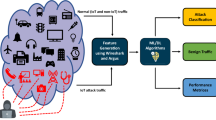
Abstract
Internet of things is enabling the world to become smarter and more amendable, and it connects the digital and physical worlds together. The Internet of things relies on resource-limited devices ranging from domestic appliances to personal devices. There is an ever-increasing number of device connected to the Internet every day that attract the attention of hackers. Adversaries deploy a range of advanced persistent threat (APT) strategies to successfully compromise these systems, one of which is the botnet attack. The IoT is potentially vulnerable to attacks launched by intelligent botnets, since these botnets detect network weaknesses and exploit them for the launch of different attacks similar to DDoS attacks. In order to provide efficient security against botnet attack to the IoT devices and network, several methods have emerged; recent and most effective mechanism is a deep learning mechanism. Our paper reviewed the security threats in IoT and several existing deep learning approaches to address the detection of botnets in the IoT environment. Furthermore, we also investigated the attack class, datasets, merits and demerits of existing deep learning approaches.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Novo O, Beijar N, Ocak M et al (2015) Capillary networks—Bridging the cellular and IoT worlds. In: Proceedings of IEEE world forum Internet things, WF-IoT 2015, pp 571–578. https://doi.org/10.1109/WF-IoT.2015.7389117.
Al-Fuqaha A, Guizani M, Mohammadi M et al (2015) Internet of Things: a survey on enabling technologies, protocols, and applications. IEEE Commun Surv Tutor 17(4):2347–2376. https://doi.org/10.1109/COMST.2015.2444095
Karbab EMB, Debbabi M, Derhab A, Mouheb D (2018) MalDozer: Automatic framework for android malware detection using deep learning. DFRWS 2018 EU—Proceedings of 5th annual DFRWS Europe, vol 24, pp S48–S59. https://doi.org/10.1016/j.diin.2018.01.007
Hussain F, Hussain R, Hassan SA, Hossain E (2020) Machine learning in IoT security: current solutions and future challenges. IEEE Commun Surv Tutor 22(3):1686–1721. https://doi.org/10.1109/COMST.2020.2986444
Antonakakis et al (2017) Understanding the Mirai Botnet, 26th USENIX security symposium (USENIX security 17), pp 1093–1110, Aug 2017. ISBN 978-1-931971-40-9
Popoola SI, Adebisi B, Hammoudeh M, Gui G, Gacanin H (2021) Hybrid deep learning for botnet attack detection in the internet-of-Things networks. IEEE Internet Things J 8(6):4944–4956. https://doi.org/10.1109/JIOT.2020.3034156
Ghafir et al (2018) Detection of advanced persistent threat using machine-learning correlation analysis. Futur Gener Comput Syst 89:349–359. https://doi.org/10.1016/j.future.2018.06.055
Koroniotis N, Moustafa N, Sitnikova E (2019) Forensics and deep learning mechanisms for botnets in Internet of Things: a survey of challenges and solutions. IEEE Access 7:61764–61785. https://doi.org/10.1109/ACCESS.2019.2916717
Yaacoub JPA, Noura M, Noura HN, Salman O, Yaacoub E, Couturier R, Chehab (2020) Securing internet of medical things systems: limitations, issues and recommendations, Futur Gener Comput Syst 105:581–606. https://doi.org/10.1016/j.future.2019.12.028
Jyotsna M, Gabhane P, Shradha Thakare M, Craig M (2017) Smart homes system using internet-of-things: issues, solutions and recent research directions. Int Res J Eng Technol 04(05). e-ISSN 2395-0056. Available: www.irjet.net
Domb M (2019) Smart home systems based on Internet of Things. IntechOpen, Chapter 65877
Vinayakumar R, Alazab M, Srinivasan S, Pham QV, Padannayil SK, Simran K (2020) A visualized botnet detection system based deep learning for the Internet of Things networks of smart cities. IEEE Trans Ind Appl 56(4):4436–4456. https://doi.org/10.1109/TIA.2020.2971952
Dirks S, Keeling M (2009) A vision of smarter cities. IBM Global Services, New York, pp 1–20
Ayaz M, Ammad-Uddin M, Sharif Z, Mansour A, Aggoune EHM (2019) Internet-of-Things (IoT)-based smart agriculture: toward making the fields talk. IEEE Access 7:129551–129583. https://doi.org/10.1109/ACCESS.2019.2932609
Farooq MS, Riaz S, Abid A, Umer T, Zikria YB (2020) Role of IoT technology in agriculture: a systematic literature review. Electronics 9(2). https://doi.org/10.3390/electronics9020319
Qureshi S, He J, Tunio S, Zhu N, Akhtar F, Ullah F, Nazir A, Wajahat A (2021) A hybrid DL-based detection mechanism for cyber threats in secure networks. IEEE Access 9:73938–73947. https://doi.org/10.1109/ACCESS.2021.3081069
De La Torre Parra G, Rad P, Choo KKR, Beebe N (2020) Detecting Internet of Things attacks using distributed deep learning. J Netw Comput Appl 163. https://doi.org/10.1016/j.jnca.2020.102662
Jung W, Zhao H, Sun M, Zhou G (2020) IoT botnet detection via power consumption modeling. Sciencedirect Smart Health 15. https://doi.org/10.1016/j.smhl.2019.100103
Moti Z, Hashemi S, Karimipour H (2021) Generative adversarial network to detect unseen Internet of Things malware. Ad Hoc Netw. https://doi.org/10.1016/j.adhoc.2021.102591
Popoola SI, Adebisi B, Hammoudeh M, Gacanin H, Gui G (2021) Stacked recurrent neural network for botnet detection in smart homes. Comput Electr Eng 92. https://doi.org/10.1016/j.compeleceng.2021.107039
Randhawa RH, Aslam N, Alauthman M, Rafiq H, Comeau F (2021) Security hardening of botnet detectors using generative adversarial networks. IEEE Access 9:78276–78292. https://doi.org/10.1109/ACCESS.2021.3083421
Manimurugan S, Al-Mutairi S, Aborokbah MM, Chilamkurti N, Ganesan S, Patan R (2020) Effective attack detection in internet of medical things smart environment using a deep belief neural network. IEEE Access 8:77396–77404. https://doi.org/10.1109/ACCESS.2020.2986013
Shareena J, Ramdas A, Haripriya AP (2021) Intrusion detection system for IOT botnet attacks using deep learning. SN Comput Sci 2(3). https://doi.org/10.1007/s42979-021-00516-9
Panda M, Mousa AAA, Hassanien AE (2021) Developing an efficient feature engineering and machine learning model for detecting IoT-botnet cyber attacks. IEEE Access 9:91038–91052. https://doi.org/10.1109/ACCESS.2021.3092054
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Sakthipriya, N., Govindasamy, V., Akila, V. (2023). Review of Deep Learning Approaches for IoT Botnet Detection. In: Kumar, S., Hiranwal, S., Purohit, S.D., Prasad, M. (eds) Proceedings of International Conference on Communication and Computational Technologies . Algorithms for Intelligent Systems. Springer, Singapore. https://doi.org/10.1007/978-981-19-3951-8_40
Download citation
DOI: https://doi.org/10.1007/978-981-19-3951-8_40
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-19-3950-1
Online ISBN: 978-981-19-3951-8
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)