Abstract
As a biometric trademark, finger vein established-based technology is exceptionally right for persona clear attestation with high security. The vibe of an individual or lady ID shape is mounted on near infrared (NIR) finger vein. The proposed self-flexible illuminance control test introduced an information mannequin of finger vein imaging and activated into photograph guaranteeing about gear. As considered with the assistance of methods for the circulation of pixels profundity of the gained picture, the proposed figuring may also pick to generally trade the illuminance improvement of lighting. Builds up the illuminance of lights beneath which the thicker bit of the finger constitution is brought and decreases the illuminance of lights beneath which the thin upper bit of the finger body is presented. With this change, the total finger physical makeup ought to be lit up fittingly as respected by method for its thickness transport, and along these lines, the overexposure and underexposure are saved as an unprecedented essential course from suitably. A NIR finger vein picture database containing 2040 photographs is made starting at now. Inside the photograph pre-overseeing arrange, Gabor channels are used to redesign got foul finger vein pictures. Inside the paper, the distinct insistence introduction of the proposed structure is outlined utilizing the revelation cost and, subsequently, the edge task. A despairing depiction-based estimation is utilized to figure the affirmation cost and offers information to situate evaluation. The suggestions show the ampleness of the proposed illuminance control comprises of, and in this way. The whole finger vein system is mainly based on individual irrefutable affirmation.
Access provided by Autonomous University of Puebla. Download chapter PDF
Similar content being viewed by others
Keywords
12.1 Introduction
The biometric-embedded architecture might be a mix of biomedical instruments and software programmed acclimated with achieving single task inside a given significant measure, over but then again and on and on, with or excepting coordinated human efforts—introduced a course of action of a system that screens and respond to oversee an external area. A condition related to the architecture through sensors, actuators, and various realities yields interfaces. Embedded structures must meet arranging and uncommon hindrances constrained on that with the assistance of the planet. Biometrics suggests the conspicuous evidence of people through their traits or characteristics (Bracken 2020; Vega et al. 2014). Biometrics is utilized in programming designing as a recognizing verification and access control. It is also acclimated to capture people in packs that are underneath perception. Biometric identifiers are the undeniable, quantifiable attributes acclimated with recognizing and portray individuals (Suresh Kumar et al. 2021). Biometric identifiers are consistently requested as physiological versus social qualities established system which might be a mix of medications and programming (Samuel et al. 2021). It is used to achieve a single task within a given period, aside from joint human efforts. RTOS portrays the methodology for the structure works.
The microcontroller might be a significantly organized chip that contains all the portions, including the controller (Narmadha et al. 2020). It pleasantly is likewise distributed by utilizing consolidating more prominent limits into the CPU chip. Biometrics is utilized to get a handle on the properties of people (Xie et al. 2017). Competitive Gabor response (CGR) data packages include a Gabor filter bank with a range of orientation strengths and magnitudes, as well as information about each bank’s peak responses. The authors create a histogram by concatenating the CGM and CGO images for a given image and combining it with the HOGC histogram (HCGR) image (Lu et al. 2014). To overcome the issues, we used a spread of sensors in an exceedingly multi-biometric system. Finger vein might be a biometric approval structure that organizes the vascular occurrence in an exceedingly individual's finger to the late obtained data.
12.2 Related Works
Shende and Dandwate introduced convolutional neural network-based multimodal biometric human authentication in 2020 (Shende and Dandwate 2020). Face, palm veins, and fingerprint channel parts, a single-pixel string, a maximum pooling window size of 2 × 2, and six-channel bits are used for multimodal biometric human authentication. The structure’s presentation is evaluated using a database of faces, palm veins, and top gravings organized by actual percentage (Thiruvikraman et al. 2021). Yong et al. investigated the finger vein pattern recognition technology in conjunction with an FPGA (Yong 2020). As with the other type of biometric affirmation development, the cutting-edge case of the finger vein affirmation has enlisted and confirmed the impediment of average speed. As a result, a finger vein spotlight extraction and planning affirmation computation suitable for FPGA is proposed. The apparatus relationship for finger vein affirmation is organized and completed using three modules: finger vein image ensuring the device, photograph supervising module, and planning show module. Finally, critical estimation is acted out and examined, which expedites the enrollment and validation of cellphone veins (Kumar et al. 2021). Madhusudhan et al. published an article on finger vein-based authentication using deep learning techniques in 2020 as security is one of the significant concerns of recent times (Madhusudhan et al. 2019). Biometric-based techniques are considered as powerfully stable and cautious in confirming a private. Hand-based biometric includes at long last wind up being suitably open all through data assortment. The authors dealt with and getting prepared biometric trademark photographs of the vast number of vendors. It is used to take a look into for more noteworthy affiliations. Critical taking in systems acts as the legend from such conditions. At present, prescribe a one-of-a-kind way of thinking for endorsement of the work of finger vein pictures. They utilized an entire convolutional neural system (CNN) to travel learning. The mannequin has been pre-masterminded on various photographs open on the ImageNet database through ResNet-50 arrangements (Revathy et al. 2019). In 2020, El Mehdi Cherrat and Bouzahir conveyed a convolutional neural systems strategy for multimodal biometric ID shape utilizing the combo of a mind-blowing engrave, finger vein, and face pictures (El mehdi Cherrat and Bouzahir 2020). The basic idea behind this paper is to support a crossbreed course of movement of joining the effect of ground-breaking tree models: Convolutional neural structure (CNN), softmax, and random backwoods (RF) classifier issue to multi-biometric finger impression, finger vein, and face-perceiving check framework (Kumar et al. 2020). In 2019, Shaveta Dargon et al. introduced a detailed report on application-shaped biometric confirmation frameworks based on expert physiological and social modalities (Dargan and Kumar 2020). The Authors explored a kind of contraction for biometric innovations based on social finger effect and finger vein plans, which provides well-being and revocability format (Hwang and Park 2018). The multi-biometric form depended on focal points based on modern engraving aspects and picture-based finger vein elements, and along these lines, the portion stage blend inclinations are used to upgrade protection consistency. Their recommendation of enhanced partial-discrete cosine transform (EP-DFT) depended on a non-invertible exchange, giving the buyer an agreeable and vital improvement in protection. Matsuda et al. suggested a finger vein approach biometric interface configuration. They introduced one-of-a-kind picking up knowledge on a technique that is known as DBC (Matsuda et al. 2016). The approach integrated the required relation map to use the grandeur in twofold organizations to manage vein attributes. Using synchronized data and SVM, DBC was seen to be cut off and shorter besides. The PolyU database and MLA database were selected and successfully executed (Sasireka and Rajesh 2014; Abitha et al. 2020). Wang et al. presented a solid and fruitful structure for one in everything about structure engrave attestation on an essential level for asset restricted applications (Xiang et al. 2016). It depended upon the midway Hadamard exchange strategy for the masterminding of cancelable one in everything about structure finger sway plans. This framework depended upon the cancelable one in everything about structure finger influence codecs and stochastic segment remodels that gave revocability, top of the line arrangement, non-invertibility, and execution and affirmed high-caliber as separated and condition of convincing work of art. Qiu et al. suggested another biometric shape finger vein procedure to trigger concern to pseudo indirect transformers and double window constraints (Qiu et al. 2017). Here, planar imaging and double windows contributed to the pixelation of the finger and the finger venous situation. The authors proposed a one-of-a-kind one-in everything about kind engraving-based attestation structure and affirmation invent that relies upon the tempestuous encryption by method for utilizing Murillo-Escobar’s be tallied and the contraption legitimately. They utilized a 32-piece microcontroller for secure endorsement frameworks and inserted pro structures, and introduced a hard and fast security evaluation at every client and real level. A severe review of the engraving assertion framework with different applications is done. For instance, mental attacker prominent affirmation, hoodlum evaluation, and other firmly shut parts of the beneficial execution of unique finger impact biometric structure, a first-class good incredible engraving picture are required (Pakutharivu and Srinath 2017). A face-biometric authentication gadget (ASM) model and principal component analysis (PCA) methods were introduced by Yim et al. (2015), who obtained a facial model (Yim et al. 2015). AdaBoost and histogram equalization (HE) techniques were used to enhance the picture’s understanding. The radial basis function neural network proved to be adequate proof in the test. By employing differential evolution (DE), all of the conventional parameters for systemic action are also evaluated and reorganized, and promising returns and accuracy rates are transmitted. These parameters include learning rates, fluctuation coefficients, and the office coefficient used by the FCM. The Authors proposed a finger-based biometric system based on a finger vein blend and a method for determining the geometry of the finger (Asaari et al. 2016) that could be used for each of the procedures described above. They made their predictions by examining the association between BLPOC variables that were not deterrent, flexible, or rescaling. The width center contour distance (WCCD) was used in this technique, a geometrical component that combines the finger width and the center contour distance (CCD), allowing for greater precision in confirming the finger geometry. Lin et al. published a classifier for the enthralling gray relativity analysis (GRA) graving assertion in 2011 (Lee and Lin 2011). They were the first to propose using a specific vein on the fingers as a new form of identification, which was proposed by Kono et al. Many studies have considered veins in their analyses (Kono et al. 2002). The acquisition of images is the first step in the process. Unfortunately, high-quality finger vein images alone are insufficient for diagnosing and treating the condition; pretreatment is required as part of the process. System architectures based on deep learning have displaced traditional systems; convolutional neural networks (CNNs) exhibit precision and speed, which are characteristics of conventional algorithms (Lee et al. 2011). The multilayer perceptron (MLP) was used to examine seven individuals and fourteen test samples. The MLP was found to have a 93% accuracy rate in identifying the subjects. In a study conducted by Wang et al. (2012), SVM was applied to a database of ten people, each of whom had 80 images. By using an optical image in each type of finger impression, one in each of them, some finger influence images are taken. To reassure refining influence, image update, double-photograph, and perspective area adjustments, the modern picture preprocessing technique is used to estimate the fractal dimension for the 2D two-figure picture; Katz’s figure and Weierstrass cosine function (WCF) have been used to clarify
12.3 Methodology
The vascular model during an individual’s finger to beginning late procured data in this proposed work. The introduced architecture could be a blend of medications, and programming will not achieve alone task internal a given period, forever ceaselessly, with or excepting human joint undertakings. The introduced course of movement of a PC system that screens respond to direct a terrace space. A condition related to the system through sensors, actuators, and various measurements yields interfaces. Embedded systems must meet engineering and particular confinements constrained on that utilizing the planet. Biometrics surmises the undeniable take a look at individuals by using their characteristics or characteristics. Biometrics is utilized in programming functioning as a visual affirmation and gets the privilege of passage to direct. It is furthermore will not to see people in packs that are under acumen. Biometric identifiers are the prominent, quantifiable credits that will not name and delineate individuals, referred to as physiological versus social properties. The introduced system could be a combo of gear and programming. It is used to achieve a particular venture internal a given time run, again and again, ceaselessly, with or without human joint undertakings. RTOS portrays the system for the structure works. The microcontroller is an orchestrated chip that contains all the sections comprising the controller. It will be cleaned by utilizing merging more cutoff factors into the CPU chip. Biometrics is utilized to work out the qualities of people. For vanquishing the limits, use an assortment of sensors during a multi-biometric structure. The Finger vein could be a biometric guaranteeing shape that assortments out.
12.4 Proposed System
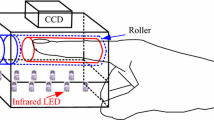
A real-time finger vein recognition system for authentication on mobile devices is proposed and shown in Fig. 12.1. The system is referenced on a given arranged and issued a one-size-finger vein validation count. The proposed system integrates three interface devices: image procurement interface, integrated mainboard, and human–machine communication module.
The photograph-acquisition module, responsible for acquiring complete images of the finger veins, serves as the system’s structural structure and foundation. The vein in the finger may be a promising biometric structure for the precise individual assertion of the certificate’s security and convenience, especially when combined with other biometric structures. Typically, the vein is hidden by the physical makeup and is therefore imperceptible to standard eyes. This indicates to the vein that it is trying to make or take something. In addition to ensuring the customer’s complete understanding and cleanliness, the unnecessary and contactless finger vein grab is consistently commendable. To create a stay body, it is necessary to use a mannequin with finger veins. As such, it is a distinguishing characteristic as well as a convincing explanation that the need for which the finger vein is acquired is still present. This system increases more assurance and settlement for unsurprising biometric finger vein validation structures for the breaking point systems.
Figure 12.2 proposed the yield which is by and large will not drive a pushed decoder IC or a chip that is getting a charge out of the information. The gatherers yields will possibly impel when significant realities are accessible. In conditions when no transporter is open, the yield will remain low. These chips are made using Motorola and Holtek. There is a striking technique to recognize crucial remote control. This may happen whether encoders and decoders are used with a scope of region settings for every transmitter and recipient pair. Inside the competition, those two-way trades are required, half-duplex side interest is allowed. The RWS-434 modules do not be a piece of inside disentangling. On the off peril that the designers need to develop simple weight or acclaim signals, for example, button presses or change terminations, the designers will have the option to use the encoder and decoder IC set depicted starting at now. Decoders with undulating and caught yields are open. A couple of encoder/decoders with similar addresses and realities procedures ought to be picked for genuine movement. The decoders get progressive zones and records from a patch up 2^12 technique for encoders transmitted with the assistance of a vehicle using an RF or an IR transmission medium. The gatherer’s yields will maybe interchange when authentic realities are open. In designs when no transporter is reachable, the yield will, in any case, beneath.
Figure 12.3 indicates the rigging pack, RF transmitter, RF recipient, GSM modem, and ARM processor, which helps in improving the proposed structure. The following are the outcome of the proposed work of this research: Biometric structures collaborate the buyers with explicit best stipulations when showed up unmistakably in a very agreement with the basic systems in two or three an assortment of the way, for example. Biometric structures empower the opportunity of close related accreditation of a person. Structures are used to request and see evidence in complex applications like banking, screen, natural sciences, character unquestionable certification, and insight. Simply verifying biometric technology is feasible, agonizing over knowledge from individual characteristics. Biometric validation techniques, frailty routes complications and dissatisfactions with general man or lady apparent improvement in qualification assortments. Multi-biometric systems combine various biometric characteristics from two sources wherever possible, and hence, the chances of achievement are more notable with less disrespect. These systems are more critical vital pointers of showing the persona than stylish structures depending upon the utilization of great cards, passwords, connecting with swipe cards, man or lady evident evidence numbers (PINs), keys, and so on less with biometric structures.
12.5 Results and Discussion
The proposed model is developed in an embedded C platform and simulated using Keil compiler. The images are modulated using MATLAB.
Figure 12.4 shows scrutinizing the finger vein configuration images which are taken from the database. Here, the database carries 500 finger vein configuration pictures below the measurement now not quite the same as 512 × 512 to 1024 × 1024. The database photographs are RGB and precise reminiscence sizes. The database snapshots are going under the recreation graph of TIF, GIF, PNG, and JPEG. Here, the JPEG game plan of the image is picked off for taking care of the system.
Figure 12.5 shows resizing the pics of analyzing the vein design, which is in the size of 256,256. Here, several photographs are reshaped or resized in a fixed size with a definitive goal of the further strategy of histogram amendment over the picture.
Figure 12.6 suggests that adjusting the resizing photographs with the aid of using histogram equalization techniques. Here, the flightiness estimations of the pixel are balanced with the aid of the neighbor pixel respect. It upgrades the full-scale see of pix when the utilizable records of the photograph address via shut specific qualities. This change the forces fit to be increased dissipated on the histogram. This action thinks about the locale of mediocre close to complexities to construct a more excellent partition. Histogram evening out accomplishes this by using satisfactorily dissipating out the most rehashed electricity respects. The proposed method is beneficial in images with foundations and the front strains that are magnificent or decrease.
Figure 12.7 indicates that the phase extraction of the leveled-out pictures. Function extraction develops from an extraordinary sport layout of figuring out statistics and creates resultant characteristics proposed to be beneficial and non-tedious, make possible the dynamic mastering and survey step. Feature extraction is identified with dimensionality diminishing. Right, when the records to computation are excessively massive ever to be readied, and it is suspected to be dreary, it might be changed into a thick path of action of elements moreover formative a phase of the most important highlights is depicted component choice. Figure 12.8 suggests the simulation of database; it offers the statistics about the result of the database if the technique is finished. Here, every solicitation image is separated and the database for the arranging procedure.
During the arranging method, the highlights are separated and the database picture. Figure 12.9 shows that the database is sorted out with the finger vein instance of the individual given as information. Arranging depends upon the segment current in a request picture with a database photograph to determine vein endorsement. Figure 12.10 suggests that the whole is pulled via and through from his file utilizing his file number, and the alternate is finished comparatively the alternate method is performed effectively.
12.6 Conclusion
The proposed correlation and the method of finger vein explanation are based on a far-reaching approximation and deficit in an embedded point. The proposed design incorporates a contraction for acquiring finger veins, an ROI division technique, and a remarkable structure to support spreading figures and deficiency features. The 600 finger images in the dataset were typical requests for a whole period of time (from summer to winter) using a standard contraction we conveyed. By taking a look at results, it demonstrated that the EER of our technique was once 0.07%, from a standard point of view not up to these of other existing frameworks.
References
Abitha N, Babysha P, Devisri S, Kumar P (2020) Application of DL/ML in diagnosis in medical imaging. J Intell Syst Robot Insights Transformations 4(1). ISSN: 2581-5636 (online)
Asaari MSM, Suandi SA, Rosdi BA (2016) Geometric feature extraction by FTAs for finger-based biometrics system. IET Biometrics 6(3):157–164
Bracken RC (2020) The ghost in the machine: biometric data, medical imaging, and embodied narrative. Public 30(60):175–187
Dargan S, Kumar M (2020) A comprehensive survey on the biometric recognition systems based on physiological and behavioral modalities. Expert Syst Appl 143:113114
El mehdi Cherrat RA, Bouzahir H (2020) A multimodal biometric identification system based on cascade advanced of fingerprint, fingervein and face images. Indonesian J Electr Eng Comput Sci 18(1):1562–1570
Escobar D, Cárdenas D, Amarillo R, Castro E, Garcés K, Parra C, Casallas R (2016) Towards the understanding and evolution of monolithic applications as microservices. In: XLII Latin American computing conference (CLEI). IEEE, pp 1–11
Hwang D, Park W (2018) Design heuristics set for X: a design aid for assistive product concept generation. Des Stud 58:89–126
Kono M, Ueki H, Umemura SI (2002) Near-infrared finger vein patterns for personal identification. Appl Opt 41(35):7429–7436
Kumar KS, Kumar TA, Radhamani AS, Sundaresan S (2020) Blockchain technology: an insight into architecture, use cases, and its application with industrial IoT and big data. In Blockchain Technology. CRC Press, pp 23–42
Kumar TA, Selvi SA, Rajesh RS, Glorindal G (2021) Safety wing for industry (SWI 2020)–an advanced unmanned aerial vehicle design for safety and security facility management in industries. In: Industry 4.0 interoperability, analytics, security, and case studies. CRC Press, pp 181–198
Lee AH, Lin CY (2011) An integrated fuzzy QFD framework for new product development. Flex Serv Manuf J 23(1):26–47
Lee EC, Jung H, Kim D (2011) New finger biometric method using near infrared imaging. Sensors 11(3):2319–2333
Lu Y, Yoon S, Xie SJ, Yang J, Wang Z, Park DS (2014) Finger vein recognition using histogram of competitive gabor responses. In: 22nd international conference on pattern recognition. IEEE, pp 1758–1763
Madhusudhan MV, Basavaraju R, Hegde C (2019) Secured human authentication using finger-vein patterns. In: Balas V, Sharma N, Chakrabarti A (eds) Data management, analytics and innovation. Advances in intelligent systems and computing, vol 808. Springer, Singapore
Matsuda Y, Miura N, Nagasaka A, Kiyomizu H, Miyatake T (2016) Finger-vein authentication based on deformation-tolerant feature-point matching. Mach vis Appl 27(2):237–250
Narmadha S, Gokulan S, Pavithra M, Rajmohan R, Ananthkumar T (2020) Determination of various deep learning parameters to predict heart disease for diabetes patients. In: International conference on system, computation, automation and networking (ICSCAN). IEEE, pp 1–6
Pakutharivu P, Srinath MV (2017) Analysis of fingerprint image enhancement using gabor filtering with different orientation field values. Indonesian J Electr Eng Comput Sci 5(2):427–432
Qiu X, Kang W, Tian S, Jia W, Huang Z (2017) Finger vein presentation attack detection using total variation decomposition. IEEE Trans Inf Forensics Secur 13(2):465–477
Revathy P, Kumar TA, Rajesh RS (2019) Design of highly efficient dipole antenna using HFSS. Asian J Appl Sci Technol (AJAST) (Peer Reviewed Q Int J) 3:01–09
Samuel TA, Pavithra M, Mohan RR (2021) LIFI-based radiation-free monitoring and transmission device for hospitals/public places. In: Multimedia and sensory input for augmented, mixed, and virtual reality. IGI Global, pp 195–205
Sasireka K, Rajesh RS (2014) Dual biometric authentication scheme for privacy protection. In: International conference on communication and network technologies. IEEE, pp 105–108
Shende P, Dandwate YH (2020) Convolutional neural network based multimodal biometric human authentication using face, palm veins and fingerprint. Int J Innovative Technol Exploring Eng (IJITEE) ISSN: 2278-3075
Suresh Kumar K, Radha Mani AS, Sundaresan S, Ananth Kumar T (2021) Modeling of VANET for future generation transportation system through edge/fog/cloud computing powered by 6G. In: Cloud and IoT‐based vehicular Ad Hoc networks, pp 105–124
Thiruvikraman P, Kumar TA, Rajmohan R, Pavithra M (2021) A survey on haze removal techniques in satellite images. Ir Interdisc J Sci Res (IIJSR) 5(2):01–06
Vega AP, Travieso CM, Alonso JB (2014) Biometric personal identification system based on patterns created by finger veins. In: 3rd IEEE international work-conference on bioinspired intelligence. IEEE, pp 65–70
Wang KQ, Khisa AS, Wu XQ, Zhao QS (2012) Finger vein recognition using LBP variance with global matching. In: International conference on wavelet analysis and pattern recognition. IEEE, pp 196–201
Xiang W, Wang G, Pickering M, Zhang Y (2016) Big video data for light-field-based 3D telemedicine. IEEE Network 30(3):30–38
Xie S, Fang L, Wang Z, Ma Z, Li J (2017) Review of personal identification based on near infrared vein imaging of finger. In: 2nd international conference on image, vision and computing (ICIVC). IEEE, pp 206–213
Yim J, Jung H, Yoo B, Choi C, Park D, Kim J (2015) Rotating your face using multi-task deep neural network. In: Proceedings of the IEEE conference on computer vision and pattern recognition, pp 676–684
Yong Y (2020) Research on technology of finger vein pattern recognition based on FPGA. J Phys: Conf Ser 1453:012037
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this chapter
Cite this chapter
Rajakumar, G., Ananth Kumar, T. (2022). Design of Advanced Security System Using Vein Pattern Recognition and Image Segmentation Techniques. In: Kumar, N., Shahnaz, C., Kumar, K., Abed Mohammed, M., Raw, R.S. (eds) Advance Concepts of Image Processing and Pattern Recognition. Transactions on Computer Systems and Networks. Springer, Singapore. https://doi.org/10.1007/978-981-16-9324-3_12
Download citation
DOI: https://doi.org/10.1007/978-981-16-9324-3_12
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-16-9323-6
Online ISBN: 978-981-16-9324-3
eBook Packages: Computer ScienceComputer Science (R0)