Abstract
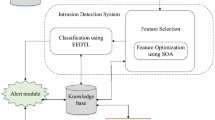
Cloud computing is the only technology available in today’s era that enables the end users or the consumers to use the cloud-based services deployed by the service providers with high on-demand availability, secure, as well as cost effectiveness in nature. This computing paradigm is surrounded by several attacks that prevents the service providers from providing their services and in turn hampers the trust of the end users. This paper aims to provide a network intrusion detection system based on enhanced deep learning framework that protects the cloud environment against the network level attacks. NSL-KDD dataset is used for training the neural network. The proposed approach performs the preprocessing of the NSL-KDD dataset by utilizing recursive feature elimination as the feature selection technique and there after the optimized dataset is trained over fully connected neural network in order to construct a deep learning-based classification model. The proposed approach computes output of the hidden neurons of the fully connected neural network by ReLU activation function whereas the Sigmoid activation function is used on the output layer. Adam optimizer is used for reducing the loss in terms of actual and the expected output. The result thus obtained by the proposed NIDS clearly depicts the enhanced accuracy for attack classification and reduction in false positive rate at the same time increase in true positive rate.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Alouffi B, Hasnain M, Alharbi A, Alosaimi W, Alyami H, Ayaz M (2021) A systematic literature review on cloud computing security: threats and mitigation strategies. IEEE Access 9:57792–57807
George SS, Pramila RS (2021) A review of different techniques in cloud computing. Mater Today: Proc 46(17):8002–8008
Attaran M, Woods J (2019) Cloud computing technology: improving small business performance using the Internet. J Small Bus Entrep 31(6):94–106
Dwivedi RK, Saran M, Kumar R (2019) A survey on security over sensor-cloud. In: 2019 International conference on confluence the next generation information technology summit (confluence), IEEE
Saran M, Tripathi UN (2021) A comprehensive review of threats, risks, attacks and secure defence mechanisms in cloud computing. J Xi’an Univ Architect Technol 13(7):674–682
Saran M, Yadav RK, Tripathi UN (2022) Machine learning based security for cloud computing: a survey. Int J Appl Eng Res 17(4):332–337
Saran M, Yadav RK, Tripathi UN, Mitigation from DDoS attack in cloud computing using Bayesian hyperparameter optimization based machine learning approach. Int J Res Trends Innov 7(11)
Tang TA, Mhamdi L, McLernon D, Zaidi SAR, Ghogho M (2016) Deep learning approach for network intrusion detection in software defined networking. In: 2016 International conference on wireless networks and mobile communications (WINCOM), IEEE, pp 258–263
Zhou L, Ouyang X, Ying H, Han L, Cheng Y, Zhang T (2018) Cyber-attack classification in smart grid via deep neural network. In: Proceedings of the 2nd international conference on computer science and application engineering, ACM. 2018, p 90
Feng F, Liu X, Yong B, Zhou R, Zhou Q (2019) Anomaly detection in ad-hoc net- works based on deep learning model: a plug and play device. Ad Hoc Netw 84:84–89
Kim J, Shin N, Jo SY, Kim SH (2017) Method of intrusion detection using deep neural network. In: 2017 IEEE international conference on Big Data and smart computing (BigComp). IEEE
Kasongo SM, Sun Y (2019) A deep learning method with filter based feature engineering for wireless intrusion detection system. IEEE Access 7:38597–38607
Kim J, Kim J, Thu HLT, Kim H (2016) Long short term memory recurrent neural network classifier for intrusion detection. In: 2016 International conference on platform technology and service (PlatCon). IEEE, pp 1–5
Taylor A, Leblanc S, Japkowicz N (2016) Anomaly detection in automobile control network data with long short-term memory networks. In: 2016 IEEE International conference on data science and advanced analytics (DSAA). IEEE, pp 130–139
Yin C, Zhu Y, Fei J, He X (2017) A deep learning approach for intrusion detection using recurrent neural networks. IEEE Access 5:21954–21961
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Saran, M., Singh, R.K. (2023). Network Intrusion Detection System for Cloud Computing Security Using Deep Neural Network Framework. In: Tripathi, A.K., Anand, D., Nagar, A.K. (eds) Proceedings of World Conference on Artificial Intelligence: Advances and Applications. WWCA 1997. Algorithms for Intelligent Systems. Springer, Singapore. https://doi.org/10.1007/978-981-99-5881-8_30
Download citation
DOI: https://doi.org/10.1007/978-981-99-5881-8_30
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-99-5880-1
Online ISBN: 978-981-99-5881-8
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)