Abstract
The Internet of Things (IoT) promises to change many aspects of our daily lives thanks to the opportunity of interconnecting a massive numbers of smart objects with increasing computational, storage, communication, and power capabilities, in such a way making “smart” and “interactive” most of the world around us. In other words, smart objects and humans will be involved together in pervasive, proactive, and collaborative activities to orchestrate and execute increasingly complex and sophisticated tasks. In such a scenario, thanks also to a greater ecological awareness of people, a promising field of application for IoT technology is the monitoring of natural habitats in automatic or semiautomatic mode. A potentially effective and efficient solution is to form composite teams joining human operators and IoT devices. In such teams, not only the kind of team members will be different, i.e., humans and IoT devices, but also the IoT devices will be heterogeneous among them in terms of characteristics and performance. However, a basic requirement for a good team is the existence of high levels of mutual trust among its members. In other words, for the formation of a good team, it becomes of primary relevance to know and adequately represent the trustworthiness of the individual team members. To this end, our contribution can be summarized as (i) introducing a trust measure that takes into account both the reputation of devices and the accuracy of their measures; (ii) designing a framework that based on the proposed trust measure forms temporary teams for environmental ecosystems made of humans and IoT devices; and (iii) testing the proposed framework by simulating a collaborative environmental monitoring activity. The simulation results confirmed the advantages of the proposed approach in terms of performance and appreciation of the composite temporary teams that have been formed in this way.
Access provided by Autonomous University of Puebla. Download chapter PDF
Similar content being viewed by others
Keywords
1 Introduction
In recent years, a significant environmental sensibility has grown throughout the world, making people aware about the importance of knowing and monitoring the state of the environment [2, 11]. This has also stimulated, on the one hand, the search for greener solutions to new and existing human processes having significant negative impacts on the environment and, on the other hand, solutions to remedy, where possible, the damage that anthropic development has caused in various ecosystems [33].
In this context, a very promising technology to change many aspects of our daily lives, making “smart” and “interactive” most of the world around us, is represented by the Internet of Things (IoT) [50]. The IoT allows to smart devices and humans to be involved together in pervasive, proactive, and collaborative activities to orchestrate and execute increasingly complex and sophisticated tasks [27]. As a consequence of the opportunity provided by the IoT of interconnecting a massive numbers of smart objects with increasing computational, storage, communication, and power capabilities, new opportunities are available for governments, agencies, businesses, and citizens to know and monitor the current state and evolution over time of an ecosystem [35, 53].
By means of IoT devices, it is possible to gather over time a wide variety of data referred to the quality of air, water, and soil, as well as temperatures, electromagnetic and acoustic pollution, and so on. Moreover, the possibility of using fixed and/or mobile IoT devices and varying their spatial density makes it possible to transform almost any habitat into a smart one [7].
In this scenario, however, it must be taken into account that the potentially wide heterogeneity of devices implies that each of them will have its own trustworthiness in terms of performance [31]. The reasons for this are manifold, including the nature of the device itself, the existence of different types of devices suitable to perform the same type of measurement, adverse environmental conditions, insufficient battery power, etc. Therefore, forming the best temporary team of devices that can support human operators in monitoring a particular habitat can also be a challenging task [17], particularly in presence of large scenarios or with respect to time-critical instances or when it is necessary to take into account conflicting issues.
Some of the strategies usually adopted to select the members to form ad hoc, temporary teams (e.g., semantic similarities, structural similarities, integration or cohesion approaches, locality principles, etc.) may not be appropriate in our highly dynamic contexts and, particularly, in presence of heterogeneous devices (e.g., in terms of skills, autonomy, resource availability, etc.) [25, 52]. To address this issue, several solutions have been proposed in the literature relying on different properties, but to this end an increasing number of proposals consider social properties of devices as fundamental to have a reasonable high expectancy of achieving mutually satisfactory interactions between them [46].
In recent years, a property that has found increasing consensus in team formation processes is the trustworthiness [19]. To this end, several definitions of trustworthiness have been proposed in the literature [10, 15], generally dependent on the particular application context, the information sources and their freshness, the data type, etc. Consequently, several measures exist to evaluate the trustworthiness of an actor and for optimizing team-building processes, also in presence of very large communities [22, 26, 38].
Also in the formation of temporary teams to perform environmental surveillance activities, the trustworthiness of the actors can play a significant role in making such scenarios not only smart but also efficient and effective. To this end, this paper proposes a framework that adopts a trust-based approach for the automated formation of IoT device teams able to support human operators in environmental surveillance. This framework was tested on a simulated scenario demonstrating a measurable improvement in team composition both in terms of performance and appreciation.
The outline of the paper is as follows. Section 2 presents the scenario of interest and introduces the framework we designed. The details of the trust model and of the proposed team formation strategy are described in Sect. 3, while Sect. 4 presents the results of our simulations. Section 5 gives an overview on the related literature and, finally, in Sect. 6 some conclusions are drawn and the forthcoming researches delineated.
2 The Framework
As previously highlighted, nowadays there exists a greater environmental awareness, and citizens, media, and national and supranational authorities (e.g., UN, EU) are increasingly committed to its protection. Most of these actions require a synergy between different actors, at all involved levels, and the use of different tools to achieve the common goal of protecting our vital environment.
Advanced environmental monitoring processes also require similar collaborative approaches. They, if on the one hand, are made easier by advances in information and communication technologies and, on the other hand, require solving new challenges such as those of forming temporary teams of smart devices and fruitfully cooperation with human operators.
Collaborative mechanisms between sensors and humans within a team are a substantial improvement over simply collecting and analyzing sensor data. In fact, building ad hoc teams allows us to improve the effectiveness and efficiency of environmental surveillance activities and optimize the overall consumption of computational, memory, and energy resources.
In the scenario defined above, suppose we form a temporary team in which a human worker, who is the team leader (TL), and mobile IoT devices work together. The elements to take into account when forming such a team will be:
-
A number m of smart IoT devices placed in the environment
-
A number n of IoT devices necessary to carry out a specific surveillance activity
-
A set of k criteria, or operation profile, characterizing the IoT devices, with respect to the surveillance activity (model, sensitivity, computational storage capacity and power, mobility, and so on).
For example, consider a complex natural ecosystem, in which a significant number of IoT devices (mobile and fixed) operate; the goal could be that to collect environmental information by selecting only those devices that meet specific requirements (e.g., detector sensitivity, etc.).
As a consequence, the surveillance process can be conducted at different levels of detail based on the number of IoT devices it uses, precision, and other characteristics. These devices will have the ability to communicate with each other and also cooperate in order to identify errors and malfunctions [42]. In this context, the framework will be able to support the TL in the formation of the teams, analyzing and keeping the profile of the devices and the activities carried out updated. Therefore, once the task and characteristics of the IoT devices required by the TL are known, the best team of collaborators of the TL will be formed.
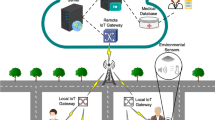
More formally, let A be an area to monitor, let SE the smart environment active on A, and let SA the set of the surveillance activities required to be performed on A (see Fig. 1).
Specifically, the m IoT devices are classified based on their operational profiles, which are kept constantly updated by the framework. For each SA, which can also be formed by several elementary tasks, a team leader is selected who will proceed to choose the n IoT devices members of his team T, classifying them in ascending order according to the measure:
where for each device, R is its rank, t is the operative time (e.g., the time required to a device for ending its current task and becomes again available), and w is the value of an integrated measure that takes into account the reputation and the accuracy of the IoT device (see Sect. 3).
The proposed framework is compliant with approaches that can differ in computational complexity and performance. In order to test the feasibility of the proposed solution, a numerical approach has been preliminary adopted here. In addition, a centralized or distributed approach could be adopted for managing the device profiles or for the calculation of their rank and their trust and accuracy; this also depends on the nature of the data to be processed or according to specific needs (response time, privacy, resource usage, etc.). This aspect can heavily affect the performance of the system also in the light of the specific devices features and the application context [12]. However, we currently consider these aspects as orthogonal to the core goal of our proposal.
However, it is simple to note how a collaborative and trusted monitoring activity, such as the one required in the proposed framework, can easily be implemented through the agent-based computing paradigm, thanks to the cooperative and social attitudes of software agents, both with real and virtual entities. In this respect, software agents can proactively perform sensing/computation/implementation tasks in the interest of human users and also applying nontrivial coordination schemes.
For this purpose, in the following we will consider that each IoT device is associated with an agent and similarly for the TL. Among the advantages of such an approach, we point out that the multi-agent system could take charge of many instances related to, e.g., device heterogeneity, thus providing the TL with an abstract, more resilient, and less critical SE.
In addition, in order to prevent tampering, protecting the integrity and reliability of the data collected and stored, the agent hosted by each device could operate autonomously from the device and appropriately encode the data (see Sect. 3) Thus, even in potential “hostile” environments, agents associated with the TL and IoT devices could mutually interact in safe modality in the absence of a central repository.
Finally, agent simulators could be exploited to simulate easily on the performance of complex coordination, computation, mobility, network, and energy models.
3 The Trust Model
In our framework, the trustworthiness of IoT devices plays a fundamental role to form the teams. To this purpose a specific trust model has been designed to characterize IoT devices. Even though a significant number of reliability, reputation and trust definition have been provided in the literature (the interested reader can refer to [3, 10, 40]). In the following we will refer to the definitions provided below:
-
Reliability. Let k be the measure of reliability of a device, in the range [0, 1], representing its ability to correctly describe the environment where it lives. k takes into account each task the device has carried out. More in detail, let y = f(x1, ⋯ , xn) ∈ [0, 1] ⊂R be a function describing the quality of the task carried out by the device and let x1, ⋯ , xn be some parameters referring to freshness, device competence, etc. Hence, k is computed as:
$$\displaystyle \begin{aligned} k^{new} = \alpha \cdot k^{old} + (1-\alpha) \cdot y, \end{aligned} $$(1)where α ∈ [0, 1] ⊂R gives more or less relevance to y in updating k.
-
Reputation. Let m be the measure of the reputation of a device, ranging in [0, 1] ⊂R, about the appreciation a device receives from the team leader community for its activity. The measure m, is computed on the basis of the feedback n ∈ [0, 1] ⊂R provided by the TLs which it cooperated with and calculated as:
$$\displaystyle \begin{aligned} m^{new} = \beta \cdot m^{old} + (1-\beta) \cdot n \end{aligned} $$(2)where β ∈ [0, 1] ⊂R gives more or less relevance to n (i.e., the last task) in updating m.
-
Trust Let w a measure of the trust of a device, belonging to [0, 1], which combines both reliability and reputation measures to characterize a IoT device in team formation processes. The measure w is computed as:
$$\displaystyle \begin{aligned} w = \gamma \cdot k + (1- \gamma) \cdot m \end{aligned} $$(3)where γ ∈ [0, 1] ⊂R gives more or less relevance to k with respect to m in order to adopt different strategies, in terms of reliability and reputation, in team formation processes based on the specific characteristics of the monitored ecosystem.
More in detail, the main peculiarities in our reputation model are:
-
Reliability and reputation respectively refers to the provided data and the data requester in order to obtain a comprehensive trustworthiness measure. This overcomes the syllogism that a trusted entity would, by default, guarantee trusted data. In fact, the premise itself does not guarantee that only qualitatively adequate data can be collected, and this is without dishonest behaviors (for simplicity’s sake, not currently considered) occurring for some illicit purpose.
-
The proposed measure of “reliability” can take into account several contextual elements that may be present in the target functions, e.g., granularity of data (sensitivity is an important aspect in some environmental surveillance activities, like chemical radiation), frequency of detection (excessive detection frequency could represent computational, storage, and transmission overhead), responsiveness (it is critical in cases of alerts for catastrophic natural events like floods, earthquakes, and similar occurrences), etc.
-
We have linearly combined reputation and precision measures in a single trustworthiness measure, like [23]. In such a way, by increasing the reputation and/or the reliability, then also the trustworthiness increases and vice versa. Notwithstanding its simplicity, behind the advantage of a predictable behavior, this linear trust model performs well, as it is shown by the results presented in Sect. 4 with respect to the proposed simulated case-study.
-
Finally, the value of the γ parameter can be modified on an ad hoc basis, for example, to take into account on the contextual knowledge, or for applying more sophisticated specific strategies. To this end, sensitivity studies could be performed aimed at maximizing the performance of the framework by balancing the various factors involved therein.
4 Experiments
The proposed framework was validated through a set of experiments simulating an intelligent environment E formed by humans and IoT devices that are supported by a multi-agent system. A time window consisting of multiple working days was simulated, and a number of environmental surveillance activities were performed for each day. In turn, each surveillance task, carried out by appropriate teams of IoT devices managed by a TL, consisted of several sub-tasks, even different among them.
For simplicity, each team consists of a TL (operating as a supervisor), a number of IoT devices (for convenience assumed mobile such as simple drones). Furthermore, it was assumed that:
-
IoT devices are heterogeneous in reliability and reputation (or, in other words, accuracy and effectiveness);
-
Each surveillance and monitoring task requires a specialized device.
The assumptions made imply that:
-
Each device requires a different amount of time to complete its task.
-
A device receives from the TL that requested its service, a different appreciation.
In the formation of a team, each TL is supported by a personal agent (TLA). The TLA cooperates with the software agents associated with the IoT devices and forms, at a given time, the best possible team optimizing this process with respect to time availability and reliability of the devices (see Sects. 2 and 3). At the end of the task, the reliability (k), reputation (m), and trustworthiness (w) of the device will be updated.
4.1 Experimental Settings
In the simulation the following setting has been adopted:
-
A unique smart environment SE.
-
30 working days.
-
150 surveillance (i.e., monitoring) tasks per day.
-
100 mobile heterogeneous IoT devices.
-
The surveillance working place must be reached in a time of 10 min.
-
Each surveillance activity consists of 4 different serial sub-tasks, each one realized by 3 different mobile IoT devices (i.e., a surveillance activity requires 12 IoT devices).
The settings of IoT devices conform to the standard values for the application domain under consideration. In addition, preliminary tests also enabled the parameters of the trust model to be configured. More in detail:
-
The initial values of w and m have been initially set to 1.0, as well as that of w.
-
The parameters α and β, used to calculate k and m, respectively, have both been set to 0.85, this for warranting a smooth behavior over time.
-
The parameter γ, used to update the w was set to 0.75, to give more relevance to the feedback issued by the team leader.
4.2 Results
The preliminary simulations carried out used two different scenarios named S1 and S2. More specifically, two different configurations were adopted in terms of the overall reliability and reputation of IoT devices, i.e., their accuracy and their appreciation by TLs. In more detail, reliability and reputation varied in different fixed intervals in a uniform manner, and, consequently, so did the reliability measure. For the S1 scenario reliability and reputation varied in a range of 10%, while for S2 they could vary in a range of 20%.
Two strategies were also adopted for the two scenarios to guide the teams’ formation processes; the first based on our approach, the other based only on the time availability of IoT devices. The results obtained are represented in Fig. 2 and confirmed that in both scenarios our strategy performs better than the one based on time availability alone. This implies that in the formation of the teams, those devices that are the more accurate and effective were chosen.
Furthermore, through the measures of reliability and reputation described in Sect. 3, it is possible to verify the advantages of our proposal in comparison to the formation of teams based only on the time of availability of a device or, in other words, based on the formation of the required team in the fastest way.
The two strategies described above for the two scenarios S1 and S2 were applied over the entire 30 days simulated considering the reliability and reputation measures of all IoT devices affiliated with the various teams thus formed.
A cumulative balance in terms of reliability and reputation for the two scenarios are depicted in Figs. 3 and 4. The benefits given by our proposal are evident in both scenarios and for both measures; moreover, the more the benefits provided by our proposal increase, the more heterogeneous the IoT devices are.
Conversely, by adopting a team formation strategy based only on the use of the devices that have maximum reliability, in that case while we will achieve the best performance in terms of accuracy if compared to any other possible strategy, but on the other hand, the time to complete a monitoring task may increase significantly and unacceptably.
5 Related Work
An increasing number of researches focus on collaborative environmental surveillance and monitoring, mainly leveraging on well-established technologies (individually considered or jointly exploited) such as wireless sensor and actuator networks (WSANs), unmanned aerial vehicles (UAVs), automated guided vehicles (AVGs), and other IoT-related ones.
In [16, 51] smart systems based on cooperating WSANs allow controlling temperature, light, and humidity levels of indoor spaces in order to identify and react to critical situations but also to improve the energy efficiency of buildings and thermal comfort of their inhabitants. In collaboration with teams of AGVs, instead, WSN-equipped workshops can benefit of reduced downtime and limited connectivity issues [20, 28]: the operations of the production lines are better synchronized with each other, while anomalies can be earlier identified and solved, often automatically, thus also limiting the human interventions.
In outdoor large-scale environments (e.g., roads, agriculture fields), WSN and UAV can collaborate in surveillance and monitoring tasks by ensuring relevant improvements in terms of effectiveness and responsiveness, especially in case of emergency situations [41, 44]. For example, collaborative smart drones have been widely exploited in the smart city domain for fire and accident detection [6], pollution [55] and parking monitoring [9], disaster management scenarios [5], and urban video-surveillance [36], often by implementing efficient data processing strategies based on lightweight AI techniques. More recently, due to the COVID-19 emergency, collaborative monitoring and surveillance systems have been implemented to hinder the virus spreading both in indoor and outdoor environments [39, 49].
In all the aforementioned works, apart from specific monitoring targets (humidity, temperature, CO/noise/pollution/water level, etc.) and implementation choices (e.g., centralized cloud-based systems or distributed ones pivoted around software agents), the collaboration between human and machines is key since the complexity of some operations demands several, heterogeneous devices to cooperate with each other and to work as one. However, to form teams by leveraging on principles such as locality [46] (i.e., to group team members geographically or socially close with each other) or similarity [13] (i.e., to ensemble team from members with common objectives, features or working modalities) is definitively challenging, especially on large-scale and dynamic scenarios. There, devices can be frequently substituted, dropped, or hijacked: therefore, the history of past interactions is not always available, and there are other few useful elements upon which estimating the reliability of candidate team members [54]. Hence, over the years, locality or similarity principles have been replaced by trust as first-class criterion for dynamic team formation, mostly supported by decentralized techniques such as EigenTrust [32] or the PeerTrust [56].
Along this line, the air-quality level and healthiness of a monitored environment has been rated in [4] by means of a trust-based decision-making protocol according to which “trusted” community members are able to forward information to health professionals and to alert people in the case of safety risks. Similarly, authors of [29] have implemented a participatory sensing for hazard detection and response system: a Trust-as-a-Service cloud utility is exploited to manage the reputation scores of the community members (i.e., users, sensors, and other IoT devices) so that they can automatically carry on both surveillance and notification tasks, even in large-scale scenarios.
Rather than scalability, trust systems of [37] and [30] put the interoperability on the spotlight. The former is SenSquare, a collaborative IoT platform for environmental monitoring capable to deal with different data formats and transmission protocols during the gathering process from heterogeneous, trusted data sources. The latter [30], instead, refers to a cloud-based data-centric framework for trustworthy IoT monitoring services: here, authors have defined a comprehensive trustworthiness score (which considers the trust of both data and entity) which is potentially compliant with the standards proposed by the Telecommunication Standardization Sector (ITU-T, which coordinates standards for telecommunications and information communication technology).
Scalability and interoperability but also smartness and autonomy are desiderata of a collaborative trust-based systems that can be achieved thanks to the software agents [24]. Just to cite a few works, an agent-based alert system has been implemented in [8] for promptly alerting in case of tsunami events: a team of “agentified” wavemeters provide certified data, automatically discarding the detection coming from less reliable or less reputed devices (according to the trust model presented by [47]).
In the industrial IoT (IIoT) scenario, instead, factory activities such as the monitoring of materials or the supply chain resource managements have been demanded to teams of trusted agents (acting as digital alias for sensors, actuators, and AVGs), automatically grouped according to mutual “on field” information/observations, social relationships, QoS, security, etc. [1, 14, 18, 21, 43, 48]. In [34] the monitoring operations of a smart grid are performed by a multi-agent system over a blockchain by exploiting game theory principles, while in [45] the authors proposed a trust-based multi-agent cooperative load balancing system aimed at monitoring CPU and memory usage reports of a highly distributed network.
In all these cases, the agent-based computing represents an enabling paradigm for the dynamic, decentralized, and scalable information processing aimed at the establishment of a sound trust system.
6 Conclusions
The formation of temporary teams that include IoT devices and human team leaders leads TLs to interact with devices whose performance, relative to their specific skills, may not be the best possible. In this article, we proposed a strategy to form the best possible team by selecting its members based on their reliability, reputation, and availability. Specific definitions of device reliability, reputation, and trustworthiness have been introduced, and a new trust-based framework was presented to support the formation of temporary teams of IoT devices.
The experiments we performed on a simulated scenario, although based on the use of realistic parameters (with the goal of considering our approach suitable for environmental surveillance applications), showed that the combination of reliability, reputation, and trustworthy information leads to measurable performance improvement in the simulations performed. In fact, the simulations have shown the potential benefits of our proposal in terms of efficiency and effectiveness.
These results obviously need to be confirmed by further experiments on real environments. Indeed, some random and unpredictable events due, for example, to malfunctions, may affect the performance of the framework. We plan to address this and other specific issues in our ongoing research.
References
Mohamed Abdel-Basset, Gunasekaran Manogaran, and Mai Mohamed. Internet of things (iot) and its impact on supply chain: A framework for building smart, secure and efficient systems. Future Gener. Comput. Syst., 86:614–628, 2018.
Yandarbayeva Louisa Abdurashidovna, Adzhieva Anna Yurevna, Tsurova Liza Akhmetovna, Misakov Anzor Valerievich, and Molamusov Zalim Khashaovich. Theoretical and methodological foundations of the regional social-ecological-economic system polyfactor monitoring. Turkish Online Journal of Design, Art and Communication, 8:39, 2018.
Abdelmuttlib Ibrahim Abdalla Ahmed, Siti Hafizah Ab Hamid, Abdullah Gani, Muhammad Khurram Khan, et al. Trust and reputation for internet of things: Fundamentals, taxonomy, and open research challenges. Journal of Network and Computer Applications, 145:102409, 2019.
Hamid Al-Hamadi and Ray Chen. Trust-based decision making for health iot systems. IEEE Internet of Things Journal, 4(5):1408–1419, 2017.
Maher Aljehani and Masahiro Inoue. Safe map generation after a disaster, assisted by an unmanned aerial vehicle tracking system. IEEJ Transactions on Electrical and Electronic Engineering, 14(2):271–282, 2019.
Saeed H Alsamhi, Ou Ma, Mohammad Samar Ansari, and Faris A Almalki. Survey on collaborative smart drones and internet of things for improving smartness of smart cities. Ieee Access, 7:128125–128152, 2019.
Anwar Alshamsi, Younas Anwar, Maryam Almulla, Mouza Aldohoori, Nasser Hamad, and Mohammed Awad. Monitoring pollution: Applying iot to create a smart environment. In 2017 International Conference on Electrical and Computing Technologies and Applications (ICECTA), pages 1–4. IEEE, 2017.
Giuseppe Barbaro, Maria Donatella Gangemi, and Giandomenico Foti. An agent-based tsunami alert system. In WOA, pages 102–107, 2017.
Elizabeth Bondi, Fei Fang, Mark Hamilton, Debarun Kar, Donnabell Dmello, Jongmoo Choi, Robert Hannaford, Arvind Iyer, Lucas Joppa, Milind Tambe, et al. Spot poachers in action: Augmenting conservation drones with automatic detection in near real time. In Proceedings of the AAAI Conference on Artificial Intelligence, volume 32, 2018.
Diego De Siqueira Braga, Marco Niemann, Bernd Hellingrath, and Fernando Buarque De Lima Neto. Survey on computational trust and reputation models. ACM Computing Surveys (CSUR), 51(5):1–40, 2018.
David E Busch and Joel C Trexler. Monitoring ecosystems: interdisciplinary approaches for evaluating ecoregional initiatives. Island Press, 2003.
Roberto Casadei, Giancarlo Fortino, Danilo Pianini, Wilma Russo, Claudio Savaglio, and Mirko Viroli. Modelling and simulation of opportunistic iot services with aggregate computing. Future Generation Computer Systems, 91:252–262, 2019.
Dong Chen, Guiran Chang, Dawei Sun, Jiajia Li, Jie Jia, and Xingwei Wang. Trm-iot: A trust management model based on fuzzy reputation for internet of things. Comput. Sci. Inf. Syst., 8(4):1207–1228, 2011.
Ray Chen, Fenye Bao, and Jia Guo. Trust-based service management for social internet of things systems. IEEE transactions on dependable and secure computing, 13(6):684–696, 2015.
Jin-Hee Cho, Kevin Chan, and Sibel Adali. A survey on trust modeling. ACM Computing Surveys (CSUR), 48(2):1–40, 2015.
Franco Cicirelli, Antonio Guerrieri, Alessandro Mercuri, Giandomenico Spezzano, and Andrea Vinci. Itema: A methodological approach for cognitive edge computing iot ecosystems. Future Generation Computer Systems, 92:189–197, 2019.
Philip R Cohen, Hector J Levesque, and Ira A Smith. On team formation. Synthese Library, pages 87–114, 1997.
Antonello Comi, Lidia Fotia, Fabrizio Messina, Domenico Rosaci, and Giuseppe ML Sarné. Grouptrust: Finding trust-based group structures in social communities. In International Symposium on Intelligent and Distributed Computing, pages 143–152. Springer, 2016.
Nancy W Coppola, Starr Roxanne Hiltz, and Naomi G Rotter. Building trust in virtual teams. IEEE transactions on professional communication, 47(2):95–104, 2004.
Ying Duan, Yun Luo, Wenfeng Li, Pasquale Pace, Gianluca Aloi, and Giancarlo Fortino. A collaborative task-oriented scheduling driven routing approach for industrial iot based on mobile devices. Ad Hoc Networks, 81:86–99, 2018.
Pooya Farahvash and Thomas O Boucher. A multi-agent architecture for control of agv systems. Robotics and computer-Integrated manufacturing, 20(6):473–483, 2004.
Jennifer Feitosa, Rebecca Grossman, William S Kramer, and Eduardo Salas. Measuring team trust: A critical and meta-analytical review. Journal of Organizational Behavior, 41(5):479–501, 2020.
G Fortino, F Messina, D Rosaci, and G. M. L. Sarné. Using trust and local reputation for group formation in the cloud of things. Future Generation Computer Systems, 89:804–815, 2018.
Giancarlo Fortino, Wilma Russo, and Claudio Savaglio. Simulation of agent-oriented internet of things systems.
Giancarlo Fortino, Claudio Savaglio, Carlos E. Palau, Jara Suarez de Puga, Maria Ganzha, Marcin Paprzycki, Miguel Montesinos, Antonio Liotta, and Miguel Llop. Towards Multi-layer Interoperability of Heterogeneous IoT Platforms: The INTER-IoT Approach, pages 199–232. Springer International Publishing, Cham, 2018.
Nicole Gillespie. Survey measures of trust in organizational contexts: An overview. Handbook of research methods on trust, 2015.
Bin Guo, Daqing Zhang, Zhu Wang, Zhiwen Yu, and Xingshe Zhou. Opportunistic iot: Exploring the harmonious interaction between human and the internet of things. Journal of Network and Computer Applications, 36(6):1531–1539, 2013.
Daqiang Guo, Ray Y Zhong, Yiming Rong, and George GQ Huang. Synchronization of shop-floor logistics and manufacturing under iiot and digital twin-enabled graduation intelligent manufacturing system. IEEE Transactions on Cybernetics, 2021.
Jia Guo, Ray Chen, Jeffrey JP Tsai, and Hamid Al-Hamadi. Trust-based iot participatory sensing for hazard detection and response. In International Conference on Service-Oriented Computing, pages 79–84. Springer, 2016.
Upul Jayasinghe, Abayomi Otebolaku, Tai-Won Um, and Gyu Myoung Lee. Data centric trust evaluation and prediction framework for iot. In 2017 ITU Kaleidoscope: Challenges for a Data-Driven Society (ITU K), pages 1–7. IEEE, 2017.
Franklin Magalhães Ribeiro Junior and Carlos Alberto Kamienski. A survey on trustworthiness for the internet of things. IEEE Access, 9:42493–42514, 2021.
Sepandar D Kamvar, Mario T Schlosser, and Hector Garcia-Molina. The eigentrust algorithm for reputation management in p2p networks. In Proceedings of the 12th int. conf. on World Wide Web, pages 640–651. ACM, 2003.
René Kemp and Babette Never. Green transition, industrial policy, and economic development. Oxford Review of Economic Policy, 33(1):66–84, 2017.
Rabiya Khalid, Omaji Samuel, Nadeem Javaid, Abdulaziz Aldegheishem, Muhammad Shafiq, and Nabil Alrajeh. A secure trust method for multi-agent system in smart grids using blockchain. IEEE Access, 9:59848–59859, 2021.
Mihai T Lazarescu. Design of a wsn platform for long-term environmental monitoring for iot applications. IEEE Journal on emerging and selected topics in circuits and systems, 3(1):45–54, 2013.
Yutong Liu, Linghe Kong, Guihai Chen, Fangqin Xu, and Zhanquan Wang. Light-weight ai and iot collaboration for surveillance video pre-processing. Journal of Systems Architecture, 114:101934, 2021.
Federico Montori, Luca Bedogni, and Luciano Bononi. A collaborative internet of things architecture for smart cities and environmental monitoring. IEEE Internet of Things Journal, 5(2):592–605, 2017.
Michael Naef and Jürgen Schupp. Measuring trust: Experiments and surveys in contrast and combination. 2009.
Liwei Ouyang, Yong Yuan, Yumeng Cao, and Fei-Yue Wang. A novel framework of collaborative early warning for covid-19 based on blockchain and smart contracts. Information sciences, 570:124–143, 2021.
Isaac Pinyol and Jordi Sabater-Mir. Computational trust and reputation models for open multi-agent systems: a review. Artificial Intelligence Review, 40(1):1–25, 2013.
Dan Popescu, Florin Stoican, Grigore Stamatescu, Oana Chenaru, and Loretta Ichim. A survey of collaborative uav–wsn systems for efficient monitoring. Sensors, 19(21):4690, 2019.
Maria Nadia Postorino and Giuseppe M. L. Sarné. An agent-based sensor grid to monitor urban traffic. In Proceedings of the 15th Workshop dagli Oggetti agli Agenti, WOA 2014, volume 1260 of CEUR Workshop Proceedings. CEUR-WS.org, 2014.
Christian Prasse, Andreas Nettstraeter, and Michael Ten Hompel. How iot will change the design and operation of logistics systems. In 2014 International Conference on the Internet of Things (IOT), pages 55–60. IEEE, 2014.
Yerra Prathyusha and Chung-Nan Lee. Uav path planning and collaborative searching for air pollution source using the particle swarm optimization. In International Computer Symposium, pages 698–709. Springer, 2018.
US Premarathne and S Rajasingham. Trust based multi-agent cooperative load balancing system (tclbs). Future Generation Computer Systems, 112:185–192, 2020.
Syama Sundar Rangapuram, Thomas Buhler, and Matthias Hein. Towards realistic team formation in social networks based on densest subgraphs. In Proceedings of the 22nd int. conf. on World Wide Web, pages 1077–1088. ACM, 2013.
Domenico Rosaci, Giuseppe M. L. Sarné, and Salvatore Garruzzo. Integrating trust measures in multiagent systems. International Journal of Intelligent Systems, 27(1):1–15, 2012.
Yosra Ben Saied, Alexis Olivereau, Djamal Zeghlache, and Maryline Laurent. Trust management system design for the internet of things: A context-aware and multi-service approach. Computers & Security, 39:351–365, 2013.
Claudio Savaglio, Giancarlo Fortino, Giandomenico Spezzano, Mario Alejandro Paguay Alvarado, Fabio Capparelli, Gianmarco Marcello, Luigi Rachiele, Francesco Raco, and Samantha Genoveva Sanchez Basantes. Edge intelligence against covid-19: a smart university campus case study. In IoT Edge Solutions for Cognitive Buildings, pages 1–25. Springer, 2022-to appear.
Sajjad Hussain Shah and Ilyas Yaqoob. A survey: Internet of things (iot) technologies, applications and challenges. In 2016 IEEE Smart Energy Grid Engineering (SEGE), pages 381–385. IEEE, 2016.
Muhammad Tahir, Rabia Noor Enam, Syed Muhammad Nabeel Mustafa, and Rukaiya Javed. Emas: Environment monitoring and smart alert system for internet of things (iot). In 2020 Global Conference on Wireless and Optical Technologies (GCWOT), pages 1–4. IEEE, 2020.
Shun Takai and Marcos Esterman. Towards a better design team formation: A review of team effectiveness models and possible measurements of design-team inputs, processes, and outputs. In International Design Engineering Technical Conferences and Computers and Information in Engineering Conference, volume 58158, page V003T04A018. American Society of Mechanical Engineers, 2017.
Silvia Liberata Ullo and GR Sinha. Advances in smart environment monitoring systems using iot and sensors. Sensors, 20(11):3113, 2020.
Ke Wang, Ship Peng Xu, Chien-Ming Chen, SK Hafizul Islam, Mohammad Mehedi Hassan, Claudio Savaglio, Pasquale Pace, and Gianluca Aloi. A trusted consensus scheme for collaborative learning in the edge ai computing domain. IEEE Network, 35(1):204–210, 2021.
Josefa Wivou, Lanka Udawatta, Ali Alshehhi, Ebrahim Alzaabi, Ahmed Albeloshi, and Saeed Alfalasi. Air quality monitoring for sustainable systems via drone based technology. In 2016 IEEE International Conference on Information and Automation for Sustainability (ICIAfS), pages 1–5. IEEE, 2016.
Li Xiong and Ling Liu. Peertrust: Supporting reputation-based trust for peer-to-peer electronic communities. IEEE transactions on Knowledge and Data Engineering, 16(7):843–857, 2004.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this chapter
Cite this chapter
Fortino, G., Fotia, L., Messina, F., Rosaci, D., Sarnè, G.L., Savaglio, C. (2023). Formation of Reliable Composite Teams for Collaborative Environmental Surveillance of Ecosystems. In: Fotia, L., Messina, F., Rosaci, D., Sarné, G.M. (eds) Security, Trust and Privacy Models, and Architectures in IoT Environments. Internet of Things. Springer, Cham. https://doi.org/10.1007/978-3-031-21940-5_7
Download citation
DOI: https://doi.org/10.1007/978-3-031-21940-5_7
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-21939-9
Online ISBN: 978-3-031-21940-5
eBook Packages: EngineeringEngineering (R0)