Abstract
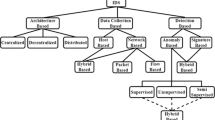
In the realm of cyber security, particularly in the area of network security, IDS has recently attracted researchers’ attention since it has been considered one of the most powerful techniques incorporated to identify harmful activity in a network system. A functional IDS examines incoming to and outgoing from the public or private network traffic data and gives warnings once malicious data are detected. Network traffic has been quickly increasing in recent years, and unfortunately conventional IDS-based solutions, which rely mostly on signatures and restrictions, are incapable to handle massive volumes of data and prohibit novel attack events and plans. Anomaly detection-based Deep Learning (DL) techniques are more adaptable and powerful with big data than conventional approaches, and this renders them appealing to scholars. The aforementioned challenges motivate us to present our technique. The major aim of this article is to implement a lightweight IDS-based Neural Network (NN) incorporating feature selection suitable for applications that do not require very high accuracy. In our experiment, we first train our model utilizing the newer dataset with higher-dimensional, CSE-CICIDS2018, to evaluate the model performance. Then, we retrain the dataset with feature selection approach, namely Recursive features elimination (Rfe), to reduce the model complexity. Finally, our research shows that our proposal outperforms the state-of-the-art in terms of model complexity and accuracy when Rfe method is applied, where the model accuracy is better than the one in the state-of-the-art by about 10%.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Man, J., Sun, G.: A residual learning-based network intrusion detection system. Secur. Commun. Netw. 2021, 1–9 (2021)
Bourou, S., El Saer, A., Velivassaki, T.-H., Voulkidis, A., Zahariadis, T.: A review of tabular data synthesis using gans on an ids dataset. Information 12(9), 375 (2021). https://doi.org/10.3390/info12090375
Alasad, Q., Lin, J., Yuan, J.-S., Fan, D., Awad, A.: Resilient and secure hardware devices using ASL. ACM J. Emerg. Technol. Comput. Syst. 17(2), 1–26 (2021). https://doi.org/10.1145/3429982
Chung, S., Kim, K.: A heuristic approach to enhance the performance of intrusion detection system using machine learning algorithms. In: Proceedings of the Korea Institutes of (CISC-W’15) (2015)
Silva, S.H., Najafirad, P.: Opportunities and challenges in deep learning adversarial robustness: a survey. arXiv preprint arXiv:2007.00753 (2020)
Fadlullah, Z.M., et al.: State-of-the-art deep learning: Evolving machine intelligence toward tomorrow’s intelligent network traffic control systems. IEEE Commun. Surv. Tutorials 19, 2432–2455 (2017)
Basavegowda, H.S., Dagnew, G.: Deep learning approach for microarray cancer data classification. CAAI Trans. Intell. Technol. 5, 22–33 (2020)
Usama, M., et al.: Black-box adversarial machine learning attack on network traffic classification. In: 2019 15th (IWCMC), pp. 84–89 (2019)
He, K., Zhang, X., Ren, S., Sun, J.: Deep residual learning for image recognition. In: 2016 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), pp. 770–778. Las Vegas, NV, USA (2016)
Szegedy, C., Vanhoucke, V., Ioffe, S., Shlens, J., Wojna, Z.: Rethinking the inception architecture for computer vision. In: 2016 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), pp. 2818–2826. Las Vegas, NV, USA (2016)
Szegedy, C., Ioffe, S., Vanhoucke, V., Alemi, A.A.: Inception-v4, inception-resnet and the impact of residual connections on learning. In: Thirty-first AAAI conference on artificial intelligence (2017)
Mirza, A.H.: Computer network intrusion detection using various classifiers and ensemble learning. In: 2018 26th (SIU), pp. 1–4 (2018)
Chkirbene, Z., Eltanbouly, S., Bashendy, M., AlNaimi, N., Erbad, A.: Hybrid machine learning for network anomaly intrusion detection. In: 2020 IEEE International Conference on Informatics, IoT, and Enabling Technologies (ICIoT), pp. 163–170. Doha, Qatar (2020)
Serinelli, B.M., Collen, A., Nijdam, N.A.: Training guidance with KDD cup 1999 and NSL-KDD data sets of ANIDINR: anomaly-based network intrusion detection system. Procedia Comput. Sci. 175, 560–565 (2020)
Ahmad, S., Arif, F., Zabeehullah, Z., Iltaf, N.: Novel approach using deep learning for intrusion detection and classification of the network traffic. In: 2020 (CIVEMSA), pp. 1–6 (2020)
Kanimozhi, V., Jacob, T.P.: Artificial Intelligence outflanks all other machine learning classifiers in Network Intrusion Detection System on the realistic cyber dataset CSE-CIC-IDS2018 using cloud computing. ICT Express 7, 366–370 (2021)
Sharafaldin, I., Lashkari, A.H., Ghorbani, A.A.: Toward generating a new intrusion detection dataset and intrusion traffic characterization. In: Proceedings of the 4th International Conference on Information Systems Security and Privacy (ICISSP 2018), vol. 1, pp. 108–116 (2018)
Bhosale, K.S., Nenova, M., Iliev, G.: Data mining based advanced algorithm for intrusion detections in communication networks. In: 2018 (CTEMS), pp. 297–300 (2018)
Aboueata, N., Alrasbi, S., Erbad, A., Kassler, A., Bhamare, D.: Supervised machine learning techniques for efficient network intrusion detection. In: 2019 28th International Conference on Computer Communication and Networks (ICCCN), pp. 1–8. Valencia, Spain (2019)
Sah, G., Banerjee, S.: Feature reduction and classifications techniques for intrusion detection system. In: 2020 (ICCSP), pp. 1543–1547 (2020)
Tanaka,A., Tomiya, A., Hashimoto, K.: Basics of neural networks. In: Tanaka, A., Tomiya, A., Hashimoto, K. (eds.) Deep Learning and Physics, pp. 35–55. Springer, Singapore (2021). https://doi.org/10.1007/978-981-33-6108-9_3
Islam, M., Chen, G., Jin, S.: An overview of neural network. Am. J. Neural Network. Appl. 5, 7–11 (2019)
Warzyński, A., Kołaczek, G.: Intrusion detection systems vulnerability on adversarial examples. In: 2018 (INISTA), pp. 1–4 (2018)
Ferrag, M.A., Maglaras, L., Moschoyiannis, S., Janicke, H.: Deep learning for cyber security intrusion detection: approaches, datasets, and comparative study. J. Inform. Secur. Appl. 50, 102419 (2020). https://doi.org/10.1016/j.jisa.2019.102419
Amaizu, G.C., Nwakanma, C.I., Lee, J.-M., Kim, D.-S.: Investigating network intrusion detection datasets using machine learning. In: 2020 International Conference on Information and Communication Technology Convergence (ICTC), pp. 1325–1328. Jeju, Korea (South) (2020)
Kanimozhi, V., Jacob, T.P.: Artificial intelligence based network intrusion detection with hyper-parameter optimization tuning on the realistic cyber dataset CSE-CIC-IDS2018 using cloud computing. In: 2019 (ICCSP), pp. 0033–0036 (2019)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Alasad, Q., Hammood, M.M., Alahmed, S. (2023). Performance and Complexity Tradeoffs of Feature Selection on Intrusion Detection System-Based Neural Network Classification with High-Dimensional Dataset. In: Al-Sharafi, M.A., Al-Emran, M., Al-Kabi, M.N., Shaalan, K. (eds) Proceedings of the 2nd International Conference on Emerging Technologies and Intelligent Systems. ICETIS 2022. Lecture Notes in Networks and Systems, vol 584. Springer, Cham. https://doi.org/10.1007/978-3-031-25274-7_45
Download citation
DOI: https://doi.org/10.1007/978-3-031-25274-7_45
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-25273-0
Online ISBN: 978-3-031-25274-7
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)