Abstract
In order to improve the efficient and simple the steps of generation an image hashing, a security and robustness image hashing algorithm based on Slant transform (ST) is proposed in this paper. By employing coefficients of Slant transform, a robust hashing sequence is obtained by preprocessing, feature extracting and post processing. The security of proposed algorithm is totally depended on the user-key which are saved as secret keys. For illustration, several benchmark images are utilized to show the feasibility of the image hashing algorithm. Experimental results show that the proposed scheme is robust against perceptually acceptable modifications to the image such as JPEG compression, mid-filtering, and rotation. Therefore, the scheme proposed in this paper is suitable for image authentication, content-based image retrieval and digital watermarking, etc.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
With the rapid development of information-communication and personal computers, copyright protection of digital media as image, video and audio becomes a more and more important issue. Image hash as one of content-based image authentication techniques has become an important research topic recently. An image hash function maps an image to a short binary string based on the image’s appearance to the human eye, so it can be used in authentication, content-based image retrieval and digital watermarking.
Security and robustness are two important requirements for image hash functions. By security, it means that one image should have different function values according to the different applications. By robustness, it means that the hash function should keep invariable by common image processing operations such as additive noise, filtering, compression, etc. The underlying techniques for constructing image hashes can roughly be classified into property-based, such as statistics [1]; interaction relation of transform field decomposition coefficients [2]; vision-based feature points [3], etc.; and content-based, such as transform field significantly coefficients [3–5]. Typical case of property-based image hash is proposed by Venkatesan et al. [1], which gets statistics by using decomposition coefficients of discrete wavelet transform (DWT). A relation-based technique generates a hash sequence by employing invariant relation of image blocks, which is expect robust to JEPG compression. For sensitive to geometric attacks, the vision-based image hash is inefficacy under common image processing. On the contrary, the content-based algorithm for its super robustness performance became more and more popular, but an expensive search is needed to handle manipulations. Recently, a new kind of robust image hashing algorithms based on non-negative matrix factorization (NMF) [6] is proposed. It is robust against most image processing, minimizes collision probability and identified the tampered place.
In this paper, an image hashing algorithm based on Slant transform (ST) is proposed for certain application. The scheme extracts a robust feature vector to generate a content-based hash sequence, which includes three-step preprocessing, feature generation and post processing. To improve the security of the proposed scheme, the user-keys are used as the encryption keys. Experimental results show that the proposed scheme is robust against common image processing. The remaining of this paper is organized as follows. The concept of Slant transform is briefly introduced in Sect. 2. The framework and the details of the proposed scheme are described in Sect. 3. In Sect. 4, some experimental results and comparison are presented. Security analysis is presented in Sect. 5. A conclusion is drawn in Sect. 5.
2 Slant Transform
The concept of an orthogonal transformation containing Slant basis vector was introduced by Enomoto and Shibata [7, 8]. The Slant vector is a discrete saw tooth waveform decreasing in uniform steps over its length. It has been seen that Slant vectors are suitable for efficiently representing gradual brightness change in a face image line.
Slant Matrix Construction: If S(n) denotes the \( N \times N \) Slant matrix (N = 2n), then
The Slant matrix for N = 4 can be written as
where a and b are real constants to be determined subject to the following conditions:
-
(1)
step size must be uniform;
-
(2)
S(2) must be orthogonal.
The properties of Slant transform are as follows:
-
(1)
The Slant transform is real and orthonormal
$$ S = S^{*} $$(3)$$ S^{ - 1} = S^{t} $$(4) -
(2)
It is a fast algorithm reducing the complexity to \( O(N\log_{2} N) \) for \( N \times 1 \) vector;
-
(3)
It is very good in energy compaction for facial images. Very few coefficients are sufficient for recognizing the stored image of face in database.
The above Slant matrices [9] are used to define the ST as:
where \( D_{x} (n)^{'} = [D_{x} (0)D_{x} (1) \cdots D_{x} (N - 1)] \), \( X(n)^{'} = [X(0)X(1) \cdots X(N - 1)] \) and S(n) is \( N \times N \) Slant Matrix.
The 2D forward and inverse Slant transform filter bank are shown in Fig. 1.
3 Proposed Algorithms
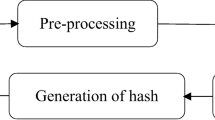
For analysis the performance of Slant transform in image hashing algorithm. An image hashing algorithm based on Slant transform is proposed in this paper. The image hash scheme can be constructed by preprocessing, extracting and post processing appropriate image features. In order to improve the property of feature extracting [10–12], the preprocessing of image is always used. The common image preprocessing includes applying a low-pass filter, rescaling, or adjusting the components of image, and so on. But in this paper, for analysis the performance of Slant transform, all the processing of image seemed as attacks to original image. To achieve robustness, security, and compactness, the feature extraction is the most important stage of constructing an image hash. A robust image feature extraction scheme should withstand various image processing that does not alter the semantic content. Various image hashing schemes mainly differ in the way randomized features and extracted. For post-processing, the aim is compression the length of hash sequence and without less the magnitude feature.
In this paper, in order to analysis the performance of Slant transform in image hashing algorithm, a novel robust image hashing algorithm based on Slant transform is proposed. The framework of proposed hashing algorithm is shown in Fig. 2, which includes the following steps:
-
(1)
Block image: block original image to n × n sub-images. For example, the blocks size is 8 × 8.
-
(2)
Slant transform: using the Slant transform to every block images.
-
(3)
Feature extraction: selected the middle-frequency coefficients by user-key.
-
(4)
Compression: compression the selected coefficients, and obtain the image hashing finally.
4 Performance Results
Performance metrics and experiment setup: to measure the performance of image hash, the normalized Hamming distance between the binary hashes is employed. The defined of normalized Hamming distance is:
where h 1 (k), h2(k) are different image hash sequence values; L is the length of image hash. The normalized Hamming distance d has the property that for dissimilar images, the expected of d is closed to 0.5, else the expected is closed to 0.
Several benchmark images (such as Lena, Baboon, Peppers, F16, Cameraman, etc.) are used to test the performance of the proposed scheme. Images used in this paper are shown in Fig. 3 and Table 1.
5 Conclusion
In this work, a novel robust image hash scheme for certain application is proposed. The Slant transform is used for constructing robust image hashes, and the user-key are used as the encryption key. The image is first blocked to sub-images, then after the Slant transform of every block image, feature vector is extracted from the transform field coefficients, finally the resulting statistics vector is quantized and the binary hashes sequence is obtained. Experimental results show that the proposed scheme is robust against common image processing such as JPEG compression, mid-filtering, and rotation. Therefore, the scheme proposed in this paper is suitable for image authentication, content-based image retrieval and digital watermarking.
References
Soo, C.P., Jian, J.D.: Closed-form discrete fraction and affine Fourier transforms. J. IEEE Trans. Signal Process. 48(5), 1338–1353 (2000)
Ozaktas, H.M., Arikan, O.: Digital computation of the fractional Fourier transform. J. IEEE Trans. Signal Process. 9, 2141–2149 (1996)
Pei, S.C., Yeh, M.H.: Two Dimensional discrete fractional Fourier transform. J. Signal Process. 67, 99–108 (1998)
Venkatesan, R., Koon, S.M., Jakubowski, M.H., Moulin, P.: Robust image hashing. In: IEEE Conference on Image Processing, pp. 664–666 (2000)
Fridrich, J., Goljan, M.: Robust hash functions for digital watermarking. In: IEEE International Conference on Information Technology: Coding and Computing, pp. 178–183 (2000)
Mihcak, K., Venkatesan, R.: New iterative geometric techniques for robust image hashing. In: ACM Workshop on Security and Privacy in Digital Rights Management Workshop, pp. 13–21 (2001)
Enomoto, H., Shibata, K.: Orthogonal transform coding system for television signals. IEEE Trans. Electromagn. Compat. 13(3), 11–17 (1971)
Vaid, S., Mishra, D.: Comparative analysis of palm-vein recognition system using basic transforms. In: IEEE International Advance Computing Conference, pp. 1105–1110 (2015)
Gupta, J., Chanda, B.: An efficient slope and slant correction technique for off-line handwritten text word. In: 4th International Conference of Emerging Applications of Information Technology, pp. 204–208 (2014)
Jin, L., Qian, W., Cong, W., Ning, C., Kui R., Wenjing, L.: Fuzzy keyword search over encrypted data in cloud computing. In: the 29th IEEE International Conference on Computer Communications (INFOCOM 2010), pp. 441–445. IEEE Press (2010)
Jin, L., Xiaofeng, C., Mingqiang, L., Jingwei, L., Patrick, L., Wenjing, L.: Secure deduplication with efficient and reliable convergent key management. IEEE Trans. Parallel and Distrib. Syst. 25(6), 1615–1625 (2014)
Jin, L., Man, H.A., Willy, S., Dongqing, X., Kui, R.: Attribute-based signature and its applications. In: 5th ACM Symposium on Information, Computer and Communications Security (ASIACCS 2010), pp. 60–69. ACM (2010)
Acknowledgments
The work presented in this paper was supported by Guangdong Provincial Science and Technology Program (No. 2014A020208139); Distinguished Young Talents in Higher Education of Guangdong (No. 2013LYM-0057). Delong Cui is corresponding author.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2016 Springer Science+Business Media Singapore
About this paper
Cite this paper
Zuo, J., Cui, D., Yu, H., Li, Q. (2016). Image Feature Extract and Performance Analysis Based on Slant Transform. In: Li, K., Li, J., Liu, Y., Castiglione, A. (eds) Computational Intelligence and Intelligent Systems. ISICA 2015. Communications in Computer and Information Science, vol 575. Springer, Singapore. https://doi.org/10.1007/978-981-10-0356-1_52
Download citation
DOI: https://doi.org/10.1007/978-981-10-0356-1_52
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-10-0355-4
Online ISBN: 978-981-10-0356-1
eBook Packages: Computer ScienceComputer Science (R0)