Abstract
In this chapter, the authors presents a new spread-spectrum based secure multiple watermarking (image and text) method for medical images in wavelet transform domain. The proposed method is applied for embedding patient identity reference as text watermark and telemedicine centre logo as the image watermark into the host medical image. The algorithm is based on secure spread-spectrum technique where pseudo-noise (PN) sequences are generated corresponding to each watermark bit of the image watermark. These PN sequences are embedded column wise into the selected wavelet coefficients in the DWT sub-band. The selection of the wavelet coefficients for embedding is performed by thresholding the coefficient values present in that column. In order to enhance the robustness of text watermarks, an error correcting code (ECC) is applied to the ASCII representation of the text watermark before embedding. The results are obtained by varying the gain factor, sub-band decomposition levels, size of watermark, and different cover images. The performance of the proposed watermarking method is analyzed against known attacks. The method was found to be robust against such attacks. Further, the performance of the proposed method has been extensively evaluated for the text watermark along with BCH code and encryption techniques. The performance of the methods are compared with other reported techniques and have been found to be giving superior performance in terms of robustness, imperceptibility, embedding capacity and security as suggested by other authors. Moreover, the performance of the multiple watermarking method is also tested with encryption and BCH error correction code simultaneously.
Access provided by CONRICYT-eBooks. Download chapter PDF
Similar content being viewed by others
Keywords
6.1 Introduction
The significant advancements in information and communication technologies (ICT) [1] has opened up newer opportunities for telemedicine by facilitating medical data transmission across geographical boundaries through Internet, mobile networks, and other wireless/wired communication channels and thus covering rural/remote areas, accident sites, ambulance, and hospitals. However, the transmission of medical data over an open communication channel poses different possibilities of threat that can severely affect its authenticity, integrity, and confidentiality [2]. Digital watermarking studies have always been driven by the improvement of robustness and a current security tool to protect electronic patient record (EPR) [3].
On the contrary, security has received little attention in the watermarking community. The first difficulty is that security and robustness are neighbouring concepts, which are hardly perceived as different. Security deals with intentional attacks whereas robustness is observed as degradation in data fidelity due to common signal processing operations. Also, digital watermarking may not be secure despite its robustness [4]. Therefore, security of the watermark becomes a critical issue in various applications. The problem of watermark security can be solved using spread-spectrum scheme [2, 5,6,7,8,9,10]. Spread-spectrum is a technique designed to be good at combating interference due to jamming, hiding of a signal by transmitting it at low power, and achieving secrecy. These properties make spread-spectrum very popular in present-day digital watermarking.
The subsequent section of the chapter is structured as follows: The related and recent state-of-the-art techniques are provided in Sect. 6.2 . The main contribution of the work is summarized in Sect. 6.3 . The spread-spectrum Watermark Design is reported in Sect. 6.4 . Section 6.5 describes the proposed work. Experimental results and brief analysis of the work is reported in Sect. 6.6 . Next, our summary of the chapter is presented in Sect. 6.7 .
6.2 Related Work
Brief reviews of recent and related watermarking methods are presented as follows:
Recently, in [2] an image watermarking scheme based on spread-spectrum technique was proposed in which different watermark messages were hidden in the same transform coefficients of the cover image using uncorrelated codes, i.e. low cross correlation value (orthogonal/near orthogonal) among codes. The authors have also proposed another algorithm [5] based on spread-spectrum technique in which two different pseudo noise (PN sequence) vectors of size identical to the size of each sub-band column are generated for each watermark message bit. This algorithm further enhances the watermarking capacity in wavelet domain. The performance of the algorithm in [5] has been analysed for text watermark in [10]. These methods are robust and secure against known attacks. D-Ferrer and Sebe´ [11] proposed a spread spectrum based invertible watermarking method for image authentication purpose in lossless format. The method is robust and highly imperceptible. Das et al. [12] proposed a watermarking method based on spread spectrum technique. The method is designed from the analytical study of state transition behavior of non-group cellular automata and the basic cryptography/encryption scheme to provide the data authenticity and security. Multiple messages have been embedded using complimentary modulation function with M–ary modulation. The experimental results have shown that the method is robust against various signal processing attacks. Interleaving and interference cancellation methods are applied to improve the performance of the method as compared to conventional matched filter detection.
Basant et al. [2] proposed a secure spread-spectrum based watermarking algorithms for embedding sensitive medical information such as doctor signature and hospital logo into radiological image for identity authentication purposes. These watermarking schemes used watermarks in binary image format only. In this method, different watermark messages are hidden in the same transform coefficients of the cover image using PN code. Performance of the method has been analyzed by varying the gain factor, sub-band decomposition levels, size of watermarks, wavelet filters and medical image modalities. The simulation results have shown that the proposed method achieved higher security and robustness against JPEG attacks. Also, they proposed another algorithm [5] based on spread-spectrum technique in which, two different pseudo noise (PN sequence) vectors of size identical to the size of each sub-band column are generated for each watermark message bit. So, this algorithm enhanced the watermarking capacity when compared with previous algorithm as proposed in [2]. Performance of the spread-spectrum based watermarking algorithm [5] has been tested for text watermark in [10]. The algorithm is applied for embedding text file represented in binary arrays using ASCII code into host digital radiological image for potential telemedicine applications. In order to enhance the robustness of text watermarks like patient identity code, BCH (Bose, Ray-Chaudhuri, Hocquenghem) error correcting code (ECC) is applied to the ASCII representation of the text watermark before embedding. Robustness and performance of the scheme was tested against some known signal processing attacks like compression, filtering, channel noise, sharpening, and histogram equalization.
Singh et al. [13] presents a robust and secure digital watermarking scheme for its potential application in tele-medicine. The algorithm embeds different medical text watermarks into selected sub-band DWT coefficients of the cover medical image using spread-spectrum technique. In the embedding process, the cover image is decomposed up to third level DWT coefficients. Three different text watermarks are embedded into the selected horizontal and vertical sub band DWT coefficients of the first, second and third level
The medical image watermarking approaches in general have focused on achieving secure and bandwidth efficient transmission of medical data. Multiple watermarking of medical images aims to simultaneously embed various types of medical watermarks on the cover medical image addressing the issues of data security, data compaction, unauthorized access and temper proofing. The proposed multiple watermarking method attempts to simultaneously address these issues consisting of different characteristics and requirements which provide effective protection mechanism for the authenticity of patient identity in the application.
6.3 Main Contribution of the Work
The objective of this method is to provide a valuable solution for different health data management issues to involve hiding multiple watermarks within cover medical image and hidden watermarks can be later recovered at the receiver side for purposes of ownership verification and unique authentication. In order to presents a secure spread-spectrum based multiple watermarking method for medical images in wavelet transform domain. Two different watermarks in the form of image and text are embedding simultaneously into medical cover image. The algorithm uses pseudo-noise (PN) sequences of each image watermark bit, which are embedding column wise into the selected DWT sub-bands coefficients. The selection of the wavelet coefficients for embedding is done by thresholding the coefficient values present in that column. In the embedding process, the cover image is decomposed at second level DWT. The image and text watermark are embedded into the selective coefficients of the first level and second level DWT respectively. In order to enhance the robustness of text watermarks, an error correcting code is applied to the ASCII representation of the text watermark before embedding. The results are obtained by varying the gain factor, sub-band decomposition levels, size of watermark, and different cover images.
The performance of the proposed watermarking method is analyzed against known attacks. The method was found to be robust against such attacks. In addition, the performance of the proposed method has been extensively evaluated for the text watermark along with BCH code and encryption techniques which is presented in Sects. 6.1 and 6.6.2, respectively. The encoded/encrypted text watermark is then embedded at multiple levels of the DWT sub-bands. The performance of the methods are compared with other reported techniques and have been found to be giving superior performance in terms of robustness, imperceptibility, embedding capacity and security as suggested by other authors. Moreover, the performance of the multiple watermarking method is also tested with encryption and BCH error correction code simultaneously in Sect. 6.3. The encryption and BCH error correction code both are applying to the sensitive patient data/report before embedding in to the medical cover image to enhance the security and robustness of the text watermark respectively. The performance of the technique is extensively evaluated and experimental results demonstrated that the method is robust, higher imperceptible, large embedding capacity, and secure than other reported technique.
6.4 Spread-Spectrum Watermark Design
There are two components to build a strong watermark: the watermark structure and the insertion strategy. For a watermark to be robust and secure, these components must be designed correctly. This can be achieved by placing the watermark explicitly in the perceptually most significant components of the data. Once the significant components are located, Gaussian noise is injected therein. The choice of this distribution gives resilient performance against collusion attacks (the mixing of several watermarked versions of the same content). The Gaussian watermark also gives strong performance in the face of quantization [2].
Watermark Structure: In its most basic implementation, a watermark consists of a sequence of real numbers X = x 1 , x 2 ,….…x n . In practice, a watermark is created where each value x i is chosen independently according to Gaussian distribution N (0, 1), where N (μ , σ 2 ) denotes a normal distribution with mean μ and variance σ 2 .
Watermarking Procedure: Extract from host digital document D, a sequence of values V = v 1 , v 2 ,……v n , into which a watermark X = x 1 , x 2 ,….…x n is inserted to obtain an adjusted sequence of values W = w 1 , w 2 ,……,w n and then insert it back into the host in place of V to obtain a watermarked document (D*).
Inserting Watermark: When X is inserted into V to obtain W, a scaling parameter k is specified, which determines the extent to which X alters V. The method for computing W is
The factor α can be viewed as a relative measure of embedding strength which is also known as gain factor (α). A large value of α will cause perceptual degradation in the watermarked document.
Choosing the Length ‘n’ of the Watermark: The choice of length n indicates the degree to which the watermark is spread out among the relevant components of the host image. In general, as the numbers of altered components are increased the extent to which they must be altered decreases.
Extracting and Evaluating the Similarity of Watermarks: It is highly unlikely that the extracted mark X ∗ will be identical to the original watermark X. Even the act of re-quantizing the watermarked document for delivery will cause X ∗ to deviate from X. The similarity of X and X ∗ is measured by
Many other measures are possible, including the standard correlation coefficient. To decide whether X and X ∗ match, one determines whether sim(X, X ∗) > T, where T is some specified threshold. Setting the detection threshold is a classical decision estimation problem.
6.5 Proposed Method
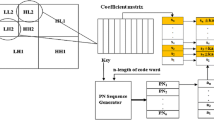
For embedding medical text and image watermarks, a new DWT based spread-spectrum watermarking algorithm is proposed that uses medical image as cover. Dyadic sub-band decomposition is performed on the cover image using Haar wavelet transform. Table 6.1 shows the robustness requirement of EPR data at different sub-bands. This table indicates importance of the data according to robustness required. In the proposed method, the image watermark representing health centre name in binary image format is embedded into intermediate frequency sub-bands (HL1 and LH1) of the first level DWT coefficients and the patient’s identity/reference as text watermark is embedded into selected sub-band DWT coefficients (HL2 and LH2) of the second level. The important allocation of watermarks according to robustness and capacity criteria at different sub-band is shown in Table 6.1.
The text watermark of eight characters representing patient identification code is converted into binary format using ASCII codes. In the embedding process, sub-band decomposition of the cover medical image is performed to obtain second level DWT coefficients. Different watermark bits are hidden in the same transform coefficients of the cover image using uncorrelated codes, i.e. low cross correlation value (orthogonal/near orthogonal) among codes. For each message (text and image) bit, two different pseudo noise (PN) sequence vectors of sizes identical to the size of DWT column vector are generated. A PN sequence is a sequence of binary numbers which appears to be random, but is in fact perfectly deterministic. The sequence appears to be random in the sense that the binary values and groups or runs of the same binary value occur in the sequence in the same proportion. PN sequences are a good tool for watermarking because of the following reasons [14]:
-
(i)
PN sequence is having correlation properties, noise like characteristics and resistance to interference.
-
(ii)
PN generator produces periodic sequences that appear to be random.
-
(iii)
PN sequences are generated by an algorithm that uses an initial seed.
-
(iv)
The PN sequence generated is actually not statically random but will pass many test of randomness.
-
(v)
Unless the algorithm and seed are known, the sequence is impractical to predict.
Since, the security level of the watermarking algorithm depends on the strength of its secret key, a gray scale image of size 1 × 35 is used as a strong key for generating pseudorandom sequences.
Based on the value of the bit of the message vector, the respective two PN sequence pairs are then added/subtracted to/from selective columns of wavelet coefficient. This selection is done by thresholding the coefficient values present in that column. In each selected sub-band, the complete coefficient range is grouped in ten equally spaced bins. The bin having the maximum number of coefficients is chosen for embedding. The embedding procedure of the proposed method is shown in Fig. 6.1.
The column wise DWT coefficients of second level horizontal and vertical sub-bands are taken for embedding. In each column, the coefficients under the threshold criteria are used for embedding and rest of the coefficients remains unchanged. Example embedding process illustrated in Fig. 6.1 shows that values of the coefficients S2 and S3 are changed after watermarking as these values lie inside the threshold range while values of coefficient S1 and S4 lying outside the threshold criteria remain same. The wavelet coefficients of cover image are divided into k number of bins having equal width for desired level. From these k numbers of bins, max_bin, having maximum number of coefficients is selected. In medical images, DWT coefficients are mostly concentrated toward the origin. Thus, max_bin has coefficients concentrated toward origin.
b 1 and b 2 are the minimum and maximum values within max_bin. In each column, the coefficients under the threshold criteria are used for embedding the data bit as follows:
where V is DWT coefficient of the cover image, W is the modified DWT coefficient after watermark embedding, α is the gain factor, X is the PN matrix and b is the message bit that has to be embedded. The corresponding column of the DWT coefficient, to which the generated sequence has to be added/subtracted, is decided by the following relation:
where p is the column in which sequence has to be added, N/4 is the number of columns in coefficient matrix. Generation of a pair of PN sequences for embedding each bit enhances the security of the watermarking algorithm. In the next subsection process for the embedding of message is discussed.
6.5.1 Message Embedding Algorithm
-
1.
Read the cover image I(M,N) of size M × N.
-
2.
Read the message to be hidden and convert it into binary sequences Dd (d=1 to n).
-
3.
Transform the host image using “Haar” wavelet transform and get first and second level sub-band coefficients.
-
4.
Generate n different PN sequence pairs (PN_h and PN_v) each of \( \frac{M}{4}\times 1 \) using a secret key to reset the random number generator.
-
5.
for d = 1 to n,
Case 1:
When message vector bit=0
Hence 1≤ p ≤(N/4), For i=1 to (M/4)
Case 2:
When message vector bit=1
Hence 1≤ p ≤(N/4), For i = 1 to (M/4)
where α is the gain factor used to specify the strength of the embedded data.
-
6.
Apply inverse “Haar” Wavelet transform to get the final watermarked imageI w (M, N).
6.5.2 Message Extraction Algorithm
The DWT coefficients of watermarked image are divided into k number of bins having equal width for desired level. From this k number of bins, max_bin, having maximum number of coefficients is selected. To detect the watermark the same PN sequence vectors used during insertion of watermark are generated by using same state key and determine their correlation with the corresponding selected column’s detail sub-bands DWT coefficients. Average of n correlation coefficients corresponding to each PN sequence vector is obtained for both LH and HL sub-bands. Mean of the average correlation values are taken as threshold, T for message extraction. During detection, if the average correlation exceeds T for a particular sequence a “0” is recovered; otherwise a “1”. The recovery process then iterates through the entire PN sequence until all the bits of the watermark have been recovered. For extracting the watermark, following steps are applied to the watermarked image:
-
1.
Read the watermarked image I w (M, N)
-
2.
Transform the stego image using “Haar” Wavelet transform and get first and second level sub-band coefficients.
-
3.
Generate one’s sequences (msg) equal to message vector (from 1 to n).
-
4.
Generate n different PN sequence pairs (PN_h1 and PN_v1) each of size \( \frac{M}{4}\times 1 \)using same secret key used in embedding to reset the random number generator.
-
5.
for d = 1 to n, Generate PN_h2(d) and PN_v2(d) as
for i = 1 to (M/4)
-
6.
Calculate the correlations between the values ccH1 and PN_h2 and store in corr_H (d) and ccV1 and PN_v2 corr_V (d).
corr_H (d) = correlation between PN_h2 (d) and ccH1 (p th column)
corr_V (d) = correlation between PN_v2 (d) and ccV1 (p th column)
Hence 1≤ p ≤ \( \frac{N}{4} \)
-
7.
Calculate average correlation avg_corr (d) = (corr_H (d)+corr_V(d))/2
-
8.
Calculate the corr(mean) = mean of all the values stored in avg_corr (d).
-
9.
Extract the watermark bit stream, using the relationship given below
for d = 1 to n
if avg_corr (d) > corr (mean)
Msg (d) = 0.
-
10.
Convert the bit sequence to message watermark to get the recovered watermark.
6.6 Experimental Results and Performance Analysis
In this section, the performance of combined DWT-SS watermarking algorithm is extensively evaluated for multiple watermarks in the form of image and text. The gray–level MRI image of size 512 × 512 [15] is taken as the cover image. The health centre logo of “NITK” as image watermark and patient’s identity/reference “MRI_1031” as text watermarks. Also, BCH code is applied to the ASCII representation of the text and the encoded text watermark is then embedded. The resulting bits are embedded in two different ways: without ECC and coded by BCH (127, 64) ECC code. The encoded text watermark length for BCH is 127 bits. Strength of watermark is varied by varying the gain factor (α) in the watermarking algorithm. For testing the robustness and quality of the watermarked image of the proposed scheme MATLAB is used. The quality of the watermarked image (as shown in Fig. 6.2) is evaluated by the parameter PSNR and robustness by NC (for image) and BER (text). Figure 6.2 shows the cover MRI image and watermarked images obtained at different gain factors. Extracted watermarks along with the original watermarks are shown in Fig. 6.3. Figure 6.4 shows that larger size watermarks are more clearly identified during extraction.
In the experiments, we are using the gain factor (α) as 1.0 to 5.0 and the value of PSNR, NC and BER are illustrated in Table 6.2, 6.3, 6.4 and 6.5. The performance of the proposed method is better in comparison with the existing [2, 5] method shown in the Table 6.6. In Table 6.2, BCH code performance (determined PSNR and NC values) up to 127 text bits has been evaluated without any noise attack. The maximum PSNR value is 31.92 dB and BER = 0.0472 at α = 1.0 to 5. Figure 6.5 shows the comparison of BER performance as obtained by the proposed method using/without using BCH code. Table 6.3 shows the NC and BER performance of the proposed method against eight different attacks. The highest NC value of 0.7402 has been obtained against the Histogram equalization attack however; the lowest NC is 0.2162 against the Median Filtering attack. The highest BER is obtained as 0.0551 against the Median Filtering attack. However, without BCH code it was 0.0629 for the same attack. It is observed that larger the gain factor, stronger is the robustness and smaller the gain factor, better is the image quality.
Figure 6.6 shows the graphical representation of the BER performance obtained by the proposed method with and without BCH code against different attacks. Table 6.4 shows the effect of watermark size on the PSNR, NC and BER performance of the proposed watermarking method. It is found that PSNR performance of the watermarked image decreases with the increase in the size of the watermark, but subsequently an improvement in the correlation between original and extracted watermarks is observed. Table 6.5 shows the effect of cover image at α = 1.5 on PSNR, NC and BER. The highest NC and BER value were obtained with Ultrasound and MRI image respectively. However, the highest PSNR value (29.82 dB) has been obtained with MRI image. Table 6.6 provides the comparison of PSNR and NC performance obtained by the proposed technique with other reported methods. The maximum NC value with proposed method has been obtained as 0.7544 against 0.659 and 0.3572 obtained by Basant et al. in [2, 5], respectively. The maximum PSNR value obtained with [2, 5] methods are 37.518 dB and 52.04 dB respectively. However, the maximum PSNR value by the proposed method is 37.75 dB. Overall, the proposed method is better than the existing methods [2, 5]. Figure 6.7 shows the graphical representation of the comparison of robustness (determined NC values) offered by the proposed method with that of [2] at different gain factors.
6.6.1 Performance Evaluation of the Proposed Method for Text Watermarking Using BCH Code
In this subsection, the performance of the above discussed method has been extensively evaluated for text watermark only using BCH code. During the embedding process, the cover image is decomposed up to third level DWT coefficients. For identity authentication purposes, the method uses three different watermarks representing the text watermark such as personal and medical record of the patient, diagnostic/image codes and doctor code/ signature. According to the importance of robustness requirements, three different text watermarks are embedded into the selected horizontal and vertical sub-band DWT coefficients of the first, second and third level, respectively. Selection of these coefficients for embedding purpose is based on threshold criteria defined above in the chapter. It is found that the proposed scheme correctly extracts the embedded watermarks without error and provides high degree robustness against known attacks while maintaining the imperceptibility of watermarked image.
In this method, the doctor’s identification code of eight characters, image/diagnostic code of eight characters and patient name of eight characters are embedded into third level HL3 and LH3 sub-bands, second level HL2 and LH2 sub-bands and the first level HL1 and LH1 sub-bands respectively. Also, BCH error correcting code is applied to the ASCII representation of the text and the encoded text watermark is then embedded into the cover medical images. The resulting bits are embedded in two different ways: without ECC and coded by BCH (127, 64) code. Performance of the proposed method has been extensively evaluated against known attacks and results are compared with other technique [10]. The proposed method gives superior robustness performance without significant degradation of the image quality of the watermarked image. The encoded text watermark length for BCH is 381 bits. The strength of the watermark is tested by varying the gain factor (α) in the watermarking algorithm. Imperceptibility performance of the scheme is evaluated by calculating the PSNR between cover image and watermarked image where as robustness performance is measured by calculating BER between original and the extracted watermark.
Fig. 6.8 shows original MRI image and watermarked image at α = 15. Figure 6.9 shows the extracted watermark image at α = 15. PSNR and BER performance of the proposed watermarking scheme with and without BCH coder are illustrated in Table 6.7. Referring this table it is observed that the highest PSNR obtained without and with BCH coder are 43.96 dB and 40.48 dB respectively (at α = 5) whereas BER obtained without and with BCH coder are 0.0236 and 0.0183 respectively. It is also observed that the watermarking scheme with BCH coder achieves desired ‘0’ BER at gain factor of 15 but its PSNR performance is slightly compromised i.e. 29.46 dB as compared to 34.95 dB achieved without coder.
In Table 6.8, robustness performance of the proposed algorithm with and without BCH coder has been tested at α = 10 against different attacks. With BCH coder, BER value = 0 is obtained against JPEG compression (Quality Factor (QF) = 90) whereas without BCH code it comes out to be 0.0052. It is also observed from the table that the implementation of BCH coder improves the BER performance for sharpening mask noise attack with threshold = 1. Table 6.9 shows PSNR and BER performance of the proposed algorithm for different imaging modalities at varying gain factor. It is observed that Ultrasound image gives maximum PSNR = 41.30 dB at gain factor of 5 whereas minimum BER value = ‘0’ is obtained with MRI image at gain factor of 11. Table 6.10 provides the performance (determined PSNR and BER values) comparison with the existing methods. The maximum BER value with proposed method has been obtained as zero against 1.5306 obtained by Kumar et al. in [10] method. The maximum PSNR value is obtained with this method is 45.51 dB. However, the maximum PSNR value is obtained by the proposed method is 49.12 dB. The existing method [10] can embed only 196 bits only whereas 381 bits can be embedded by the proposed method. Overall, the proposed method is better than the existing method in terms of image quality of the watermarked image, robustness of the extracted watermark and embedding capacity also.
From the above extensive discussion, we have observed some important remarks:
As shown in Table 6.3, the highest value of NC = 0.7402 is obtained for Histogram equalization attack whereas its lowest value of 0.2162 is achieved for median filtering attack. The lowest BER value 0 is obtained for JPEG compression (QF = 30, 50, 70, 90), Sharpening mask (threshold = 0.9), Scaling factor (2 and 2.5), Gaussian LPF (standard deviation = 0.6), Salt and pepper noise (density = 0.02) and Histogram equalization attacks, however, higher value of BER = 0.0551 is observed for median filtering attack. The higher robustness as indicated by NC value = 0.7544 is achieved in our proposed method as compared to other reported techniques [2, 5]. Referring Table 6.6 it is seen that maximum value of NC = 0.7544 is achieved at gain factor '∝' = 5 as compared to its corresponding maximum NC values of ‘0.6590’ and ‘0.3572’ in [2, 5] respectively. Further, it is also evident from Table 6.6 that the proposed method offers up to 63.51% superior performance in terms of robustness over reported techniques [2, 5]. The performance of the proposed watermarking method has been extensively evaluated only for text watermark at multilevel DWT sub-bands. This is carried out by applying BCH code on the EPR data as text watermark before embedding into the cover. The BER of the text watermark has been evaluated against different known attacks as in Table 6.8. The BER = 0 is obtained for JPEG compression (QF = 90), sharpening mask (threshold = 1.0) and Salt and pepper noise (density = 0.001), however, higher value of BER = 0.0603 is obtained for JPEG compression attacks (QF = 5). The PSNR and BER performance of the proposed method is also compared with [10] as shown in Table 6.10 from which it is evident that the proposed method offers up to 7.93% enhancement in visual quality of the watermarked image and 1.53% reduction in BER over [10].
6.6.2 Performance Evaluation of Proposed Method Using Multilevel Encrypted Text Watermarking
In order to enhance the security of the text watermark, reduce save the massage encryption/decryption time and address the health data management issues, the encrypted text watermark is embedding into the appropriated DWT sub-bands. In this subsection, simultaneous embedding of three watermarks (i.e. doctor code, image reference code and patient record) using multilevel watermarking of cover medical image has been proposed to address the issues of medical data confidentiality, data security, data compaction, unauthorized access and temper proofing. The suggested method uses wavelet based spread-spectrum watermarking where the encrypted text watermarks are embedded at multiple levels of the DWT sub-bands of the cover image. The performance of the developed scheme was evaluated and analyzed against known attacks by varying watermark size and the gain factor. It is found that the proposed multilevel watermarking method enhances the security of the patient data. The advantage of the work is summarized as follows:
-
(i)
Improved capacity: The method proposed by Basant et al. [10] and Singh et al. [13] has been embedded 196 and 381 bits respectively. However, in our proposed method we can embed 728 bits (116 characters) with the acceptable performance in terms of robustness and imperceptibility.
-
(ii)
Enhanced security of the text watermark: security of the medical text watermark may be enhanced by using simple encryption method to save execution time. For tele-diagnosis, the encryption and decryption speed has become an important factor if the situation demands.
-
(iii)
Reduced bandwidth requirements: The EPR data in the form of three different text watermarks are embedding in the same medical cover image which reduce the bandwidth requirements as essential importance in medical applications
-
(iv)
Health data management: Further, the proposed method addressing the medical data management issues data security, data compaction, unauthorized access and temper proofing, having different characteristics and requirements. This has been achieved by allocation of watermarks according to robustness and capacity requirements at different DWT sub-band of the cover image. The allocation of the watermarks is presented in Table 6.11 [16].
Table 6.11 Allocation of watermarks according to robustness and capacity criteria at different sub-band
In this method, the personal and medical record of the patient is embedded into selected sub-bands of the second level. However, identification code of the doctor and patient’s diagnostic/image codes of the patient are embedded into selected sub-bands of the third level. The doctor identification and image reference codes are embedded into third level HL3 and LH3 sub-bands, while the patient record is embedded into HL2 and LH2 sub-bands of second level DWT sub-band. Also, encryption is applied to the ASCII representation of the text watermark and the encrypted text watermark is then embedded. Thus, the method enhances security of the text watermark. The encryption method used in the present work is simple to reduce the execution time during encryption and decryption. The EPR data is encrypted and decrypted using the equations 1 and 2, respectively as given in section “Encryption and decryption process for text watermark” of chapter “Robust and Imperceptible Hybrid Watermarking Techniques for Medical Images”.
The performance of the proposed watermarking method was tested for encrypted text medical watermark considering gray–level medical images of size 512 × 512 [15] as cover image. Two different text watermarks doctor identification code of ten characters and radiological image reference code of five characters are embedded into third level HL3 and LH3 sub-bands, while the patient record of varying size is embedded into HL2 and LH2 sub-bands of second level DWT as the third watermark. Encryption is applied to the ASCII representation of these text watermarks and the encrypted text watermarks are then embedded providing the extra level of security during embedding process. The strength of watermark is varied by varying the gain factor (α) in the watermarking algorithm. Figure 6.10 shows the cover CT Scan image and watermarked images obtained at different gain factors. Figure 6.11 shows the EPR data using as text watermarks. In the experiment, values of PSNR and BER are illustrated in Tables 6.12, 6.13, and 6.14 for varying gain factors (α) in the range of 5.0 to 15.0.
Table 6.12 shows the effect of gain factor on the performance (determined PSNR and BER values) of the proposed method for different sizes of watermark. With the encryption, maximum PSNR value is 40.02 dB and BER = 0.1538 against maximum size of watermark at α = 5. However, PSNR value is 31.05 dB and BER = 0 at α = 15.
Table 6.13 shows the effect of encryption on BER performance as obtained by the proposed multilevel watermarking method against ten different attacks. The highest BER value of 0.3846 is obtained against JPEG compression attack with quality factor (QF) = 10 with encryption which is slightly better than the BER performance without encryption (BER = 0.4326). Further, from Table 6.3 it is evident that the proposed technique reduces BER up to 0.124% while providing extra level of security of the text watermark using encryption compared to the method without using the encryption of text watermark.
Table 6.14 shows the effect of cover medical images on PSNR and BER performance as obtained by the proposed method at gain factor (α) = 15. It is observed that the highest PSNR and BER were obtained with MRI image, which is also shown in Figs. 6.12 and 6.13, respectively. Figure 6.14 shows BER performance of the proposed multilevel watermarking method against known attacks at gain factor (α) = 15.
6.6.3 Performance Evaluation of the Proposed Method for Image and Text Watermarking Using Encryption and BCH Code Simultaneously
The performance of the method is also tested for multiple watermarks using encryption and BCH code simultaneously. For the extensive analysis of the proposed work, we have tested the method with some minor changes as follows:
-
1)
The methods discussed in Sects. 6.1 and 6.2 using threshold criteria for the embedding purpose. However, the watermark bits are embedding here without using the threshold criteria.
-
2)
The method using the same algorithm for image watermark, as disused in Sect. 6.5. However, the text watermark embedding and extraction process is different, as discussed detail in [17].
In this context, the method adopts to extend two existing single watermarking techniques [5, 17] to achieve several goals in medical image watermarking like security, high capacity and robustness. Figure 6.15 show the embedding process of the proposed technique. The proposed dual watermarking algorithm embeds health centre’s logo as image watermark using spread spectrum watermarking technique and embedding of sensitive patient’s information as text watermark (up to 150 Characters) into the high frequency component (HH2 Sub-band) of the DWT cover image is considered.
Further, the proposed dual watermarking method is embedding two different watermarks in cover medical image simultaneously, which has fewer constraints than the other two dual watermarks methods [18,19,20]. The main contribution of the work is summarized as follow:
-
(i)
Dual watermarking and improved capacity: The method reported in [6, 21,22,23,24,25,26,27,28,29] has embedded only one watermark. The proposed technique is embedding multiple watermarks simultaneously in non-interfering way [20] to enhance the security and capacity of the hidden watermark and reduce the bandwidth and storage requirements for medical applications. The proposed technique can embeds up to 150 characters with acceptable visual quality of the watermarked image. However, the methods reported in [10, 13, 16] can embed only 196 bits, 381 bits and 728 bits respectively.
-
(ii)
Improved performance: In Table 6.18, robustness and security performance of text watermark have been improved using encryption technique and BCH channel coding. Further, the encryption technique [14] along with BCH coding based method is compared with only BCH coding based method and performance of the proposed scheme has been observed in terms of robustness of the image and text watermark against different signal processing attacks. The proposed method using the combination of encryption and watermarking to protecting the sensitive patient data.
-
(iii)
The proposed technique is also addressing the health data management issue [14, 16] in which more important patient/doctor data is embedding at higher level DWT and the less important data is embedding at lower level DWT.
The PSNR NC and BER Performance of the proposed dual watermarking algorithm is extensively evaluated for medical data. The 8-bit grey scale MR image of size 512 × 512 [15], health centre’s logo of different sizes and patient’s information of 150 characters and are considered as cover image, image and text watermark respectively. The perceptual quality (as determined by PSNR) of the cover image with hidden watermark and the robustness of the extracted watermarks (as determine by NC for image and BER for text watermark) is evaluated at varying gain factors. We have noticed that the perceptual quality is better at lower gain factor, however, stronger the robustness at higher gain values. In BCH error correcting code, redundant bit information is added in binary sequence such that error is distributed over redundant bits and hence, the BER value in the extraction process is reduced. Figure 6.16a, b show the cover MR and watermark health centre logo image respectively. Figure 6.17a–c presents the watermarked images at different gain factors. Figure 6.18 show the patient data as text watermark.
Table 6.15 shows the PSNR and NC performance of the proposed dual watermarking method at different gain factors using varying number of characters. The highest PSNR (38.63 dB) has been obtained for the maximum size of the text watermark (151 characters) at gain = 1. However, highest NC (0.8673) has been obtained for the same size of the text watermark at gain = 7. Referring this table, it is observed that PSNR decreases for increasing number of characters embedded and chosen gain factors. However, robustness (NC values) of the image watermark is increasing at higher gain factors. In addition, the value of gain factor = 5 provides a good balance between visual quality of the watermarked image and the robustness of the extracted watermark. Table 6.16 shows the PSNR, NC and BER performance of the proposed method for different sizes of the image watermark at gain = 5. It is observed that the NC values have been found ranges from 0.5794 to 0.8026 for different size of image watermark. However, BER for recovered text watermark (size = 145 characters = 1015 bits) is ‘0’ for all cases using BCH error correcting code, indicating a perfect recovery of the text watermark. Table 6.17 presents the PSNR, NC and BER performance of the proposed method for different cover images such as MRI, Brain CT Scan, Ultrasound, Barbara and Lena images at gain factor = 5. In this table, the PSNR values are above than 30.00 dB for all the considered cover images. The highest PSNR were obtained with Lena image (PSNR = 37.04dB). The range of NC values from 0.7254 to 0.8657. The highest NC value were obtained for MRI image (NC = 0.8657). However, the lowest NC value were obtained for CT Scan image (NC = 0.7254). Referring this table, it is observed that all the BER values have been found ‘0’ except the Ultrasound image which is greater than ‘0’.
Table 6.18 shows the NC and BER performance of the proposed dual watermarking method against known attacks at gain factor = 3 using text bits = 140. Without using the encryption, the highest NC value (0.9615) has been obtained for Gaussian LPF and sharpening mask and the lowest NC value of 0.3498 is obtained against salt and pepper attacks. The highest BER (12.85%) has been found against median filtering attack, whereas lowest BER (0%) is found against Gaussian low pass filtering, sharpening mask, JPEG compression, histogram equalization and cropping. Referring this table, it is observed that all the NC values (with encryption) is greater than the NC values as obtained without using the encryption method except for Gaussian LPF and sharpening mask. Table 6.19 presents the NC and BER performance of the proposed dual watermarking method against known attacks at gain factor = 5 using text bits = 1015. It is observed that all the NC values (with encryption) are greater than 0.7 except for Gaussian Noise (Mean = 0, Var-0.01), Salt & Pepper Noise (with density = 0.05), JPEG Compression (QF-10), Median Filtering (3 x 3). It is also observed that the BER performance is highly dependent on the noise variations. The results indicate that the proposed dual watermarking method is robust against various signal processing attacks. In addition, the performance of the proposed method highly depends on size of the watermarks, gain factor and noise variations.
6.7 Summary
In this chapter, the authors presents spread-spectrum based methods for secure multiple watermarking of medical images in wavelet domain which simultaneously embeds text and image both or text watermarks only into a cover medical image. The use of spread-spectrum technique secures the image watermark whereas improvement in robustness of the text watermark has been achieved using BCH code before embedding. Experimental results were obtained by varying watermark size, gain factor and medical cover image modalities. The performance of the developed technique was tested against the known attacks. The method is also compared with other reported techniques and has been found to be giving superior performance for robustness with acceptable perceptual quality of the watermarked image suggested by other reported techniques. The proposed method offers up to 63.51% superior performance in terms of robustness over other reported techniques.
Further, the performance of the proposed watermarking method has been extensively evaluated only for text watermark at multilevel DWT sub-bands by applying BCH code on the watermark considered as EPR data before embedding into the cover has been investigated. The performance of the developed technique was tested against the known attacks. The PSNR and BER performance of the proposed method is also compared with other reported technique. It is evident that the proposed method offers up to 7.93% enhancement in visual quality of the watermarked image and 1.53% reduction in BER over the reported techniques. Moreover, the method is also addressing the health data management issue where the encrypted text watermarks are embedded at multiple levels of the DWT sub-bands of the cover image. From the above discussion, we have observed that method reduces BER up to 0.124% while providing extra level of security of the text watermark using encryption method. Moreover, the performance of the method is also tested for multiple watermarks using encryption and BCH code simultaneously.
The proposed techniques is providing a potential solution to existing problem of secure medical data transmission over open and bandwidth constrained network. It also deals the problem of patient identity theft, which is a growing and dangerous concern in this area. For improvement in error correction capability of extracted text watermark bits, length of the error correction code may be suitably increased. Correlation and security of the method can be improved further by using other extended PN sequences such as random sequence, maximal length sequence, gold sequence and Kasami sequence.
References
O. Vikas, Multilingualism for cultural diversity and universal access in cyberspace: an Asian perspective, UNESCO, May 2005
B. Kumar, H.V. Singh, S.P. Singh, A. Mohan, Secure spread-spectrum watermarking for telemedicine applications. J. Inf. Security 2(2), 91–98 (2011)
G. Coatrieux, H. Maitre, B. Sankur, Y. Rolland, R. Collorec, Relevance of watermarking in medical imaging, in Proceeding of the Information Technology Applications in Biomedicine, pp. 250–255, 2000
C. Pujara, A. Bhardwaj, V.M. Gadre, Secured watermarking fractional wavelet domains. IETE J. Res. 53(6), 573–580 (2007)
B. Kumar, A. Anand, S.P. Singh, A. Mohan, High capacity spread-spectrum watermarking for telemedicine applications. World Acad. Sci. Eng. Technol. 5, 58–62 (2011)
I.J. Cox, J. Kilian, F.T. Leighton, T. Shamoon, Secure spread spectrum watermarking for multimedia. IEEE Trans. Image Process. 6(12), 1673–1687 (1997)
H.S. Malvar, D.A.F. Florencio, Improved spread spectrum: a new modilation technique for robust watermarking. IEEE Trans. Signal Process. 51(4), 898–905 (2003)
L. Perez-Freire, F. Perez-Gonzalez, Spread-spectrum watermarking security. IEEE Trans. Inf. Forensics Security 4(1), 2–24 (2009)
G. Xuan, C. Yang, Y. Zheng, Y.Q. Shi, Z. Ni, Reversible data hiding based on wavelet spread spectrum, in IEEE International Workshop on Multimedia Signal Processing, Siena, Italy, pp. 211–214, 2004
B. Kumar, S.B. Kumar, D.S. Chauhan, Wavelet based imperceptible medical image watermarking using spread-spectrum, in Proceeding of 37th International Conference on Telecommunications and Signal Processing, Berlin, Germany, pp. 660–664, 2014
J. Domingo-Ferrer, F. Sebé, Invertible spread-spectrum watermarking for image authentication and multilevel access to precision-critical watermarked images, in Proceedings of the International Conference on Information Technology: Coding and Computing, pp. 1–6, 2002
T.S. Das, V.H. Mankar, S.K. Sarkar, Spread spectrum based robust image watermark authentication, in International Conference, Madurai, India, pp. 673–676, 2007
A.K. Singh, B. Kumar, M. Dave, A. Mohan, Robust and imperceptible spread-spectrum watermarking for telemedicine applications. Proc. Natl. Acad. Sci., India, Sect. A: Phys. Sci. (2015). doi:10.1007/s40010-014-0197-6
A.K. Singh, M. Dave, A. Mohan, Multilevel encrypted text watermarking on medical images using spread-spectrum in DWT domain. Wirel. Pers. Commun. 83(3), 2133–2150 (2015)
MedPix TM Medical Image Database available at http://rad.usuhs.mil/medpix/medpix.html
A. Giakoumaki, S. Pavlopoulos, D. Koutsouris, Secure and efficient health data management through multiple watermarking on medical images. Med. Biol. Eng. Comput. 44, 619–631 (2006)
N. Terzija, M. Repges, K. Luck, W. Geisselhardt, Digital image watermarking using DWT: performance comparison on error correcting codes, in Visualization, Imaging, and Image Processing Proceeding (364), 2002
K. Wu, W. Yan, J. Du, A robust dual digital-image watermarking technique, in International Conference on Computational Intelligence and Security Workshop, pp. 668–671, 2007
C. Chemak, M.S. Bouhlel, J.C. Lapayre, A new scheme of robust image watermarking: the double watermarking algorithm, in Proceedings of the 2007 Summer Computer Simulation Conference, SCSC 2007, San Diego, CA, USA, pp. 1201–1208, 2007
H. Shen, B. Chen, From single watermark to dual watermark: a new approach for image watermarking. Comput. Electr. Eng. 38, 1310–1324 (2012)
A. Singh, A. Tayal, Choice of wavelet from wavelet families for DWT–DCT–SVD image watermarking. Int. J. Comput. Appl. 48(17), 9–14 (2012)
M.I. Khan, M.M. Rahman, M.I.H. Sarker, Digital watermarking for image authentication based on combined DCT, DWT, and SVD transformation. Int. J. Comput. Sci. 10(5), 223–230 (2013)
A. Srivastava, P. Saxena, DWT-DCT-SVD based semi blind image watermarking using middle frequency band. IOSR J. Computer Eng. 12(2), 63–66 (2013)
N.J. Harish, B.B.S. Kumar, A. Kusagur, Hybrid robust watermarking techniques based on DWT, DCT, and SVD. Int. J. Adv. Electr. Electron. Eng. 2(5), 137–143 (2013)
B.L. Gunjal, R.R. Manthalkar, An overview of transform domain robust digital image watermarking algorithms. J. Emerg. Trends Computer Inf. Sci. 2(1), 13–16 (2011)
F. Chen, H. He, Y. Huo, H. Wang, Self-recovery fragile watermarking scheme with variable watermark payload, Proceedings of the 10th International Conference on Digital-Forensics and Watermarking, Atlantic City, NY, pp. 142–155, 2011
N.H. Divecha, N.N. Jani, Image watermarking algorithm using DCT, DWT and SVD, in Proceedings on National Conference on Innovative Paradigms in Engineering and Technology, vol. 10, 2012, pp. 13–16
K.A. Navas, A.M. Cheriyan, M. Lekshmi, S.A. Tampy, M. Sasikumar, DWT–DCT–SVD based watermarking, in Proceedings of the 3rd International Conference on Communication Systems Software and Middleware and Workshop, Bangalore, pp. 271–274, 2008
B. Wang, J. Ding, Q. Wen, X. Liao, C. Liu, An image watermarking algorithm based on DWT DCT and SVD, in IEEE International Conference on Network Infrastructure and Digital Content, Beijing, pp. 1034–1038, 2009
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2017 Springer International Publishing AG
About this chapter
Cite this chapter
Singh, A.K., Kumar, B., Singh, G., Mohan, A. (2017). Secure Spread Spectrum Based Multiple Watermarking Technique for Medical Images. In: Singh, A., Kumar, B., Singh, G., Mohan, A. (eds) Medical Image Watermarking. Multimedia Systems and Applications. Springer, Cham. https://doi.org/10.1007/978-3-319-57699-2_6
Download citation
DOI: https://doi.org/10.1007/978-3-319-57699-2_6
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-57698-5
Online ISBN: 978-3-319-57699-2
eBook Packages: Computer ScienceComputer Science (R0)