Abstract
With the development of information technology, Internet of things (IoT) has been applied widely in human civilization, but it leads to the increase of the risk about information security. The traditional security solutions have revealed the lack of compatibility with IoT because of the differences about complex communication protocol, low energy, processing ability, and limited memory. Therefore, the suitable IoT security solutions need the balance between energy and costs as well as wide adaption for the various network protocols. Our research team, after had been under a long process of analyzing theoretical documents and operating simulated experiments, recognized that the lightweight cryptography is the most optimal solution in new network platform generation. Our team also improved and implemented CurveCP which is one of these lightweight cryptographies in the wireless sensor networks (WSN) to enhance data secure and information security of IoT system. This study briefly describes the improvement of CurveCP lightweight cryptography by reducing length of cryptographic key as well as implement in IoT system. It also includes the simulation experiment, solutions evaluation, conclusion, and future development.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Bernstein, D.J.: CurveCP: Usable Security for the Internet. University of Illinois, Chicago, 22 Jan 2017
Van Tanh, N. Tri, N.Q., Giang, N.L., Tuan, N.A.: Design of comprehensive security solution on Internet of Things with improved DTLS protocol and overhearing mechanism. In: Fundamental and Applied Information Technology Research (FAIR), Nha Trang, Vietnam (2020)
Li, D.X., He, W., Li, S.: Internet of things in industries: a survey. IEEE Trans. Ind. Inf. 10(4), 2233–2243 (2014)
Hankerson, D., Menezes, A.J., Vanstone, S.: Guide to Elliptic Curve Cryptography. Springer Publishing (2003)
Pauly, T., Perkins, C., Rose, K., Wood, C.: A Survey of Transport Security Protocols. University of Glasgow, 6 Sept 2018
Dunkels, A.: Contiki: bringing IP to sensor networks. ERCIM News J. Eur. Union (2009)
Pedro, Mugdhe, Samarth: Cooja simulator—Contiki tutorials. In: Autonomous Networks Research Group. University of South California (2016)
Mojzís, J.: Tinyssh. The SSH Library (2018)
Bernstein, D.J., Lange, T., Schwabe, P.: NaCl: Networking and Cryptography Library. University of Illinois, Chicago (2016)
Felker, R.: Musl 1.1.24 reference manual. License of Massachusetts Institute of Technology (2011)
Culler D., Estrin D., Srivastava M.: Guest Editors’ Introduction: Overview of Sensor Networks, pp. 41–49 (2004). https://doi.org/10.1109/mc.2004.93
Mansfield, K.C., Antonakos, J.L.: Computer Networking from LANs to WANs: Hardware, Software, and Security. Boston Cengage Learning, p. 501 (2010)
SAS Team: What is network latency (and how do you use a latency calculator to calculate throughput)? The SAS Group of Companies Limited, Apr 2019
Abdellatif, M.: [Contiki Developer] Power Consumption, 17 July 2017
Johnson, M., Healy, M., van de Ven, P., Hayes, M.J., Nelson, J., Newe, T., Lewis, E.: A comparative review of wireless sensor network mote technologies. In: IEEE Sensors Conference, p. 1442 (2009)
Hofstrand, D.: Energy Measurements and Conversions. Iowa State University Extension and Outreach (2007)
Van Tanh, N., Tri, N.Q., Tuyen, N.G., Duc, T.Q., Anh, T.H., Tung, B.T.: The flooding attack in low power and lossy networks: a case study. In: The 7 th IEEE International Conference on Smart Communications in Network Technologies (SaCoNet 2018). El Oued, Algeria (2018)
Văn Tánh, N., Trí, N.Q.,
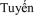 , N.G., Giang, N.L.,
, N.G., Giang, N.L.,
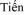 , N.V.: Design a security system for internet of things with detecting and author proceedings of eliminating denial of service attack based on overhearing mechanism. In: The 3rd Symposium of Information Security (SoIS 2018). Da Nang, Vietnam (2018)
, N.V.: Design a security system for internet of things with detecting and author proceedings of eliminating denial of service attack based on overhearing mechanism. In: The 3rd Symposium of Information Security (SoIS 2018). Da Nang, Vietnam (2018)Samonas, S., Coss, D.: The CIA strikes back: redefining confidentiality, integrity and availability in security. J. Inf. Syst. Secur. 10(3), 21–45 (2014)
Acknowledgements
Our team sends the gratefulness to tutors and the colleagues for providing adequate support about infrastructure and advice during the researching process. They work in Bach Khoa Cipher Security Center and other faculties in School of Information Communication Technology, Hanoi University of Science and Technology as well as Vietnam National University. This research is funded by Hanoi Department of Science and Technology under the project 01C-02/01-2019-3.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Van Tanh, N., Tri, N.Q., Giang, N.L., Le, DT. (2022). Security Solution for the Internet of Things with the Innovative Lightweight Encryption Algorithm CurveCP. In: Gandhi, T.K., Konar, D., Sen, B., Sharma, K. (eds) Advanced Computational Paradigms and Hybrid Intelligent Computing . Advances in Intelligent Systems and Computing, vol 1373. Springer, Singapore. https://doi.org/10.1007/978-981-16-4369-9_49
Download citation
DOI: https://doi.org/10.1007/978-981-16-4369-9_49
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-16-4368-2
Online ISBN: 978-981-16-4369-9
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)





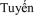 , N.G., Giang, N.L.,
, N.G., Giang, N.L.,
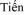 , N.V.: Design a security system for internet of things with detecting and author proceedings of eliminating denial of service attack based on overhearing mechanism. In: The 3rd Symposium of Information Security (SoIS 2018). Da Nang, Vietnam (2018)
, N.V.: Design a security system for internet of things with detecting and author proceedings of eliminating denial of service attack based on overhearing mechanism. In: The 3rd Symposium of Information Security (SoIS 2018). Da Nang, Vietnam (2018)