Abstract
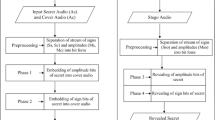
Today, security of data transmission is a big problem in society. Information security fields play a vital role in network communication. To secure information, cryptography and steganography are widely used. Image steganography become popular because images are frequently used on internet. In this paper, the combination of cryptography and steganography is used to provide more secure which mean that it provides two layers protection. The secret audios or important speeches are recorded and this secret data is encrypted using Advance Encryption Standard (AES). This cipher data is embedded into cover images using Random-Based Least Significant Bit method. The random positions of image for LSB are also generated by the use of AES key. The resulting stego images are sent to the receiver and the receiver needed to perform the reverse processes to obtain the secret data. The image quality is analyzed in terms of both Mean Square Error (MSE) and Peak Signal to Noise Ratio (PSNR) measured between the cover image and stego image.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Jirwan, N., Singh, A., Vijay, S.: Review and analysis of cryptography techniques. Int. J. Sci. Eng. Res. 4(3), 1–6 (2013)
Dilawar, A.: Image Steganography: for hiding audio messages within gray scale images. Department of Computer Science and Software Engineering, International Islamic University (2014)
Sakthisudhan, K., Prabhu, P., Thangaraj, P.: Secure audio steganography for hiding secret information. In: International Conference on Recent Trends in Computational Methods, Communication and Controls (ICON3C 2012). Bannari Amman Institute of Technology, Erode – India (2012)
Sherly, A.P., Amritha, P.P.: A compressed video steganography using TPVD. Int. J. Database Manag. Syst. (IJDMS) 2(3), August 2010. TIFAC CORE in Cyber Security, Amrita Vishwa Vidyapeetham, Coimbatore
Announcing the ADVANCED ENCRYPTION (AES): Federal Information Processing Standards Publication 197, United States National Institute of Standards and Technology (NIST), 26 November 2001
Stallings, W.: Cryptography and Network Security Principles and Practices, 4th edn., 16 November 2005
Lin, E.T., Dell, E.J.: A review of data hiding in digital images. In: Video and Image Processing Laboratory School of Electrical and Computer Engineering
Dilawar, A.: Image Steganography: For Hiding audio messages within Gray scale images. Department of Computer Science and Software Engineering, International Islamic University (2014)
Bhagyashri, A.P. et al.: Review of an improved audio steganographic technique over LSB through random based approach. IOSR J. Comput. Eng. (IOSR-JCE). Government Engineering College Aurangabad MS, India
Acknowledgments
First of all, I would like to express my special thanks to Dr. Aung Win, Rector, University of Technology (Yatanarpon Cyber City). I would like to express my respectful gratitude to Dr. Soe Soe Khaing, Pro-rector, University of Technology (Yatanarpon Cyber City), for her kind permission to complete this thesis. I am thankful to her for giving enough consideration to her ideas and views. I would like to express grateful thank to Dr. Cho Me Me Maung, Professor and Head and Dr. Hnin Hnin Htun, Professor and Course Coordinator, Department of Computer Engineering, for her kind guidance, encouragement in making my thesis to complete successfully. I am very grateful to my supervisor, Dr. Tin Myint Naing, Associate Professor, University of Technology (Yatanarpon Cyber City), for his kind guidance and encouragement. He has been very supportive in this thesis, and also guides a lot, particularly, at the level of quality of presentation.
Author information
Authors and Affiliations
Corresponding authors
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Naing, S.W., Naing, T.M. (2019). Secret Audio Messages Hiding in Images. In: Zin, T., Lin, JW. (eds) Big Data Analysis and Deep Learning Applications. ICBDL 2018. Advances in Intelligent Systems and Computing, vol 744. Springer, Singapore. https://doi.org/10.1007/978-981-13-0869-7_24
Download citation
DOI: https://doi.org/10.1007/978-981-13-0869-7_24
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-13-0868-0
Online ISBN: 978-981-13-0869-7
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)