Abstract
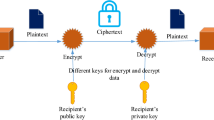
In this ever-changing world of technology, data security is of utmost importance. This research paper focuses on identifying the best combination of cryptography and steganography algorithms for securing data. The proposed approach developed a complete end-to-end system that encrypted text message using the Advanced Encryption Standard algorithm. The encrypted message was then embedded onto images using steganography techniques like Least Significant Bit, Discrete Cosine Transform and Discrete Wavelet Transform. The message was later decrypted and extracted. The performance of the algorithms was evaluated using various metrics. The best performing combination of algorithms for each metric was then identified.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Kaspersky, Cryptography Definition, http://kaspersky.com/resource-center/definitions/what-is-cryptography, 2021
SearchSecurity, What is cryptography?—Definition from WhatIs.com, https://searchsecurity.techtarget.com/definition/cryptography, 2021
SearchSecurity, What is cryptology?—Definition from WhatIs.com, https://searchsecurity.techtarget.com/definition/cryptology, 2021
SearchSecurity, What is cryptanalysis?—Definition from WhatIs.com, https://searchsecurity.techtarget.com/definition/cryptanalysis, 2021
The Economic Times, What is Cryptography? Definition of Cryptography, Cryptography Meaning—The Economic Times, https://economictimes.indiatimes.com/definition/cryptography, 2021
Fruhlinger J (2021) What is cryptography? How algorithms keep information secret and safe, CSO Online. https://www.csoonline.com/article/3583976/what-is-cryptography-how-algorithms-keep-information-secret-and-safe.html
Codr J, Unseen, An overview of steganography and presentation of associated java application c-hide, https://www.cse.wustl.edu/~jain/cse571-09/ftp/stegano/index.html
Dickson B (2020) What is steganography? A complete guide to the ancient art of concealing messages, https://portswigger.net/daily-swig/what-is-steganography-a-complete-guide-to-the-ancient-art-of-concealing-messages, 2020/02/06
Steganography Tutorial (2020) A complete guide for beginners, https://www.edureka.co/blog/steganography-tutorial, 2020/11/25
Semilof M, Clark C (2018) What is steganography?—Definition from whatis.com, https://searchsecurity.techtarget.com/definition/steganography#:~:text=Steganography%20is%20the%20technique%20of,for%20hiding%20or%20protecting%20data, 2018/12/28
Srivatsava J, Sheeja R (2020) Implementation of triple DES algorithm in data hiding and image encryption techniques. Int J Adv Sci Technol 29(3):10549–10559
Damrudi M, Jadidy Aval K (2019) Image Steganography using LSB and encrypted message with AES, RSA, DES, 3DES and Blowfish. Int J Eng Adv Technol (IJEAT) 8(6S3):2249–8958
Saikumar I (2017) DES–data encryption standard. Int Res J Eng Technol (IRJET) 4(3):1777–1782
Mittal S, Arora S, Jain R (2016) Data security using RSA encryption combined with image steganography. In: 1st India international conference on information processing (IICIP) IEEE, pp 1–5
Bhargava S, Mukhija M (2019) Hide image and text using LSB, DWT and RSA based on Image steganography. ICTACT J Image Video Process 9(3):1940–1946
AbdelWahab O, Hussein A, Hamed H, Kelash H, Khalaf A, Ali H (2019) Hiding data in images using steganography techniques with compression algorithms. TELKOMNIKA 17(03):1168–1175
Zagade S, Bhosale A (2014) Secret data hiding in images by using DWT techniques. Int J Eng Adv Technol (IJEAT) 03(05):230–235
Goel S, Rama A, Kaur M (2013) A review of comparison techniques of image steganography. Glob J Inc. (USA) 13(4):9–14
Vimal Kumar Murugan G, Uthandipalayam Subramaniyam R (2020) Performance analysis of image steganography using wavelet transform for safe and secured transaction. Multim Tools Appl 79:9101–9115
Baziyad M, Rabie T, Kamel I (2020) Achieving stronger compaction for DCT-based steganography: a region-growing approach. In: Trends and innovations in information systems and technologies. WorldCIST 2020. Advances in intelligent systems and computing, vol 1160. Springer Nature Switzerland, pp 251–261
Desai J, Hemalatha S, Shishira S (2014) Comparison between DCT and DWT steganography algorithms. Int J Adv Inf Sci Technol (IJAIST) 24(24):2319–2682
Huu Q, Dinh T, Tran N, Van T, Minh T (2021) Deep neural networks based invisible steganography for audio-into-image algorithm. In: IEEE 8th Global conference on consumer electronics (GCCE), pp 423–427
Harahap M, Khairina N (2020) Dynamic steganography least significant bit with stretch on pixels neighborhood. J Inf Syst Eng Bus Intell 6(2):151–158
Forouzan B, Mukhopadhyay D (2007) Cryptography and network security. Tata McGraw-Hill Publishing Company Limited, New Delhi
Chan CK, Cheng LM (2004) Hiding data in images by simple LSB substitution. Pattern Recogn 37(3):469–474
Ahmed N, Natarajan T, Rao KR (1974) Discrete cosine transform. IEEE Trans Comput C-23(1):90–93
Sari W, Rachmawanto E, Setiadi I, Sari C (2017) A good performance OTP encryption image based on DCT-DWT steganography. TELKOMNIKA 15(4):1987–1995
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Biju, A., Kunder, L., Angel Arul Jothi, J. (2022). Analysis on Advanced Encryption Standard with Different Image Steganography Algorithms: An Experimental Study. In: Saraswat, M., Sharma, H., Balachandran, K., Kim, J.H., Bansal, J.C. (eds) Congress on Intelligent Systems. Lecture Notes on Data Engineering and Communications Technologies, vol 111. Springer, Singapore. https://doi.org/10.1007/978-981-16-9113-3_29
Download citation
DOI: https://doi.org/10.1007/978-981-16-9113-3_29
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-16-9112-6
Online ISBN: 978-981-16-9113-3
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)