Abstract
A novel approach of image watermarking using Lagrangian twin support vector regression (LTSVR) and combination of a variant of wavelet transform and QR decomposition for copyright protection application is proposed in this chapter. Firstly, host image decomposed into low-frequency subband (LL) and detail subbands by applying lifting wavelet transform (LWT). Secondly, the blocks of LL depend on the fuzzy entropy, and the selected regions of LL are transformed using QR factorization. Then, image dataset is formed using the elements of matrix R (called feature vector) of each selected block. This image dataset acts input to LTSVR to find the function approximation which defines the relationship between the input and target. The scrambled bits of the binary watermark are inserted into the predicted values obtained through the trained LTSVR upon comparing with the target value. The scrambled bits are obtained by applying Arnold transformation, which provide security to the proposed approach. Experimental results using various kinds of images and comparison of existing methods prove that the proposed approach is highly imperceptible and robust.
Access provided by CONRICYT-eBooks. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
The Internet is a very popular distribution medium all over the world for digital contents as it is inexpensive, no storage requirements, and fast access since few decades. With the success of digital communication on the Internet, various problems related to copyright protection of digitized properties, illegal copying, ownership of multimedia data, data security, etc., have arisen. Digital watermarking provides a solution to soft contents [1, 2] for copyright protection and its applications. Watermarking is the method of embedding the secret information known as watermark in an imperceptible manner into the original digital media without losing its visual quality [2]. Spatial- and frequency-domain watermarking are two different domains of digital image watermarking. In the literature of digital watermarking [3,4,5,6], it has been found that frequency-domain watermarking shows more robustness against attacks as compared to spatial-domain watermarking [7]. The use of machine learning algorithms such as BPNN, PNN [3, 8], support vector regression [4, 7], genetic algorithms [5], and their combination-based hybrid image watermarking system is designed by various researchers [5, 9] to increase the imperceptibility and robustness. Significant amount of imperceptibility and robustness against image processing attacks is achieved [5, 6] due to the adaptive learning capability of image datasets and good generalization ability against noise of these machine learning algorithms. In this paper, a newly designed LTSVR machine learning approach by Balasundaram et al. [10] is employed in image watermarking. The generalization performance of LTSVR on synthetic datasets which is obtained from UCI repository and against noisy datasets is already examined [10]. With the help of the work presented in this paper, high generalization against noisy datasets and the adaptive learning capability of LTSVR onto image watermarking for improving the robustness is examined.
The novel work presented in this paper is a grayscale image watermarking approach using LTSVR and based upon the feature extracted with the help of hybrid LWT-QR factorization. The selected blocks of the approximate subband (LL) of the image are used to insert the watermark. QR transformation [11] method is applied to non-overlapping regions selected using fuzzy entropy [12] to get Q and R matrix. The elements (feature vector) of R are used to make dataset for LTSVR training. The predicted value obtained using function generated by the LTSVR training is used to insert the watermark bits. A number of grayscale images are used to verify the performance of the approach presented against attacks. Due to the limitations on the number of pages, the results on Lena and Elaine images are explained in this paper. The generalization performance of LTSVR against noisy datasets is measured by the visual quality of extracted watermark which indicates the robustness of the approach, and the security of the watermark is obtained through Arnold transformation. Fuzzy entropy [12] is sensitive to image variations; it is used for selecting smooth non-overlapping blocks and discards blocks with redundant data.
The outlines of the remaining part are as follows. The mathematical description of LTSVR and QR transformation is explained in Sect. 2. In Sect. 3, the novel grayscale image watermarking approach is discussed. The outcomes of the work, comparison along with the discussions, are explained in Sect. 4. Conclusion and future directions are discussed in Sect. 5.
2 Preliminaries
2.1 QR Decomposition
The QR decomposition [11] of a matrix X (also called orthogonal-triangular decomposition) is given in
where Q is a unitary matrix and R is an upper triangular matrix, both matrices are of order of \(p\times q\). The columns of Q are obtained through the process of Gram–Schmidt orthogonalization [11]. The main characteristics of matrix R is that \(|R_{1i}|>R_{ji}\) for i \(=\) to q and j \(=\) 2 to p [11]. Also the maximum energy of the signal is concentrated in the elements of first row of matrix R. The QR decomposition has less computational complexity than other factorization method such as singular value decomposition (SVD) [13]. These interesting features of R matrix made the utilization of QR factorization in digital watermarking applications by various researchers [11].
2.2 Formulation of Lagrangian Twin Support Vector Regression
Balasundaram et al. [10] designed a novel machine learning approach called LTSVR for regression problems. This algorithm has successfully used and tested on different kinds of datasets. In this paper, the application of LTSVR is tested onto grayscale image watermarking. The adaptive learning ability and its generalization against noisy image datasets of the LTSVR algorithm is checked by applying a lot of experiments on different textured images. 2-norm nonlinear TSVR determines the insensitive up- and down-bound regressors in the feature space by solving the pair of quadratic programming problems (QPP) as
the dual QPP of [12] can be formed as a pair of minimization problems as
where \( u_{1},u_{2} \in R^{m} \) are the Lagrangian multipliers, and for finding the value of \( Q_{1},Q_{2},r_{1},r_{2} \), we refer the reader to [10]. The kernel regression function estimation \( f:R^{n} \rightarrow R \) will be determined using
where
are the down- and up-bound regressors [14]. According to the KKT conditions, the pair of dual QPP [12] will become determining solutions for the complementarily problems [15]:
respectively. The optimality conditions (6) are satisfied iff for any \(\alpha _{1},\alpha _{2}\succ 0\), the relations
respectively. The following simple iterative scheme that constitutes the convergence of LTSVR algorithm to solve the pair of problems defined by (7) is
3 Proposed Approach for Image Watermarking
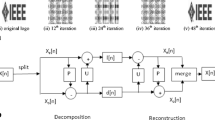
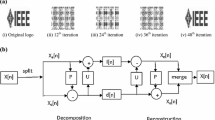
A novel grayscale image watermarking approach using LTSVR and hybridization of LWT-QR factorization which includes embedding and extracting procedure of watermark is explained as follows:
3.1 Watermark Insertion Algorithm
Consider a grayscale image \(Img=\lbrace Img \left( r,s\right) :1 \le r \le M1, 1 \le s \le M2 \rbrace \) of order of \(M1 \times M2\). In this work, a binary watermark logo of order of \(N1 \times N2\) is used for embedding and extracting purpose. The approach for inserting the watermark into the host image is as follows:
1. Firstly, the scrambled image \(\S _{m}\) of the original binary watermark is formed using Arnold transformation [16]. Then, it transformed into 1-D vector to insert into the host. That is, \(SW_{m}=\lbrace w_{k}:k=1,2,\ldots ,l_{w}\rbrace \) where \(l_{w}\) = watermark length and \(w_{k}=\lbrace 0,1\rbrace \).
2. Using one-level LWT, the host image is divided into the low-frequency subband and detailed subbands denoted by LL and LH, HL, and HH, respectively, with order \(M_{L}\times N_{L}\) where \(M_{L}=\frac{M1}{2^{r}}, M2_{L}=\frac{M2}{2^{r}}\). Here, decomposition level is denoted by r. The lifting coefficients of low-frequency subband are divided into blocks of order of \(4\times 4\). Fuzzy entropy [12] of every block is calculated and arranged in descending order.
3. Perform QR decomposition to the selected blocks of low-frequency subband using (1) to get the Q and R matrix of order equal to the block size. From the experimental results, it is found that \(r_{1,4}\) is the appropriate element to embed the scrambled watermark. The feature vector formed using the upper triangular elements \(\lbrace r_{1,1},r_{1,2},r_{1,3},r_{2,2},r_{2,3},r_{2,4},r_{3,3},r_{3,4},r_{4,4}\rbrace \) is supplied as input to LTSVR corresponding to target vector made up of the element \(r_{1,4}\). Thus, an image dataset constructed using the feature vectors of all the selected non-overlapping blocks of order of \(m\times l\) is formed (Here \(l = 10\)).
4. Based upon the fuzzy entropy, the dataset is constructed using the suitable features of the image blocks for training of the LTSVR. That is,
where the target output vector consists of \(r_{1,4}\) element of each selected block and remaining nine upper triangular elements of each block are supplied as input to LTSVR. The feature vectors of odd number of selected regions are used to train the LTSVR, i.e., \(\textit{DS}=\lbrace \left( x_{i},d_{i}\right) :i=1,3,5,\ldots ,m\rbrace \). The function obtained after the training of LTSVR using (8) is used to find the predicted value corresponding to the target vector of even number of blocks. On comparing the predicted value corresponding to the target vector \(d_{i}=\lbrace r_{1,4}:i=2,4,6,\ldots ,m\rbrace \), the watermark bits are inserted as follows:
where, \(r_{1,4}^{'}\) is the watermark embedded value after inserting the watermark which is replaced by the \(r_{1,4}\) of R of the selected region, \(r_{1,4}^{\textit{LTSVR}}\) is the predicted value found by the training function of LTSVR, \(\alpha \) denotes the strength of watermark, and wm_bit represents bit of scrambled image. After performing a number of experiments, the value of \(\alpha =20\) is chosen to minimize the trade-off between two conflicting requirements.
5. After replacing \(r_{1,4}\) by \(r_{1,4}^{'}\) of the selected regions of low-frequency subband, inverse QR decomposition is performed to get the watermark LL subband which is followed by inverse LWT transform to get the watermarked image. Then, PSNR using (9) is computed for quality evaluation of watermarked image.
3.2 Watermark Extraction Procedure Using Trained LTSVR
The extraction of watermark from the signed image includes the following steps:
1. Similar to Step 2 of embedding procedure, the low-frequency subband and detail subband of signed image denoted by \(\textit{LL}^{'}, \textit{LH}^{'}, \textit{HL}^{'}, and\,\textit{HH}^{'}\), are obtained using one-level LWT. The regions of low-frequency subband are selected as per the index of fuzzy entropy.
2. QR decomposition is applied to the selected blocks of \(\textit{LL}^{'}\) subband using (1) to obtain \(Q^{'}\) and \(R^{'}\) of order of \(4\times 4\). Similar to Step 4 of watermark embedding, features are extracted and form the watermarked dataset. Then, features of the even number regions are supplied to trained LTSVR to extract the watermark, that is
are acts input to the function obtained after training to get the output \(r_{1,4}^{\textit{LTSVR}}:i=2,4,\ldots ,m\) corresponding to target vector \(d_{i}=\lbrace r_{1,4}^{'}:i=2,4,\ldots ,m\rbrace \). Then, \(\textit{LTSVR}\) output (predicted value) is compared with the target vector corresponding to the selected regions of the watermarked image to get scrambled vector \(SW_{m}^{'}\)
where \(r_{1,4}^{\textit{LTSVR}}\) is the \(\textit{LTSVR}\) output and \(r_{1,4}^{'}\) is the actual output of each block.
3. The scrambled binary sequence obtained using Step 2 is in a vector form. To obtain its scrambled image, it is changed into 2-D array, and then, recovered watermark image is formed using inverse Arnold transformation [16]. The bit error rate (BER) value using (10) is computed to measure the quality of the recovered watermark.
Watermarked images corresponding to Fig. 1 along with extracted watermark without attack
4 Result Analysis, Comparison, and Discussion
The performance of the approach described here is evaluated on the grayscale images Lena and Elaine of order of \(512 \times 512\) shown in Fig. 1. A binary logo of order of \(32 \times 32\) shown in Fig. 2 is used as a binary watermark. The optimal value of LTSVR parameters \(C1=C2=50\) and the spread of RBF kernel \(\sigma =10^{-3}\) are determined by k-fold crossvalidation on the dataset used for training by varying \(C1=C2=\lbrace 50,100,\ldots ,500\rbrace \) and \(\sigma =\lbrace 10^{-3},10^{-2},\ldots ,10^{3}\rbrace \), respectively. The learning capability of LTSVR and its generalization performance is demonstrated by the imperceptibility and robustness of watermark against various types of image processing attacks on different textured images shown in Fig. 1. LTSVR requires more parameters to be selected as compared to LSVR [17] which leads to slow the learning speed.
4.1 Performance Evaluation
The performance of the proposed approach is evaluated using the imperceptibility of the watermark and its robustness. The imperceptibility is found by the quality of the watermarked image as measured by PSNR given in the equation as follows:
where MSE is the mean square error. The watermarked images obtained after embedding process along with the recovered watermark after extraction procedure are revealed in Fig. 3 corresponding to Figs. 1 and 2. Bit error rate (BER) is given as
The quality parameters PSNR and BER corresponding to the watermarked image and extracted watermark along with the visualization of images are indicated in Fig. 3 when no image processing attack is performed. The PSNR value more than 40 dB as indicated in Fig. 3 of the watermarked version images shows the good quality of watermarked images with high imperceptibility of the watermark. The accurate watermark extraction using the proposed approach when no attack is performed is verified by the zero BER value as shown in Fig. 3 The robustness of the approach described in this paper is investigated by performing several kinds of image processing operations such as blurring, salt-and-pepper noise, Gaussian noise, histogram equalization, JPEG compression, gamma correction, median filtering, average filtering, scaling and cropping on all the watermarked images followed by the watermark extraction process. The visual quality of recovered watermark as measured by the BER value against all the attacks is shown in Table 1 corresponding to all watermarked images. BER values are shown in Table 1, and it is observed that corresponding to all the attacks, the proposed approach has lower BER value which signifies that the extracted watermark has good visual quality and recognizable.
4.2 Comparison Results
The effectiveness of the scheme presented in this paper is examined by comparing the robustness against attacks with the method described by Songs et al. [11] on Lena image. For fair comparison, same kinds of attacks are executed on Lena image and then watermark extraction procedure is performed. The outcomes of the watermark extraction procedure measured by the BER value against attacks are given in Table 2 and shown in Fig. 4. From Table 2 and Fig. 4, we found that the visualization of the recovered watermark is better than the scheme introduced by Song et al. [11] as quantified by the lower BER value against all the attacks except against rotation and salt-and-pepper noise operations. By comparison with the existing methods, it is inferred that the approach presented in this paper has better performance than the scheme [11].
BER value comparisons against image processing operations on Lena image with [11]
5 Conclusion
In this work, an effective approach of grayscale image watermarking using LTSVR and through the combination of wavelet transform and QR decomposition is described for copyright protection applications. Fuzzy entropy is not only used to discard the regions of the image which are not relevant to embed the watermark but also reduces the time complexity. Selection of LL sub band using LWT and appropriate coefficient selection of each region using QR decomposition results in enhancing the performance as measured by imperceptibility and robustness. The robustness measured by different kinds of attacks performed on test images is accomplished by the good generalization property of LTSVR as revealed from the experimental results using proposed approach. The scrambled watermark obtained using Arnold transformation provides the security to the original watermark. The experimental and comparison results on different textured images with the existing methods prove that the approach described in this paper attains imperceptibility as well as robustness.
References
Cox, I.J., Kilian, J., Leighton, F.T., Shamoon T.: Secure spread spectrum watermarking for multimedia. IEEE Trans. on Image Processing. 6, 1673–1687, 1997.
Moulin, P., Mincak, M.: A framework for evaluating the data-hiding capacity of image sources. IEEE Trans. on Image Processing. 11, 1029–1042, 2002.
Wen, X.B., Zhang, H.: A new watermarking approach based on probabilistic neural network in wavelet domain. Soft Computing, No. 13, pp. 355–360, 2009.
Peng, H., Wang, J.: Image watermarking method in multiwavelet domain based on support vector machines. The Journal of Systems and Software, No. 83, pp. 1470–1477, 2010.
Mehta, R., Rajpal, N., Vishwakarma, V. P.: Robust Image Watermarking Scheme in Lifting Wavelet Domain Using GA-LSVR Hybridization, International Journal of Machine Learning and Cybernetics, DOI: 10.1007/s13042-015-0329-6, 2015.
Mehta, R., Rajpal, N., Vishwakarma, V. P.: A robust and efficient image watermarking scheme based on Lagrangian SVR and lifting wavelet transform. International Journal of Machine Learning and Cybernetics, DOI: 10.1007/s13042-015-0329-z, 2015.
Shen, R.M., Fu, Y.G.: A novel image watermarking scheme based on support vector regression. The Journal of System and Software, No. 78, pp. 1–8, 2005.
Tang, G., Lio, X.: A neural network based blind watermarking scheme for digital images. Lecture Notes in Computer Science (LNCS), 3174, pp. 645–650, 2004.
Jing, Li., Liu, F.: Robust image watermarking scheme with general regression neural network and FCM algorithm. Lecture Notes in Computer Science (LNCS), 5226, pp. 243–250, 2008.
Balasundaram, S., Tanveer, M.: On Lagrangian twin support vector regression. Neural Computing and Applications, 22, 257–267, 2013.
Song, W., Jian-Jun, H., Zhao-Hong, Li., Liang, H.: Chaotic system and QR factorization based robust digital image watermarking algorithm. J. Cent. South Univ. Technology, No. 18, pp. 116–124, 2011.
Kumar, R., Das, R.R., Mishra, R.R., Dwivedi, R.: Fuzzy entropy based neuro-wavelet identifier-cum-quantifier for discrimination of gases/odors. IEEE sensors Journal. 11, 1548–1555, 2011.
Lei, B., Soon, I.Y., Zhou, F., Li Z., Lei, H.: A robust audio watermarking scheme based on lifting wavelet transform and singular value decomposition. Signal Processing, Vol. 92, No. 9, pp. 1985–2001, 2012.
Daubeches, I., Sweldens, W.: Factoring wavelets into lifting steps. Journal of Fourier Analysis and Applications, Vol. 4, No. 3, pp. 247–269, 1998.
Mangasarian, O.L., Musciant, D.R.: Lagrangian support vector machines. Journal of Machine Learning Research, Vol. 1, pp. 161–177, 2001.
Wu, L., Deng, W., Zhang, J., He, D.: Arnold transformation algorithm and anti Arnold transformation algorithm. In: Proc. of 1st International Conference on Information Science and Engineering (ICISE), pp. 1164–1167, 2009.
Balasundaram, S., Kapil: On Lagrangian support vector regression. Expert System with Applications, No. 37, pp. 8784–8792, 2010.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2018 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Yadav, A.K., Mehta, R., Raj Kumar (2018). Lagrangian Twin SVR Based Grayscale Image Watermarking Using LWT-QR Decomposition. In: Perez, G., Mishra, K., Tiwari, S., Trivedi, M. (eds) Networking Communication and Data Knowledge Engineering. Lecture Notes on Data Engineering and Communications Technologies, vol 4. Springer, Singapore. https://doi.org/10.1007/978-981-10-4600-1_11
Download citation
DOI: https://doi.org/10.1007/978-981-10-4600-1_11
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-10-4599-8
Online ISBN: 978-981-10-4600-1
eBook Packages: EngineeringEngineering (R0)