 0.1035 &~ -0.0020 &~ -0.0096\\ 0.0014 &~ -0.0020 &~ 0.0935 &~ 0.0010\\ 0.0047 &~ -0.0096 &~ 0.0010 &~ 0.0919 \end {array} \right ]\) and \(F=\left [ \begin {array}{cc} -5.5159 \\ 27.5302 \\ -6.1322\\ 11.0624 \end {array} \right ]\). Note that, one can easily find that Z is a negative definite matrix. The fractional orders αi(i= 1,2,3,4) are also set to 0.9 to ensure the existence of chaos [16].
Figure 1a-d show the state trajectories of the master and slave systems. The synchronization errors are revealed in Fig. 2a-d. As expected, one can observe that the state trajectories of the slave system track those of the master, and the synchronization errors tend to zero.
4 The proposed cryptosystem
The architecture of the proposed encryption algorithm is shown in Fig. 3.
As can be seen, a fractional-order hyperchaotic system is used as pseudo-random generator. The pixel positions of the plain image are scrambled first by circular permutations and secondly by the sorted chaotic sequences index positions. Finally the substitution of the pixels value is done by a XOR and expanded XOR operations. The encryption algorithm can be described as follows.
4.1 Generating and selecting the chaotic sequences
Due that the synchronization between the master and the slave systems, need some time to occur (see Fig. 2). Equation (9) is iterated TS + 8MN time to generate the chaotic sequences after we discard the first TS elements to avoid initial synchronization errors.
4.2 Generation of the scrambling and diffusion sequences
In this stage we generate S1, S2, Ind.xi and \(D_{f_{i}}\), where S1, S2 and Ind.xi are used as scrambling sequences and \(D_{f_{i}}\) as diffusion sequences. The following described the generation process.
4.2.1 Scrambling sequences
-
Step 01 Sort the first MN elements of the selected chaotic sequences x1,2,3 in ascendant order according to the following equation:
$$ [Val.x_{i}(K)~,Ind.x_{i}(K)] = sort (x_{i}(K)) , \quad i=1,2,3 ,\quad K=1,2,\dots,MN $$(28)where V al.xi, Ind.xi are arrays with size 1 × MN which contains the values and the indexs position respectively.
-
Step 02 Produce three others arrays \(x^{\prime }_{i}\) with size 1 × 8MN by the following formula:
$$ {x}_{i}^{\prime}= mod\left( \left[(\lceil|x_{i}|\rceil-|x_{i}|) \times 10^{8}\right],256\right),\quad i=1,2,3 $$(29)where |∙| denote the absolute value, mod(∙) refer to the module operation and ⌈a⌉ refers to get the smallest integer greater than or equal to a.
-
Step 03 Combien all there arrays \({x}_{i}^{\prime }\) into an array S with the size 1 × 24MN.
$$ S=cat({x}_{1}^{\prime}, {x}_{2}^{\prime}, {x}_{3}^{\prime}) $$(30)Then get two new arrays S1 and S2 with the length M and 24N respectively, using (31) shown as follows,
$$ \begin{array}{@{}rcl@{}} &&S1= \left[S(1),S(2),\dots,S(M) \right]\\ && S2= \left[S(M+1),S(M+2),\dots,S(24N) \right] \end{array} $$(31)
4.2.2 Diffusion sequences
-
Step 01 The arrays V al.xi are processed using (32) as follows,
$$ Val.x_{i} =mod\left( \left[(\lceil|Val.x_{i}|\rceil-|Val.x_{i}|) \times 10^{8}\right],256\right) $$(32)then transform them to binary matrices BVi with the size of M × 8N and combine them into a M × 24N matrix TV by the following:
$$ T_{V}=cat(BV_{1},~BV_{2},~BV_{3}) $$(33) -
Step 02 Rows circular shift. The rows shift result \({T}_{V}^{\prime }\) is obtained by following rules: the row rw of TV is moved by the step number S1(rw) and \(rw=1,2,\dots ,M\).
-
Step 03 Process the matrix \({T}_{V}^{\prime }\) by a circular column shift operation where the column col of \({T}_{V}^{\prime }\) is moved by the step number S2(col) and \(col=1,2,\dots ,24N\) resulting \(T_{V}^{\prime \prime }\).
-
Step 04 Convert the binary values of \({T}_{V}^{\prime \prime }\) into decimal base resulting a matrix with size M × 3N then split it into three sub–matrices \(T_{sub_{i=1,2,3}}\) with size M × N and after combine the elements of each sub-matrix \(T_{sub_{i=1,2,3}}\) into an array \(D_{f_{i=1,2,3}}\) with size 1 × MN respectively.
-
Step 7 Substitute the elements of each array \(D_{f_i}\) using the XOR operation as follows,
$$ D_{f_{i}}= D_{f_{i}} \oplus Val.x_{i} $$(34)where the ⊕ denotes the XOR operation.
4.3 Image scrambling
The proposed scrambling of the plain image is performed by the following steps
-
Step 01 Decompose the RGB image P into PR, PG, PB components, then transform them into binary matrices R, G, B with the size of M × 8N and combine them into a M × 24N matrix TE as:
$$ T_{E}=cat(R, G, B) $$(35) -
Step 02 Rows circular shift. The rows shift result \({T}_E^{\prime }\) is obtained by following rules: the row rw of TE is moved by step number S1(rw).
-
Step 03 Process the matrix \({T}_E^{\prime }\) by a circular column shift operation, where the column col of \({T}_E^{\prime }\) is moved by step number S2(col) resulting \({T}_E^{\prime \prime }\).
-
Step 04 Convert the binary values of \({T}_E^{\prime \prime }\) into decimal base resulting a matrix with size M × 3N, then split it into three sub–matrices of size M × N after combining the elements of each sub–matrices into 1-dimensional arrays \(I_{D_{i=1,2,3}}\) with size 1 × MN then rearrange the elements of each \(I_{D_{i=1,2,3}}\) according to Ind.xi= 1,2,3 respectively to get the scrambled image as shown in the following equation
$$ I_{D_{i}}(K)=I_{D_{i}}(Ind.x_{i}(K)) , \quad i=1,2,3 ,\quad K=1,2,\dots,MN $$(36)
4.4 Image diffusion
In this stage we proceed as follows,
-
Step 1 Diffuse the elements of each array \(I_{D_{i}}\) as follows:
$$ I_{E_{i}}=I_{D_{i}} \oplus D_{f_{i}} $$(37) -
Step 2 Use the XOR and expanded XOR operations to perform another substitution by the following equation
$$ \begin{array}{@{}rcl@{}} I_{E_{i}}(K)=&&eXOR\left( \left( I_{E_{i}}(K), \left( mod \left( \left( (4 \times x_{i}(K)-2 \times x_{i+1}(K)) \times 10^{8}\right),256\right)\right)\right) \right) \oplus (mod (\\ & & \left( x_{i+1}(K)\times 10^{8}\right),256)) , \quad i=1,2,3 ,\quad K=1,2,\dots,MN \end{array} $$(38) -
Step 3 Convert the arrays \(I_{E_{i}}\) into matrices with size M × N which are separately the red, green and blue components of the final encrypted image.
4.5 Decryption process
The decryption is done by an inverse of encryption process, using the synchronized sequences \( y_{j(j=1,2,3,\dots ,n)}\). The decryption is done by a inverse of encryption process, using the synchronized sequences \( y_{j(j=1,2,3,\dots ,n)}\).
5 Numerical simulation and cryptanalysis
For the experimental setup a Matlab version 9, operating system Windows 7, processor Core i5-3320M and 4 GB memory were used. In the simulations the fractional order hyperchaotic Liu system is used. The cryptosystem is applied on sevral different images named Lena, Panda, Vegetables, Baboon, Peppers, Girl, Black and also images from USC-SIPI database set. The plain images are shown in Fig. 4a-c while corresponding encrypted and decrypted images are shown in Fig. 4d-i, respectively.
Encryption and Decryption output of the proposed cryptosystem. a plain-image of Lena. b plain-image of Vegetables. c plain-image of Panda. d encrypted-image of Lena. e encrypted-image of Vegetables. f encrypted-image of Panda. g decrypted image of Lena. h decrypted image of Vegetables. i decrypted image of Panda
The following evaluation parameters, were taken into consideration to test the performance of the proposed cryptosystem.
5.1 Key space
A good cryptosystem, should have a large enough key space to resist an exhaustive. Here, the fractionbal order derivatives αi(i = 1 : 4) and the parameters ηi(i = 1 : 5) are used as the secret key, therefore, the secret key-set is as (η1, η2, η3, η4, η5, α1, α2, α3, α4), where each key independent of others. In the simulations (repeated over 100 times) we find that the precision of each secret key is approximately 10− 15, then the key space size is about 10135, so it can resist brute force attacks and in comparison with the references given in Table 2 it larger than [11, 14, 36, 40, 44].
5.2 Differential analysis
It is well known that a good algorithm can also withstand a brutal differential attack. To test it resistance, two known tests known as Changing Pixel Frequency Rates (NPCR) and Unified Average Intensity Change (UACI) which introduce by [2, 3] to investigate a cryptosystem against differential attacks. The NPCR test is given by (39) and the UACI by (40) as follow
where E1 and E2 are two encrypted images generated from inputs which differ in one-bit only. M, N represent the height and width of the encrypted images and L denotes the largest intensity allowed in the image for any pixel respectively. D(i,j) is defined like follows
The NPCR and UACI scores for Lena, Panda, Vegetables and Peppers encrypted images are listed in Table 3. The NPCR and UACI scores are compared to [13, 40, 53].
5.3 Key sensitivity analysis
An efficient cryptosystem should have a sensitivity to its secret key-set. In anthoer word a very small change in the secret key-set will cause a significant change in the decrypted image. To analyze the sensitivity of the secret key-set we do a litlle modification in initial one (i.e γ0 = (η1, η2, η3, η4, η5, α1, α2, α3, α4)) we obtaine the other secret key-sets as following γ1 = (η1 + 10− 15, η2, η3, η4, η5, α1, α2, α3, α4), γ2 = (η1, η2 + 10− 15, η3, η4, η5, α1, α2, α3, α4), γ3 = (η1, η2, η3 + 10− 15, η4, η5, α1, α2, α3, α4), γ4 = (η1, η2, η3, η4 + 10− 15, η5, α1, α2, α3, α4),γ5 = (η1, η2, η3, η4,η5 + 10− 15, α1, α2, α3, α4), γ6 = (η1, η2, η3, η4, η5, α1 + 10− 15, α2, α3, α4), γ7 = (η1, η2, η3, η4, η5, α1, α2 + 10− 15, α3, α4), γ8 = (η1, η2, η3, η4, η5, α1, α2, α3 + 10− 15, α4) and γ9 = (η1, η2, η3, η4, η5, α1, α2, α3, α4 + 10− 15). Using the secret key-sets, the rate of difference is calculated for Lena, Vegetables and Panda and shown in Tables 4 and 5. The results of key sensitivity are also compared to [40, 45] and the proposed cryptosystem has clear advantage over it.
5.4 Statistical analysis
5.4.1 Histogram and uniformity analysis
The image histogram reflects the distribution of the pixels value. A strong cryptosystem should mask the perceptual meaning of the plain image and flatten its histogram (i.e., become near uniform distribution). The histograms before and after encryption are shown in Fig. 5 for the test image Lena. It clear that the encrypted image histograms are sufficiently uniform.
According to the quantitative analysis method in [49], to measure the uniformity of an encrypted image we compute the variance of it histograms. The lower the variance value indicate a higher uniformity of the encrypted image The variance can be calculated as
where zi and zj are the frequencies at ith and jth gray levels respectively. In Table 6, the variances of histograms of encrypted images, for each secret key-set are provided.
In order to further examen the influence of the modification of the secret set-keys on the uniformity of the encrypted images, we compute the percentage of the variance differences between two encrypted images obtained separately by the initial secret key-set g0 and the secret key-sets γi(i = 1,2,...,9). The percentage can be computed by (43) as,
where \(PP(var)_{\gamma _{i}}\) is the percentage of variance difference when only one key is changed, \(var_{\gamma _{0}}\) and \(var_{\gamma _{i}}\) represent the histogram variances of the encrypted image by the secret key-set γ0 and \(\gamma _{i=1,2,\dots ,9}\) respectively. The results are listed in Table 7. The percentage of average variance difference scores by the proposed cryptosystem are better than [45] and comparable to [40].
5.4.2 Correlation of two adjacent pixels
It well known that in an image there is strong interconnected relationship between a adjacent pixels in the horizontal, vertical and diagonal directions, so it is very important for a good encryption process to not preserve those relationships or at least weaken them, to get the ability to face on statistical attacks. Those relationships are elaborated in Fig. 6a-c for plain Lena image Fig. 4a and Fig. 6d-f for the corresponding encrypted Fig. 4d.
In the simulations, we select randomly 3000 pairs of adjacent pixels to measure the correlation coefficients for Fig. 4a and Fig. 4d in the three directions using (44),
where the covariance cov(x,y) is obtainted by
the variance value D(x) is obtainted by
the mean value E(x) is obtainted by
and x, y are the gray values of two adjacent pixels and L is the number of samples taken , (in this case L = 3000). The results are listed in Table 8, and it clear that our algorithm has a low correlation as compared with the plain image (i. e. no information leakage from the encrypted images when statistical attacks happen). One can easily see that the results are comparable to the results in [13, 40, 42].
5.5 Evaluating the pixels randomness
It is observed from Fig. 4d-f that the encrypted images appear to be noise and similar to random images, so the proposed cryptosystem sucessfully masked the perceptual semantic of the plain images. we use the information entropy metric and the Chi-Square test to evaluate this randomness.
5.5.1 Information entropy
The information entropy is evaluated to analyze the spreading of the gray scales of the image, in other words to measure the randomness of the image. The ideal entropy score of encrypted message is 8 in higher the value higher will be the uniform distribution. Mathematically, we can represent the entropy H for a data source x is characterized as:
where Pr(xi) and k are the probability and the total number of the gray value xi, respectivly.
We have calculated the information entropy for five plain images and their corresponding encrypted images by using our encryption algorithm and some other [13, 39, 40]. The results are given in Table 9. It’s well shown that the information entropy values obtained by our proposed cryptosystem is far better than [39, 40] and comparable to [13] and we can see that our scores are very close to the theoretical value.
5.5.2 The Chi-Square test
The variance of an histogram is the output which represents the variation in the frequency of gray levels and the Chi-square score is a measurement of how expectations are compare with the output. The low scores of Chi-square demonstrate that we have a better randomness in the encrypted image. The Equation for Chi-Square test can be defined as follow,
where zi is the number of pixels at ith gray level and kk/256 is the expected frequency at ith gray level. The scores of the Chi-square test for three different images are listed in Table 10 and compared with [13, 14, 40]. From the results The are comparable to [13, 14], and better than [40].
5.6 Pixel modification based measurements
The quality of an image depends upon the pixel difference which is calculated by means the mean square error (MSE) and peak signal to noise ratio) values (PSNR). Those metrics are for the comparison of unlike images.
5.6.1 The mean square error
An encrypted image should not be equivalent to the plain image due to the application of the encryption procedure, which surely adds some noise to the actual digital content. We compute the Mean Square Error (MSE) between the plain and encrypted images to analyze the level of enciphering. Mathematically, MSE is defined as:
where E and I represent the encrypted and the plain images respectively. M and N indicate the width and the height of the test image, respectively. A larger value of the MSE enhances the security. Table 11 provides a comparison of the MSE scores of our proposed cryptosystem with the one in [10]. The table shows that our proposed cryptosystem has clear advantage.
5.6.2 The Peak Signal Noise Ratio
PSNR metric is a ratio between the plain and the encrypted images [8,50]. It employed as a security evaluation parameter when the plain and the encrypted images are taken as a signal and a noise respectivtly. A higher value of PSNR declare that the encrypted image is close to the plain image which is of course not desirable in any encryption procedure. Mathematically, PSNR can be written as:
The lower PSNR value provide an evidence that a plain image is significantly different from its corresponding encrypted and also become very difficult to retrieve it. The result for PSNR metric is listed in Table 12. As compared with the other algorithms in [13, 39, 40], the effectiveness of the proposed cryptosystem is evident by lower values of PSNR.
5.6.3 The gray difference degree (GVD)
The gray difference degree is another measure of pixel modification by comparing the plain and the encrypted image. The GVD score approaches to 1 indicates that the two images are completely different.
where the pair \((x^{\prime },y^{\prime })\) comes in fourth cases like \((x^{\prime },y^{\prime })=\left \{ \begin {array}{lr} (x-1,y)\\ (x,y-1)\\ (x+1,y)\\ (x,y+1) \end {array} \right .\). I(x,y) and \(I(x^{\prime },y^{\prime })\) represents the gray score at position (x,y) and \((x^{\prime },y^{\prime })\) respectively.
The GVD, can be computed by using Eq. (53) as
where
and AN and \(AN^{\prime }\) are the Average Neighborhood gray value before and after the encrypting respectively. Table 13 contains the GVD values of images from USC-SIPI database set (Table 14). Further we compute the GVD score of Lena and Baboon images as shown in Table 15. The listed results are comparable to [13, 40].
5.7 Robustness analysis
In the real issue, the errors often occur in the data while being transmitted by a physical communication system. A unimportant change in the encrypted image may cause a strong distortion in the decryption procedure which results in failure to recover the plain image such that one can loses the plain image completely. A decent cryptosystem should be designed in a way that it does not have domino effect in the decryption procedure [40]. To illustrat the performance of our cryptosystem in those situations, we applied it to the following scenarios:
-
1.
Attack in the transmission channel, where we applied occlusion attack to the encrypted images.
-
2.
Noise in the transmission channel, in this scenario we add noise to the encrypted images.
5.7.1 Occlusion attack scenario
In the communications channels, lossing some parts of the transmitted (i. e. the encrypted) image can occur, so in this section we test our proposed cryptosystem to show it reaction under an occlusion attack. To show the strength of proposed cryptosystem we remove 1/16, 1/8, 1/4 and 1/2 part respectively of the encrypted image Fig. 4d is removed as shown in Fig. 7a-d and resultant the decrypted images shown in Fig. 7e-h.
The PSNR, MSE, NPCR and UCI scores are listed for the lossy decrypted images in Table 16. The scores are far better than [5, 39, 40].
5.7.2 Noise addition scenario
In order to show the robustness of our proposed cryptosystem on a noisy envirement, we take for example Fig. 4f and we contaminaed it by the Salt & Pepper noise where the noise density is 0.005, 0.05 and 0.5 which resulting the images in Fig. 8a-c, with their corresponding decrypted images are displayed in Fig. 8d-f. With a similar way, the Gaussian noise with a zero mean and a noise variances of 0.002, 0.05 and 0.3 is add to Fig. 4f resultant the images shown in Fig. 9a-c and the corresponding decrypted images are displayed in Fig. 9a-f.
The noisy encrypted images are decrypted and scores of NPCR, UACI and PSNR are computed and compared with [39, 40, 45] shown in Tables 17 and 18. It clear that the PSNR, NPCR and UACI scores obtain by using our propsed cryptosystem are far better than the others cryptosystems.
To further investigate the robustness to resist the transmission noise, In a similarty, we perform on Fig. 4e the same scenario as for Fig. 4f, the only difference in this case we change the noise parameters, where the densities of Salt & Pepper noise is choosen as 0.01, 0.05, 0.1 and 0.25, and the Gaussian noise the variances is set as 0.0001, 0.0003 and 0.0005. The results are shown in Tables 19 and 20 which clearly shows that the proposed cryptosystem has better results than [5, 26, 40].
6 Conclusions
In this paper, a master-slave synchronization scheme using a static error feedback for fractional-order hyperchaotic systems have been studied for a known time delay existing in the master-slave configuration. The delay-dependent criterion been given based upon a Lyapunov function. The criterion have been applied to fractional-order hyperchaotic Liu systems. The simulation results show that the proposed synchronization scheme gives good performance in the presence of time delay in the outputs of the systems. Further, we implement the synchronized systems into a new cryptosystem for image encryption and decryption. Several performance tests are done such as key space and key sensitivity analysis, pixels randomness valuation and pixel modification based measurement and a comparison with other cryptosystems show that the proposed cryptosystem is stronger than the usual cryptosystem due to the hardness of an additional securities derived from the fractional order derivativess and has a good security performence. In addition, one can observe the hight performance of the proposed cryptosystem on occlusion attack and noise addition applied to the encrypted images. The obtained results show good resistance in those scenarios.
References
Behnia S, Akhshani A, Mahmodi H, Akhavan A (2008) A novel algorithm for image encryption based on mixture of chaotic maps. Chaos Solitons Fractals 35:408–419
Biham E, Shamir A (1991) Differential cryptanalysis of DES-like cryptosystems. J Cryptol 4:36–72
Biham E, Shamir A (1993) Differential cryptanalysis of the full 16-round DES BT - advances in cryptology – CRYPTO.’ 92. In: Brickell EF (ed) 12th annual international cryptology conference santa barbara, California, USA August 16–20, 1992 Proceedings, Springer Berlin Heidelberg, Berlin, Heidelberg pp 487–496
Bowong S (2004) Stability analysis for the synchronization of chaotic systems with different order: application to secure communications. Phys Lett A 326:102–113
Chai X, Chen Y, Broyde L (2017) A novel chaos-based image encryption algorithm using DNA sequence operations. Opt Lasers Eng 88:197–213
Chapaneri S, Chapaneri R, Sarode T (2014) Evaluation of chaotic map lattice systems for image encryption. In: Proceedings of international conference on circuits, systems, communication and information technology applications (CSCITA) pp 59–62
Chen C, Feng G, Guan X (2004) Robust synchronization of chaotic Lur’e systems via delayed feedback control. Phys Lett A 321:344–354
Chen HF, Liu JM (2000) Open-loop chaotic synchronization of injection-locked semiconductor lasers with Gigahertz range modulation. IEEE J Quant Electron 36:27–34
Chen F, Zhang W (2007) LMI Criteria for robust chaos synchronization of a class of chaotic systems. Nonlinear Anal 67:3384–3393
Diaconu AV, Costea A, Costea MA (2014) Color image scrambling technique based on transposition of pixels between RGB channels using knight’s moving rules and digital chaotic map. Mathematical Problems in Engineering. https://doi.org/10.1155/2014/932875
Enayatifar R, Sadaei HJ, Abdullah AH, Lee M, Isnin IF (2015) A novel chaotic based image encryption using a hybrid model of deoxyribonucleic acid and cellular automata. Opt Lasers Eng 71:33–41
Feng D, An H, Zhu H, Zhao Y (2019) The synchronization method for fractional-order hyperchaotic systems. Phys Lett A 383:1427–1434
Firdous A, ur Rehman A, Saad Missen MM (2019) A highly efficient color image encryption based on linear transformation using chaos theory and SHA-2. Multimed Tools Appl 78:24809–248352
Gan Z, Chai X, Han D, Chen TY (2019) A chaotic image encryption algorithm based on 3-D bit-plane permutation. Neural Comput Applic 31:7111–7130
Gu K (2000) An integral inequality in the stability problem of time-delay systems. In: Proceedings of the 39th IEEE conference on decision and control, Los Alamitos, CA pp 2805–2810
Han Q, Liu CX, Sun L, Zhu R (2013) A fractional order hyperchaotic system derived from a Liu system and its circuit realization. Chin Phys B 22:020502–02050
Hartley TT, Lorenzo CF, Qammer HK (1995) Chaos in a fractional order Chua’s system. IEEE Trans Circuits Syst I 42:485–490
Hegazi AS, Matouk AE (2011) Dynamical behaviors and synchronization in the fractional order hyperchaotic Chen system. Appl Math Lett 24:1938–1944
Hua Z, Jin F, Xu B, Huang H (2018) 2D logistic-sine-coupling map for image encryption. Signal Process 149:148–161
Huang X, Sun T, Li Y, Liang J (2014) A color image encryption algorithm based on a fractional-order hyperchaotic system. Entropy 17:28–38
Huang Y, Huang L, Wang Y, Peng Y, Yu F (2020) Shape Synchronization in Driver-Response of 4-D Chaotic System and Its Application in Image Encryption. IEEE Access 8:135308–135319
Kalpana J, Murali P (2015) An improved color image encryption based on multiple DNA sequence operations with DNA synthetic image and chaos. Opt - Int J Light Electron Opt 126:5703–5709
Khalil HK (1993) Nonlinear systems. Macmillan Publishing, Company NY
Kiani-B A, Fallahi K, Pariz N, Leung H (2009) A chaotic secure communication scheme using fractional chaotic systems based on an extended fractional Kalman filter. Commun Nonlinear Sci 14:63–79
Kilbas A, Srivastava H, Trujillo J (2006) Theory and applications of fractional differential equations. NorthHolland mathematics studies 204
Kulsoom A, Xiao D, ur-Rehman A, Abbas SA (2016) An efficient and noise resistive selective image encryption scheme for gray images based on chaotic maps and DNA complementary rules. Multimed Tools Appl 75:1–23
Li Z, Xu D (2204) A secure communication scheme using projective chaos synchronization. Chaos Soliton Fract 22:77–81
Liang Y, Liu G, Zhou N, Wu J (2015) Color image encryption combining a reality-preserving fractional dct with chaotic mapping in hsi space. Multimed Tools Appl 75:6605–6620
Liao X, Chen G (2003) SChaos synchronization of general Lur’e systems via time-delay feedback control. Int J Bifurc Chaos 13:207–213
Liu Y, Zhang J, Han D, Wu P, Sun Y, MY S (2020) A multidimensional chaotic image encryption algorithm based on the region of interest. Multimed Tools Appl 79:17669–17705
Liu S, Zhou X, Li X, Jiang W (2016) Asymptotical stability of Riemann–Liouville fractional nonlinear systems. Nonlinear Dyn 86:65–71
Muthukumar P, Balasubramaniam P (2013) Feedback synchronization of the fractional order reverse butterfly-shaped chaotic system and its application to digital cryptography. Nonlinear Dyn 74:1169–1181
Muthukumar P, Balasubramaniam P, Ratnavelu K (2017) A novel cascade encryption algorithm for digital images based on anti-synchronized fractional order dynamical systems. Multimed Tools Appl 76:23517–23538
Nana B, Woafo P, Domngang S (2009) Chaotic synchronization with experimental application to secure communications. Commun Nonlinear Sci 14:66–76
Odibat ZM (2010) Synchronization of chaotic fractional-order systems via linear control. Int J Bifurcat Chaos 20:81–97
Pak C, Huang L (2017) A new color image encryption using combination of the 1D chaotic map. Signal Process 138:129–137
Podlubny I (1999) Fractional differential equations. Academic Press, New York
Smaoui N, Karouma A, Zribi M (2011) Secure communications based on the synchronization of the hyperchaotic Chen and the unified chaotic systems. Commun Nonlinear Sci Numer Simul 16:79–93
ur Rehman A, Liao X (2019) A novel robust dual diffusion/confusion encryption technique for color image based on Chaos DNA and SHA-2. Multimed Tools Appl 78:2105–2133
ur Rehman A, Liao X, Ashraf R, Ullah S, Wang H (2018) A color image encryption technique using exclusive-OR with DNA complementary rules based on chaos theory and SHA-2. Int J Light Electron Opt 159:348–367
Vidhya R, Brindha M (2020) A novel dynamic chaotic image encryption using butterfly network topology based diffusion and decision based permutation. Multimed Tools Appl. https://doi.org/10.1007/s11042-020-09462-9
Wang X, Zhang H (2015) A color image encryption with heterogeneous bit-permutation and correlated chaos. Opt Commun 342:51–60
Wang X, Zhang H (2015) A color image encryption with heterogeneous bit-permutation and correlated chaos. Opt Commun 342:51–60
Wei X, Guo L, Zhang Q, Zhang J, Lian S (2012) A novel color image encryption algorithm based on DNA sequence operation and hyper-chaotic system. J Syst Softw 85:290–299
Wu X, Kan H, Kurths J (2015) A new color image encryption scheme based on DNA sequences and multiple improved 1D chaotic maps. Appl Soft Comput J 37:24–39
Wu X, Li Y, Kurths J (2015) A new color image encryption scheme using cml and a fractional-order chaotic system. PloS one. https://doi.org/10.1371/journal.pone.0119660
Xu Y, Wang H, LI Y, Pei B (2014) Image encryption based on synchronization of fractional chaotic systems. Commun Nonlinear Sci Numer Simulat 19:3735–3744
Xu Y, Wang H, Li Y, Pei B (2014) Image encryption based on synchronization of fractional chaotic systems. Commun Nonlinear Sci Numer Simulat 19:3735–3744
Yalçin ME, Suykens JAK, Vandewalle J (2001) Master-slave synchronization of Lur’e systems with time-delay. Int J Bifurc Chaos 11:1707–1722
Zhang W, Cao J, Wu R, Alsaadi FE, Alsaedi A (2019b) Lag projective synchronization of Fractional-Order delayed chaotic systems. J Franklin Inst 356:1522–1534
Zhang Q, Guo L, Wei X (2010) Image encryption using DNA addition combining with chaotic maps. Math Comput Model 52:2028–2035
Zhang YQ, Hao JL, Wang XY (2020) An efficient image encryption scheme based on S-Boxes and fractional-order differential Logistic map. IEEE Access 8:54175–54188
Zhang LM, Sun KH, Liu WH, He SB (2017) A novel color image encryption scheme using fractional-order hyperchaotic system and DNA sequence operations. Chin Phys B 26:100504
Zhang YQ, Wang XY (2014) A symmetric image encryption algorithm based on mixed linear-nonlinear coupled map lattice. Inf Sci 273:329–351
Zhang H, Ye R, Liu S, Cao J, Alsaedi A, Li X (2018) LMI-based approach to stability analysis for fractional-order neural networks with discrete and distributed delays. Int J Syst Sci 49:537–545
Zhou NR, Wang YX, Gong LH, He H, Wu JH (2011) Novel single–channel color image encryption algorithm based on chaos and fractional Fourier transform. Opt Commun 12:89–96
Zhu C (2012) A novel image encryption scheme based on improved hyperchaotic sequences. Opt Commun 285:29–37
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Bouridah, M.S., Bouden, T. & Yalçin, M.E. Delayed outputs fractional-order hyperchaotic systems synchronization for images encryption. Multimed Tools Appl 80, 14723–14752 (2021). https://doi.org/10.1007/s11042-020-10425-3
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-020-10425-3