Abstract
This paper present a secure medical image watermarking technique applying spread-spectrum concept in wavelet transform domain is proposed. In the first step, discrete wavelet transform(DWT) decomposes the cover medical image into four frequency sub-bands using Mexican hat as mother wavelet and then corresponding to each pixel of the binary watermark a pair of Pseudo-Noise (PN) is embedded into a horizontal (HL) and a vertical (LH) sub-band. In order to maintain the imperceptibility of the watermarked image, strength of the generated PN sequence pair is adjusted according to specified document to watermark ratio (DWR). For the extraction the watermark, statistical profile of DWT coefficients of watermarked image is determined and the obtained probability distribution function (pdf) is utilized for designing the watermark detection procedure. Proposed detector considers the best fitted Cauchy statistical model of heavy-tailed family, which accurately models the non-Gaussian DWT coefficients of an image. The robustness of the method is examined for various kinds of attacks with varying watermark to document ratio. Further, experimental results show that the proposed technique offer more robustness than other state-of-the-art method.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
In recent time, implementing e-Health solutions has become a trend amongst the various research groups across the world [8, 12]. The Information and communication technology (ICT) has been potentially useful for cost effective and speedy communication of electronic medical record (EMR) over open channels for e-Health applications [38]. However, electronic medical record (EMR) is widely communicated, stored and exchanged without any consideration of security [3, 11, 12, 23, 26, 30, 32, 37, 38]. In addition, identity theft related to medical is a growing and dangerous crime in the present time [8]. Therefore, the authenticity of the medical information and related images is of prime concern as they form the basis of inference for diagnostic purposes. To address these issues, potential researchers are using watermarking as a value added tools for data management and distribution in healthcare applications [8, 13, 14, 25, 26, 30, 32, 38]. Other interesting applications of digital watermarking are military, communication, privacy protection, identification, media file archiving, broadcast monitoring, remote education and insurance companies, secured E-voting systems, fingerprinting, real time audio/video, robotics, rightful ownership of identity card and digital cinema [38]. Most of the available watermarking techniques for healthcare applications are based on spatial domain [1, 4, 5, 10, 19], transform domain [8, 13, 14, 25, 28, 31,32,33, 39] or combination of both [2, 15, 18, 27, 34,35,36]. Recently, potential researchers are using robust and secure spread spectrum watermarking technique whereas the watermark information is embedding in a wavelet domain [18, 34,35,36]. However, wavelet coefficients of an image are non-Gaussian, such a Gaussian detector is neither robust nor optimal [29]. Therefore, modeling of host media becomes important for detection performance. In order to obtain a robust detector, a suitable technique is to treat the watermark detection as a statistical detection problem. Further, the binary hypothesis examination is formulated using a more accurate probability density function (pdf) of the coefficients of image.
In this paper, we present a watermarking technique applying secure spread-spectrum concept in wavelet domain where embedding strength is varied according a parameter called ‘watermark-to-document ratio (WDR)’ in order to ensure imperceptibility of the cover medical images. It is well established that spread-spectrum concept, popularly used as modulation scheme to provide secure communication over open channels. Further, the concept used in watermarking with the aim to achieved higher degree of security [38]. For the extraction of binary image watermark, statistical profile of DWT coefficients of watermarked image is determined and the obtained probability distribution function (pdf) is utilized for designing the watermark detection procedure using Cauchy statistical model of heavy-tailed family. The rest of the paper is organized as follows. Section 2 contains a brief preliminary on design of statistical watermark detector for medical images, Statistical modeling of wavelet coefficient, Likelihood- Ratio Test and Threshold determination for watermark detector. The proposed watermarking framework followed by watermark embedding and extraction algorithms is presented in Section 3. The results and analysis of the work is discussed in Section 4. Section 5 presents the conclusions of the proposed research.
2 Preliminaries
2.1 Design of statistical watermark detector for medical images
Although most of the watermarking schemes use different kinds of correlating detector for watermark detection, however their detection performances are generally not optimal [7, 29]. In facts, these detection methods do not take into account the actual statistical properties of the watermarked data. A statistical distribution is fully described by its pdf. Therefore, it becomes mandatory to obtain the best suitable pdf which closely models the DWT coefficients of the watermarked image.
2.2 Statistical modeling of wavelet coefficient
Recently, it is concluded by potential researchers, the histograms of wavelet coefficients have heavier tails and are more sharply peaked at zero than assumed by Gaussian distribution in the sub-band representation of medical images [16, 17, 22]. Further, the heavier-tailed characteristic of wavelet coefficients, the generalized student t-distribution is selected to model the statistics of sub-band coefficients of the selected medical image [16].
In view of above, we examine the appropriateness of long-tail distributions for statistical modeling of sub-band wavelet coefficients in a CT medical image. The chi-square goodness-of-fit test [6] is performed to recognize the most suitable fit. It compares a sample of data with identified statistical distribution. If the number of categories of data sample = N, observed frequency in each category = O, and expected frequency in corresponding category = E, then
The model with a lower chi-square value is a better fit. Chi-square values of 2nd level HL and LH sub-band wavelet coefficients are presented in Table 1. It can be observed from the table that Cauchy distribution provides the best statistical model for the sub-band DWT coefficients under consideration as the Chi-Square value for Cauchy distribution is the lowest amongst the considered long-tailed distributions. The pdf of Cauchy distribution is defined as [20]:
Here, the location parameter and shape parameter are −∞<δ<∞ and γ> 0, respectively.
The obtained best fitted Cauchy distribution pdf will be used in designing a nearly optimum watermark detector based on the binary hypothesis test.
2.3 Likelihood- ratio test (LRT)
In designing process, we assume that the watermark image does not change the distribution characteristics of cover image after embedding. With the help of the obtained statistical model, we can derive a watermark detector and the most widely-used approach in this direction is to construct a Likelihood- Ratio Test (LRT) [37].
Based on the embedding rule, we can formulate a two-sided parameter test
Given that Θ and α are known a-priori we can formulate a Neyman-Pearson (NP) detector to decide H1 if
where T denotes a detection threshold obtained by exploiting the NP criterion [21]. We obtain the LRT statistics for the Cauchy model (LRT-C) [7, 21]
2.4 Threshold determination for watermark detector
The Likelihood- Ratio Test detection statistics follow a Gaussian law with mean μ0 under H0 and mean μ1 under the alternative hypothesis [7, 21].
Detector Threshold is calculated as:
Where μ0 = variance and Pf = probability of false alarm. It can be defined as [21]:
Probability of false alarm is one of the important performance parameters, which determines the accuracy of statistical watermark detector.
3 Proposed method
In this paper, we present a watermarking algorithm using robust DWT and secure spread spectrum techniques with adaptive embedding strength. In the embedding of binary watermark, the cover medical image is decomposed by DWT using Mexican hat as mother wavelet. Mexican Hat provides better detection and localization of patches and gaps, which can be exploited well in case of medical images. Adding watermark into Mexican Hat DWT provides more robustness toward affine transforms. This wavelet has the advantage of better resolution for smoothly changing time series [38]. However, it is being computationally expensive to use than the Haar wavelets. The detail discussion of watermark embedding and extraction process is presented in subsection 3.1 and 3.2, respectively. The power of the PN-sequence pair is varied according to specified watermark to document to ratio (WDR) in order to maintain the imperceptibility of watermarked medical image. By defining WDR, we ensure that watermark do not suppress the cover image in any frequency band. This is achieved by varying the power of watermark according to cover image so that defined WDR remain maintained. This concept to set a watermark to document ratio to get the embedding strength of watermark introduced in [9].WDR is defined as:
Where, σx = Variance of cover image, σw = Variance ofwatermark image, W[k] = Wavelet coefficient ofWatermark Image, X[k] = Wavelet Coefficient of Cover Image.The embedding strength of ith level HL and HL subbands are represented as k1(i) and k2 (i) respectively. These values are claculated as:
where x(i) and y(i) is the PN Matrix.
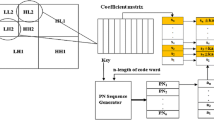
Figure 1 show the clear relation between eembedding strength and variance of subband DWT coefficients of the cover image (considered as document) for specified DWR values. It is evident that for a higher value of DWR, gives lower value of embedding strengh and vice-versa. The complete watermarking frame work is depicted in Fig. 2.
3.1 Watermark embedding process
The embedding algorithm for binary watermark is formulated as follows:
-
STEP 1: Read the cover image I (M, N) of size M × N.
-
STEP 2: Change the information into binary image D and rearrange it in one dimension (d = 1to n).
-
STEP 3: Calculate the second level sub-band coefficients cA2, cH2, cV2, cD2 after wavelet transform using Mexican hat as mother wavelet
-
STEP 4: Generate n number of PN-sequence pairs (PNh and PNv) size equals to number of rows in cH2 and cV2 with secret key and random number generator.
-
STEP 5:
Get the variance x(i) and y(i) of cH(i) and cV(i) respectively.
Get embedding strength k1(i) and k2(i) for given DWR as
-
STEP 6
ford = 1 to n,
ifmessage = 0,
then
if message = 1,
then
do
-
STEP 7: Take inverse“Mexican Hat” Wavelet transform to get watermarked image
3.2 Watermark extraction process
The extraction algorithm for binary watermark is formulated as follows:
-
STEP 1: Read the watermarked image I w (M, N)
-
STEP 2: Take the wavelet transform watermarked image using “Mexican hat” and get cA2, cH2, cV2, cD2 coefficients.
-
STEP 3: Generate 1’s sequences (msg) identical to message vector
-
STEP 4:
for i = 1 to n.
Generate n different PN-sequence pairs (PNh and PNv) Same secret key to reset the random number generator. Perform Cauchy modeling of wavelet coefficient and get the shape and location parameters γ, δ respectively.
Get the mean μ0and variance σ2 of LRT statistics.
Get the threshold Th_h(i) for Th_v(i) for cH2(i) and cV2(i) as
Once threshold (T) is being calculated decision is being made in favor of H1 or H0 corresponding to 1 or 0.
The Eq. (11) is termed as Likelihood Ratio test.
if
then
otherwise
-
STEP 5: Reshape this extracted bits to get the binary matrix which represent pixel values for watermarkimage.
-
STEP 6: Convert the matrix back to image to get the recovered watermark.
4 Experimental results performance analysis
Experiment has been carried out using 1024 × 1024 8 bit grey scale CT scan image cover image obtained from Medpix database [24]. A binary image of size 50 × 9is considered as watermark image as shown in Fig. 3a. Performance of the proposed variable gain watermarking scheme as well as the statistical watermark detector have been evaluated by considering suitable performance parameters such as PSNR, Correlation, WDR and probability of false alarm (pfa). PSNR between cover image and watermarked image and correlation between watermark and extracted watermark corresponding to different DWR is being represented in Table 2 corresponding to embedding at level 1 and level 2 wavelet decompositions. Referring this Table, the maximum PSNR value is obtained as 43.9986 dB for first level decomposition of DWT at WDR =20. However, minimum PSNR value is 33.1989 dB at WDR =10 for the same level of DWT decomposition. With reference to Table 2, it is further noticed that the maximum Correlation value is obtained as 0.9508 for first level decomposition of DWT at WDR =10 at. However, minimum Correlation value is 0.6871 at WDR =10 for the same level of DWT decomposition.
Figure 3b–f shows the extracted watermark corresponding to different DWR for embedding performed at first level sub-band decomposition. Figure 4a–e shows the extracted watermarks at second level wavelet decomposition. Table 3 shows the correlation between watermark image and extracted watermark image for given pfa. Tolerable pfa is fixed considering the degree of sensitivity of the watermark information. Extracted watermark at different false alarm probability is presented in Fig. 5. The perceptibility of watermarked image can be verified from Figs. 6 and 7 for level 1 and level 2 embedding of watermark, respectively. It is observed that no noticeable change occurs after the embedding.
Further, we have evaluated our algorithm against different attacks. Robustness of the watermark is analyzed against attacks like compression, JPEG compression, Gaussian noise, and salt & pepper noise for different quality factor. Table 4 shows the robustness of method for different attacks at gain = 6. With reference to this table, we observed that the NC value is 1 for Gaussian noise (mean = 0, var.-0.01), Poisson noise and Histogram Equalization. However, the minimum NC value is obtained by the proposed method is 0.4066 for JPEG compression, whereas Quality Factor (QF) =10. Furthermore, robustness of the proposed method has been compared with other recent reported techniques [35] for JPEG compression attack in Table 5. Referring this table it can be inferred that the NC values as obtained by proposed method vary in the range from 0.4066 to 0.9953. However, NC values as obtained by Singh et al. [35] vary in the range from 0.5306 to 0.7394. Further, it is observed that the method offered up to 34.60% enhancement in robustness over the method as reported in [35]. Robustness of the method for Gaussian and Salt & pepper noise is compared with Singh et al. [35] in Table 6. With reference to this table it is noticed that the maximum NC value has been obtainedby Singh et al. is 0.7391for Salt & pepper (density = 0.02) noise.However, proposed method obtained the maximum NC value is 0.9953for this attack. Further, the smallest NC value is obtained by the proposed method is 0.9256 for Gaussian noise (var =0.05). However, the smallest NC value obtained with [35] is 0.6944for the same attack. Referring this table it is observed that the method offered up to 36.33% enhancement in robustness over the method in [35]. The results indicate that the robustness of proposed method is better than the other similar existing technique [35].
5 Conclusion
In this paper, we presented a spread-spectrum based watermarking technique with adaptive watermarking capacity in wavelet transform domain for medical images. The binary watermark image was embedded into the selected sub-band of DWT using Mexican hat wavelet. For the extraction of the watermark, statistical profile of DWT coefficients of watermarked image was determined and it was observed that the Cauchy distribution provided the best fit for modeling the DWT coefficients of watermarked image. This obtained probability distribution function (pdf) was utilized for designing the watermark detection procedure. This proposed detector is considered the Cauchy statistical model of heavy-tailed family, which accurately models the non-Gaussian DWT coefficients of an image. The performance of the proposed technique was evaluated against attacks with varying watermark to document ratio (WDR). Experimental results have been demonstrated that the proposed technique is more robust than recent reported method. In addition, there are a few methods to determine the most suitable statistical model for any specified data set such as Kolmogorov- Smirnov test, Anderson–Darling test, Kuiper's test. An attractive feature of the chi-square goodness-of-fit test is that it can be applied to any univariate distribution for which the cumulative distribution function can be calculated. Correlation and security of the method can be improved further by using other extended PN sequences such as random sequence, maximal length sequence, gold sequence and Kasami sequence. Further, some more computationally efficient wavelet filters may be tries to improve the performance of proposed algorithm.
References
Agung BW Tjokorda, Adiwijaya, Permana FP (2012) Medical image watermarking with tamper detection and recovery using reversible watermarking with LSB modification and run length encoding (RLE) compression. In: Proc. of the 2012 International Conference on Communication, Networks and Satellite, Bali, pp. 167–171
Al-Haj A, Amer A (2014) Secured telemedicine using region-basedwatermarking with tamper localization. J Digit Imaging 2(6):737–750
Al-Qershi OM, Khoo BE (2010) ROI–based tamper detection and recovery for medical images using reversible watermarking technique. In: Proc of the IEEE International Conference on Information Theory and Information Security, Beijing, pp 151–155
Alsaade FW (2016) Watermarking system for the security of medical image databases used in telemedicine. Res J Inf Technol 8(3):88–97
Badshah G, Liew SC, Zain JM, Ali M (2016) Watermarking of ultrasound medical images in teleradiology using compressed watermark. Journal of Medical Imaging (Bellingham) 3(1):216–225
Balakrishnan N, Voinov V, Nikulin MS (2013) Chi-squared goodness of fit tests with applications. First Edition, Academic Press
Briassouli A, Tsakalides P, Stouraiti A (2005) Hidden messages in heavy-tails: DCT-domain Watermarkdetection using alpha-stable models. IEEE Trans Multimedia 7(4):700–715
Chauhan DS, Singh AK, Kumar B, Saini JP (2017) Quantization based multiple medical information watermarking for secure e-health, multimedia tools and applications, pp 1–13. https://doi.org/10.1007/s11042-017-4886-4
Eggers JJ, Girod B (2001) Quantization effects on digital watermarks. Signal Proc 81(2):239–263
Eswaraiah R, Reddy ES (2014) A fragile ROI-based medical image watermarking technique with tamper detection and recovery. In: Proc. of 2014 fourth international conference on communication systems and network technologies, Bhopal, pp 896–899
Eswaraiah R, Reddy ES (2015) Robust medical image watermarking technique for accurate detection of tampers inside region of interest and recovering original region of interest. IET Image Process 9(8):615–625
Giakoumaki A, Perakis K, Tagaris A, Koutsouris D (2006) Digital watermarking in telemedicine applications-towards enhanced data security and accessibility. In: Proc. of the 28th annual international Conference of the IEEE Engineering in Medicine and Biology Society, New York City, USA, pp 6328–6331
Giakoumaki A, Pavlopoulos S, Koutsouris D (2006) Secure and efficient health data management throughmultiple watermarking on medical images. Med Biol Eng Comput 44(8):619–631
Hajjaji MA, El-Bay B, Abdelali AB, Mtibaa A (2014) Combining Haar wavelet and Karhunen Loevetransforms for medical images watermarking. Biomed Res Int 2014:1–15, Article ID 313078
Kannammal A, Subha Rani S (2014) Two level security for medical imagesusing watermarking/encryption algorithms. Int J Imaging Syst Technol 24(1):111–120
Kaur L, Chauhan RC, Saxena SC (2005) Space- frequency quantiser design for ultrasound image compression based on minimum description length criterion. Med Biol Eng Comput 43(1):33–39
Kumar B, Singh SP, Mohan A, Anand A, Singh HV (2009) Statistical modelling of wavelet coefficients of ct scan image. In: Proc. of the International Conference on Emerging Trends in Electronic and Photonic Devices & Systems, Varanasi, India, pp 162–165
Kumar B, Singh HV, Singh SP, Mohan A (2011) Secure spread-spectrum watermarking for telemedicine applications. J Inf Secur 2(2):91–98
Kundu MK, Das S (2010) Lossless ROI medical image watermarking technique with enhanced security andhigh payload embedding. In: Proc. of the 20th International Conference On Pattern Recognition (ICPR), Istanbul, Turkey, pp 1457–1460
Kwitt R, Meerwald P, Uhl A (2008) A lightweight Rao-Cauchy detector for additive watermarking in the DWT-domain. In: Proc. of the 10th ACM workshop on multimedia and security, Oxford, UK, pp 33–41
Kwitt R, Meerwaldand P, Uhl A (2009) Efficient detection of additive watermarking in the DWT-domain. In: Proc. of the 17th European signal processing conference, Glasgow, UK, pp 2072–2076
Lam EY (2004) Statistical modelling of the wavelet coefficients with different bases and decomposition levels. IEE Proceedings - Vision, Image and Signal Processing 151(3):203–206
Masek J, Burget R, Karasek J, Uher V, Guney S (2013) Evolutionary improved object detector for ultrasound images. In: 36th International Conference on Telecommunications and Signal processing, Italy, pp 586–590
MedPix™Medical Image Database available at http://rad.usuhs.mil/medpix/medpix.html
Pandey R, Singh AK, Kumar B, Mohan A (2016) Iris based secure NROI multiple eye image watermarkingfor Teleophthalmology. Multimed Tools Appl 75(22):14381–14397
Pavelin A, Klapan I, Kovac M, Katic M, Stevanovic R, Rakic M, Klapan N (2006) A Functional telemedicine environment in the framework of the Croatian healthcare information system. In: Remote Cardiology Consultations Using Advanced Medical Technology Vol. 372, IOS press, pp 79–93
Priya S, Santhi B, Swaminathan P (2014) Study on medical image watermarkingTechniques. J Appl Sci 14(14):1638–1642
Priyanka, Maheshkar S (2017) Region-based hybrid medical image watermarking for secure telemedicine applications. Multimed Tools Appl 76(3):3617–3647
Rahman SMM, Ahmad MQ, Swamy MNS (2009) A new statistical detector for DWT-based additive image watermarking using the gauss–Hermite expansion. IEEE Trans Image Process 18(8):1782–1796
Rocek A, Slavicek K, Dostal O, Javornik M (2016) A new approach to fully-reversible watermarking in medical imaging with breakthrough visibility. Biomed Signal Process Control 29:44–52
Sharma A, Singh AK, Ghrera SP (2016) Robust and secure multiple watermarking technique for medical images. Wirel Pers Commun 92(4):1611–1624
Singh AK, Dave M, Mohan A (2015) Hybrid technique for robust and imperceptible multiple watermarkingusing medical images. Multimed Tools Appl 75(14):8381–8401
Singh AK, Dave M, Mohan A (2015) Robust and secure multiple watermarking in wavelet domain. Journal of Medical Imaging and Health Informatics 5(2):406–414
Singh AK, Dave M, Mohan A (2015) Multilevel encrypted text watermarking on medical images using spread-Spectrum in DWT domain. Wirel Pers Commun 83(3):2133–2150
Singh AK, Kumar B, Dave M, Mohan A (2015) Multiple watermarking on medical images using selective DWT coefficients. Journal of Medical Imaging and Health Informatics 5(3):607–614
Singh AK, Kumar B, Dave M, Mohan A (2015) Robust and imperceptible spread-Spectrum watermarking for telemedicine applications. Proc Natl Acad Sci, India, Sect A 85(2):295–301
Singh AK, Kumar B, Singh SK, Ghrera SP, Mohan A (2016) Multiple watermarking technique for securing online social network contents using back propagation neural network. Futur Gener Comput Syst:1–16. https://doi.org/10.1016/j.future.2016.11.023
Singh AK, Kumar B, Singh G, Mohan A (2017) Medical image watermarking: techniques and applications, book series on multimedia systems and applications, Springer, USA, ISBN: 978-3319576985
Zear A, Singh AK, Kumar P (2016) Multiple watermarking for healthcare applications. J Intell Syst. https://doi.org/10.1515/jisys-2016-0036
Acknowledgments
The Author’s are sincerely thankful to the potential/ anonymous reviewer’s for their critical comments and suggestions to improve the quality of the paper.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Chauhan, D.S., Singh, A.K., Adarsh, A. et al. Combining Mexican hat wavelet and spread spectrum for adaptive watermarking and its statistical detection using medical images. Multimed Tools Appl 78, 12647–12661 (2019). https://doi.org/10.1007/s11042-017-5348-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-5348-8