Abstract
In biometrics, picking of the right methodology is a testing errand for recognition of a person. Due to the advantage of widely accepted identification, face, and signature-based biometric modality are selected as a significant pattern as compared with other modalities. Different Face and signature successions of a similar subject may contain varieties in determination, light, pose, facial appearances and sign position. These varieties add to the difficulties in planning a viable multimodal-based face and signature recognition algorithm. This paper proposed about the face and signature recognition method from a large dataset with the different pose and multiple features. Face recognition is the first stage of a system then the signature verification will be done. Here, data glove signaling means of signing process are taken into account to do signature verification system. Hence the proposed work have used Face, and the corresponding signature is detected from data glove signal patterns to features-level fusion for the verification system. The proposed Legion feature based verification method will be developed using four important steps like, i) Preprocessing, ii) feature extraction from face and data glove signals, iii) Legion feature based feature matching through Euclidean distance, iv) Legion feature Neural network (LFNN) fusion based on weighted summation formulae where two weights will be optimally found out using Legion optimization algorithm, vi) Recognition based on the final score. Finally, based on the feature library the face image and signature can be recognized. The comparability estimation is finished by utilizing least Euclidean separation fusion based LFNN to decide perceived and non-perceived images. Also, in a similar examination, a proposed strategy is compared with current technique by several performance metrics and the proposed LFNN technique efficiently recognize the face images and corresponding signature from the input databases than the existing technology.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Recognizable proof of people utilizing face and signature examination has been for quite a while a critical research point. Nowadays advancement has advanced to the detail that, example representations and substance can be seen in machine produced reports in a extensive assortment of models. Be that as it may, acknowledgment of people is harder to accomplish. The need to automate human confirmation has as of late turned out to be increasingly evident. A reliable person recognizable proof framework would empower financial and bank organizations to the check and money order forgeries are fundamental lessen, A critical monetary misfortune was represent in every year.
The safety efforts was fundamentally enhanced, the framework can likewise be utilized to suit individuals who have lost their IDS amid disasters (e.g., tremor). Likely the most imperative feature of a biometric is its capacity to gather the signature from noncooperating subjects. Other than applications identified with distinguishing proof and confirmation, for example, access to control, law implementation, ID and permitting, observation, and so on., face recognition is additionally helpful in human-PC cooperation, virtual reality, database recovery, multimedia, computer entertainment, etc. The framework displayed in this paper can be utilized to take care of two distinct issues related to individual identification proof: check - it confirms whether a given signature and facial picture have a place with the a human whose signature and face characteristics are known early, acknowledgment - it searches for the character of a given subject (signature and face) through an energizing database.
Face Recognition is a noninvasive methodology where a bit of the subject’s face is captured, and the resulting picture is diminished to a computerized code. The assignment of face recognition quiet positions distinctive difficulties like the adjustment in lighting, posture, and pivoted faces regardless of achievement in some commercial frameworks. Facial recognition records the spatial geometry of recognizing highlights of the face. It is exceptionally testing to create face recognition strategies which can endure the impacts of maturing, facial appearances, slight varieties in the imaging condition and varieties in the pose of a face concerning the camera.
A signature register can be part with two orders: Static: In this mode, customers form their signature on paper, computerized it’s an optical scanner or comer, and a biometric structure sees the mark by analyzing its shape Dynamic: In this mode, customers create their mark on a digitizing tablet, shrewd pen, or pen tablet. Considering the most imperative security levels required by the online systems (dynamic), by far most of the endeavors of the experts in this field address this gathering.
To overcome the disadvantages and disappointments of regular strategies, we have proposed a successful strategy which can help in legitimate acknowledgment of the face and signature in our proposed framework. By incorporating at least two biometric techniques, these sorts of arrangements meet the most astounding and most stringent security requirements. Face and signature biometrics have a place with both physiological and behavioral classes. Additionally face and signature have the favorable position over different biometrics since it is a characteristic, nonintrusive, and simple to utilize biometrically. At long last, the likeness factor is looked at and the decision limit for recognized or expelled as confirmed or impersonation, independently.
This work has organized in five section. In section 1 discuss the introduction about the face and signature recognition. In section 2 describes the previous researches related to face and signature analysis. In section 3 describes the proposed materials and methods. Section 4 discuss the performance comparionsion and results of the projected method. Fincally the section 10 concluding the merits and demrits of the proposed system.
2 Literature review
Various research works have been done in the field of unimodal and multimodal biometric frameworks in the current years. A portion of the current examines in the field of unimodal and multimodal biometric systems are said underneath.
Recognizing objects from broad picture databases,histogram-based techniques have shown straightforwardness and helpfulness in 10 years prior. At initially, this musing depended on shading histograms that were in [18]. Following this idea different upgrades were made by unmistakable humans, abusing this idea, for instance, surface histograms for 2D challenge recognition suggested in [8], shape-record histograms for extending picture acknowledgment proposed and social histograms used in [6] for line-plan recognition. Thus, covering imperativeness histogram measures the scattering of DCT coefficients of an image. Its execution is expounded and dismembered in [19, 20].
The closest expel between histograms of different face pictures can be used for acknowledgment purposes. Diverse detachment measures may impact the acknowledgment rate. Euclidean separation can be utilized as it produces solid and agreeable outcomes. Note that a K-SVD based face acknowledgment method was as of late proposed in [1],yet we contrast in a couple of key regions For the test input, the input signals corresponding to the signature and face traits will be verified using score level fusion method where the optimal weights to distance matching will be found using the proposed G-Firefly algorithm [9]. G-Firefly is an extension of the firefly algorithm [21] integrating the advantages of a genetic algorithm [3].
The available situation information is obtained from computerized tablet and processed using a Hybrid model based signature verification system [12]. The procured information fills in as the premise for the division procedure of the relating checked off-line data [14]. A technique for confirming manually recorded signature where numerous static and dynamic signature components are extracted and used to prepare a few system topologies is displayed [4, 5, 10, 11, 13, 15, 16, 22].
A Hidden Markov Model based Handwritten Sign confirmation framework for delivering to and checking the information in [2]. Instrumented datagloves furnished with sensors for identifying finger twist for perceiving hand marks is utilized as a part of written by hand confirmation [17]. A strategy for program transcribed sign verification depends on standard components that outline several parts of mark shape and elements of target generation is talked about in [7].
3 Model description
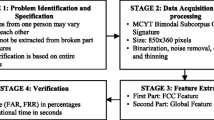
The proposed demonstrate comprise of two ward parts. The first is utilized for face and signature investigation in the event that it is confirmed then the it checks with the signature handling (see Fig. 1). Face Recognition is a noninvasive technique where a part of the subject’s face is gotten and the succeeding image is decreased to a computerized code. Facial acknowledgment reports the altitudinal geometry of perceiving components of the face. In face acknowledgment confront particularly, Legion Histogram include Method had worked as another route for removing arithmetical elements from a image. LHC technique takes face image and measure the interesting qualities and registers the format comparing to every face. Utilizing formats, the calculation then contrasts that image and another image and creates a score that measures how comparative the images are to each other. At that point the signs from the information glove will be intertwined with face image from the webcam in view of the score level for signature confirmation.
The Fig. 1 shows the architecture of the proposed system and the functional components. Face and signature biometrics are belongs to both physiological and behavioral classifications. What’s more face and signature has advantage over different biometrics because it is a natural, nonintrusive, and easy-to-use biometric The proposed signature verification method will be developed using four important steps like, i) Preprocessing, ii) feature extraction from face and data glove signals, iii) Legion feature based feature matching through Euclidean distance, iv) Legion feature Neural network (LFNN) fusion based on weighted summation formulae where two weights will be optimally found out using Legion optimization algorithm, vi) Recognition based on the final score.
3.1 Face analysis
Normally a 2-D power lattice which speaks to a perspective of a 3-D genuine protest of A facial images. The acknowledgment framework ought to be coldhearted not objective to variations in scale, location and in-plane pivot however ought to give appropriate reactions notwithstanding of changes in outward appearance, hairdo, glasses and lighting conditions. Programmed confront acknowledgment strategies exploit full face perspectives and quantities of face. The proposed strategy portrayed in this paper exploits full face sees. It utilizes nonlinear AMF sifting to dismiss insignificant data, makes the subsequent image harsh to various lighting conditions, changes in outward appearances, measure, introduction, glasses and so forth and decreases the info field estimate from 48 × 40 pixels to a compelling information estimate 12 × 10.
3.2 On-line signature tracing
Information glove (http://www.5dt.com) is another measurement in the arena of simulated actuality situations, at first intended to fulfill the stringent prerequisites of present day movement acquisition and animation experts. The high data quality, low cross-relationship, and high data rate make it ideal for online signature affirmation systems. The dynamic features of the data glove give information on:
-
1.
Examples were unmistakable to a people’s signature estimate.
-
2.
The signature procedure used to amid the time
-
3.
Subordinate rolling the hand direction.
Consequently, while most info contraptions offer two or three degrees of flexibility, the data glove is terrific in giving distinctive degrees of adaptability in that it provides information on both the stream of the pen movement amid the signature and the human’s hand shape. Figure 2 exhibits the 5DT Data Glove 14 Ultra with the region of the sensors (http://www.5dt.com).
Sensor Mappings for 5DT Data Glove 14 Ultra. Courtesy From (http://www.5dt.com)
The vast majority of the analysts focus their endeavors to make an advanced a component vector that would efficiently portray dismembered signature and make examinations with the set away one possible. Therefore the foremost highlights of an signature more often than exclude height and width, incline viewpoint of the signature forecasts. The signal handling applications and signature authentication, non linear vector successions are estimated or registered. Such a circumstance arises at whatever point multivariable signs are projected in settled areas. For the examination of such information progressions, a wide variety of multivariate examination construction assemblies are open. The concealed subject of much multivariate examination is change and elucidation of the watched wonders.
4 Process methodology
Face and signature biometrics are belongs to both physiological and behavioral categories. In addition face and signature has advantage over other biometrics because it is a natural, nonintrusive, and easy-to-use biometricThe proposed signature verification method will be developed using four important steps like, i) Preprocessing, ii) feature extraction from face and data glove signals, iii) Legion feature based feature matching through Euclidean distance, iv) Legion feature Neural network (LFNN) fusion based on weighted summation formulae where two weights will be optimally found out using Legion optimization algorithm, vi) Recognition based on the final score.
4.1 Preprocessing
4.1.1 Preprocessing based on adaptive median filter (AMF) for face
At, to begin with, the information sources signal is preprocessed to fit for the feature extraction step. Consider the grayscale as x which experiences preprocessing with the assistance of Adaptive Median Filter to dispense with the noise. The Adaptive Median Filter does the spatial getting ready to find the different pixel of a picture chafed by the inspiration commotion. This filter is sublime in perceiving the disturbance yet at removing a level of clamor. The Adaptive median filter performs in light of the close-by estimations incorporates that see the drive by enrolling the difference amidst the standard deviation of pixels inside the filter window and the related current pixel.
The procedure for Adaptive median filtering is outlined as takes after,
-
1.
Initialize the window size w = 3.
-
2.
Compute the maximum \( \left(s{d}_{a,b}^{\min, w}\right) \), minimum \( \left(s{d}_{a,b}^{\max, w}\right) \) and median \( \left(s{d}_{a,b}^{med,w}\right) \) of the pixel values in \( \left(s{d}_{ia,b}^w\right) \).
-
3.
When \( s{d}_{a,b}^{\min, w}<s{d}_{a,b}^{med,w}<\left(s{d}_{a,b}^{\max, w}\right) \), then jump to step 5 or increase the size of the window w by 2.
-
4.
When w ≤ wmax then jump to 2 or substitue ya, b by \( s{d}_{a,b}^{med,{w}_{max}} \)
-
5.
When \( s{d}_{a,b}^{\min, w}<{y}_{ia,b}<s{d}_{a,b}^{\max, w} \), then ya, b is not a noise candidate or else substitute <yia, b by \( <s{d}_{a,b}^{med,w} \)
A median \( s{d}_{a,b}^{med,w} \) substitutes the noise competitors though other pixels were unaltered. From the predefined input gray scale the impulse noise is disposed of picture by methods for adaptive median filter with preprocessed image (x') at that point experiences the extraction phase.
4.1.2 Preprocessing for signature (Adaptive Filter)
At the point when the data originates from the equipment, it is raw, and we need to preprocess it to standardize the mistakes because of examining, quantization, a speed of hardware, signature position and so on. We are utilizing 5DT dataglove for our trials, and we have additionally encountered the need of preprocessing the data. The preprocessing based Adaptive Filter system of inspecting the point consistently to have measured up to some focuses per unit time. Proposed Adaptive filter connected to any digitizer to compute most extreme conceivable focuses on the signature curve. Here we make utilization of the focuses close by keeping in mind the end goal to figure the parameters of focuses which are absent. Hence the preprocessed signature withpressure & timing information gives the best result with Euclidian Distance (ED) as distance measure.
Algorithm:

4.2 Feature extraction
4.2.1 Histogram based feature extraction (HFE):(Face)
A frequency of each gray level image characterized based on histogram. The variety of histogram is determined by the image to compose which implies histogram of the double image will utilize two frequency esteems. Extraction step returns separated HOG highlights from a true-color image, I. The features are returned in a 1-by-N vector, where N is the HOG full length. The returned highlights encode nearby shape data from areas inside a picture. Then the extracted information will be used for classification and recognition. This four standard deviation arrays are used as a feature vectors for face. The steps for Face feature extraction are as listed below.
Histogram based feature extraction Algorithm (Face)

4.2.2 Vector normalization (VN) based feature extraction FOR signature
Feature Extraction is standard progress is signature acknowledgment. We are utilizing vector quantization based course of action for Feature vector period. This course of action is fast and giving amazing outcomes. As the dynamic signature affirmation supervises time-based direct of signature we are utilizing Vector Quantization along the timing pivot of the signature, the got information is in taking after edge, and each point contains information about X, Y, Z-Coordinates, Pressure, Azimuth, and Altitude of the pen tip. Thus ith point Pi can be considered as P = {Xi,Yi,Zi,Ti,Pr,Az,Alt},Where Ti‟ is the timestamp or arrangement number of particular point in the signature. This is a multi-dimensional component vector, and we execute gathering over the Time turn of the signature using Vector institutionalization computation.
Signature feature extraction Algorithm:
-
1.
Catch the Signature focuses and store in an exhibit.
-
2.
Include the component centers making most outrageous concentrations around a signature twist.
-
3.
Separate the time between the time of the signature into n Intervals: This will be used for batching the component centers.
-
4.
For every interim read every one of the focuses sort the focuses in rising request of the timestamp.
-
5.
For VN discover middle the arranged bunch and think about it as Code vector for that here and now. For VN we locate the normal of every section measurement e.g. X, Y, Z, Pr and so forth.
-
6.
Rehash this system for every one of the interims.
5 Similarity measure using legion feature
5.1 Similarity measure using legion histogram correlation (LHC) for face
The most important part for preparing a learning model is training the classifier. The database is partitioned into 2 parts as: training Set (80%),Testing Set (20%). This means that 80% of the data (images) of every individual are used for preparing the training data-set and rest 20% is used for testing the Algorithm. For accomplishing the perfection in the precision of proposed framework, the merger of Legion Histogram Correlation (LHC) strategies is utilized as a part of the usage of a recommended framework. For preparing, grayscale pictures with 256 receptacles are utilized. Right off the bat, a frequency of every canister is enlisted and secured in vectors for additionally taking care of. Likewise, mean of sequential nine frequencies from the set away vectors are discovered and are acquired in another vector for later use in the testing stage. This mean vector is used for figuring the aggregate differences among the mean of arranged pictures and the test picture. Finally, the base qualification found perceives the planned class with test image. Besides the LHC esteems between test picture and pictures of the foreseen class are figured for coordinate/bewilder on the introduce of arranged cutoff regard. The proposed techniques used for planning and testing are showing up as takes after.
LHC Training Algorithm.

LHC Testing Algorithm.

5.2 Similarity measure using legion vector correlation for signature
In this segment we utilize one of the broadly utilized signals handling methods. We are utilizing „Transforms‟ to extricate ghastly elements from the dynamic signature include focuses. We are thinking about inferred elements, for example, speed, increasing speed and their plots for this count. Here we are talking about multi-algorithmic biometric utilizing various elements. We have utilized Discreet wavelet Transform (DWT). The change are utilized on taking after element vectors.
procedure
-
1.
Signature Feature Points P = {Xi,Yi,Zi,Ti,Pr,Az,Alt}
-
2.
Combination of Velocity and Acceleration Feature focuses.
-
3.
Push and Column Mean of the weight appropriation of the Signature.
-
4.
Push and Column Standard Deviation of the weight. Appropriation of the signature weight dispersion.
6 Legion feature fusion with neural network (LFNN) for face and signature verification
Here we report comes about on the confirmation execution when we performed combination of results got utilizing both modalities i.e. face and signature flow. The proposed combination was performed by taking the greatness of a score vector whose individual components were comparing scores from the LFNN based classifier.
The Legion Feature based Artificial Neural Network is used to learn the face and signature acknowledgment and it is prepared by utilizing the elements values which are coerced from every last image or signals from the Biometric devices. The proposed neural structure used as a Technique all around scores for the required highlights. The inventive LFNN is the base to three units namely,input unit, n hidden units and one output unit. The involvement of the neural framework is the part vector have removed fromtheimages and signals. The entire system is divided into training stage and testing stage. The system is prepared under a huge arrangement of various face and signature database keeping in mind the end goal to empower them to adequately perceive the correct inquiry face and signature in the testing stage.
6.1 Learning or training stage
In the training stage, the input image and a signal feature are separated, and extracted component vector is given as the addition to the proposed neural system. The proposed legion based feed-forward neural network is proposed with different weights(w1,w2,w3,...,wn), and system arrangement is portrayed in Fig. 3. The number of network components in the input layer is f1,f2,f3,..., fn, then the hidden layer with n-neurons, and the output layer O1,O2,O3…On neurons with optimal weights are adjusted to reduce the error. The following procedure is used in the training phase
-
Step 1: Initialize the genuine weight for all neurons of the info layer. Produce singular weights inside the interim [0, 1] and assign it to the shrouded layer neurons and furthermore the output layer neurons.
-
Step 2: The back progation algorithm based training error value adopted from the Trainingpahaseerr = otar − oout
Where the network output is oout and target output is otar are evaluated as \( {o}_{out}=\left[{Y}_2^{(1)}{Y}_2^{(2)}\dots {Y}_2^{(N)}\right] \). Then the proposed training network outputs and the activation functions are as follows.
\( {Y_2}^{(l)}=\sum \limits_{r=1}^{N_H}{w}_{2r1}{Y}_1(r) \)Where,
\( {Y}_1(r)=\frac{1}{1+\exp \left(-{w}_{11r}\cdot {o}_{in}\right)} \)
-
Step 3: Update the weights(w)and change in weights (Δw) of all neurons asw = w + Δw, which can be determined as
Δw = γ. Y2. Trainingphaseerr
Where the learning rate (γ), typically it varies from 0.2 to 0.5.
-
Step 4: Check the Training phase error is minimized to 0.1.and Repeat the process from step 2.
6.2 Recognition/ Testing Phase
In the recognition stage, the input image and signals are maintained by the learning network having accurate weights on the nets. The output is registered so on distinguishing the images and signs based on the arranged dataset. In the regular neural framework, the methodology will be stopped in the track of testing. In the proposed stable neural structure is used for the testing procedure, and upgrade the estimation renewal is the ultimate objective to weights used for testing. In our proposed process the weights are improved with the help of the optimization procedure. By joining optimization upgrade handle, the affirmation precision will be improved along these lines giving better recognition of the picture and flags. The structure of the manufactured neural system is outlined in Fig. 3.
6.2.1 Optimal weights generation and selection in LFNN
The Legion component count is a meta-heuristic evaluation, enthused by the Network weights in the LFNN structure. The optimal computation organize best suited weight values used to Precision improved Recognition parameters. The Legion element calculation is obviously clarified underneath,
Well ordered method of Legion component calculation
-
Step 1: Reset the LFNN Group values si (i = 1,2,…,n)
-
Step 2: Determine frequency (f) and speed (v)
-
Step 3: Adjust the pulse rate (r) and disturbance (L)
-
Step 4: Estimate the best value
Wellness = greatest coordinated information
-
Step 5: Generate new arrangement by altering recurrence and overhauling speed
Where i = {1, 2,… n} n speak to the quantity of Legion component s. E and ɤ is an irregular number E& ɤϵ [0,1]. S0 is the current worldwide best area. Lx = <Lix> is the normal of clamor.
-
Step 6: If the arbitrary number is more noteworthy than the beat rate
-
Step 7: Select the sequence of activity among the greatest and make an adjacent view around the best design by controlling in-discriminately
-
Step 8: optimal best calculation
-
Step 9: if (f(si) < f(sn && rand <Li). Recognize new value by extending the pulse rate and decreasing the noise.
-
Step 10: Observe the best optimal zone.
By utilizing the LFNN estimating as showed up over, the weights are improved which makes the LFNN as accurate recognition of image and signals with upgraded performance metrics. The LFNN states the better precision to the extent seeing the right face image and signals on account of fusing the advancement procedure. Different information are connected to our proposed framework and the authentication is done with the pattern of proposed LFNN, and the results with improved recognition accuracy and precision are evaluated.
7 Performance analysis
The execution of a proposed strategy for face and sign recognition is observed by utilizing the real measures said underneath.
7.1 Accuracy
Accuracy processes in what way close the known image is to the request input.
7.2 Recall
Recall decides the part of signals that are pertinent to the subject input flags that are adequately perceived.
7.3 Precision
Precision is the division of signs perceived that are significant to the question input.
7.4 F-Measure
F-measure is a weighted harmonic mean of precision and recall
7.5 Specificity
Specificity methods the amount of input signs that are applicable to the request input that are not properly recognized.
7.6 Sensitivity
Sensitivity procedures the amount of contributionthat are applicable to the requestinvolvementthat are positivelypredictable.
Object identification and acknowledgment process are tried with various datasets of information confront and signature, and the result of the proposed System has been demonstrated as follows.
8 Results and discussions
The usage of the proposed approach is done in the working stage of MATLAB (version 2015a). The input Face pictures and signals are chosen frame standard database and these are handled by our proposed strategy. The input signal is filtered using adaptive filter for preprocessing. For each preprocessed signal extracted, extensive features are extracted. Once the feature extraction is done the final stage is the recognition of face and signal from the input query signal. The technique used here for the recognition process is LFNN where the ANN is modified using optimization technique called LF algorithm. Finally the face and signature is recognized from the input using the proposed technique. The experimental result is shown in the below sections. Table 1 illustrates the performance of assessment parameters utilized for the recognition of the face and sign for various dataset.
The recognized image and notrecognized face and signature verification have been shown in Figs. 4 and 5. The testing dataset takes a solitary protest as information. The information picture and flag is preprocessed by using an adaptive median filter and arranged by utilizing LF. At that point, the preprocessed picture is extricated by using LHC and LVC algorithm. At that point By utilizing LFNN at last perceived picture and the non-perceived picture has been distinguished.
9 Comparative analysis
From the correlation Table 2, it has been revealing that the accuracy, recall, precision, specificity and sensitivity of the suggested LFNN method has 0.63,0.56,0.93,0.69,0.73 and 0.56 individually which is greater than the other conventional methods like PCA, ICA. In addition Proposed technique False proportion is decreased to 0.08 which makes our framework productive. False Positive Rate, False negative Rate, and False Rejection Rate are furthermore fundamentally diminished when contrasted and the current ICA and PCA methodology. The relationship graph is given below.
The comparison chart in Fig. 6 demonstrates the proposed technique LFNN is higher than the current PCA, ICA strategy as far as Accuracy, Sensitivity, Specificity, exactness, review, FM. From the above Comparisons Table 2 shows thecomparison of different Recognition Models.
Figure 7,illustrates the analysis of time unpredictability delivered by various strategies and the outcome demonstrates that the proposed technique has created less time delay than different methods.
10 Conclusion
In this work proposed an effective LFNN based face and Signature acknowledgment framework for Authentication keeping in mind the end goal to reduce the computational complexity of existing strategy. The closeness estimation is finished by utilizing least Euclidean separation combination based LFNN to decide perceived and non-perceived images. Also in the relative examination, a proposed strategy is compared with an existing technique based on accuracy, sensitivity, specificity, precision, recall, FM. The comparison results in t demonstrate that proposed face and signature recognition in light of LFNN procedure has productively recognized the face images and relating signature from the input databases than the existing procedure.
Change history
20 May 2023
This article has been retracted. Please see the Retraction Notice for more detail: https://doi.org/10.1007/s11042-023-15838-4
References
Biswas S, Aggarwal G, Chellappa R (2009) Robust estimation of albedo for illumination-invariant matching and shape recovery. IEEE Trans Pattern Analysis and Machine Intelligence 29(2):884–899
Garcia-Salicetti S, Houmani N, Dorizzi B (2009) A novel criterion forwriter enrolment based on a time-normalized signature sampleentropy measure. EURASIP J Adv Signal Process 2009:9
Goldberg D (1989) Genetic Algorithms in Search, Optimization and Machine Learning. Addison-Wesley Professional, Reading, MA ISBN 978-0201157673
Gu YY, Zhang Y, Zhang YT (2003) A Novel Biometric Approach in Human Verification by Photoplethysmographic Signals. In: proceedings of 4th International IEEE EMBS Special Topic Conference on Information Technology Applications in Biomedicine, pp. 13–14
Kamel N s, sayeed s (2008) SVD-based signature verification technique using data glove. Int J Pattern Recognit Artif Intell 22(3):431–443
Lay JA, Guan L (1999) Image Retrieval Based on Energy Histograms of the Low Frequency DCT Coefficients. IEEE International Conference on Acoustics, Speech and Signal Processing 6:3009–3012
Lee LL, Toby B, Erez A (1996) Reliable on-line humansignature verification systems. IEEE Trans Pattern Anal MachIntell 18(6):643–647
Li Y, Hancock ER. Face recognition using shading-based curvature attributes. IEEE Proceedings ofthe 17th International Conference on Pattern Recognition (ICPR'04) 1051–4651/04
Nakanishi I, Sakamoto H, Nishiguchi N, Itoh Y, Fukui Y (2006) Multimatcheron-line signature verification system in DWT domain. IEICE Trans Fundam E89-A(1):178–185
Rahmat R, Kamel SS (2009) Subspace-Based Signature Verification Technique using Reduced-Sensor Data Glove. IEEE Symposium on Industrial Electronics and Applications (ISIEA 2009)
Samraj A, Sayeed S, Kiong LC, Mastorokis NE (2010) Eliminating Forgers Based on Intra Trial Variability in Online Signature Verification Using Handglove and Photometric Signals. J Inf Secur 1:23–28
Sayeed S, Besar R, Kamel NS (2006) Dynamic Signature Verification Using Sensor Based Data Glove. Proceedings of ICSP 3
Sayeed S, Kamel NS (2009) A Sensor-Based Approach for Dynamic Signature Verification using Data Glove. Signal Processing: An International Journal 2(1)
Sayeed S, Kamel NS, Besar R (2007) Virtual reality based dynamic signature verification using data glove. International Conference on Intelligent and Advanced Systems
Sayeed S, Kamel NS, Besar R (2008) Enhancement of Glove-Based Approach to Dynamic Signature Verification by Reducing Number of Sensors. International Symposium on Information Technology 2:1–9
Sayeed S, S. Kamel N, Besar R (2009) A Novel Approach to Dynamic Signature Verification Using Sensor-Based Data glove. Am J Appl Sci 6(2):233–240
Song OT, Khoh WH, Teoh A (2009) Dynamic handwrittensignature verification based on statistical quantization mechanism. International Conference on Computer Engineering and Technology(ICCET’08), Singapore, vol. 2: p. 312–6
Swain MJ, Ballard DH (1990) Indexing via color histogram. In Proceedings of Third International Conference on Computer Vision (ICCV), pages 390–393, Osaka
Tjahyadi R, Liu WQ, An S, Venkatesh S (2007) Face recognition via the overlapping energy histogram. In: Proceedings of the International Joint Conference on Artificial Intelligence (IJCAI200 7)
Wright J, Yang AY, Ganesh A, Sastry SS, Ma Y (2009) Robust face recognition via sparse representation. IEEE Trans Pattern Analysis and Machine Intelligence 31(2):210–227
Yang XS (2009) Firefly algorithms for multimodal optimization. Stochastic Algorithms: Foundations and Applications, Lecture Notes in Computer Sciences 5792:169–178
Yao JC, Sun XD, Wan YB (2007) A pilot study on using derivatives of photop phlythesomogrpic signals as biometric identifier. In: Proceedings of 24th Annual International Conference of the IEEE EMBS, pp. 4576–4579
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article has been retracted. Please see the retraction notice for more detail:https://doi.org/10.1007/s11042-023-15838-4
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Vaijayanthimala, J., Padma, T. RETRACTED ARTICLE: Multi-modal biometric authentication system based on face and signature using legion feature estimation technique. Multimed Tools Appl 79, 4149–4168 (2020). https://doi.org/10.1007/s11042-019-07871-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-019-07871-z