Abstract
Digital image watermarking has become an interesting research field to face the issues created by the increasing use of Internet for distribution of digital data. For the couple of decades, authenticity of digital data has been concern for everyone. Digital image watermarking plays a vital role in protection of copy rights. In frequency domain watermarking, discrete cosine transform (DCT)-based watermarking process is most common because the majority of image compression methods are developed in DCT domain. This research presents a robust discrete wavelet transform (DWT) and fast Fourier transform (FFT) manner-based digital watermarking (DW). In the initial stage, split the original (cover) image into two horizontal and two vertical sub-bands using 3-DWT-FFT sub-band using changing their values. In this thesis, the embedding and extraction technique for watermarking is presented based on DWT & FFT transforms. In this technique, the embedding and de-embedding of the watermark is much easier than other transform techniques. Various values of PSNR’s, MSE’S & NC’s are analyzed for watermarked image quality and extracted watermark quality.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
The watermarking is an old technique for hiding information. Cryptography is the oldest technique for hiding the owner information. In cryptography, the owner data is encoded such that it can be decoded only by the receiver with the help of some look up table or pre-defined rule. Next comes the steganography in which the data is hidden with the host image. Steganography is invisible and cannot be detected by any third person except by the receiver. The third method of hiding ownership data is watermarking. The image watermarking may be visible or invisible. We shall be discussing the invisible watermarking in this paper.
In this paper, we have used frequency domain-based watermarking technique. The use of discrete wavelet transform (DWT) and fast Fourier transform (FFT) gives a better result than the DCT based image watermarking technique. 3rd level DWT & then FFT is used for embedding followed by inverse FFT (IFFT), and finally, we take inverse DWT (IDWT) that gives the watermarked image. The watermarking is a reversible operation.
There are total six sections in this paper. Section 1 gives the introduction of the digital image watermarking. Section 2 offers a few connected works. Section 3 briefs us with the techniques used in this paper. Section 4 gives the algorithm for embedding and extraction of the watermark. Section 5 includes the results of the MATLAB simulations and discussion. Section 6 is the conclusion of this paper. Finally, the references used is the paper are given.
2 Literature Review
He and Hu [1], proposed a algorithm of color image watermarking, depending upon (DWT-DCT-SVD). RGB color space is converted into YUV space, and then, embedding is done in the luminance component Y [1].
Pal et al. [2]. In this paper, a detail study of watermarking and steganography techniques are discussed. With the increasing demand of Internet, data security and authentication have been concern for every one [2].
Ginanjar et al. [3]. In this paper, a genetic algorithm based on phase shift keying is proposed for invisible watermarking. Audio watermarking has been done with this technique, and performance of the technique is evaluated [3].
Maheshwari [4]. In this paper, discrete wavelet transform and singular vale decomposition-based digital image watermarking technique has been proposed. First water mark is embedded by DWT method by breaking it into four bands LL, LH, HL, HH, then, SVD of each sub-band is taken, and second watermark is embedded. Various performance parameters are evaluated for this technique [4].
Mirzaei et al. [5]. In this paper, an invisible watermarking method using local gradient analysis has been given. Image is divided into many small-small blocks, and then, watermark is embedded into the frequency components of these blocks [5].
Muni SekharI et al. [6]. In this paper, edge-based watermarking techniques have been discussed. A new method, reference image and edge (RIE), has been introduced which can defeat the smoothing impact of earlier edge-based watermarking techniques [6].
Draganić et al. [7]. Public key cryptography signature (PKCS) is used in this technique for hiding the 32 bit serial number for the purpose of source verification and ownership rights [7].
3 Techniques Used in Research
-
A.
Discrete Wavelet Transform (DWT)
Discrete wavelet transform is a method for converting spatial domain signal into frequency domain signal. For the purpose of image, we use two-dimensional DWT. DWT uses wavelets for decomposition of time domain signal into frequency domain. The wavelets are basically limited in time and space both, whereas the normal sine- and cosine-based transform (i.e., FFT) or the cosine only based transform (i.e., DCT) is not limited to both time and frequency domains. The most commonly used wavelet in DWT is the ‘haar’ wavelet. DWT may be calculated from two filters. One is low-pass filter, and another is high-pass filter. These filters can be expressed as follows (Fig. 1):
-
B.
Fast Fourier Transform (FFT)
The FFT is a form of Fourier transform tool that is used to convert the two-dimensional picture into its SIN and COS functions [3]. The FFT is used in signal processing, image processing, audio processing, and video processing. The two-dimensional fast Fourier transform can be written as
The inverse transform is defined as
4 Propose Work
-
A.
Problem statement
DCT can be applied for an image only in block wise. Further, after DCT, the coefficients are arranged in a zig-zag way, and then, quantization is done. During quantization, the invariance property and some upper band frequency got disturbed. Also, taking block-wise DCT is very cumbersome algorithm, and it takes lot of time and hardware to implement it. Also, when we test the DCT based watermarking technique for various types of attack, we find that it is less robust to these attacks.
-
B.
Propose Methodology
This research presents a robust discrete wavelet transform (DWT) and fast Fourier transform (FFT) manner-based digital watermarking (DW). In the initial stage, split the original (cover) image into four sub-bands using 3-DWT-FFT sub-band using changing their values. In this thesis, the embedding and extraction technique for watermarking is presented based on DWT & FFT transforms. In this technique, the insertion and extraction of the watermark are found to be simpler than other transform techniques. Various values of PSNR’s, MSE’S & NC’s are analyzed for watermarked image quality and extracted watermark quality.
-
C.
Propose Algorithm
-
1.
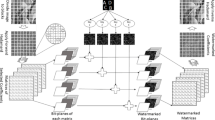
Third–level DWT is applied to the host image.
-
2.
After third-level decomposition, LH band is selected.
-
3.
Similarly, third-level DWT is taken for watermark image, and its LH band is selected.
-
4.
The FFT coefficients of both the sub-bands are taken.
-
5.
For invisible watermarking, suitable scaling factor is chosen.
-
6.
Coefficients of the LH band of host image are modified by adding watermark coefficients scaled by the scaling factor.
$$I^{{\prime }}_{\text{LH}} = I_{\text{LH}} + \alpha W_{\text{LH}}$$(5) -
7.
Apply IFFT and IDWT to obtain the watermarked host image.
-
8.
Extract the invisible watermark from the LH band by using equation:
$$W^{{\prime }}_{\text{LH}} = \frac{{I^{{\prime }}_{\text{LH}} - I_{\text{LH}} }}{\alpha }$$(6) -
9.
Take the IFFT & IDWT to get the extracted watermark.
-
10.
Compare the watermarked image with original host image and calculate the PSNR & MSE. Also calculate the normalized cross-correlation (NC) for extracted and original watermark (Fig. 2).
5 Result
The above algorithm is tested for various data set as mentioned below. First, we calculate the PSNR and MSE values for watermarked images for various data sets. Then, we calculate the normalized cross-correlation for extracted image. Finally, we have done some attack (i.e., cropping, salt and pepper, and rotation) on the watermarked image, and the normalized cross-correlation has been calculated for various data sets and various embedding intensities (α) (Fig. 3).
If we change the scaling factor, the visible watermark becomes invisible (Fig. 4; Tables 1, 2 and 3).
Irrespective of the scaling factor (α) we get the same normalized correlation (NC) and structural similarity index (SSIM) for the extracted watermark in the absence of any noise in the system.
Now, we intentionally add some noise, i.e., salt and pepper noise, cropping, and rotation of watermarked image, and then, the robustness of the propose method is checked as follows (Table 4).
6 Conclusions
This paper implemented watermarking for images using 3-DWT-FFT scheme which has proved a high level of robustness in opposition to DCT based watermarking. Majority of attacks including noise, blurring, other styles of IP attacks which can be tested by using getting better the watermark from any of the sub-band, which actually shows that remodel domain is extra robust than spatial domain. Generally, LL band is not changed as any kind of modifications in it could be easily perceived with the aid of human eyes. The simulation result shows that the mean square error (MSE) has decreased significantly while the peak signal-to-noise ratio (PSNR) has increased for DWT-FFT over DCT for host image. Also, the normalized cross-correlation (NC) has increased for watermark image in the DWT-FFT based technique.
The future work can be conducted by increasing PSNR and NC using principle component, scaling factor, and multiple dataset, and the second approach we can use is optimal scaling.
References
He Y, Hu Y (2018) A proposed digital image watermarking based on DWT-DCT-SVD. In: 2018 2nd IEEE advanced information management, communicates, electronic and automation control conference(IMCEC 2018). 978-1-5386-1803-5/18/$31.00 ©2018 IEEE
Pal P, Singh HV, Verma SK (2018) Study on watermarking techniques in digital images. In: Proceedings of the 2nd international conference on trends in electronics and informatics (ICOEI 2018). IEEE conference record: # 42666; IEEE Xplore ISBN: 978-1-5386-3570-4, 978-1-5386-3570-4/18/$31.00 ©2018 IEEE
Ginanjar RR, Kim DS, Moon CB (2018) Enhanced digital audio watermarking using genetic algorithm. In: 2018 IEEE international conference on consumer electronics-Asia (ICCE-Asia). 978-1-5386-5807-9/18/$31.00 ©2018 IEEE
Maheshwari DB (2018) An analysis of wavelet based dual digital image watermarking using SVD. In: 2018 International conference on advances in communication and computing technology (ICACCT), Amrutvahini College of Engineering, Sangamner, Ahmednagar, India. 8–9 Feb 2018. 978-1-5386-0926-2/18/$31.00 ©2018 IEEE
Mirzaei MR, Karimi M, Karimi N, Samavi S (2017) Blind image watermarking based on local analysis of gradients. In: 2017 25th Iranian conference on electrical engineering (ICEE). IEEE 20 17 © $3 l.00/978-1-5090-5963-8/17
Muni SekharI V, Kumar CS, RaoI KVG, Sambasiva RaoII N, Gopichand M (2017) A reversible RIE based watermarking scheme. In: 2017 IEEE 7th international advance computing conference. 978-1-5090-1560-3/17 $31.00 © 2017 IEEE. https://doi.org/10.1109/iacc.2017.179
Draganić A, Marić M, Orović I, Stanković S (2017) Identification of image source using serialnumber-based watermarking under compressive sensing conditions. MIPRO 2017, Opatija, Croatia, 22-26 May 2017
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Arif, J., Gangwar, S.P. (2021). An Efficient Watermarking Process Based on Three-Level DWT and FFT Technique. In: Harvey, D., Kar, H., Verma, S., Bhadauria, V. (eds) Advances in VLSI, Communication, and Signal Processing. Lecture Notes in Electrical Engineering, vol 683. Springer, Singapore. https://doi.org/10.1007/978-981-15-6840-4_24
Download citation
DOI: https://doi.org/10.1007/978-981-15-6840-4_24
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-15-6839-8
Online ISBN: 978-981-15-6840-4
eBook Packages: EngineeringEngineering (R0)