Abstract
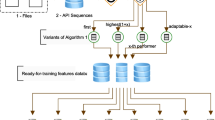
Malicious software attacks are increasing every day despite so many preventive measures, and many detection mechanisms are available in the literature. Most of the detection mechanisms use either static or dynamic attributes of the malicious and legitimate samples with machine learning classification methods to distinguish malware from benignware. In this article, the static and dynamic features are joined to prepare a hybrid feature set which is used with machine learning algorithms for classification. The operation code sequences of samples are extracted through static analysis, and API call sequences are extracted through dynamic analysis. Both the feature vectors are joined to form a hybrid feature set which is then passed through three machine learning algorithms for experimental evaluation. Hybrid feature set has achieved higher accuracy and low error rate in comparison with the static and dynamic datasets when used individually with all the selected algorithms.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
AV-TEST Page. https://www.av-test.org/en/statistics/malware/. Last accessed 24 Dec 2021
Igor S, Felix B, Xabier UP, Pablo GB (2013) Opcode sequences as representation of executables for data-mining-based unknown malware detection. Inf Sci 231:64–82
Ding Y, Dai W, Yan S, Zhang Y (2014) Control flow-based opcode behavior analysis for malware detection. In: Computers & security. Elsevier, pp 1–10
O’kane P, Sezer S, McLaughlin K (2016) Detecting obfuscated malware using reduced opcode set and optimised runtime trace. Secur Inform 5:2
Zhang J, Qin Z, Yin H, Ou L, Hu Y (2016) IRMD: malware variant detection using opcode image recognition. In: Proceedings of 22nd international conference on parallel and distributed systems. IEEE, pp 1175–1180
Wang T, Xu N (2017) Malware variants detection based on opcode image recognition in small training. In: 2nd international conference proceedings on cloud computing and big data analysis. IEEE, pp 328–332
Alqurashi S et al (2017) A comparison between API call sequences and opcode sequences as reflectors of malware behavior. In: Proceedings of the 12th international conference for internet technology and secured transactions. IEEE, pp 105–110
Ki Y, Kim E, Kim HK (2015) A novel approach to detect malware based on API call sequence analysis. Int J Distrib Sens Netw 2015(6):1–9
Fan CI, Hsiao HW, Chou CH, Tseng YF (2015) Malware detection systems based on API log data mining. In: Proceedings of international computer software and applications conference. IEEE, pp 255–260
Liu J, Wang Y, Wang Y (2017) Inferring phylogenetic networks of malware families from API sequences. In: Proceedings of international conference on cyber-enabled distributed computing and knowledge discovery. IEEE, pp 14–17
Ma X, Guo S, Bai W, Chen J, Xia S, Pan Z (2019) An API semantics-aware malware detection method based on deep learning. Secur Commun Netw 2019
Amer E, Zelinka I (2020) A dynamic windows malware detection and prediction method based on contextual understanding of API call sequence. Comput Secur 92
Alazab M, Alazab M, Shalaginov A, Mesleh A, Awajan A (2020) Intelligent mobile malware detection using permission requests and API calls. Futur Gener Comput Syst 107:509–521
Shijo PV, Salim A (2015) Integrated static and dynamic analysis for malware detection. In: Proceedings of the international conference on information and communication technologies, vol 46. Elsevier, Kochi, pp 804–811
Santos I, Devesa J, Brezo F, Nieves J, Bringas PG (2013) OPEM: a static-dynamic approach for machine-learning-based malware detection. In: Herrero Á et al (eds) International joint conference CISIS’12-ICEUTE’12-SOCO’12 special sessions. Advances in intelligent systems and computing, vol 189. Springer, Berlin, Heidelberg
Su M, Chang J, Fung K (2017) Machine learning on merging static and dynamic features to identify malicious mobile apps. In: Proceedings of ninth international conference on ubiquitous and future networks. IEEE, pp 863–867
Wang Y, Cai W, Lyu P, Shao W (2018) A combined static and dynamic analysis approach to detect malicious browser extensions. Secur Commun Netw
Maryam A, Ahmed U, Aleem M, Lin JC-W, Islam MA, Iqbal MA (2020) cHybriDroid: a machine learning-based hybrid technique for securing the edge computing. Secur Commun Netw
Li Z, Li W, Lin F et al (2020) Hybrid malware detection approach with feedback-directed machine learning. Sci China Inf Sci 63
Samantray OP, Tripathy SN (2021) An opcode-based malware detection model using supervised learning algorithms. Int J Inf Secur Privacy (IJISP) 15(4):18–30
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Samantray, O.P., Tripathy, S.N. (2023). An Efficient Hybrid Approach for Malware Detection Using Frequent Opcodes and API Call Sequences. In: Shukla, A., Murthy, B.K., Hasteer, N., Van Belle, JP. (eds) Computational Intelligence. Lecture Notes in Electrical Engineering, vol 968. Springer, Singapore. https://doi.org/10.1007/978-981-19-7346-8_63
Download citation
DOI: https://doi.org/10.1007/978-981-19-7346-8_63
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-19-7345-1
Online ISBN: 978-981-19-7346-8
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)