Abstract
Currently Supervisory Control And Data Acquisition (SCADA) system intends to be connected to the open operating environment. Thus, protecting SCADA systems from malicious attacks is getting more and more attention. A key management scheme is essential for secure SCADA communications. In this paper, we propose an efficient key management scheme for SCADA systems with good security properties and performance.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
Introduction
In order to deliver critical services, such as water, sewerage and electricity distribution, nations are increasingly depends on Supervisory Control And Data Acquisition (SCADA) systems. As the change of the operating environment in SCADA system from close to open, the risk of SCADA incidents occurring is increasing. Nowadays, SCADA system has been exposed to a wide range of network security problems. If the SCADA system is damaged from the attacks, this system can have a widespread negative effect to society. One critical security requirement for SCADA systems is that communication channels need to be secured. Secure keys need to be established before cryptographic techniques can be used to secure communications.
Note that un-encrypted data communication via networks is vulnerable to several types of attacks. Therefore, secure data communication between each device is required to secure the SCADA system. Secure key management is essential for data encryption. In this paper, we focus on the key management scheme for SCADA systems and propose an efficient key management scheme (EKMS) with good security properties. Compared with the previous schemes, the presented key management scheme is more efficient in terms of the communication cost. Our scheme is based on a symmetric balanced incomplete block design (SBIBD), which can provide the authentication service and resist different key attacks. The structure of SBIBD makes the computation of a common conference key for each remote terminal unit (RTU) quite convenient.
The rest of this paper is organized as follows: In the following section, related work is briefly introduced. The proposed key management scheme is described in detail in section Efficient Key Management Scheme for SCADA System. Security analysis and performance analysis of our scheme are presented in section Security Analysis and Performance Analysis. Finally, the conclusions of this paper are covered in section Conclusions.
Related Work
A SCADA system consists of three types of equipment communicating with each other: (1) human–machine interface (HMI) that operators interact with; (2) master terminal unit (MTU) that provides supervisory control of an RTU; and (3) the remote terminal unit (RTU) that interacts with the physical environment. In this paper, the term node will be used to refer to any entity in the system. The structure of SCADA systems is based on master–slave structure, which is shown in Fig. 1. The structure of a SCADA system will normally include one central MTU, which communicates with a hierarchy of other nodes, including Sub-MTU and RTUs. Master stations and sub-master stations, are computers with resources at least as plentiful as a modern desktop computer.
Recently, SKE [1] was proposed by Sandia, where the MTU has to encrypt data with each key of the RTUs individually to broadcast a message. After that, SKMA [2] was proposed, where two types of keys must be managed by an MTU or RTUs. The long-term node-key distribution center (KDC) key is shared between the KDC and a node. The other key is the long-term node–node key shared between two nodes. Later, ASKMA [3] proposed a key-management scheme suitable for secure SCADA communication using a logical key hierarchy to support broadcast communication and multicast communication, but it may be less efficient.
Due to the constrains of low-rate data transmission and real-time processing in different operational environment, satisfying the security requirements of confidentiality, integrity and availability in a SCADA system is really a challenging issue. In this paper, resort to a symmetric balanced incomplete block design (SBIBD), we design a novel key management scheme for SCADA systems with good security properties and performance.
Efficient Key Management Scheme for SCADA System
In this section, we propose an efficient key management scheme for SCADA system. By our scheme, the communication among Sub-MTUs can be secure and efficient, so can the communication among RTUs. The process of key management among RTUs is described as follows. Note that the process of key management among Sub-MTUs is similar to that of RTUs.
Each RTU registers to the Sub-MTU and gets their private key. After that, every RTU can process the key agreement to compute the common conference key. First of all, the Sub-MTU chooses two prime order group \( G_{1} \) and \( G_{2} \) and a modified Weil pairing map \( \widehat{e} \) defined in [4]. Next, the Sub-MTU selects two one-way hash functions \( H:\{ 0,1\}^{*} \to G_{1} \) and \( h:\{ 0,1\}^{*} \to Z_{q}^{*} \) where H maps its arbitrary length to a nonzero point of \( G_{1} \) while h maps its input with arbitrary length to a nonzero integer. At last, the Sub-MTU picks a random integer \( s \in Z_{q}^{*} \) as its private key, computes its public key \( P_{pub} = s\mathcal{G} \), and publishes \( \left( {p,q,G_{1} ,G_{2} ,\mathcal{G},\widehat{e},P_{pub} ,H,h} \right) \), but keeps s secret. Each RTU \( U_{i} \)’s identity is \( ID_{i} \in \left( {0,1} \right)^{*} \). The Sub-MTU computes \( U_{i} \)’s public key \( Q_{i} = H(ID_{i} ) \) and then \( U_{i} \)’s private key \( S_{i} = sQ_{i} \) which is issued to \( U_{i} \) via a secure channel.
The common conference key among RTUs is calculated by employing SBIBD, where the number of blocks is the same as that of participants. We choose a (7, 4, 2)-design. Let a finite set X = {1, 2, 3, 4, 5, 6, 7}, then \( B_{1} \) = {1, 2, 4, 7}, \( B_{2} \) = {1, 2, 3, 5}, \( B_{3} \) = {2, 3, 4, 6}, \( B_{4} \) = {3, 4, 5, 7}, \( B_{5} \) = {1, 4, 5, 6}, \( B_{6} \) = {2, 5, 6, 7}, \( B_{7} \) = {1, 3, 6, 7}. Accordingly, a (7 × 7) incidence matrix L is depicted in Fig. 2. The rows and columns of the matrix correspond to the blocks and the elements, respectively. The entry \( l_{ij} \) in the ith row and the jth column of L is a 1 if the block i contains the element j and is a 0 otherwise.
For computing the common conference key among RTUs, two rounds are required in our scheme.
-
1.
Each RTU \( U_{i} \) selects a random number \( r_{i} \) as secret key by itself for every session and then calculates \( m_{i} = \widehat{e}\left( {\mathcal{G},r_{i} S_{i} } \right) \). Simultaneously, \( U_{i} \) calculates \( T_{i} = r_{i} Q_{i} \). Let \( D_{i} = \{ m_{i} ,T_{i} \} \). RTU i receives message \( D_{j} \) from RTU j in case \( l_{ij} = 1 \) and \( j \ne i \), namely \( j \in B_{i} - \{ i\} \). \( m_{i} \) is used for generating conference key while \( T_{i} \) is used for authentication. We now describe the key agreement process from the viewpoint of RTU 1. \( U_{1} \) receives \( D_{2} \), \( D_{4} \), \( D_{7} \) from \( U_{2} \), \( U_{4} \), \( U_{7} \) and then makes
where \( c_{ij} = \prod\nolimits_{{x \in B_{i} - \{ j\} }} {m_{x} } \) and \( W_{ij} = \sum\nolimits_{{x \in B_{i} - \{ j\} {\text{ and }}j \ne i}} {T_{x} } \). In the viewpoint of RTU 1, we have that \( c_{1j} = \prod\nolimits_{{x \in B_{1} - \{ j\} }} {m_{x} } \) and \( W_{1j} = \sum\nolimits_{{x \in B_{1} - \{ j\} {\text{ and }}j \ne 1}} {T_{x} } \). Simultaneously, other RTUs do the same process.
-
2.
Let \( E_{ji} = \{ c_{ji} ,W_{ji} \} \). RTU i receives \( E_{ji} \) from RTU j in case \( l_{ji} = 1 \), \( j \ne i \). Here, similar to that in round 1, \( c_{ji} \) is used for generating conference key while \( W_{ji} \) is used for authentication. Particularly, \( U_{1} \) receives \( E_{j1} \) from RTU j, if \( l_{j1} = 1 \), \( j \ne 1 \). Therefore, \( U_{1} \) receives \( E_{21} \), \( E_{51} \), \( E_{71} \) from \( U_{2} \), \( U_{5} \), \( U_{7} \) and derives \( c_{21} \), \( c_{51} \), \( c_{71} \). Then the common conference key K is calculated as \( K = m_{1} \times c_{11} \times c_{21} \times c_{51} \times c_{71} = \widehat{e}\left( {\mathcal{G},2\sum\nolimits_{i = 1}^{7} {r_{i} S_{i} } } \right) \), where \( c_{21} = \widehat{e}\left( {\mathcal{G},r_{2} S_{2} + r_{3} S_{3} + r_{5} S_{5} } \right) \), \( c_{51} = \widehat{e}\left( {\mathcal{G},r_{4} S_{4} + r_{5} S_{5} + r_{6} S_{6} } \right) \), and \( c_{71} = \widehat{e}\left( {\mathcal{G},r_{3} S_{3} + r_{7} S_{7} + r_{6} S_{6} } \right) \).
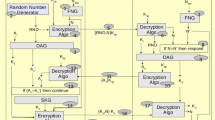
Then, following our scheme, the process for calculating the common conference key among all the RTUs is shown in Fig. 3.
In our scheme, we take advantage of RTUs’ identity information for authentication.
-
1.
Let \( D_{i} = \{ m_{i} ,T_{i} \} \), RTU i receives \( D_{j} \) from RTU j in case \( l_{ij} = 1 \) and \( j \ne i \). We now describe the authentication process from the viewpoint of RTU 1. \( U_{1} \) receives \( D_{2} \), \( D_{4} \), \( D_{7} \) from \( U_{2} \), \( U_{4} \), \( U_{7} \) and makes
Hence, \( U_{1} \) can authenticate the entity of \( U_{2} \), \( U_{4} \), \( U_{7} \) only if \( \widehat{e}\left( {P_{pub} ,T_{2} } \right) = m_{2} \), \( \widehat{e}\left( {P_{pub} ,T_{4} } \right) = m_{4} \), and \( \widehat{e}\left( {P_{pub} ,T_{7} } \right) = m_{7} \), respectively. Generally speaking, if \( \widehat{e}\left( {P_{pub} ,T_{i} } \right) = m_{i} \), then \( U_{j} \) can authenticate counterpart’s entity.
-
2.
Let \( E_{ji} = \{ c_{ji} ,W_{ji} \} \) and \( W_{ji} = \sum\nolimits_{{x \in B_{j} - \{ i\} {\text{ and }}j \ne i}} {T_{x} } \). RTU i receives \( E_{ji} \) from RTU j in case \( l_{ji} = 1 \), \( j \ne i \). Particularly, in the viewpoint of RTU 1, \( W_{j1} = \sum\nolimits_{{x \in B_{j} - \{ 1\} {\text{ and }}j \ne 1}} {T_{x} } \,{\text{and}}\, E_{j1} = \{ c_{j1} ,W_{j1} \}.\) \( U_{1} \) receives \( E_{21} \), \( E_{51} \), \( E_{71} \) from \( U_{2} \), \( U_{5} \), \( U_{7} \), then derives \( W_{21} \), \( W_{51} \), \( W_{71} \) and calculates
Therefore, the RTU of \( U_{2} \), \( U_{5} \), \( U_{7} \) can pass the authentication by \( U_{1} \) only if \( \widehat{e}(P_{pub} ,W_{21} ) = c_{21} \), \( \widehat{e}(P_{pub} ,W_{51} ) = c_{51} \), \( \widehat{e}(P_{pub} ,W_{71} ) = c_{71} \), respectively. Broadly speaking, if \( \widehat{e}(P_{pub} ,W_{ji} ) = c_{ji} \), then \( U_{i} \) can authenticate counterpart’s entity.
Security Analysis and Performance Analysis
A passive adversary tries to learn information about the conference key by eavesdropping on the broadcast channel. We show that an eavesdropper cannot get any information about the secret key \( r_{i} \) of \( U_{i} \) due to Weil Diffie-Hellman (WDH) problem [5] in \( \left( {G_{1} ,G_{2} ,\widehat{e}} \right) \) and discrete algorithm problem (DLP) in elliptic curves. In active attack, an adversary not only just records the data, but also can alter, inject, intercept and replay messages. Our protocol can be able to provide the authentication service by sending a special message \( T_{i} \) and \( W_{ji} \) in first round and second round, respectively. Our scheme has the security properties of known session key security, perfect forward secrecy, key-compromise impersonation resistance and no key control.
The communication cost of previous schemes are all \( O(n^{2} ) \), while the communication cost of our scheme is only \( O(n\sqrt n ) \)even though the communication round is 2.
Conclusions
SCADA system is a significantly important system that plays a very important role in national infrastructure, such as electric grids and water supplies. However, SCADA system is becoming increasingly vulnerable to adversarial manipulation due to the extreme operational environment. In this paper, we present a novel key management scheme for SCADA systems with good performance and security properties. We believe that our scheme must be promising in the secure communication in SCADA system in the future.
References
Beaver C, Gallup D, Neumann W, Torgerson M (2002) Key Management for SCADA. Available: http://www.sandia.org/ scada/documnets/013252.pdf
Colin RD, Boyd C, Manuel J, Nieto G (2006) SKMAA key management architecture for SCADA systems. In: 4th Australasian information security workshop, pp 138–192
Choi D, Kim H, Won D, Kim S (2009) Advanced key management architecture for secure SCADA communications. IEEE Trans Power Del 24(3):1154–1163
Boneh D, Franklin M (2001) Identity-based encryption from weil pairing. In: Advances in Cryptology-CRYPTO01, Lecture Notes in Computer Science, vol 2139, pp 213–229
Kim Y, Perrig A, Tsudik G (2004) Group key agreement efficient in communication. IEEE Trans Comput 53(7):905–921
Acknowledgments
This work was supported by the research fund from Nanjing University of Information Science and Technology under Grant No. S8113003001, National Science Foundation of China under Grant No. 61272421.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2014 Springer Science+Business Media Dordrecht
About this paper
Cite this paper
Shen, J., Wang, J., Ren, Y., Zhang, J., Wang, S. (2014). Efficient Key Management Scheme for SCADA System. In: Huang, YM., Chao, HC., Deng, DJ., Park, J. (eds) Advanced Technologies, Embedded and Multimedia for Human-centric Computing. Lecture Notes in Electrical Engineering, vol 260. Springer, Dordrecht. https://doi.org/10.1007/978-94-007-7262-5_70
Download citation
DOI: https://doi.org/10.1007/978-94-007-7262-5_70
Published:
Publisher Name: Springer, Dordrecht
Print ISBN: 978-94-007-7261-8
Online ISBN: 978-94-007-7262-5
eBook Packages: EngineeringEngineering (R0)