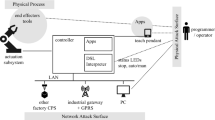
Abstract
The recent integration and collaboration of robots with networks expose new challenges and problems in terms of security. However, to the best of our knowledge, there has not been any comprehensive review of the vulnerabilities and attack surfaces of networked industrial robotic (NIR) systems under the framework of industrial control systems (ICS). Therefore, this paper provides an overview and further analysis of this field. We discuss the structure of the NIR systems in a modern factory, considering physical dynamics, control systems, and manufacturing networks, and then explore the vulnerabilities and the attack surface of this paradigm. Moreover, a new effort is that typical data integrity (DI) attacks that may cause serious robot equipment failures are elaborated in detail, which mainly achieves intrusion by tampering with the data of sensors or controllers through known or potential attack paths. In particular, the covert nature of several DI attacks is revealed. We analyze the existing anomaly detection strategies of the robot system and present numerical examples using dynamics-based control law to illustrate how adversaries achieve stealth to traditional detectors and the impact of the undermined robot system. Conclusively, a security framework integrating protective, detective, and responsive actions is proposed as a compensatory countermeasure for traditional methods against DI attacks. We believe that understanding these attacks and associated defense mechanisms will help accelerate the implementation of robot-based smart manufacturing technology.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Code Availibility
The code that supports the findings of this article is available from the corresponding author upon reasonable request.
References
Mello, R.C., Scheidegger, W.M., Múnera, M.C., Cifuentes, C.A., Ribeiro, M.R.N., Frizera-Neto, A., et al.: The poundcloud framework for ros-based cloud robotics: Case studies on autonomous navigation and human-robot interaction. Robot. Auton. Syst. 150, 103981 (2022)
Afrin, M., Jin, J., Rahman, A., Rahman, A., Wan, J., Hossain, E.: Resource allocation and service provisioning in multi-agent cloud robotics: A comprehensive survey. IEEE Communications Surveys & Tutorials 23(2), 842–870 (2021)
Khalid, A., Kirisci, P., Khan, Z.H., Ghrairi, Z., Thoben, K.D., Pannek, J.: Security framework for industrial collaborative robotic cyber-physical systems. Comput. Ind. 97, 132–145 (2018)
Bhardwaj, A., Avasthi, V., Goundar, S.: Cyber security attacks on robotic platforms. Netw. Secur. 2019(10), 13–19 (2019)
Kaspersky, I.C.S.: Threat landscape for industrial automation systems. Statistics for H 1, 2021 (2021)
Vilches, V.M., Kirschgens, L.A., Calvo, A.B., Cordero, A.H., Pisón, R.I., Vilches, D.M., Rosas, A.M., Mendia, G.O.,Juan, L.U.S., Ugarte, I.Z., Gil-Uriarte, E., et al.: Introducing the robot security framework (rsf), a standardized methodology to perform security assessments in robotics. arXiv preprint arXiv:1806.04042 (2018)
Mello, R.C., Scheidegger, W.M., Múnera, M.C., Cifuentes, C.A., Ribeiro, M.R.N., Frizera-Neto, A., et al.: The poundcloud framework for ros-based cloud robotics: Case studies on autonomous navigation and human-robot interaction. Robot. Auton. Syst. 150, 103981 (2022)
Rahman, A., Jin, J., Rahman, A., Cricenti, A., Afrin, M., Dong, Y.N.: Energy-efficient optimal task offloading in cloud networked multi-robot systems. Comput. Netw. 160, 11–32 (2019)
Galambos, P.: Cloud, fog, and mist computing: Advanced robot applications. IEEE Systems, Man, and Cybernetics Magazine. 6(1), 41–45 (2020)
Dieber, B., Breiling, B., Taurer, S., Kacianka, S., Rass, S., Schartner, P.: Security for the robot operating system. Robot. Auton. Syst. 98, 192–203 (2017)
Hochgeschwender, N., Cornelius, G., Voos, H.: Arguing security of autonomous robots. In 2019 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS), pages 7791–7797. IEEE (2019)
DeMarinis, N., Tellex, S., Kemerlis, V. P., Konidaris, G., Fonseca, R.: Scanning the internet for ros: A view of security in robotics research. In 2019 International Conference on Robotics and Automation (ICRA), pages 8514–8521. IEEE (2019)
Maggi, F., Quarta, D., Pogliani, M., Polino, M., Zanchettin, A. M., Zanero, S.: Rogue robots: Testing the limits of an industrial robots security. Trend Micro, Politecnico di Milano, Tech. Rep. pages 1–21 (2017)
Alshamrani, A., Myneni, S., Chowdhary, A., Huang, D.: A survey on advanced persistent threats: Techniques, solutions, challenges, and research opportunities. IEEE Communications Surveys Tutorials. 21(2), 1851–1877 (2019)
Butun, I., Österberg, P., Song, H.: Security of the internet of things: Vulnerabilities, attacks, and countermeasures. IEEE Communications Surveys Tutorials. 22(1), 616–644 (2019)
Tasooji, T. K., Khodadadi, S., Marquez, H. J.: Event-based secure consensus control for multirobot systems with cooperative localization against dos attacks. IEEE/ASME Transactions on Mechatronics. (2023)
Liang, H., Chang, Z., Pan, Y.: Dual-event-triggered intelligence security control for multi-agent systems against dos attacks with applications in mobile robot systems. IEEE Trans. Artif, Intell (2023)
Wang, X., Na, J., Niu, B., Zhao, X., Cheng, T., Zhou, W.: Event-triggered adaptive bipartite secure consensus asymptotic tracking control for nonlinear mass subject to dos attacks. IEEE Transactions on Automation Science and Engineering (2023)
Naha, Arunava, Teixeira, André, Ahlén, Anders, Dey, Subhrakanti: Sequential detection of replay attacks. IEEE Transactions on Automatic Control 68(3), 1941–1948 (2022)
Ramadan, Mohamad, Abdollahi, Farzaneh: An active approach for isolating replay attack from sensor faults. Eur. J. Control. 69, 100725 (2023)
Porter, M., Hespanhol, P., Aswani, A., Johnson-Roberson, M., Vasudevan, R.: Detecting generalized replay attacks via time-varying dynamic watermarking. IEEE Trans. Autom. Control. 66(8), 3502–3517 (2020)
Galambos, P.: Cloud, fog, and mist computing: Advanced robot applications. IEEE Systems, Man, and Cybernetics Magazine. 6(1), 41–45 (2020)
Huang, D., Shi, X., Zhang, W.A.: False data injection attack detection for industrial control systems based on both time-and frequency-domain analysis of sensor data. IEEE Internet Things J. 8(1), 585–595 (2020)
Wang, Y., Zhang, Z., Ma, J., Jin, Q.: Kfrnn: An effective false data injection attack detection in smart grid based on kalman filter and recurrent neural network. IEEE Internet Things J. 9(9), 6893–6904 (2021)
Sui, T., Mo, Y., Marelli, D., Sun, X., Fu, M.: The vulnerability of cyber-physical system under stealthy attacks. IEEE Trans. Autom. Control. 66(2),637–650 92020)
Wang, J., Lai, Y., Liu, J.: Stealthy attack detection method based on multi-feature long short-term memory prediction model. Futur. Gener. Comput. Syst. 137, 248–259 (2022)
Ferrari, P., Sisinni, E., Bellagente, P., Rinaldi, S., Pasetti, M., de Sá, A.O., Machado, R.C., Carmo, L.F.D.C., Casimiro, A.: Model-based stealth attack to networked control system based on real-time ethernet. IEEE Trans. Ind. Electron. 68(8), 7672–7683 (2020)
An, D., Zhang, F., Yang, Q., Zhang, C.: Data integrity attack in dynamic state estimation of smart grid: Attack model and countermeasures. IEEE Trans. Autom. Sci. Eng. 19(3), 1631–1644 (2022)
Guo, H., Sun, J., Pang, Z.H.: Stealthy false data injection attacks with resource constraints against multi-sensor estimation systems. ISA Trans. 127, 32–40 (2022)
Xu, Y., Deng, G., Zhang, T., Qiu, H., Bao, Y.: Novel denial-of-service attacks against cloud-based multi-robot systems. Inf. Sci. 576, 329–344 (2021)
Quarta, D., Pogliani, M., Polino, M., Maggi, F., Zanchettin, A. M., Zanero, S.: An experimental security analysis of an industrial robot controller. In 2017 IEEE Symposium on Security and Privacy (SP), pages 268–286. IEEE (2017)
Teixeira, A., Shames, I., Sandberg, H., Johansson, K.H.: A secure control framework for resource-limited adversaries. Automatica. 51, 135–148 (2015)
Pu, H., He, L., Cheng, P., Sun, M., Chen, J.: Security of industrial robots: Vulnerabilities, attacks, and mitigations. IEEE Netw. (2022)
Conti, M., Donadel, D., Turrin, F.: A survey on industrial control system testbeds and datasets for security research. IEEE Communications Surveys Tutorials. 23(4), 2248–2294 (2021)
Li, W., Xie, L., Wang, Z.: Two-loop covert attacks against constant value control of industrial control systems. IEEE Transactions on Industrial Informatics. 15(2), 663–676 (2018)
Makhdoom, I., Abolhasan, M., Lipman, J., Liu, R.P., Ni, W.: Anatomy of threats to the internet of things. IEEE Communications Surveys Tutorials. 21(2), 1636–1675 (2018)
Dong, Y., Gupta, N., Chopra, N.: False data injection attacks in bilateral teleoperation systems. IEEE Trans. Control Syst. Technol. 28(3), 1168–1176 (2019)
Kim, S., Park, K.J., Lu, C.: A survey on network security for cyber-physical systems: From threats to resilient design. IEEE Communications Surveys Tutorials. 24(3), 1534–1573 (2022)
Fang, C., Qi, Y., Cheng, P., Zheng, W.X.: Optimal periodic watermarking schedule for replay attack detection in cyber-physical systems. Automatica. 112, 108698 (2020)
Guo, H., Sun, J., Pang, Z.H.: Stealthy fdi attacks against networked control systems using two filters with an arbitrary gain. IEEE Transactions on Circuits and Systems II: Express Briefs. 69(7), 3219–3223 (2022)
Jurkat, A., Klump, R., Schneider, F.: Tracking the rise of robots: the ifr database. Jahrbücher für Nationalökonomie und Statistik. 242(5–6), 669–689 (2022)
Xue, T., Wang, W., Ma, J., Liu, W., Pan, Z., Han, M.: Progress and prospects of multimodal fusion methods in physical human-robot interaction: A review. IEEE Sensors J. 20(18), 10355–10370 (2020)
Lee, M.A., Zhu, Y., Zachares, P., Tan, M., Srinivasan, K., Savarese, S., Fei-Fei, L., Garg, A., Bohg, J.: Making sense of vision and touch: Learning multimodal representations for contact-rich tasks. IEEE Tran. Robot. 36(3), 582–596 (2020)
Tanwani, A. K., Mor, N., Kubiatowicz, J., Gonzalez, J. E., Goldberg, K.: A fog robotics approach to deep robot learning: Application to object recognition and grasp planning in surface decluttering. In 2019 international conference on robotics and automation (ICRA), pages 4559–4566. IEEE (2019)
Hu, L., Miao, Y., Wu, G., Hassan, M. M., Humar, I.: Irobot-factory: An intelligent robot factory based on cognitive manufacturing and edge computing. Futur. Gener. Comput, Syst. 90:569–577 (2019)
Pak, Y.J., Kong, Y.S., Ri, J.S.: Robust pid optimal tuning of a delta parallel robot based on a hybrid optimization algorithm of particle swarm optimization and differential evolution. Robotica. 41(4), 1159–1178 (2023)
Girbes-Juan, V., Schettino, V., Demiris, Y., Tornero, J.: Haptic and visual feedback assistance for dual-arm robot teleoperation in surface conditioning tasks. IEEE Trans. Haptics. 14(1), 44–56 (2020)
Wang, J., Zhu, Y., Qi, R., Zheng, X., Li, W.: Adaptive pid control of multi-dof industrial robot based on neural network. Journal of Ambient Intelligence and Humanized Computing. 11, 6249–6260 (2020)
Zhen, S., Ma, M., Liu, X., Chen, F., Zhao, H., Chen, Y.H.: Model-based robust control design and experimental validation of collaborative industrial robot system with uncertainty. Asian J. Control. 25(2), 1663–1674 (2023)
Guo, H., Pang, Z.H., Sun, J., Li, J.: An output-coding-based detection scheme against replay attacks in cyber-physical systems. IEEE Transactions on Circuits and Systems II: Express Briefs 68(10), 3306–3310 (2021)
Ghaderi, M., Gheitasi, K., Lucia, W.: A blended active detection strategy for false data injection attacks in cyber-physical systems. IEEE Trans. Control Netw. Syst. 8(1), 168–176 (2020)
Sui, T., Mo, Y., Marelli, D., Sun, X., Fu, M.: The vulnerability of cyber-physical system under stealthy attacks. IEEE Tran. Autom. Control. 66(2), 637–650 (2020)
Fu, Z., Pan, J., Spyrakos-Papastavridis, E., Lin, Y.H., Zhou, X., Chen, X., Dai, J.S.: A lie-theory-based dynamic parameter identification methodology for serial manipulators. IEEE/ASME Transactions on Mechatronics. 26(5), 2688–2699 (2020)
Lee, T., Wensing, P.M., Park, F.C.: Geometric robot dynamic identification: A convex programming approach. IEEE Trans. Robot. 36(2), 348–365 (2019)
Shao, X., Xie, L., Li, C., Li, Y.: Robot dynamics modeling with a novel friction model and extracted feasible parameters using constrained differential evolution. J. Intell. Robotic Syst. 108(1), 5 (2023)
Junejo, A.R., Gilal, N.U., Doh, J.: Physics-informed optimization of robust control system to enhance power efficiency of renewable energy: Application to wind turbine. Energy. 263, 125667 (2023)
Mukherjee, P., Santilli, M., Gasparri, A., Williams, R.K.: Distributed adaptive and resilient control of multi-robot systems with limited field of view interactions. IEEE Robot. Autom. Lett. 7(2), 5318–5325 (2022)
Alguliyev, R., Imamverdiyev, Y., Sukhostat, L.: Cyber-physical systems and their security issues. Comput. Ind. 100, 212–223 (2018)
Cook, Allan, Janicke, Helge, Smith, Richard, Maglaras, Leandros: The industrial control system cyber defence triage process. Comput. Secur. 70, 467–481 (2017)
Cao, K., Hu, S., Shi, Y., Colombo, A.W., Karnouskos, S., Li, X.: A survey on edge and edge-cloud computing assisted cyber-physical systems. IEEE Trans. Ind. Inf. 17(11), 7806–7819 (2021)
Mahmud, R., Kotagiri, R., Buyya, R.: Fog computing: A taxonomy, survey and future directions. Internet of Everything: Algorithms, Methodologies, Technologies and Perspectives. pages 103–130 (2018)
Rahman, A., Jin, J., Cricenti, A.L., Rahman, A., Kulkarni, A.: Communication-aware cloud robotic task offloading with on-demand mobility for smart factory maintenance. IEEE Trans. Ind. Inform. 15(5), 2500–2511 (2018)
Malik, A.W., Rahman, A.U., Ali, M., Santos, M.M.: Symbiotic robotics network for efficient task offloading in smart industry. IEEE Trans. Ind. Inform. 17(7), 4594–4601 (2020)
Bharti, S., McGibney, A.: Corol: a reliable framework for computation offloading in collaborative robots. IEEE Internet Things J. 9(19), 18195–18207 (2022)
Zhou, C., Hu, B., Shi, Y., Tian, Y.C., Li, X., Zhao, Y.: A unified architectural approach for cyberattack-resilient industrial control systems. Proc. IEEE. 109(4), 517–541 (2020)
Makarova, O., Lihota, M.: Simulation of computer attack scenarios for industrial robots from the point of intruder view. In 2021 Ural Symposium on Biomedical Engineering, Radioelectronics and Information Technology (USBEREIT), pages 0474–0477. IEEE (2021)
Munteanu, A., Muradore, R., Merro, M., Fiorini, P.: On cyber-physical attacks in bilateral teleoperation systems: An experimental analysis. In 2018 IEEE Industrial Cyber-Physical Systems (ICPS), pages 159–166. IEEE (2018)
Maggi, F., Balduzzi, M., Vosseler, R., Rösler, M., Quadrini, W., Tavola, G., Pogliani, M., Quarta, D., Zanero, S.: Smart factory security: A case study on a modular smart manufacturing system. Procedia Comput. Sci. 180, 666–675 (2021)
Lagraa, S., Cailac, M., Rivera, S., Beck, F., State, R.: Real-time attack detection on robot cameras: A self-driving car application. In 2019 Third IEEE International Conference on Robotic Computing (IRC), pages 102–109. IEEE (2019)
Eiza, M.H., Ni, Q.: Driving with sharks: Rethinking connected vehicles with vehicle cybersecurity. IEEE Veh. Technol. Mag. 12(2), 45–51 (2017)
Buerkle, A., Eaton, W., Al-Yacoub, A., Zimmer, M., Kinnell, P., Henshaw, M., Coombes, M., Chen, W.H., Lohse, N.: Towards industrial robots as a service (iraas): Flexibility, usability, safety and business models. Robot Comput-Integr Manuf. 81, 102484 (2023)
Hu, G., Tay, W.P., Wen, Y.: Cloud robotics: architecture, challenges and applications. IEEE Netw. 26(3), 21–28 (2012)
Mello, R.C., Scheidegger, W.M., Múnera, M.C., Cifuentes, C.A., Ribeiro, M.R., Frizera-Neto, A., et al.: The poundcloud framework for ros-based cloud robotics: Case studies on autonomous navigation and human-robot interaction. Robot. Auton. Syst. 150, 103981 (2022)
Ferrer, E. C., Hardjono, T., Pentland, A., Dorigo, M.: Secure and secret cooperation in robot swarms. Sci. Robot. 6(56), eabf1538 (2021)
Riazuelo, L., Tenorth, M., Di Marco, D., Salas, M., Gálvez-Löpez, D., Mösenlechner, L., Kunze, L., Beetz, M., Tardós, J.D., Montano, L., et al.: Roboearth semantic mapping: A cloud enabled knowledge-based approach. IEEE Trans. Autom. Sci. Eng. 12(2), 432–443 (2015)
Tenorth, M., Beetz, M.: Representations for robot knowledge in the knowrob framework. Artif. Intell. 247, 151–169 (2017)
Tian, N., Matl, M., Mahler, J., Zhou, Y.X., Staszak, S., Correa, C., Zheng, S., Li, Q., Zhang, R., Goldberg, K.: A cloud robot system using the dexterity network and berkeley robotics and automation as a service (brass). In 2017 IEEE International Conference on Robotics and Automation (ICRA). pages 1615–1622. IEEE (2017)
Beetz, M., Beßler, D., Haidu, A., Pomarlan, M., Bozcuoǧlu, A. K., Bartels, G.: Know rob 2.0a 2nd generation knowledge processing framework for cognition-enabled robotic agents. In 2018 IEEE International Conference on Robotics and Automation (ICRA), pages 512–519. IEEE (2018)
Tzafestas, S.G.: Synergy of iot and ai in modern society: The robotics and automation case. Robot. Autom. Eng. J. 31, 1–15 (2018)
Ayaida, M., Messai, N., Valentin, F., Marcheras, D.: Talkrobots: A middleware for robotic systems in industry 4.0. Futur. Internet. 14(4), 109 (2022)
Renganathan, V., Summers, T.: Spoof resilient coordination for distributed multi-robot systems. In 2017 International Symposium on Multi-Robot and Multi-Agent Systems (MRS), pages 135–141. IEEE (017)
Clark, G., Doran, M., Glisson, W.: A malicious attack on the machine learning policy of a robotic system. In 2018 17th IEEE International Conference On Trust, Security And Privacy In Computing And Communications/12th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE), pages 516–521. IEEE (2018)
Neshenko, N., Bou-Harb, E., Crichigno, J., Kaddoum, G., Ghani, N.: Demystifying iot security: an exhaustive survey on iot vulnerabilities and a first empirical look on internet-scale iot exploitations. IEEE Communications Surveys Tutorials. 21(3), 2702–2733 (2019)
Stellios, I., Kotzanikolaou, P., Psarakis, M., Alcaraz, C., Lopez, J.: A survey of iot-enabled cyberattacks: Assessing attack paths to critical infrastructures and services. IEEE Communications Surveys Tutorials. 20(4), 3453–3495 (2018)
Cottrell, K., Bose, D. B., Shahriar, H., Rahman, A.: An empirical study of vulnerabilities in robotics. In 2021 IEEE 45th Annual Computers, Software, and Applications Conference (COMPSAC). pages 735–744. IEEE (2021)
Zhou, Y., Xie, ., Pan, H.: Research on a pso-h-svm-based intrusion detection method for industrial robotic arms. Appl. Sci. 12(6), 2765 (2022)
Yaacoub, J. P. A., Noura, H. N., Salman, O., Chehab, A.: Robotics cyber security: Vulnerabilities, attacks, countermeasures, and recommendations. International Journal of Information Security. pages 1–44 (2022)
Li, L., Xie, L., Hao, B., Yang, L., Hu, T., Wang, Z.: Data logic attack on heavy-duty industrial manipulators. IEEE Access. 8, 17419–17433 (2020)
Zhang, W., Ma, Z., Wang, H., Deng, J., Li, P., Jia, Y., Dong, Y., Sha, H., Yan, F., Tu, W.: Study on automatic ultrasound scanning of lumbar spine and visualization system for path planning in lumbar puncture surgery. Math. Biosci. Eng. 20(1), 613–623 (2023)
Hollerer, S., Fischer, C., Brenner, B., Papa, M., Schlund, S., Kastner, W., Fabini, J., Zseby, T.: Cobot attack: a security assessment exemplified by a specific collaborative robot. Procedia Manuf. 54, 191–196 (2021)
Tariq, I., Sindhu, M.A., Abbasi, R.A., Khattak, A.S., Maqbool, O., Siddiqui, G.F.: Resolving cross-site scripting attacks through genetic algorithm and reinforcement learning. Expert Syst. Appl. 168, 114386 (2021)
Alsabbagh,W., Langendörfer, P.: A fully-blind false data injection on profinet i/o systems. In 2021 IEEE 30th International Symposium on Industrial Electronics (ISIE). pages 1–8. IEEE (2021)
Xiao, B., Yin, S.: Exponential tracking control of robotic manipulators with uncertain dynamics and kinematics. IEEE Trans. Ind. Inform. 15(2), 689–698 (2018)
Akpinar, K.O., Ozcelik, I.: Methodology to determine the device-level periodicity for anomaly detection in ethercat-based industrial control network. IEEE Trans. Netw. Serv. Manag. 18(2), 2308–2319 (2020)
Volkova, A., Niedermeier, M., Basmadjian, R., de Meer, H.: Security challenges in control network protocols: A survey. IEEE Communications Surveys Tutorials. 21(1), 619–639 (2018)
Gaz, C., Cognetti, M., Oliva, A., Giordano, P.R., De Luca, A.: Dynamic identification of the franka emika panda robot with retrieval of feasible parameters using penalty-based optimization. IEEE Robot. Autom. Lett. 4(4), 4147–4154 (2019)
Mishra, P., Varadharajan, V., Tupakula, U., Pilli, E.S.: A detailed investigation and analysis of using machine learning techniques for intrusion detection. IEEE communications surveys tutorials. 21(1), 686–728 (2018)
Abou El Kalam, A., Ferreira, A., Kratz, F.: Bilateral teleoperation system using qos and secure communication networks for telemedicine applications. IEEE Syst. J. 10(2):709–720 (2015)
Mahmoud, R., Yousuf, T., Aloul, F., Zualkernan, I.: Internet of things (iot) security: Current status, challenges and prospective measures. In 2015 10th international conference for internet technology and secured transactions (ICITST), pages 336–341. IEEE (2015)
Gammella, E., Buratti, P., Cairo, G., Recalcati, S.: The transferrin receptor: the cellular iron gate. Metallomics. 9(10), 1367–1375 (2017)
Raja, M. A. Z., Naz, H., Shoaib, M., Mehmood, A.: Design of backpropagated neurocomputing paradigm for stuxnet virus dynamics in control infrastructure. Neural Computing and Applications. pages 1–20 (2022)
Sami, S., Dai, Y., Tan, S. R. X., Roy, N., Han, J.: Spying with your robot vacuum cleaner: eavesdropping via lidar sensors. In Proceedings of the 18th Conference on Embedded Networked Sensor Systems. pages 354–367 (2020)
Bonaci, T., Herron, J., Yusuf, T., Yan, J., Kohno, T., Chizeck, H. J.: To make a robot secure: An experimental analysis of cyber security threats against teleoperated surgical robots. arXiv preprint arXiv:1504.04339. (2015)
Olivato, M., Cotugno, O., Brigato, L., Bloisi, D., Farinelli, A., Iocchi, L.: A comparative analysis on the use of autoencoders for robot security anomaly detection. In 2019 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS). pages 984–989. IEEE (2019)
Agrawal, N., Tapaswi, S.: Defense mechanisms against ddos attacks in a cloud computing environment: State-of-the-art and research challenges. IEEE Communications Surveys & Tutorials. 21(4), 3769–3795 (2019)
Ramanan, P., Li, D., Gebraeel, N.: Blockchain-based decentralized replay attack detection for large-scale power systems. IEEE Transactions on Systems, Man, and Cybernetics: Systems. 52(8), 4727–4739 (2021)
Li, D., Gebraeel, N., Paynabar, K.: Detection and differentiation of replay attack and equipment faults in scada systems. IEEE Trans. Autom. Sci. Eng. 18(4), 1626–1639 (2020)
Nisioti, A., Mylonas, A., Yoo, P.D., Katos, V.: From intrusion detection to attacker attribution: A comprehensive survey of unsupervised methods. IEEE Communications Surveys & Tutorials 20(4), 3369–3388 (2018)
de Sá, A.O., da Costa Carmo, L.F.R., Machado, R.C.: Covert attacks in cyber-physical control systems. IEEE Transactions on Industrial Informatics. 13(4), 1641–1651 (2017)
Pasetti, M., Ferrari, P., Bellagente, P., Sisinni, E., de Sá, A.O., do Prado, C.B., David, R.P., Machado, R.C.S.: Artificial neural network-based stealth attack on battery energy storage systems. IEEE Transactions on Smart Grid. 12(6):5310–5321 (2021)
Cheng, P., Yang, Z., Chen, J., Qi, Y., Shi, L.: An event-based stealthy attack on remote state estimation. IEEE Transactions on Automatic Control. 65(10), 4348–4355 (2019)
Sikder, A.K., Petracca, G., Aksu, H., Jaeger, T., Uluagac, A.S.: A survey on sensor-based threats and attacks to smart devices and applications. IEEE Communications Surveys & Tutorials. 23(2), 1125–1159 (2021)
Zhang, F., Kodituwakku, H.A.D.E., Hines, J.W., Coble, J.: Multilayer data-driven cyber-attack detection system for industrial control systems based on network, system, and process data. IEEE Transactions on Industrial Informatics. 15(7), 4362–4369 (2019)
Abduvaliyev, A., Pathan, A.S.K., Zhou, J., Roman, R., Wong, W.C.: On the vital areas of intrusion detection systems in wireless sensor networks. IEEE Communications Surveys & Tutorials. 15(3), 1223–1237 (2013)
Giraldo, J., Urbina, D., Cardenas, A., Valente, J., Faisal, M., Ruths, J., Tippenhauer, N.O., Sandberg, H., Candell, R.: A survey of physics-based attack detection in cyber-physical systems. ACM Computing Surveys (CSUR). 51(4), 1–36 (2018)
Ruan, J., Liang, G., Zhao, J., Qiu, J., Dong, Z.Y.: An inertia-based data recovery scheme for false data injection attack. IEEE Transactions on Industrial Informatics. 18(11), 7814–7823 (2022)
Pu, H., He, L., Zhao, C., Yau, D.K., Cheng, P., Chen, J.: Fingerprinting movements of industrial robots for replay attack detection. IEEE Transactions on Mobile Computing. 21(10), 3629–3643 (2021)
Ngamakeur, K., Yongchareon, S., Yu, J., Sheng, Q.Z.: Deep cnn-lstm network for indoor location estimation using analog signals of passive infrared sensors. IEEE Internet Things J. 9(22), 22582–22594 (2022)
Gao, Y., Liu, Y., Jin, Y., Chen, J., Wu, H.: A novel semi-supervised learning approach for network intrusion detection on cloud-based robotic system. IEEE Access. 6, 50927–50938 (2018)
Zhang, J., Pan, L., Han, Q.L., Chen, C., Wen, S., Xiang, Y.: Deep learning based attack detection for cyber-physical system cybersecurity: A survey. IEEE/CAA J. Autom. Sin. 9(3), 377–391 (2021)
Lou, X., Tran, C., Tan, R., Yau, D.K., Kalbarczyk, Z.T., Banerjee, A.K., Ganesh, P.: Assessing and mitigating impact of time delay attack: Case studies for power grid controls. IEEE Journal on Selected Areas in Communications. 38(1), 141–155 (2019)
Yu, Y., Zeng, X., Xue, X., Ma, J.: Lstm-based intrusion detection system for vanets: A time series classification approach to false message detection. IEEE Transactions on Intelligent Transportation Systems. 23(12), 23906–23918 (2022)
Jahromi, A.N., Karimipour, H., Dehghantanha, A., Choo, K.K.R.: Toward detection and attribution of cyber-attacks in iot-enabled cyber-physical systems. IEEE Internet Things J. 8(17), 13712–13722 (2021)
Qiao, Y., Wu, K., Jin, P.: Efficient anomaly detection for high-dimensional sensing data with one-class support vector machine. IEEE Transactions on Knowledge and Data Engineering. 35(1), 404–417 (2021)
Pu, Z., Cabrera, D., Bai, Y., Li, C.: A one-class generative adversarial detection framework for multifunctional fault diagnoses. IEEE Trans Ind. Electron. 69(8), 8411–8419 (2021)
Ding, D., Han, Q.L., Xiang, Y., Ge, X., Zhang, X.M.: A survey on security control and attack detection for industrial cyber-physical systems. Neurocomputing. 275, 1674–1683 (2018)
Qiao, F., Li, Z., Kong, Y.: A privacy-aware and incremental defense method against gan-based poisoning attack. IEEE Transactions on Computational Social Systems. (2023)
Khan, H.A., Sehatbakhsh, N., Nguyen, L.N., Callan, R.L., Yeredor, A., Prvulovic, M., Zajić, A.: Idea: Intrusion detection through electromagnetic-signal analysis for critical embedded and cyber-physical systems. IEEE Transactions on Dependable and Secure Computing. 18(3), 1150–1163 (2019)
Zhao, L., Li, W., Li, Y., et al.: Research on dual security control for a non-linear cps with multi-objective constraints under dos attack and actuator fault: An active-passive attack-tolerant approach. J. Control Sci. Eng. 2022 (2022)
Lin, C. Y., Wu, S. C., Kuo, P. H., Huang, M. J., Hong, S. W., Yau, H. T.: Application of chaotic encryption and decryption in wireless transmission from sensory toolholders on machine tools. IEEE Sensors Journal. (2023)
Wai, R.J., Muthusamy, R.: Fuzzy-neural-network inherited sliding-mode control for robot manipulator including actuator dynamics. IEEE Transactions on Neural Networks and learning systems. 24(2), 274–287 (2012)
Pang, Z.H., Fan, L.Z., Sun, J., Liu, K., Liu, G.P.: Detection of stealthy false data injection attacks against networked control systems via active data modification. Inf. Sci. 546, 192–205 (2021)
Lei, W., Pang, Z., Wen, H., Hou, W., Han, W.: Fdi attack detection at the edge of smart grids based on classification of predicted residuals. IEEE Transactions on Industrial Informatics. 18(12), 9302–9311 (2022)
Xie, C.H., Yang, G.H.: Observer-based attack-resilient control for linear systems against fdi attacks on communication links from controller to actuators. International Journal of Robust and Nonlinear Control. 28(15), 4382–4403 (2018)
Guo, L., Yu, H., Hao, F.: Optimal allocation of false data injection attacks for networked control systems with two communication channels. IEEE Trans. Control Netw. Syst. 8(1), 2–14 (2020)
Pang, Z.H., Liu, G.P., Zhou, D., Hou, F., Sun, D.: Two-channel false data injection attacks against output tracking control of networked systems. IEEE Transactions on Industrial Electronics. 63(5), 3242–3251 (2016)
Chen, S., Wu, Z., Christofides, P.D.: A cyber-secure control-detector architecture for nonlinear processes. AIChE J. 66(5), e16907 (2020)
Griffioen, P., Weerakkody, S., Sinopoli, B., Ozel, O., Mo, Y.: A tutorial on detecting security attacks on cyber-physical systems. In 2019 18th European Control Conference (ECC). pages 979–984. IEEE (2019)
Chen, Y., Kar, S., Moura, J.M.: Optimal attack strategies subject to detection constraints against cyber-physical systems. IEEE Trans. Control of Netw. Syst. 5(3), 1157–1168 (2017)
Conti, M., Donadel, D., Turrin, F.: A survey on industrial control system testbeds and datasets for security research. IEEE Communications Surveys & Tutorials. 23(4), 2248–2294 (2021)
Li, H., Gao, Y., Shi, P., Lam, H.K.: Observer-based fault detection for nonlinear systems with sensor fault and limited communication capacity. IEEE Transactions on Automatic Control. 61(9), 2745–2751 (2015)
Ramadan, M., Abdollahi, F.: An active approach for isolating replay attack from sensor faults. European Journal of Control. 69, 100725 (2023)
Cai, X.T., Li, W.D.: Partial encryption of feature-based product models for collaborative development. Robotics and Computer-Integrated Manufacturing. 63, 101918 (2020)
Cui, Y., Kara, S., Chan, K.C.: Manufacturing big data ecosystem: A systematic literature review. Robotics and computer-integrated Manufacturing. 62, 101861 (2020)
Fernández-Jiménez, F.J., Martínez-de Dios, J.R.: A robot-sensor network security architecture for monitoring applications. IEEE Internet of Things Journal. 9(8), 6288–6304 (2021)
Benkhelifa, E., Welsh, T., Hamouda, W.: A critical review of practices and challenges in intrusion detection systems for iot: Toward universal and resilient systems. IEEE communications surveys & tutorials. 20(4), 3496–3509 (2018)
Bang, A.O., Rao, U.P., Visconti, A., Brighente, A., Conti, M.: An iot inventory before deployment: a survey on iot protocols, communication technologies, vulnerabilities, attacks, and future research directions. Computers & Security. page 102914 (2022)
Guo, Z., Karimian, N., Tehranipoor, M.M., Forte, D.: Hardware security meets biometrics for the age of iot. In 2016 IEEE International Symposium on Circuits and Systems (ISCAS). pages 1318–1321. IEEE (2016)
Huang, L., Meng, Z., Deng, Z., Wang, C., Li, L., Zhao, G.: Toward verifying the user of motion-controlled robotic arm systems via the robot behavior. IEEE Internet of Things Journal. 9(22), 22422–22433 (2021)
Dhillon, P.K., Kalra, S.: A lightweight biometrics based remote user authentication scheme for iot services. Journal of Information Security and Applications. 34, 255–270 (2017)
Bhuyan, M.H., Bhattacharyya, D.K., Kalita, J.K.: Network anomaly detection: methods, systems and tools. Ieee communications surveys & tutorials. 16(1), 303–336 (2013)
An, D., Zhang, F., Cui, F., Yang, Q.: Toward data integrity attacks against distributed dynamic state estimation in smart grid. IEEE Transactions on Automation Science and Engineering. (2023)
Maushart, F., Prorok, A., Hsieh, M. A., Kumar, V.: Intrusion detection for stochastic task allocation in robot swarms. In 2017 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS). pages 1830–1837. IEEE (2017)
Sehatbakhsh, N., Nazari, A., Alam, M., Werner, F., Zhu, Y., Zajic, A., Prvulovic, M.: Remote: Robust external malware detection framework by using electromagnetic signals. IEEE Transactions on Computers. 69(3), 312–326 (2019)
Pu, H., He, L., Zhao, C., Yau, D. K., Cheng, P., Chen, J.: Detecting replay attacks against industrial robots via power fingerprinting. In Proceedings of the 18th Conference on Embedded Networked Sensor Systems. pages 285–297 (2020)
Weerakkody, S., Ozel, O., Sinopoli, B.: A bernoulli-gaussian physical watermark for detecting integrity attacks in control systems. In 2017 55th Annual Allerton Conference on Communication, Control, and Computing (Allerton). pages 966–973. IEEE (2017)
Kumar, R., Goyal, R.: On cloud security requirements, threats, vulnerabilities and countermeasures: A survey. Comput. Sci. Rev. 33, 1–48 (2019)
Wang, D., Huang, J., Tang, Y., Li, F.: A watermarking strategy against linear deception attacks on remote state estimation under k-l divergence. IEEE Transactions on Industrial Informatics. 17(5), 3273–3281 (2020)
Ma, L., Chu, Z., Yang, C., Wang, G., Dai, W.: Recursive watermarking-based transient covert attack detection for the industrial cps. IEEE Transactions on Information Forensics and Security. 18, 1709–1719 (2023)
Song, Z., Skuric, A., Ji, K.: A recursive watermark method for hard real-time industrial control system cyber-resilience enhancement. IEEE Transactions on Automation Science and Engineering 17(2), 1030–1043 (2020)
Volden, Ø., Solnør, P., Petrovic, S., Fossen, T.I.: Secure and efficient transmission of vision-based feedback control signals. Journal of Intelligent & Robotic Systems. 103(2), 26 (2021)
Salem, O., Alsubhi, K., Shaafi, A., Gheryani, M., Mehaoua, A., Boutaba, R.: Man-in-the-middle attack mitigation in internet of medical things. IEEE Transactions on Industrial Informatics. 18(3), 2053–2062 (2021)
Zhou, Y., Cao, Z., Dong, X., Zhou, J.: Bldss: A blockchain-based lightweight searchable data sharing scheme in vehicular social networks. IEEE Internet of Things Journal. (2022)
Teranishi, K., Shimada, N., Kogiso, K.: Development and examination of fog computing-based encrypted control system. IEEE Robotics and Automation Letters. 5(3), 4642–4648 (2020)
Wu, C., Yao, W., Luo, W., Pan, W., Sun, G., Xie, H., Wu, L.: A secure robot learning framework for cyber attack scheduling and countermeasure. IEEE Transactions on Robotics. (2023)
Keramat, F., Queralta, J. P., Westerlund, T.: Partition-tolerant and byzantine-tolerant decision-making for distributed robotic systems with iota and ros 2. IEEE Internet of Things Journal. (2023)
Paridari, K., OMahony, N., Mady, A.E.D., Chabukswar, R., Boubekeur, M., Sandberg, H.: A framework for attack-resilient industrial control systems: Attack detection and controller reconfiguration. Proceedings of the IEEE. 106(1), 113–128 (2017)
Sharpe, R., Van Lopik, K., Neal, A., Goodall, P., Conway, P.P., West, A.A.: An industrial evaluation of an industry 4.0 reference architecture demonstrating the need for the inclusion of security and human components. Computers in industry. 108:37–44 (2019)
Huang, H., He, W., Li, J., Xu, B., Yang, C., Zhang, W.: Disturbance observer-based fault-tolerant control for robotic systems with guaranteed prescribed performance. IEEE Transactions on Cybernetics. 52(2), 772–783 (2020)
Li, X.M., Zhou, Q., Li, P., Li, H., Lu, R.: Event-triggered consensus control for multi-agent systems against false data-injection attacks. IEEE transactions on cybernetics. 50(5), 1856–1866 (2019)
Zhao, Y., Du, X., Zhou, C., Tian, Y.C., Hu, X., Quevedo, D.E.: Adaptive resilient control of cyber-physical systems under actuator and sensor attacks. IEEE Transactions on Industrial Informatics. 18(5), 3203–3212 (2021)
Zhao, Y., Du, X., Zhou, C., Tian, Y.C.: Anti-saturation resilient control of cyber-physical systems under actuator attacks. Inf. Sci. 608, 1245–1260 (2022)
Alemzadeh, H., Chen, D., Li, X., Kesavadas, T., Kalbarczyk, Z.T., Iyer, R.K.: Targeted attacks on teleoperated surgical robots: Dynamic model-based detection and mitigation. In 2016 46th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN). pages 395–406. IEEE (2016)
Farivar, F., Haghighi, M.S., Jolfaei, A., Wen, S.: Covert attacks through adversarial learning: Study of lane keeping attacks on the safety of autonomous vehicles. IEEE/ASME Transactions on Mechatronics. 26(3), 1350–1357 (2021)
Zhou, L., Kumar, V.: Robust multi-robot active target tracking against sensing and communication attacks. IEEE Transactions on Robotics. (2023)
Funding
The research was supported by the National Key R &D program of China (Grant No. 2022YFB4703000).
Author information
Authors and Affiliations
Contributions
Xingmao, Shao: Conceptualization, Methodology, Writing-Original Draft; Lun Xie: Methodology, Supervision; Chiqin Li: Conceptualization; Zhiliang Wang: Supervision. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Ethics approval
Not applicable
Consent to participate
Not applicable
Consent for publication
Not applicable
Conflict of interest
Not applicable
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Shao, X., Xie, L., Li, C. et al. A Study on Networked Industrial Robots in Smart Manufacturing: Vulnerabilities, Data Integrity Attacks and Countermeasures. J Intell Robot Syst 109, 60 (2023). https://doi.org/10.1007/s10846-023-01984-2
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10846-023-01984-2