Abstract
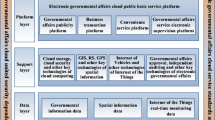
As the economy and society enter the period of rapid post-industrialization, the pressures on resources and the environment are becoming more obvious. Therefore, the environmental protection work faces more challenges. There are many important elements in the environmental emergency detection system, such as emergency monitoring data, information, and command transmission. In order to deal with all kinds of sudden environmental pollution accidents in a timely manner and to reduce the damage to the environment caused by accidents, we need to ensure the safety of the environment. Therefore, we must use scientific methods to manage sudden environmental pollution accidents. In this paper, we combine Internet technology, GIS technology and multimedia database technology, and establishes a decision support system for emergency monitoring and disposal based on multimedia information systems. Its basic hardware includes environmental risk source monitoring, emergency monitoring, command and dispatch, environmental emergency network and environmental emergency monitoring center construction. The software system includes basic software environment, environmental emergency monitoring and command information sharing platform, application software and unified portal. The entire system is integrated according to an organized organizational system, providing detection systems and early warning systems for sudden environmental pollution incident prevention and emergency response. The system we designed can collect and process relevant information in a very short time. The system can quickly handle emergency decision-making and minimize the adverse effects caused by sudden environmental pollution accidents. Experiment results show the well performance of the proposed system. The multimedia based user interface guarantees the user experience.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
With the rapid development of the chemical industry, chemical parks at all levels are constantly emerging and the pressure on the environment is increasing. Although all chemical industrial parks have passed the regional EIA, various environmental protection infrastructure constructions are basically in place, and the awareness of environmental protection enterprises in the district has continued to increase. However, many problems such as unclear quantities of chemical dangerous goods, unclear impacts of major hazards, frequent occurrence of small-scale safety accidents, widespread environmental risk hazards, inadequate environmental supervision capabilities, lagging regulatory technologies, and lag in environmental emergency response are urgently needed.
Hazardous chemicals include flammable, explosive, toxic, and easily oxidized, infectious, radioactive, and corrosive materials. They are widely used in various fields of the national economy and are indispensable raw materials for economic development. Safety monitoring and management of hazardous chemicals production, storage and transportation processes. This has a bearing on the overall situation of safe production, concerns the safety of the people’s lives and property, and is always an important part of work safety.
According to the statistics of China’s Environmental Status Bulletin, in the fresh water environment of China in 2006 and 2011, the proportion of water quality bodies of Grades IV to V and Grade V was 49%. 54%, it can be seen that China’s surface water pollution situation is not optimistic. At present, China is in the process of restructuring its industrial structure. The government proposes that economic development must be coordinated with environmental protection. Thanks to the advancement of production technology and people’s increasing awareness of environmental protection, the total discharge of major pollutants in the country is positive. Decreasing year by year, through efforts to increase pollution control and environmental management, the wastewater discharged from industrial production fluctuates within a basically stable range, and the water environment quality remains generally stable. However, new water environmental problems emerge in an endless stream. Pollution incidents frequently occur, such as sudden ammonia-nitrogen pollution accident in Sichuan’s Lancang River in 2004, a large benzene pollution accident in Songhua River in 2005, and sudden arsenic pollution accident in drinking water sources in Xinyang River, Yueyang City, Hunan Province in 2006, and Dalian Xingang in 2010. Oil pipeline explosion accident, 2011 Hangzhou Xinanjiang phenol leakage accident, Guangxi Hechi Yizhou City Longjiang River cadmium pollution accident, and January 2013 Shanxi turbid river aniline leakage accident. These major sudden water pollution incidents have a series of uncertainties. After the accident, a large amount of water environmental pollutants are released within a short time. The pollutants migrate downstream along with the river water, seriously damaging the ecological environment of the water area, especially the nature reserve. Concentrated drinking water sources have a great impact on the residents’ normal production and living water security, which directly threatens the health of the people and leads to serious social and public crisis. Faced with the needs of rapid socio-economic development and urbanization, the response to sudden water environmental incidents is a new topic that must be kept high attention in this new historical period.
Sudden environmental pollution accidents have no fixed emission method and emission route. They occur suddenly and are fierce. They emit large amounts of pollutants instantaneously or within a short period of time. They cause serious pollution and damage to the environment and cause heavy losses to the people and state property. According to the nature of pollutants and the way they occur, sudden environmental pollution accidents include: nuclear pollution accidents, oil spill accidents, leakage of toxic chemicals, explosions, and diffusion pollution accidents, and pollution accidents caused by abnormally large amounts of discharged wastewater. The main characteristics of emergent environmental pollution accidents can be summarized as follows: Sudden occurrence, diversity of forms, severity of hazards, and arduousness of disposal and disposal. The classification of emergent environmental pollution incidents is the primary criterion for graded response. According to the seriousness and urgency of emergencies, the “National General Plan for Environmental Pollution Incidents” classifies sudden environmental pollution incidents into special major environmental pollution incidents (Level I), major environmental pollution incidents (Level II), and Environmental pollution incidents (Level III) and general environmental pollution incidents (Level IV).
2 System requirements and process analysis
2.1 The overall needs of the system
The environmental pollution accident emergency monitoring and command system requires the management of key hazards and chemical dangerous goods under the computer network environment and the emergency monitoring and management of environmental pollution accidents, and provides advanced technical means for the emergency, preplan management and emergency command of environmental pollution accidents. Policy support.
Management of key hazards
Dangerous materials that are stored in a centralized manner in production companies, hazardous raw materials used in industrial processes, intermediate products, and final products are all dangerous sources. The source of danger can be managed by establishing a database. Record in the database the geographical location of the hazard, existing pollutants or dangerous goods, and the name, nature and origin of the pollutants that may be produced under specific conditions, the scope of the impact of the environmental accident, the extent of the damage, and the amount of storage, etc. To inquire the attribute information and geographical information of the risk source, generate emergency prevention methods and disposal plans for emergency environmental accidents for specific risk sources.
Chemical dangerous goods management
The substances that can cause pollution are dangerous goods. It is necessary to establish a database for dangerous goods, record the name, physical and chemical properties, health hazards, monitoring methods, safety precautions, emergency treatment and disposal methods, laboratory monitoring methods, and the use of instruments and equipment for dangerous goods, so as to achieve rapid computer search and query.
Emergency detection of dangerous goods
After a sudden environmental accident occurs, it is required to promptly identify the information of the pollutant and prepare for the next step. There are many ways to monitor contaminants or dangerous goods. Different methods use different detection instruments and principles. We can enter these methods into the database, together with reference documents such as relevant standards and specifications, in order to prepare for queries and searches, and to provide help and assistance for the monitoring of pollutants [5, 6, 9].
Early warning management of dangerous goods
Certain dangerous goods and dangerous sources have higher frequency of pollution accidents under certain climate conditions. Therefore, under such special weather conditions, it should be possible to search for such dangerous goods, issue early warning information to relevant departments, increase vigilance and prevent pollution accidents.
Decision support and department linkage
When a sudden environmental accident occurs, the environmental protection department is required to promptly make countermeasures to effectively handle emergencies and maximize the safety of life and property of the country and people. In this case, it is necessary to quickly mobilize relevant personnel and consult experts to make decisions. Once a sudden environmental pollution accident occurs, it is generally impossible for a certain department or unit to handle it properly and quickly. Therefore, in the event of major sudden environmental pollution accidents, relevant plans should be launched immediately and reported to the local or higher level government departments in a timely manner. The government should take the lead and all departments should work together. Therefore, the system should have functions such as emergency plans, decision support, department linkage, and on-site monitoring to assist the leaders in decision-making and reduce losses.
2.2 System development purpose and principle
The system builds a network multimedia information center based on B/S mode. Provides a platform for the organization, integration, control, and division of various types of multimedia resources and effective management. Relying on the platform to plan out the key resources, and provide a variety of retrieval portals, the use of simple and convenient, to achieve the purpose of information exchange and resource sharing. Provide users with multimedia resources with a large amount of information and rich content [2,3,4].
According to the needs of the system development user, the following principles are strictly observed during development:
-
1.
Highlight focus and focus on practicality.
The focus will be on how to build a multimedia resource platform that combines the organization, integration, control, and division of multimedia resources, and effectively manages all of them, so as to solve the problems of sharing and interaction of multimedia resources. The system provides basic support environments for applications such as browsing, on-demand, and management planning of various types of resources;
-
2.
The software architecture is reasonable and easy to develop.
Combined with the network multimedia resource management information system, the database has a large number of visits, frequent interactions, different data forms, and difficulty in management and maintenance.
The system integrates the current popular J2EE platform based software architecture and proposes integration.
“Ajax+Structs+Spring+Hibernate” software architecture. Encapsulates various data access details. The use of XML-based “data bus” design ideas shields data format differences and differences between visits and provides a unified access interface to the business logic layer of the object-oriented API, simplifying the development process and improving development efficiency.
-
3.
The level is clear and meets the standard.
The system adopts the standard development mode of JAVA WEB - MVC. A standard application interface is provided between layers.
-
4.
Safe and stable, simple and quick.
The overall requirements of the system are: no loopholes in security, no abnormal operation, simple operation, fast response, and beautiful interface.
-
5.
Reduce platform requirements and enhance system adaptability.
The system is deployed in a network environment. Users only need to access the system through a browser on a PC, without special client configuration and dedicated hardware support.
2.3 Display of multimedia resources
The functional module is suitable for users to classify directory tree branches by means of media resources and to browse the multimedia resources under corresponding media categories layer by layer. It is suitable for users to ask for polyhedral resources in a coarse and generic manner and is one of the commonly used functions of users.
The design requirements are as follows:
-
Operation authority: Each level user operates according to the corresponding authority and can only obtain the multimedia resources under the corresponding level.
-
Arrangement of multimedia resources: all resources are hierarchically arranged by directory tree branches; all the resources contained in the subfolders included in the current folder are arranged and displayed together; similar resources are inverted according to their multimedia resource number, that is, the latest The arrangement of resources is shown first [1, 7, 11].
-
Display mode: The relevant resources can be displayed (or played) in thumbnails, catalog information lists, previews, etc., respectively.
-
Log Management: The system automatically records the operation.
-
Automatic statistics: record user downloads, browsing times, etc.
The function buttons are as follows:
-
Toggle: Interchange display of thumbnails and record information lists.
-
Preview: The resource description information can be displayed in the form of a card, which contains functions such as picture restoration (or on demand, audition).
-
Picture Restoration: Displays the current picture in 100% proportion.
-
Bulk package download: Batch downloads selected multimedia resources by permission.
-
Single Download: Download resources by permission.
This system provides users with multiple retrieval modes. It is suitable for user-defined query conditions to retrieve the multimedia resources under the corresponding confidentiality level; it is suitable for the user to have a more explicit request for resources, that is, to satisfy the user’s need of “finding a given goal”. These search modes are divided into: single condition search, compound condition search, reference relation search, synonym search, which is one of the commonly used functions of users.
-
Single-term condition retrieval: Using the “keyword” as an entry condition, retrieve the data in the database. It can be the AND of multiple keywords.
-
Compound condition search: All the entries can be used as entry criteria to retrieve the data in the database. Element conditions can be “and” can be “or”; operators include: <, <=, =, >, >=, <>, including before, including, after the inclusion, not including.
-
Reference relation search: When a resource has two or more genus characteristics, it can be recorded by the main genus and the reference genus. The main genus of resources is unique: that is, the main genus of any resource must have one and only one; and the reference genus of resources can be vacant, single, and multiple. When a resource has more than one reference genus, the method for recording is that the reference genres are separated by a single space. The reference relation retrieval method is based on the multi-general characteristics of resources, uses the reference genera of resource descriptions as clues, and uses reference relationships to expand the search scope purposefully and appropriately. To meet specific needs. This is one of the distinctive search methods of this system.
-
Synonym retrieval: Retrieving based on synonyms table. For example, the words “vehicle” and “car” are similar but have similar meanings and thus constitute a synonymous relationship. When the description is “vehicle”, if the search is based on “car”, no target can be found in the general matching search. The use of synonyms retrieval can effectively improve the recall rate and precision rate to meet specific needs. This is one of the characteristic search methods of this system [8, 10, 12].
The bitmap image storage space is calculated as follows:
The formula for calculating the amount of uncompressed video files is as follows:
The storage capacity of uncompressed Wave sound files is calculated as follows:
2.4 Sampling point of multimedia data
Assume there is an image denoted by f(x,y), its resolution is 512*512. Then the discretization of x and y is called sampling, and the discretization of f(x,y) values is called quantization (Figs. 1, 2, 3, 4, 5 and 6).
The concept of bitmaps is as follows. The color of each point in the picture is stored as a binary number as an element in the digital matrix. The elements in the digital matrix are called pixels; the digitized matrix is placed in the display buffer and corresponds to the points on the display. This is the bitmap image. Bitmap images are also referred to as “raster images.” When you zoom in a bitmap image to a certain extent, you will find that it is composed of small squares (image grids). These small squares are pixels.
For multimedia computers to process images and video, first the continuous image function f(x,y) must be spatially and discretely discretized.
-
Sampling: The discretization of spatially continuous coordinates (x, y) is called sampling.
-
Quantization: Discretization of f(x,y) colors, called quantization.
-
Digitization: Combining two kinds of discretization, called digitization.
The result of the discretization is called a digital image.
-
Sampling Theorem: Let the maximum frequency of the continuous signal x(t) be fm. Sample the sampling frequency fs to obtain the discrete signal x(nT) if it satisfies:
That can be completely determined by x(nT) continuous signal x(t). When the sampling frequency is equal to 2 fm, that is, fs0 = 2 fm, fs0 is said to be the Nyquist frequency.
In multimedia data, there must be two sampling points at the highest frequency.
2.5 Uniform quantization and non-uniform quantization
In the uniform quantization model, the entire data range is divided in N equal intervals of length Q. Where interval i is mapped to the middle value of this interval.
We have: xi: partition levels and \( \hat{x_i} \): reconstruction levels.
For uniform quantization, we have:
For uniform quantization, we have:
Shown as follows:
2.6 Information entropy and Huffman coding
The amount of information and information entropy are calculated as follows:
In 1951, Huffman and his classmates at MIT Information Theory needed to choose whether to complete the semester report or the final exam. The subject of Robert M. Fano’s semester tutor report to them is to find the most efficient binary code. Since it was impossible to prove which of the existing codes was the most effective, Huffman gave up the research on existing coding and turned to new explorations. Eventually he discovered the idea of encoding based on ordered frequency binary trees and quickly proved that this method is most effective. of. Thanks to this algorithm, the students finally excel at blue, surpassing his mentor who had studied similar codes with Shannon, the founder of information theory. Huffman uses a bottom-up approach to build a binary tree, avoiding the worst drawback of the suboptimal Shannon-Fano coding—top-down tree construction.
In 1952, David A. Huffman published an article “A Method for the Construction of Minimum-Redundancy Codes” when he was studying for a doctoral degree at MIT. It is generally called Huffman coding.
Huffman proposed an indefinite-length encoding method, also called Huffman coding, in 1952 based on the encoding ideas described by Shannon in 1948 and Fano in 1949. The basic method of Huffman coding is to scan the image data once and calculate the probability of occurrence of various pixels. The unique codewords of different lengths are specified according to the probability, and a Huffman code table of the image is obtained. The encoded image data records the code word of each pixel, and the correspondence between the code word and the actual pixel value is recorded in the code table.
Huffman coding is a type of variable length coding (VLC). Huffman proposed an encoding method in 1952. This method constructs the shortest code word of the different word heads based on the probability of occurrence of characters. It is sometimes called the best code, and is generally called Huffman code. A theorem is cited below. This theorem ensures that the code length is assigned by the probability of occurrence of the characters, and the average code length is the shortest.
3 Work content and procedures
3.1 Environmental emergency monitoring system
Environmental emergency monitoring and command system integrates hardware and software. Its basic hardware includes environmental risk source monitoring, emergency monitoring, command and dispatch, environmental emergency network and environmental emergency monitoring center construction. The software includes basic software environment, environmental emergency monitoring and command information sharing platform, application software and unified portal. The entire system is integrated according to an orderly organizational structure system to provide the application and management of environmental risk sources, risk analysis and risk assessment, and online information acquisition and analysis of emergencies for emergency environmental pollution incident prevention and emergency response. Development and impact analysis of disaster events, classification and release of early warnings, assessment of crowd evacuation and evacuation, optimization of emergency plan and start-up, real-time information acquisition of on-site and emergency, collaborative command and consultation mechanism, dynamic emergency decision-making command and resources The overall effectiveness evaluation and emergency response assessment of the configuration, emergency response, and information management functions such as simulation drills.
The hardware network environment layer mainly includes two parts: environmental risk source monitoring, emergency monitoring capability construction, and monitoring center construction. Environmental risk source monitoring and emergency monitoring provide the entire system with real-time monitoring and emergency site information for accident early warning and alarms. Emergency monitoring refers to the collection of incidents through drones, emergency monitoring vehicles, ships, environmental emergency monitoring terminals, and PDAs. Information for the command center to handle emergency, command and dispatch decisions. The basic software environment layer mainly provides system development and construction tools, GIS software platform and database software. The data service layer is the data support layer of the system, including the system’s data resources and data resource management functions, and provides basic data support for the system. The application platform layer is mainly composed of middleware of a group of geographic information systems and management information systems. It is the business logic concentration point of the entire system and directly provides services for the application system layer. It is in a very important position in the overall architecture of the entire system. The application system layer is the integration and implementation of various functional modules of the system. It includes sudden pollution incident emergency systems, pollution source data and video surveillance alarm systems, environmental monitoring and mobile law enforcement management systems, environmental quality monitoring data management systems, and environmental monitoring services integrated management. The system, as well as the secondary core application software and other six main application modules. The portal layer is the portal integration interface for each functional module of the system. The user layer is the system’s integration of functions and interfaces customized by users, such as decision makers and business offices.
3.2 Emergency monitoring (rapid characterization of pollutants)
Environmental emergency monitoring capabilities include the ability to quickly obtain on-site information and rapid analysis of pollutants. The rapid acquisition of on-site information refers to the use of vehicles such as drones, vehicles, and boats that can travel to the scene at the first time when an incident occurs, and can transmit on-site information in the form of video, sound, and data to the surveillance command center, or on-site. After monitoring and analysis, the analysis results will be reported to the monitoring command center or emergency command department to provide decision support for the emergency command. The major R&D and production achievements currently exist: environmental emergency monitoring drones, environmental emergency monitoring vehicles, environmental emergency monitoring ships, environmental emergency monitoring terminals, and various water and gas emergency monitoring equipment.
The main methods of monitoring environmental pollution include chemical methods, biological methods, etc., which generally refer to the characterization and quantification of special pollutants in the environment through chemical or biological reactions. In response to today’s pollution incidents, traditional chemical methods have major flaws. If all toxic substances cannot be detected, there is a lower limit for concentration analysis and it is not possible to correlate toxic concentrations with the toxic effects of organisms. With the rapid development of life science and technology, biological detection methods have become more and more important. The research hotspots in this field include biotoxicity detection of single and multiple contaminants, microbial population testing of pollution treatment systems, bioassay of water body health, and monitoring and control technology of solid waste biological treatment processes.
Biological toxicity testing of single and multiple contaminants
In the field of bio-toxicity detection of single pollutants, the State Key Laboratory of Chemo-Biosensing and Metrology has developed a series of biosensors and developed a series of bio-sensing detection methods, such as trace Cr(VI) and Hg in the environment. (II) High-sensitivity biosensing detection technology for benzoquinone and organochlorine pesticides. In the study of bio-toxicity detection of complex contaminants, domestic units have initially explored the combination of artificial intelligence pattern recognition technology and light-emitting micro-organisms monitoring technology in order to quickly determine the type and pollution of pollutants in the event of sudden environmental pollution. Degree, and possible sources of pollution.
Detection of microbial populations in pollution treatment systems
The pollution treatment system micro-population detection has great significance for stabilizing the biological treatment system and improving the biological treatment efficiency. Scholars from the Chengdu Institute of Biology, Chinese Academy of Sciences and other institutions have used modern molecular biology methods to establish routine monitoring and control methods for microbial populations in wastewater treatment systems. They have also conducted long-term tracking of functional bacteria in biological treatment systems for pollution treatment and found that Functional bacteria are stable in the system. In order to achieve real-time and accurate control of the reactor, rapid microbial population detection must firstly break through. Domestic reports on the use of fluorescence in situ hybridization and flow cytometry for microbial cell detection and analysis of activated sludge cell suspensions have been reported.
Water body health bioassay
The analysis of the health status of water bodies is also a major application area of biological monitoring. Although the physical and chemical indicators of water can reflect the nature of the water body to a certain extent, it is difficult to define the toxicity and health of the water body. The advantage of biological monitoring is that it can determine the bio-toxicity of environmental pollutants and reflect the micro-pollutants in the water body. There is an irreplaceable advantage to compound pollutants.
Solid waste biological treatment monitoring and control technology
The real-time monitoring and automatic control of solid waste biological treatment systems has always been a challenge, and equipment that is not available internationally has been available. Scientists from the Institute of Geography of the Chinese Academy of Sciences have worked hard to develop a monitoring probe for temperature, moisture, and oxygen for composting, and realized real-time, automated real-time monitoring of sludge composting, solving the problem of odor pollution that is common in the compost industry. The Northwestern A&F University used BIOLOG microplate technology to analyze the changes of the microbial communities in the reclaimed land, and explained the BIOLOG data using the principal component analysis method. The results were satisfactory.
3.3 Risk source identification and dynamic supervision system
Based on the structure and function of the environmental risk source identification and dynamic supervision system in industrial clusters, the system will identify the environmental risk source by establishing a risk source identification system, a risk source basic database, a risk source dynamic supervision system, and a data resource management and maintenance system. Dynamic supervision.
The identification of risk sources by the risk source identification system and the management of risk sources enhances people’s awareness of risks and precautions of risk sources, and accelerates the speed of accident rescue personnel’s definition on the spot and improves the accuracy of rescue decision-making.
The classification of risk sources is the basis of the declaration, census, and management of risk sources. The classification of science and rationality helps to objectively reflect the essential characteristics of risk sources. Combine the characteristics of hazard sources in environmental pollution accidents to help objectively reflect the nature of environmental hazards and the characteristics of pollution in the environment, facilitate the management of risk sources, and facilitate emergency response measures in the event of an accident. For other purposes. At present, the classification of hazardous sources in China is based on the six types of environmental pollution accidents, including sources of atmospheric pollution, sources of water pollution, sources of oil, solid waste, sources of radioactive pollution, sources of biological pollution, and sources of unknown pollutants. Classification criteria. The system will classify the hazard sources according to the basic conditions and data information of the hazards. Classified management not only facilitates the retrieval of dangerous sources, but also facilitates the statistical work of hazardous sources.
3.4 The establishment of a database
The main data managed by the emergency warning network system for sudden environmental pollution accidents are: basic geographic information data, environmental professional spatial data, hazard source data, dangerous goods data, monitoring and analysis method data, emergency monitoring and liaison organization data, and environmental emergency expert data. Emergency monitoring vehicle data, emergency monitoring data, weather monitoring data, emergency accident disposal plan data, environmental emergency accident management data, environmental pollution accident case data management, environmental pollution accident warning system data, environmental pollution accident diffusion analysis model data, pollution diffusion Analog event data, etc.
The basic geographic information data and environmental professional spatial data in these data can be managed by the GIS platform and relational database, making the spatial data and attribute data of these geographic elements matched and matched. For other data can be managed directly using a relational database.
In the database design process, the design principles of the database should be followed, and the entity-attribute (E-R) method can be used for design.
System integration program
The system uses the GIS common platform and database management integration framework to implement the system’s various functional modules, and adopts the integration of application integration and component integration to organize the various functional components together.
Data access plan
Access to data uses ADO.NET’s data cache technology to speed up the interaction and response of the system.
Data interaction and network topology
The entire system runs on a wireless CDMA network. According to the structure of the system, the system is divided into the local version and the central version. The difference between the local version and the central version is that the local version only pays attention to the data of the monitoring vehicle, while the central version needs to monitor the overall emergency command status. The overall data transmission is based on the data acquisition communication module, through which the transfer between databases is achieved.
Between the center version system and the monitoring vehicle and between several monitoring vehicles, the connection and communication are based on the wireless network, and at the same time, a logical connection relationship is established with the digital acquisition communication system.
3.5 Construction of emergency response system
Through the integration of safety technical parameters of the company into the scope of supervision, automatic inspection and automatic warning of major risk source safety conditions can be done in a timely manner to prevent accidents and realize dynamic monitoring and overall management of major risk sources.
Based on unfavorable weather conditions, the system determines whether one or more of the pollutants discharged by the park on the same day exceeds the standard and whether measures need to be taken to protect the sensitive points and residential areas around the park. The increase in the type and quantity of pollutants caused by accidents will have an adverse impact on the overall control of the park as a whole. The risk prediction model is used to calculate the scope, intensity of the accident and the maximum concentration of downwind landings to estimate whether the combined effects of the accidental emissions will meet or exceed the critical mass of the surrounding sensitive points or residential areas.
The hazardous chemicals accident emergency decision support subsystem in the park combines the emergency rescue knowledge base, emergency plan database, emergency treatment case database, and GIS spatial analysis technology to provide timely and accurate information for accident emergency decision-making commanders: The distribution location, the company site electronic floor plan, the company site scene aerial picture, emergency plan, hazardous chemical properties and disposal measures, emergency rescue organization, the distribution of emergency rescue forces, the scope of the impact of the disaster, the best path for the rescue, etc. Supporting information greatly improves the response capability of emergency rescue and the science of disaster relief.
The emergency communication system plays an important role in information contact and information transmission in the emergency response command system and is an important part of the emergency system. In the event of a major accident, the communications system should ensure timely notification of the relevant emergency agencies, local governments, and relevant departments at higher levels, and have multi-channel alarm functions and multi-channel communication tools. The system includes a public broadcasting management system, a short message group management system, and an outdoor announcement management system.
3.6 Mathematical momentum model for monitoring objects in the environment
According to Navier-Stokes three-dimensional equation, we have the system’s control equation:
The relationship between the various gradient stresses in the system is controlled by:
The continuity equation is:
The definition of the CFL number is based on the Cartesian coordinate system and the equation is:
3.7 Information discrimination system
Pseudo-information often leads to false alarms and missed alarms in early-warning systems. It generates more serious risks than incomplete information. Therefore, the initial information cannot be directly applied and must be identified to eliminate false positives. There are five ways to discriminate information:
-
(2)
Conduct comparative verification of various sources of information. If there is a contradiction between them, the source of information must be incorrect.
-
(3)
Analyze the information transmission process to ascertain the time points reflected in the information and analyze possible errors in the transmission.
-
(4)
Conduct an affair analysis. If the information is obviously inconsistent with the affair, the source of the information is incorrect.
-
(5)
Anti-evidence analysis. That is to establish the relationship between the information and the current event status, and then from the current incident to reverse the original information, if the counter-evidence results and the original information bias is greater, then prove that the information source is wrong or out of date.
-
(6)
Unfavorable evidence. That is, assuming that the information is true, then analyze the unfavorable conditions that may occur under this assumption. If such an unfavorable situation is very serious, then such information should be used with caution.
Information storage
The purpose of information storage is to accumulate information for backup purposes and should be constantly updated and supplemented.
Inferring information
Use existing information or lack of information to make judgments and infer the accident signs.
Since the early warning information system completes the function of converting the original information to the symptom information, it is required that the information basic management work must satisfy the following conditions:
-
(1)
Standardization. Each job requires clear responsibilities and quantitative requirements, and the information sources meet the consistency requirements.
-
(2)
Standardization. Accurate technical standards should be used for measurement and measurement in the process of collecting information.
-
(3)
Unified. All types of statements, ledgers, and original documents must have a unified format and content, and be uniformly coded.
-
(4)
Procedural. Data collection, transmission, and sorting must all have clear procedures, deadlines, and responsibilities.
3.8 Early warning evaluation index system
The purpose of establishing an early warning evaluation index system is to make information quantitative, organized, and operational. According to the technical level, the early warning indicators can be divided into potential indicators and indicators. Potential indicators are mainly used to quantify potential factors or symptom information. Showing indicators is mainly used to quantify the appearance or status information. However, the selection of actual warning indicators mainly considers factors related to people, machines, rings, and pipes.
The establishment of early warning evaluation indicators and the establishment of evaluation index standards are the preconditions for the early warning system to carry out activities such as identification, diagnosis, and pre-control. It is one of the key links in early warning management activities.
The construction of early warning evaluation indicators should follow the following principles:
-
1.
Sensitivity. That is, indicators can accurately and sensitively reflect the true state of the hazard.
-
2.
Scientific nature. That is, the selection of indicators, the determination of indicator weights, the selection of data, and the calculation must be based on accepted scientific theories to ensure that the indicators not only meet the comprehensiveness and relevance requirements, but also avoid mutual overlap.
-
3.
Dynamic. The accident process itself is a dynamic process. Therefore, the evaluation index should be dynamic and comprehensively reflect the trend of accident development.
-
4.
Operability. Make full use of available statistical data and related company, industry safety norms and standards.
-
5.
Guidance. The evaluation indicators should reflect the overall strategic objectives of the industry in order to regulate and guide the behavior and direction of the company’s future development.
-
6.
Predictability. Early warning indicators should be selected to reflect the status quo and predict future indicators.
Early warning criteria refer to a set of criteria or principles for determining whether an alert should be issued and what level of alert should be issued at different warning levels. The setting of early warning standards must be based on standards. If the criteria are designed too loosely, it will make it dangerous to fail to cause an alarm, which will result in a missed alarm, thus weakening the role of early warning. If the warning criteria are set too strict, it will cause an alarm to be issued when an alarm should not be issued, which will result in false alarms and false alarms for related personnel. Repeated false alarms will cause related personnel to lose trust in the alarm signal. Early warning guidelines have different forms based on different warning methods.
According to the intrinsic characteristics and understanding of the evaluation indicators, there are three forms of early warning methods: index early warning, factor early warning, and comprehensive early warning. However, the fourth form often appears in the actual warning process, namely, false alarms and missed alarms.
Indicator warning
Refers to issuing different levels of alarms based on changes in the magnitude of warning indicators. The indicator for the alarm is X. As shown in the figure below, its security zone is [xa, xb]. Its primary risk areas are [xc, xa] and [xb, xd]. Its higher risk areas are xe, xc] and [xd, xf]. The warning guidelines are as follows:
When xa ≤ x ≤ xb, no alarm occurs;
When xc ≤ x ≤ xa or xb ≤ x ≤ xd, an alarm is issued;
When xe ≤ x ≤ xc or xd ≤ x ≤ xf, a secondary alarm is issued;
When x ≤ xe or x ≥ xf, a three-level alarm is issued.
Factor warning
When some factors cannot use the quantitative indicators to alarm, factor early warning can be used. This early warning method is a kind of qualitative warning with respect to the early warning of indicators. For example, in safety management, when there are people’s unsafe behaviors and management defects, an alarm will be issued. The warning guidelines are as follows:
When the factor x appears, an alarm is issued;
When factor x does not appear, no alarm is issued.
This is an all-or-nothing warning.
When the warning indicator x is an uncertain (random) factor, the warning must be made in the form of a probability.
Comprehensive warning
Combining the above two methods together and taking into consideration a number of factors, a comprehensive alarm model is derived.
Mis-alerts and missed police. There are two types of false alarms. One is that the system issues an accident alert and the incident does not occur. The other is that the system issues an accident alert that eventually appears, but the level of its occurrence differs from that of the forecast by one level (eg, a high-level alert is issued, but in fact is an elementary alert). The general false alarm refers to the former situation. The cause of false alarms is mainly due to the improper setting of indicators, excessively strict warning criteria (ie, the design of the safety zone is too narrow, the design of the danger zone is too wide), and the information data is wrong. Missing alarm is the phenomenon that the warning system did not issue an alarm and the accident eventually occurred. One of the main reasons is that small-probability events are excluded from consideration. However, these low-probability events may also occur. Second, the early warning criteria are too loose (ie, the design of the safety zone is too wide and the design of the danger zone is too narrow).
3.9 Implementation of early warning system
A complete warning system provides a material basis for the realization of accident warning. Early warning system realizes early warning and control of accidents through early warning analysis and pre-control measures. Early warning analysis Complete monitoring, identification, diagnosis and evaluation functions. Pre-control measures Complete the functions of correcting and correcting the bad trends of accident symptoms.
-
(1)
Monitoring
Monitoring is the premise of early warning activities. The tasks of monitoring include two aspects: First, all-round and whole-process monitoring of the weak links and important links in safety production is conducted. At the same time, various signs of accidents are collected and corresponding databases are established. The second is to process a large amount of monitoring information (organize, classify, store, and transmit), establish information files, and perform historical and technical comparisons. That is, through the arrangement, analysis, and storage of historical data and real-time data, an early warning information file is established. The information in the information file is shared with the entire early warning system, and it will timely and accurately input the next warning link.
The main working means of the monitoring process is the application of scientific monitoring indicators system to achieve the proceduralization, standardization and dataization of the monitoring process.
-
(2)
Recognition
Identification is the use of the evaluation index system to analyze the monitoring information to identify various types of accident signs, accident incentives, and the trend of accident activities that will occur during production activities. The main task of recognition is to apply “appropriate” identification indicators to judge the occurrence of abnormal symptoms and possible chain reactions.
-
(3)
Diagnosis
Analyze the causes of the various accidents that have been identified and predict the development trends to determine which phenomena are major and which are subordinate and episodic. The main task of diagnosis is to identify the most dangerous and most harmful major factors among many hazards, analyze the causes, and accurately and quantitatively describe the development process and possible development trends. The diagnostic tool is a unified evaluation index system of company characteristics and industry safety production commonality.
-
(4)
Evaluation
A descriptive evaluation of the major accident symptoms that have been confirmed to determine what kind of impact the production activities will suffer under the impact of these accident symptoms, and determine whether the state of production at this time is normal, vigilant, or dangerous, extremely dangerous, and crisis Status, and grasp its development trend, and accurately report alarms when necessary. The risk may be static and may be dynamic. Some are more obvious and some are potential. On the one hand, it can be judged through perceptual knowledge and historical experience. On the other hand, it is through the collation, analysis, and induction of various objective accident records, and when necessary, consulting with experts.
Monitoring, identifying, diagnosing, and evaluating these four early warning activities are causal links in the sequence. Monitoring activities are the preconditions for the development of the early warning system. There is no clear and accurate monitoring information. The activities in the last three links are blind or even meaningless. Identifying activities is a crucial link. Its identification of accidents can enable enterprises’ production safety management to determine the focus of early-warning tasks among the complex and varied disaster-causing factors, and also to make diagnostic and evaluation activities have clear goals. Diagnostic activities and evaluation activities are technical analysis processes. The analysis of the causes and processes of major accident phenomena and the evaluation of the consequences of accident losses can enable companies to have a scientific basis for identification when adopting pre-control measures or crisis management strategies. The entire process of early warning activities presents an orderly and causal relationship. Among them, the monitoring information system of monitoring activities is shared by the entire early warning management system, and the results of the activities of the three links of identification, diagnosis, and evaluation will be saved into the monitoring system by information. In addition, the evaluation indicators used in these four activities are also shared and united.
4 Multimedia data simulation
4.1 Software platform
The system uses a high-level programming language Visual C++ 6.0 (hereinafter referred to as VC) in combination with a three-dimensional graphics development interface OpenGL 1.2 as a software development platform.
VC has always been the most powerful visual object-oriented language development tool in the Microsoft development suite. It is an integrated development environment for WIN32 applications. It uses a message response mechanism and has a powerful window management mechanism and menu functions in human-computer interaction. With other languages can not be compared to the advantages. OpenGL is a software interface of 3D graphics hardware developed by SGI of the United States. Because of its good stability and portability, it has become a cross-platform 3D graphics engine, and it is the most widely used 3D graphics standard. It includes more than 250 graphics functions and provides functions such as view transformation, model transformation, basic element drawing, coloring, lighting, shadowing, blanking, anti-aliasing, texture mapping, and animation. It has now become a de facto graphics industry standard.
Therefore, under the Windows 2000 operating system, the system uses VC as a development platform and uses OpenGL 1.2 to implement three-dimensional graphics programming. This is making them perform their best and has achieved good experimental results.
We use the explosion (leakage) of chemicals as a sudden pollution incident. The system is mainly composed of three parts. The first part is a three-dimensional scene, which prepares for the future improvement of the system. The second part is the software introduction. The third part is the feedback of this system. The following figures are partial interface effect diagrams of this system.

(a) menu.

(b) daytime.

(c) nightfall.

(d) at night.
In the modeling of the environment, especially in the modeling of buildings such as campuses or communities, the modeling of buildings should be determined depending on the specific application. For some representative buildings or buildings that require specific performance, we should model them in detail. For some alternative architectural buildings, we only observe the entire distance and do not need a detailed description of the interior.
4.2 Windows system based multimedia framework
The DirectX Software Development Kit is a set of programming interfaces that Microsoft provides programmers to develop high-performance graphics, sound, input, output, and online games on the Windows operating platform. Microsoft defines DirectX as “hardware device independent”, that is, using DirectX can be used for device-independent methods to provide device-related performance. The establishment of the DirectX standard can provide a strategy for hardware development. Hardware vendors have to follow this standard for product improvement. At the same time, by using the interface provided by DirectX, developers can make full use of the high performance that the hardware may bring, without the need to The specific implementation details of the relationship hardware.
DirectX uses the COM (Component Object Model) standard, so versions of different objects can have different interfaces. This allows programs developed with DirectX to be fully compatible and supported even in the future.
DirectShow is a member of the DirectX family that provides a complete solution for high-performance multimedia applications such as playback, audio and video capture of multimedia files in various formats on the Windows platform; DirectShow integrates other members of the DirectX family (such as DirectDraw, Techniques such as DirectSound etc. provide convenience for multimedia applications.
4.3 System module function test
The purpose of testing and debugging of programs and systems is to discover possible errors in programs and systems and correct them in a timely manner. According to the description of the module processing process in the system design document, the program designer selects a suitable computer programming language and prepares a program that is correct, clear, robust, easy to maintain, easy to understand, and highly efficient. In order to do a good job in program design, you need to understand and master the criteria for measuring the quality of the program, the steps for programming, and the methods for programming. In the development of this system, we used Visual C++ 6.0 as a development tool. Visual C++ 6.0 provides a true object-oriented visual programming method. With only a small amount of code, you can program with a standard Windows style, and code maintenance is very convenient. In the scene, three-dimensional model and simulation effects with PLIB and OpenGL combined to achieve better results.
Module functional testing, also known as unit testing, is a small piece of code written by the developer to verify that a small, well-defined function of the code under test is correct. In general, a unit test is used to determine the behavior of a particular function under a particular condition (or scene). The system is composed of multiple functional modules, each consisting of one or several programs. This test was mainly completed by myself. I put all the programs in each module in series and debugged. After debugging, the correct control relationship was finally established between each program in each module, and the correctness among modules was achieved. Communication.
However, it is impossible to find all the errors in the system test. Therefore, some undiscovered errors may be hidden in the system, and these errors will be exposed after the system is running. System maintenance means that after the system is put into use, various modifications are made to the system, including maintenance of hardware, software, code, and documents. The contents of system maintenance generally have four items: corrective maintenance, preventive maintenance, and perfect maintenance adaptive maintenance.
Corrective maintenance is to correct system maintenance by correcting errors in the system. These errors were not exposed during the system test and they occurred during the operation phase. Maintenance must be performed for this error, otherwise the system cannot operate normally.
Preventive maintenance is to prevent system errors, and the system maintainability must be considered during the system analysis and design phase.
Perfect maintenance is to improve the system’s new needs and maintain the system. The so-called new demand is in the system operation stage, the user puts forward new function or performance requirement.
Adaptive maintenance is the system’s maintenance in order to adapt to changes in the environment.
5 Conclusion
Based on the economic data of 31 provinces and regions in China, this paper uses a spatial panel data model with time-space specific effects to examine the contribution of institutional variables to regional economic growth in China. Meanwhile, we use multimedia data visualization technology to make the data clearer.
Compared with the estimation results of traditional econometric models, the contribution values of economic growth factors in spatial econometric models have been reduced to varying degrees, and empirical results that ignore spatial attributions are necessarily biased. Among them, the spatial flow of factors will have a leading role in the economic growth of neighboring provinces. Institutional factors directly contribute to regional economic growth, and capital and technological production factors can also be explained by institutional factors. This shows that the contribution of traditional production factors to economic growth will inevitably include the role of institutional elements, and institutional elements will have more explanatory power for economic growth. The spatially balanced development of institutional supply, institutional innovation, and institutional factors is an important factor affecting regional economic development in China.
References
Gai K, Qiu M, Zhao H (2016) Cost-aware multimedia data allocation for heterogeneous memory using genetic algorithm in cloud computing. IEEE Transactions on Cloud Computing PP(99):1
He, B. X., & Zhuang, K. J. (2016). Research on the Intelligent Information System for the Multimedia Teaching Equipment Management. In Information System and Artificial Intelligence (ISAI), 2016 International Conference on (pp. 129-132). IEEE
Jeong HY, Yeo SS (2014) The quality model for e-learning system with multimedia contents: a pairwise comparison approach. Multimedia Tools and Applications 73(2):887–900
Khobragade MVB, Patil MLH, Patel MU (2015) Image retrieval by information fusion of multimedia resources. Image 4(5):155–173
Lin, E. C. H., Shih, Y. C., & Chang, R. C. (2016) A Research on Integrating AR and Multimedia Technology for Teaching and Learning System Design. In International Conference on Frontier Computing (pp. 725-731). Springer, Singapore
Lv Z, Chirivella J, Gagliardo P (2016) Bigdata oriented multimedia mobile health applications. J Med Syst 40(5):120
Maigrot C, Claveau V, Kijak E, Sicre R (2016). MediaEval 2016: A multimodal system for the Verifying Multimedia Use task. In: MediaEval 2016: "Verfiying Multimedia Use" task
Panjanathan R, Ramachandran G (2017) Enhanced low latency queuing algorithm with active queue management for multimedia applications in wireless networks. International Journal of High Performance Computing and Networking 10(1-2):23–33
Pereira MH, de Souza CL, Pádua FL, Silva GD, de Assis GT, Pereira AC (2015) SAPTE: A multimedia information system to support the discourse analysis and information retrieval of television programs. Multimedia Tools and Applications 74(23):10923–10963
Zhang F (2016) Research on the Optimization of Multimedia Information Technology in College English Teaching. Revista Ibérica de Sistemas e Tecnologias de Informação E12:252–262
Zhang Y, Shen J, Wen J, Hu Y, Li Y, He L (2016) Uncertainty-based dynamic multimedia human health risk assessment for polycyclic aromatic hydrocarbons (PAHs) in a land oil exploitation area. Human and Ecological Risk Assessment: An International Journal 22(7):1552–1573
Zhu W, Cui P, Wang Z, Hua G (2015) Multimedia big data computing. IEEE multimedia 22(3):96–c3
Acknowledgements
Special fund for science and technology development in 2016 of Department of science and technology of Guangdong Province under Grant No. 2016A020223007.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Lei, Y., Zhou, X. & Xie, L. Emergency monitoring and disposal decision support system for sudden pollution accidents based on multimedia information system. Multimed Tools Appl 78, 11047–11071 (2019). https://doi.org/10.1007/s11042-018-6665-2
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-6665-2