Abstract
The security of digital data has been attending more than past, spatially image data security. In this study, a hybrid image encryption method has been proposed based on genetic algorithm and chaos. Encryption process consists of three main steps: confusion phase, diffusion phase, and improvement phase using a genetic algorithm. At first, Chen’s chaotic map is used in the confusion phase to generate a scrambled image by shuffling plain-image pixels, and in the diffusion step, Logistic-Sine map alters those pixels gray-level values. It produces some of encrypted images which were considered as the initial population for the genetic algorithm. Then, by using the genetic algorithm, the encrypted images are optimized as much as possible. Finally, the best encrypted image is the final cipher image. The experimental results and several security analyses show that the proposed modified method provides an efficient scheme for image encryption and good robustness against frequent statistical and security attacks.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Nowadays, with the rapid development in digital technology and communication networks, digital data and information are store and transmit more and more, over the networks. Thus, developing techniques for maintaining the security of storing and transmitting digital data has been more and more interested. Digital images and videos carrying a large amount of essential information for many applications, thus image data protection against unauthorized users has become an important issue for searches [19, 20]. One of the methods of protecting information is to use encryption algorithms. By image encryption techniques, the original image converted to an encrypted image that is not easy to understand.
On one hand, different kinds of image encryption methods based on different technologies have been presenting that, among them, chaos-based techniques are more interested in recent years. The chaotic encryption was characterized by high sensitivity to initial situations and parameters, pseudo-random behavior, non-periodicity, the simplicity of implementation in hardware & software, and mixing property. Therefore, it is widely attractive to image encryption [8, 18, 21, 37]. On the other hand, one of the most frequently used optimization algorithms is a genetic algorithm (GA), and it also has some applications in cryptography fields. To traverse the solution search space, GA uses selection, crossover, and mutation operators inspired by evolutionary biology. In this algorithm, each solution encoded as a string called a chromosome. The algorithm starts by initializing a population with random or default values. For the first time, Abdullah et al. [1] proposed an encryption method based on a hybrid genetic algorithm and chaotic function. They used the chaotic logistic map function to encrypt images and produce several encrypted images as the initial population for genetic algorithms. Then, by using the genetic algorithms, these encrypted images are optimized to choose the final encrypted image as the best cipher image with the low correlation coefficient between pixels and high entropy. In this study, a hybrid GA and chaos-based image encryption method proposed. In the proposed scheme, the encryption process includes three main confusion phases, diffusion phase, and applying the GA algorithm for improvement.
A list of abbreviations and acronyms used throughout the paper was given in Table 1. The rest of this paper was organized as follows. The preliminary and related work are described in sections 2 and 3, respectively. Section 4 describes the proposed method, and section 5 gives the simulation results and analysis. Finally, the paper concluded in section 6.
2 Preliminary
Here, we briefly describe chaotic systems like Chen and Logistic-Sine chaotic map and genetic algorithms, which are the basic components of the most chaotic based encryption methods as well as our proposed method.
2.1 Chaotic maps
Chaotic maps are subtypes of non-linear dynamical systems that are similar to the noise signal but very certain. The chaotic map employed to produce disordered sequence [15]. High sensitivity to initial value is one of the important characters of these systems. It means if a little change was made in the primary value, a sharp change can happen in the result, so this main characteristic becomes this system’s robustness, effectiveness, and non-predictable that makes these suitable for encryption applications [8, 17, 31]. The Chaotic system was explained as follows:
Where X0 is the initial value, and the output is a sequence of n numbers between 0 and 1. The f system called the chaotic system when it is non-linear, deterministic, susceptible to initial situations, irregularity, and non- predictable.
2.2 Chen chaotic system
Chen system is a hyper chaotic system, and because of sophisticated mathematical equations and sequences generated by this system are randomized, and their prediction is difficult. The complexity and the large key space of hyper chaotic systems is the reason why these systems have higher resistance against all types of attacks [26]. The hyper chaotic Chen system is defined as follows:
Where a, b, and c are control parameters of the system. In the case of a = 35, b = 3, and c = 28, the system behaves as a chaotic system [13, 23], and gives three random sequences by repeating the Chen system, as shown in Fig. 1.
2.3 Logistic-sine chaotic system
Logistic-Sine (LS) system is a nonlinear mixture of two different 1D chaotic Logistic and Sine systems [37]. The 1D chaotic systems like Logistic Sine, and Tent map have a lot of applications due to their natural structures. Still, they have some difficulties consist of the restricted range of chaotic behaviors or discontinuous range of these, the vulnerability to low-computation-cost analysis, and the non-uniform distribution of data [2, 34, 37]. The combined LS system solves the above problems and has excellent chaotic properties like a wide range of parameters and uniform distribution of data [37]. Figure 2 illustrated the combination of Logistic and Sine chaotic systems.
Where L(r, Xn),and S((4 − r), Xn) are Logistic and Sine chaotic systems with parameter r ∈ (0, 4], respectively, and Xn is the chaotic output sequence. Also, n is the iteration number, and mod is modulo operation that assures its output in [0,1]. LS system was described by the following equation [37]:
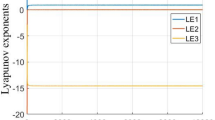
Compared with its corresponding maps, Logistic, and Sine, LS has more complex, chaotic properties. When one of its maps is out of the chaotic range, this chaotic system can still have chaotic behaviors. The bifurcation diagram and Lyapunov Exponent of Logistic and LS systems are illustrated in Figs. 3 and 4, respectively. In the Logistic system, if r ∈ (0,3.57) the system has non-chaotic behavior and its chaotic behavior is restricted only within [3.57,4] where the chaotic behavior of the LS system exists within the whole range of (0,4] [37]. The Lyapunov exponent acts as an indicator to measure the chaotic behavior of systems [14]. As illustrated in Fig. 4, the LS Lyapunov exponent closes to 0.7 in range r ∈ (0, 4].
2.4 Genetic algorithm
One of the best algorithms used to solve a wide variety of optimization problems is the Genetic Algorithm (GA). The GA is a heuristic search algorithm inspired by Darwin’s theory of evolution. This algorithm shows the natural selection procedure in which the right individuals are selected for reproduction to produce offspring. GA acts on a population of some solutions where the population size is the number of solutions. Each solution is called an individual solution. Every single one of these individual solutions has a chromosome. The chromosome has been presented as a set of parameters that characterize the individual. Each chromosome has a set of genes. Each gene is as a string of 1 s and 0 s as illustrated in Fig. 5.
Besides, every individual has a fitness value. A fitness function used to select the best individuals. The result of the fitness function is the fitness value that represents the solution quality. The higher the amount of fitness, the higher the solution quality. Choosing the best individuals based on their quality is used to produce what is called the mating pool, where the higher quality individual is more likely to be chosen in the mating pool. The individuals in the mating pool are called parents. Every two parents selected from the mating pool will generate two offspring. By just mating high-quality individuals, it was expected to get a better-quality offspring than its parents. So, this will kill the corrupt individuals from making more corrupt individuals. By keeping selecting and mating high-quality individuals, there will be higher chances just to keep good properties of the individuals and leave out bad ones. Finally, this will end up with the desired optimal or acceptable solution. Individuals in the mating pool are called parents. Both parents from the mating pool produce two children. Only by pairing high-quality individuals are they expected to have better quality offspring than their parents. So, this causes corrupt individuals eliminated by producing more bad individuals. By keeping the selection and mating of high-quality individuals, you are more likely just to maintain the good qualities of the individuals and avoid the bad ones. Finally, it ends with the desired or desirable solution.
Offspring that were currently produced by using selected parents only have the characteristics of their parents, and there is no change in them anymore. Nothing new added to it, and so there will be the same parenting bugs in the new offspring. Changes will be made for each offspring to create new individuals in order to fix this problem. All the newly created individuals will be a new population, replacing the old population used previously. Any population created is called generation. The process of replacing the old population with the new population is called replacement. Figure 6 summarizes the GA steps.
3 Related work
Many data encryption methods use chaotic maps [1,2,3, 7, 12, 22, 27, 28, 31, 33] because it is widely applicable and easy to understand. Chaotic based image encryption occurs in two steps, confusion, and diffusion. In the confusion step, an image’s pixels scrambled using a secret key based upon control parameters. While in the diffusion step. While in the diffusion stage, the pixel values changed using the sequence generated by the chaos. Both methods make chaos encryption very secure [9]. The core of a chaos-based cryptosystem is the chaotic map, one-dimensional (1D), and high-dimensional (HD) are two types of chaotic map that 1D chaotic map has fewer parameters and variables, and simpler phase space trajectory rather than HD chaotic map [21].
In 1998, Fredrick proposes the first chaos-based permutation-diffusion algorithm for image encryption [11]. He used a 2D chaotic map to shuffle pixels of plain-image, and next by exploiting a 1D chaotic function, these pixels gray-level are altered sequentially [18]. After that, many chaos-based encryption methods introduced according to his scheme [32]. However, different researchers use different chaos systems. The analysis shows that each algorithm has its own strengths and weaknesses in terms of security and efficiency. The essential problems of these algorithms relate to three aspects: chaos system selection, cryptographic architecture selection, and cryptographic implementation [12].
Chaos systems are used as the backbone of cryptographic systems so that their complex behavior depends on control parameters and initial conditions. The chaotic system selection must be such that it can guarantee chaotic behavior for all values of control parameters. If this is not the case, the codes associated with the dynamic system will no longer be secure. Confusion and diffusion features that reflect security are directly related to the probability distribution function of the underlying chaos system. Hence a chaotic map with a uniform probability distribution function is the best choice to prevent information leakage from an encryption system.
For example, Pareek et al. [28], proposed an image encryption approach based on the logistic map, they employed an 80-bit secret key and two chaotic logistic maps in their method. This external secret key provided the initial situations for logistic maps by applying variant weightage to all bits. Another plaintext-dependent image encryption algorithm introduced in [29]. They employed the logistic map for encryption gray-scale images. The original image was partitioned into blocks and then, by XOR operation and chaotic windows, encrypted. They used 1D logistic chaotic map in their algorithm. However, that is efficient and simple but has a small key space, so they used the chaotic logistic map several times in their algorithm to overcome this drawback. To do parallel processing, they used two 16 × 16 chaotic blocks. Hua and Zhou [14] proposed a 2D Logistic-adjusted-Sine map (2D-LASM), in which the logistic map used to tune the sine map input, and; afterwards its phase plane extended to 2D [14]. Hua et al. [15] proposed a 2D chaotic map called Logistic-modulated-sine-coupling-logistic chaotic map (LSMCL). they exploit logistic map to modulate sine map and couple logistic and sine map together. In addition, an image encryption method based on the chaotic improved logistic system (ILS) proposed in [3]. In [16], a method for data stream encryption presented using a genetic algorithm and pseudo-random sequence. Zhang et al. employ a hyper chaotic Chen system for image encryption [35]. Chai et al. [6] proposed an image encryption technique using a 2D logistic chaotic map and DNA sequence operations. In [36], to improve the security and robustness of existing image encryption algorithms and decrease the security risks of encryption algorithms against most of the attacks, authors presented an image encryption algorithm based on image augmentation, chaos, and DNA coding.
Nepomuceno et al. [25] use natural interval extensions and the lower bound error to generate a random sequence based on the pseudo-orbits of the 1D logistic map. Their proposed method produces a large key space, which can be easily increase. Therefore, it is more important to choose a proper chaos system than to design an encryption algorithm. No matter how good and how strong the cryptographic system designed, the cipher can easily break if the poor chaos system had selected [12].
In another view, one of the major limitations when running chaotic systems on digital devices is their numerical precision. in fact, after a certain number of iterations, the generator may indicate a certain degree of periodicity or digital chaos destruction. So, these limits the digital chaos encryption effect to large amounts of information, such as high-resolution images. Although most chaos-based encryption algorithms report good statistical properties, they are slow to execute due to their inherent dependence on the data of the proposed programs. Some of these methods designed to using sophisticated chaos systems that require significant computational resources. Technology is constantly evolving with significant advances, including multi-core processors, which is why new threats and vulnerabilities devised that endanger security information in communications systems. Therefore, some researchers used parallel computing to increase security and speedup of the encryption process [5, 10, 30]. For example, Song et al. exploited the multi-threading technique in which every thread competes with others to encrypt images. They used the logistic map and Lorenz system for generating keystream for permutation and diffusion, respectively.
4 The proposed encryption scheme
The proposed method includes three main steps: confusion, diffusion, and optimization step by the GA. In the first phase, a scrambled image will be generated by using Chen map function and moving all of the pixels of the original image. In the next phase, intensity valves of pixels will be changed by LS map function, and the initial population for GA will be generate. In the last phase, correlation coefficient between pixels will be calculated by using the genetic algorithm, the best cipher will be select.
4.1 Confusion phase
A suitable encryption system has to be susceptible to encryption keys, and good key space is large enough to have the best strength against any kind of attack [37]. In hyper-chaotic functions, space keys are very large, so they have most security against attacks. The proposed algorithm, we used hyper-chaotic Chen function that is one of the hyper-chaotic systems, which is explained by Eq. 2.
We set system parameters as a = 35, b = 3, and c = 28. The primary values are X0, Y0 and Z0 that consider as systems-keys. We set these initial values as X0 = − 9, Y0 = − 5, Z0 = 14.
The confusion phase consists of the following steps:
-
Step 1.
Take the plain image as input.
-
Step 2.
Change the 2D original image I (M × N) to 1D array A of length L = M × N.
-
Step 3.
Generating three random sequences Xn, Yn,Zn by using Chen-chaotic function.
-
Step 4.
One of three above random sequences is selected and arranged low to high as 1D array W.
-
Step 5.
Indexes of array W saved in new array D.
-
Step 6.
All Pixels of 1D array A moved according to elements of D.
-
Step 7.
Reshape 2D-image I of size M × N from 1D array A and generate a scramble image as presented in Fig. 7.
4.2 Diffusion phase
The LS chaotic map is a nonlinear mixture of two different Logistic map, and Sine map [37]. The Logistic map has an analogous chaotic behavior with the Sine map. So, both of them have problems that by combining them, a system with more complex chaotic properties generated. One of the Logistic chaotic map problems is its limited chaotic range within [3.57, 4] which, in LS map solved. The LS map has a wider chaotic range within (0,4], as shown in Fig. 4(b). Also, the chaotic sequences range in the Logistic map is non-uniform distribution in [0,1], but the LS map sequences have a uniform-distribution within [0,1], as shown in Fig. 4(a).
In the proposed method, we used the LS map that explained in Eq. (3) to change intensity valves of scramble Image’s pixels from confusion phase by following these steps:
-
Step 1.
Split the scrambled 2Dimage with size 512 × 512 to four 256 × 256 blocks, as shown in Fig. 8.
-
Step 2.
Employ the LS function to encrypt all pixels in each block as follow:
-
A.
In each block, the first five pixels are selected as the encryption key for forming the initial value.
-
B.
Each of these initial values is an eight-bit block that is converted into decimal numbers and reserved in array B with size 40 by using the following equation:
-
C.
apply the LS function (Eq.3) on above initial values as follows:
Where r1 and r2 are random numbers in (0, 4].
-
Step 3.
Step2 must repeated 256 times, and then the initial population of the genetic algorithm with 256 members (512 × 512) will be obtained.
4.3 Optimization phase using genetic algorithm
In the proposed method, we used GA to optimize and selecting the best-encrypted images by the below steps. The initial population for GA formed in previous phases after employing LS function.
-
Step 1.
The correlation coefficient between the next pixels of the encrypted image considered as the fitness function that will be calculate in each stage. The horizontal, vertical, and diagonal correlation coefficients between two next pixels can be obtain by Eq.6 [7, 8, 37].
-
Step 2.
The master population made by choosing 10 % of the population with the minimum correlation.
-
Step 3.
Use the rest population and the crossover operation for generating new generations and select the best from by evaluated fitness function. The best generated with the minimum correlation coefficient was chosen.
-
Step 4.
Steps 1 to 3 will be repeated 100 times to generated new generations and select the best-encrypted images. Finally, the best-encrypted image with the minimum correlation coefficient will be select as the cipher image. The process of this approach illustrated in Fig. 9.
5 Simulation results and analysis
The results of validating the proposed method’s efficiency described in this section. Input images are gray scale with dimension 512 × 512. Some experiments performed to Image evaluation, and their results shown. Finally, we compared the proposed encryption method with some recent methods [1, 8, 21, 27, 29] in term of some security measures defined in Table 2.
5.1 Statistical analysis
5.1.1 Histogram analysis
The histogram is one of the most statistical characteristics that shows the distribution of gray pixels of an image [22, 26]. The histogram of the plain image is regular, and the attackers can extract some information. The histogram of the cipher image of a suitable encryption approach should be uniform [6]. In fact, a beneficial image encryption method must generate a uniformly distributed histogram for the cipher images [22]. In Fig. 10, the outputs of our method for some images and their histogram illustrated. As shown in Fig. 8, all encrypted images have a uniform histogram. Thus, the attacker is not able to extract any information about gray values from the encrypted image, so the proposed method is strength against statistical assaults.
5.1.2 Correlation analysis
The correlation coefficient is also an important characteristic in the image encryption area, which is defined by the correlation between two adjacent pixels in an image [8]. In an ordinary image, the values of adjacent pixels are close, so its correlation coefficients are always high [4, 7]. A strength image encryption algorithm should generate cipher images with low correlation among adjacent pixels in three directions as far as possible [1, 8, 37].
The correlation coefficient in horizontal, vertical, and diagonal directions can be obtain by the following Eq.6 [7, 8, 37].
Here, x and y are gray values of two next pixels, and N is the total number of pairs of vertically, horizontally, or diagonally neighbor pixels of the image [4, 7]. The proposed approach and Table 3 have encrypted some sample plain images in 512 × 512 presents the correlation coefficients of these images and their corresponding encrypted images.
As shown in Table 3, two neighbor pixels of plain images are highly correlated (close to 1), where the neighbor pixels in ciphers have low correlation (close to 0). Also, Fig. 11 illustrates the correlation coefficient of neighbor pixels in the Lena image and its cipher, respectively. As a result, the correlations of adjacent pixels of encrypted images generated by the proposed encryption approach in all directions are approximately equal to zero. Thus, this proposed method has good efficiency in image encryption and is secure against statistical attacks.
(a) The plain Lena image- (b) distributions of two horizontally neighboring pixels- (c) distributions of two vertically neighbor pixels- (d) distributions of two diagonally neighbor pixels; (e) the cipher image of Lena- (f) distributions of two horizontally neighboring pixels- (g) distributions of two vertically neighbor pixels- (h) distributions of two diagonally neighboring pixels
5.1.3 Information entropy analysis
The entropy has been used for defining the level of randomness in an image. [1, 21]. Calculating the entropy of a message with 2 M symbols was introduced by the following equation.
Where M is the number of bits which is need to indicate the symbol Si (M for gray level images is 8), and P(Si) represents the probability of the existence of symbol Si in the image [1, 33]. In 8-bit gray-scale images, all of the pixels are distributed randomly and has 256 symbols. The probability of each symbol is 1/256, and the entropy is equal with eight. So in an ideal encryption system with the distributed histogram of output, the entropy of cipher images should be equal to eight [37]. Table 4 shows the entropy of specific gray encrypted pictures generated by our proposed scheme.
5.2 Differential attacks
The sensitivity of cipher image to the slight changes (even one bit), in the plain image, is an important feature in image encryption. In other words, by changing even one bit in plain image, the cipher image must be changed. By comparing the encrypted images of the original image and the modified original image, the sensation of changing a single pixel of the original image can be measured. NPCR and UACI are two criteria for measuring this property. The Number of Pixels Change Rate (NPCR) and Unified Average Changing Intensity (UACI) calculated by Eqs. 11–13.
Here, M and N are sizes of the image, C1, and C2 are corresponding cipher images of the original images that have one different pixel. First, the clear image is encrypted. Afterward, one pixel of the original image is modified, and then it is encrypted. The calculated NPCR and UACI between two obtained cipher images were shown in Table 5. Figure 12. shows the cipher images of the original image Ruler.512 and its modified image that have only one different pixel with it. The optimal values of these parameters are NPCR and UACI are 0.9961, and 0.3346, respectively.
5.3 Key analysis
Key space and key sensitivity analysis, play main roles to strength against brute-force attack.
5.3.1 Key space analysis
The encryption algorithm has to have a large key space in order to resist brute-force attacks. In fact, a brute-force attack has made by seeking all possible keys to obtain the real key. We used three initial values X0, Y0, Z0, and two parameters r1and r2 in our algorithm. The precision of the initial values and parameters was 10−14 in our analysis. Therefore, the key space of the proposed algorithm could be calculated as: (1014)3 × (1014)2 = (10)70 ≅ 2224, so the key space is large enough.
5.3.2 Key sensitivity analysis
Another important feature in the encryption algorithm is the sensitivity to small changes in keys. In other word, the encryption algorithm must have a large key space to resist brute-force attacks and must be sensitive to any change of its keys. As it was mentioned in section 4, keys of our algorithm consist of two parameters (r1 and r2) where r1 and r2 are in the range of (0, 4]. For key sensitivity, a primary key set (k1) is r1 = 3.99 and r2 = 3.79. We use k1 to encrypt plain image of Barbara to obtain the encrypted image defined as E1. Then we generated another key set (K2) by changed r1 to 3.99000000000001 while keeping others unchanged. Using kj2 to encrypt the Barbara image again and generated another encrypted image (E2). Table 6 shows the result of evaluating the difference between these two encrypted images (E1, E2). The proposed algorithm is highly sensitive to changing key value, even a small change (10−14) in the key value. In the decryption process, we used k1 to encrypt the Barbara image and then used k2 to decrypt the encrypted image. Figure 13 shows the decrypted results. As we can see, by using the correct key (k1), the decryption process works correctly and reconstruct the original image completely. However, the decryption process will fail by a small change in key value. Table 7 shows the NPCR and UACI results by changing keys. Hence, the proposed algorithm is very sensitive to the key value in encryption and decryption processes.
The Peak Signal to Noise Ratio (PSNR) is utilized to measure the discrepancy between plain image P and decrypted image D [15]. For good decrypted image, the discrepancy between the plain image and the decrypted image must be low and the value of PSNR must be high. PSNR is defined by Eq.14:
The Mean Square Error (MSE) is the difference between the plain image and the decrypted image. For a good performance, this difference must be very low. MSE is evaluated by Eq.15:
Where pm(i, j) and pd(i, j) is the grey-scale values of the pixels of plain and decrypted images with M × N size, respectively. For a good encrypting method, the discrepancy between the plain image and the decrypted image is very low, so MSE is low, and PSNR will be high.
Table 8 shows the comparison of the proposed approach with several recently related approaches, which states our algorithm efficiency in terms of statistical analysis. According to this table, all methods are acceptable, and among these comparable methods, there is no one works best on all criteria for all the images tested. The proposed method performs better than others in terms of entropy and correlation in most cases. However, the fitness function definition is an essential step in the proposed method, and the other parameters can also be improved by more precisely defining a combined fitness function for the optimization algorithm.
5.4 Noise attack and data loss
When an image transmitted in the real physical world, the data might have noised or lost. Therefore, a great design encrypted image algorithm should be robust against noise and loss data and recover the original image without missing too much critical information [15, 22, 27].
We tested our algorithm against salt-pepper noise by appending this noise to the encrypted image and then decrypting it again. PSNR results for Lena plain image with salt-pepper noise illustrated in Table 9. Figure 14 shows our algorithm has good robustness against noise as well as other methods.
The results of the salt-peppers attack. (a), (b) adding noise with d = 0.001 and the resulting decrypted image, (c), (d) adding noise with d = 0.01 and the resulting decrypted image, (e), (f) adding noise with d = 0.05 and the resulting decrypted image, (g), (h) adding noise with d = 0.1 and the resulting decrypted image
To test the effect of data loss in the proposed algorithm, first, the plain image was encrypted, then we replaced a 50 × 50-pixel partition of the encrypted image with zero value. So, the modified encrypted image was decrypted by our algorithm. The results of the data loss attack illustrated in Fig. 15. As can be seen, even by losing 50% of the pixels, we are still able to get a sharp decrypted differentiable image. Therefore, our algorithm is tight against the data loss attack.
6 Conclusions
In this paper, an improved gray scale image encryption algorithm based on chaotic systems presented.
The chaotic systems like Logistic, Sine, and Tent map have a lot of applications due to their natural structures, but they have some difficulties. The combined LS system solves above problems and has good chaotic properties like a wide range of parameters and uniform distribution of data. By using this combination, different chaotic systems can be found.
3In this schema, three disordered functions in confusion, and diffusion phases were employed for encryption and reducing the coefficient of correlation between pixels, and also to increase the security level of encryption system as well as possible. Then by using genetic algorithm, the encryption process is improved, and the best cipher images selected while the correlation coefficient among pixels in three vertical, horizontal and diagonal directions was closed to zero. As we are using two chaotic systems, the proposed algorithm has a large and secure key space. Also, this algorithm makes uniformly distributed histograms for cipher images. Thus, the attacker is not able to get any information about gray level values distribution from the encrypted image, and hence the proposed method is resistant against statistical attacks. The decryption system is susceptible to key, and if there is a small change in key, the output of the decryption system has a distributed histogram and will be like a noise.
In the future, we can exploit chaotic quantum systems and hyper-chaos as well as the significant effect of coupling and modulation to design more complex encryption algorithms with different simple quantum chaotic systems to enhance the encryption process. Also, other heuristic optimization algorithms such as particle swarm optimization (PSO), Black Widow Optimization (BWO), Barnacles Mating Optimizer (BMO) algorithms instead of GA. It is obvious that a particular chaos function is not suitable for all types of images. So, one can use some machine learning techniques to choose a proper chaotic function corresponding to the input image to improve the encryption process.
References
Abdullah AH, Enayatifar R, Lee M (2012) A hybrid genetic algorithm and chaotic function model for image encryption. AEU-Int J Electron Commun 66(10):806–816
Arroyo D, Diaz J, Rodriguez FB (2013) Cryptanalysis of a one round chaos-based substitution permutation network. Signal Process 93(5):1358–1364
Attaullah ST, Jamal SS (2020) An improved chaotic cryptosystem for image encryption and digital watermarking. Wirel Pers Commun 110(3):1429–1442
Belazi A, El-Latif AAA, Diaconu A-V, Rhouma R, Belghith S (2017) Chaos-based partial image encryption scheme based on linear fractional and lifting wavelet transforms. Opt Lasers Eng 88:37–50
Çavuşoğlu Ü, Kaçar S (2019) A novel parallel image encryption algorithm based on chaos. Clust Comput 22(4):1211–1223
Chai X, Chen Y, Broyde L (2017) A novel chaos-based image encryption algorithm using DNA sequence operations. Opt Lasers Eng 88:197–213
Enayatifar R, Abdullah AH, Isnin IF (2014) Chaos-based image encryption using a hybrid genetic algorithm and a DNA sequence. Opt Lasers Eng 56:83–93
Enayatifar R, Abdullah AH, Isnin IF, Altameem A, Lee M (2017) Image encryption using a synchronous permutation-diffusion technique. Opt Lasers Eng 90:146–154
Fadhel S, Shafry M, Farook O (2017) Chaos image encryption methods: a survey study. Bullet Electric Eng Inform 6(1):99–104
Flores-Vergara A, Inzunza-González E, García-Guerrero EE, López-Bonilla OR, Rodríguez-Orozco E, Hernández-Ontiveros JM, Cárdenas-Valdez J, Tlelo-Cuautle E (2019) Implementing a chaotic cryptosystem by performing parallel computing on embedded systems with multiprocessors. Entropy 21(3):268
Fridrich J (1998) Symmetric ciphers based on two-dimensional chaotic maps. Int J Bifurcat Chaos 8(06):1259–1284
Gayathri J, Subashini S (2016) A survey on security and efficiency issues in chaotic image encryption. Int J Inf Comput Secur 8(4):347–381
Hu H, Liu L, Ding N (2013) Pseudorandom sequence generator based on the Chen chaotic system. Comput Phys Commun 184(3):765–768
Hua Z, Zhou Y (2016) Image encryption using 2D logistic-adjusted-sine map. Inf Sci 339:237–253
Hua Z, Jin F, Xu B, Huang H (2018) 2D logistic-sine-coupling map for image encryption. Signal Process 149:148–161
Kumari A, Goyal S (2016) Encryption and Code Breaking of Image Using Genetic Algorithm in MATLAB. Int J 4(7)
Li J, Liu H (2013) Colour image encryption based on advanced encryption standard algorithm with two-dimensional chaotic map. IET Inf Secur 7(4):265–270
Li C, Luo G, Qin K, Li C (2017) An image encryption scheme based on chaotic tent map. Nonlinear Dynamics 87(1):127–133
Liao X, Qin Z, Ding L (2017) Data embedding in digital images using critical functions. Signal Process Image Commun 58:146–156
Liao X, Yu Y, Li B, Li Z, Qin Z (2019) A new payload partition strategy in color image steganography. IEEE Trans Circ Syst Vid Technol
Liu W, Sun K, Zhu C (2016) A fast image encryption algorithm based on chaotic map. Opt Lasers Eng 84:26–36
Liu Y, Wang J, Fan J, Gong L (2016) Image encryption algorithm based on chaotic system and dynamic S-boxes composed of DNA sequences. Multimed Tools Appl 75(8):4363–4382
Lü J, Chen G (2002) A new chaotic attractor coined. Int J Bifurc Chaos 12(03):659–661
Mozaffari S (2018) Parallel image encryption with bitplane decomposition and genetic algorithm. Multimed Tools Appl 77(19):25799–25819
Nepomuceno EG, Nardo LG, Arias-Garcia J, Butusov DN, Tutueva A (2019) Image encryption based on the pseudo-orbits from 1D chaotic map. Chaos: An Interdiscip J Nonlin Sci 29(6):061101
Niyat AY, Moattar MH, Torshiz MN (2017) Color image encryption based on hybrid hyper-chaotic system and cellular automata. Opt Lasers Eng 90:225–237
Noshadian S, Ebrahimzade A, Kazemitabar SJ (2018) Optimizing chaos based image encryption. Multimed Tools Appl:1–22
Pareek NK, Patidar V, Sud KK (2006) Image encryption using chaotic logistic map. Image Vis Comput 24(9):926–934
Rostami MJ, Shahba A, Saryazdi S, Nezamabadi-Pour H (2017) A novel parallel image encryption with chaotic windows based on logistic map. Comput Elect Eng
Song W, Zheng Y, Fu C, Shan P (2020) A Novel Batch Image Encryption Algorithm Using Parallel Computing. Inform Sci
Takkar P, Singh V (2017) Image encryption approach using chaotic map for gray scale images
Tewani R, Garg Y, Bagga JS, Singh A, Bhalsodia R (2020) Image Encryption Using Permutation–Diffusion Approach. Advances in Data Sciences, Security and Applications: Springer 363–73
Xu L, Gou X, Li Z, Li J (2017) A novel chaotic image encryption algorithm using block scrambling and dynamic index based diffusion. Opt Lasers Eng 91:41–52
Ye G (2010) Image scrambling encryption algorithm of pixel bit based on chaos map. Pattern Recogn Lett 31(5):347–354
Zhang M, Peng B, Chen Y editors (2019) An Efficient Image Encryption Scheme for Industrial Internet-of-Things Devices. Proceedings of the 2nd International ACM Workshop on Security and Privacy for the Internet-of-Things
Zhang Q, Han J, Ye Y (2019) Image encryption algorithm based on image hashing, improved chaotic mapping and DNA coding. IET Image Process 13(14):2905–2915
Zhou Y, Bao L, Chen CP (2014) A new 1D chaotic system for image encryption. Signal Process 97:172–182
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Ghazvini, M., Mirzadi, M. & Parvar, N. A modified method for image encryption based on chaotic map and genetic algorithm. Multimed Tools Appl 79, 26927–26950 (2020). https://doi.org/10.1007/s11042-020-09058-3
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-020-09058-3