Abstract
The evolution of communication networks has created a huge requirement for massive connectivity, efficient spectral utilization, and high reliability. With the introduction of non-orthogonal Multiple Access (NOMA) technique, most of the user requirements were satisfied. Since NOMA performs the superimposed transmission of user signals in the same resource block, to differentiate these signals, Successive Interference Cancellation (SIC) technique will be used. Till now, most of the research has focused on combining NOMA with key technologies such as Reconfigurable Intelligent Surfaces (RIS), massive Multiple Input Multiple Output (MIMO), millimeter Waves, etc. Whereas, few works have been done on studying the physical layer security of NOMA in direct cooperative satellite networks. In this paper, we study the connection and secrecy performance of such a system in the presence of two legitimate users and one eavesdropper. Closed-form expressions were derived to understand and simulate device performance. To authenticate these expressions, we also performed the Monte-Carlo simulations.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
Radio access networks (RAN) grant permission to the user to access particular resources of the radio spectrum for the purpose of data transmission [1]. With the evolution of communication networks from 1G to 5G, the performing capability of the network has also elevated in terms of connectivity, latency and user data rates. Numerous Internet of Things (IoT) applications have come into existence like smart homes, automated cars, virtual and augmented reality, etc. These services have demanded the requirements of high reliability, low latency, huge connectivity and high data speed [2,3,4]. Energy limitations are the most significant problem of IoT networks; however, energy harvesting techniques have also been proposed that have contributed to solving this obstacle [20, 21]. Key technologies such as millimeter wave (mmWave) communications, Multiple Input Multiple Output (MIMO), beamforming, and non-orthogonal Multiple Access (NOMA) technique were proposed by the International Telecommunication Union (ITU) to support the development of 5G and 6G communication networks. Integrating the NOMA technique with satellite communication networks is said to be a key development for 5G [5,6,7,8].
Comparing the performance metrics of NOMA and Orthogonal Multiple Access (OMA) technique, the NOMA has proved to be more efficient than the older technique. NOMA utilizes the same resource block to transmit the data of multiple users [9,10,11,12]. All user signals are superimposed, and these signals are differentiated by allocating different power level coefficients to the different users. The allocation of power levels is based on the channel gain of the user. Users with high channel gain will be allotted less power and low channel gain will be allotted with more power. At the receiver, these signals are separated by performing the successive interference cancellation (SIC) technique. The ability of NOMA to perform massive connectivity, acquire less latency and high reliability has made it a novel approach in many other technologies. Very little research has been done on integrating NOMA with terrestrial networks [13, 14]. In [13], the authors conducted a comprehensive study on Cloud RAN technology employed by NOMA networks. In [14], the authors have considered integrating NOMA assisted MIMO technology and NOMA assisted cooperative relay (CR) technology into the terrestrial network applications.
Research works in [15, 16] have mentioned that the problem of security in satellite terrestrial relay networks (STRN) can be approached using Physical Layer Security (PLS). The general concept of PLS is to provide access to the legitimate users while blocking the malicious users and their interception. In [17] and [18], the authors have investigated the secrecy problems in the cognitive SRTN system. In [22], the authors have proposed the cooperative multi-hop transmission protocol (CMT) in the underlay cognitive radio networks and analyze secrecy outage probability (SOP) with the existence of a secondary eavesdropper. Several studies were performed to understand and neutralize the secrecy issues in NOMA networks [19] and [23]. In [19], the authors have studied the application of PLS in NOMA and derived the full analysis of SOP. In [23], a similar system was studied, but in the presence of perfect SIC and imperfect SIC in both the power domain NOMA and code domain NOMA was studied. Asymptotic mathematical expressions were derived to analyze the performance of the system.
To the best of our knowledge, a few paper has considered secure performance of STRN, this motivates us to study secure STRN relying on multiple antennas.
2 System Model
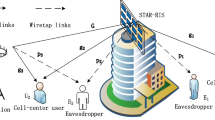
In this paper, we assume a NOMA cooperative satellite network. We assume a satellite (S), two destinations \(D_{i} ({\text{i}} \in \{ 1,2\} )\), and an eavesdropper (E) as shown in Fig. 1. Moreover, (S) is equipped with \(M\) antennas. In addition, we denote \({\mathbf{h}}_{i}\) as the \(M \times 1\) Shadowed-Rician channel vector form of S to \(D_{i}\) and \({\mathbf{h}}_{E}\) is the \(M \times 1\) Shadowed-Rician channel vector form of (S) to \(E\).
Moreover, (S) sends the signal \(s = \sqrt {(a_{1} )} x_{1} + \sqrt {(a_{2} )} x_{2}\), where \(a_{1}\), \(a_{2}\) are the power allocation coefficient and \(x_{1}\), \(x_{2}\) are the message of \(D_{1}\), \(D_{2}\). Therefore, the received signal from S to \(D_{i}\) is given by
where \(P_{S}\) denotes the power transmit at S, \(a_{1}\) and \(a_{2}\) are the power allocation coefficient, \((.)^{\dag }\) is the conjugate transpose, \(\nu_{i} \sim CN(0,\sigma_{i}^{2})\) denotes the additive white Gaussian noise (AWGN), \({\mathbf{w}}_{i}\) is the \(M \times 1\) transmit weight vector and \({\mathbf{w}}_{i} = \frac{{{\mathbf{h}}_{i} }}{{||{\mathbf{h}}_{i} ||_{F} }}\) as [28], in which \(\left\| \cdot \right\| _{F}\) is Frobenius norm.
Next, \(D_{2}\) is decoded with the signal \(x_{2}\) and the signal-to-interference-plus-noise-ratio (SINR) is given by
where \(\eta_{S} = \frac{{P_{S} }}{{\sigma_{i}^{2} }}\) is the transmitted signal-to-noise ratio (SNR), \(\eta_{i} = \eta_{S} \left\| {{\mathbf{h}}_{i} } \right\|_{F}^{2}\). Then, \(D_{1}\) is decoded with the signal \(x_{1}\) and the SINR is given by.
with NOMA protocol in [24], by applying SIC to decode its own signal \(x_{1}\) at \(D_{1}\), the SNR is given by
Meanwhile, the received signal at \(E\) is given by
where \(\nu_{E} \sim(CN,\sigma_{E}^{2} )\) Then the SINR of E to detect the signal \(x_{2}\) of \(D_{2}\) is given by [25]
where \(\eta_{S} = \frac{{P_{S} }}{{\sigma_{E}^{2} }},\eta_{E} = \eta_{S} \left\| {{\mathbf{h}}_{E} } \right\|_{F}^{2}\). Similar to \(D_{1}\), the SINR of \(E\) to detect the signal \(x_{1}\) of \(D_{1}\) is given by
In the next section, we intend to examine two performance metrics to highlight advances of Non-Orthogonal Multiple Access (NOMA) and multiple antennas scheme to the considered system.
3 Performance Analysis
In this section, we analyze the connection outage probability (COP) and secrecy outage probability (SOP) of \(D_{i}\). First, the probability density function (PDF) of the channel coefficient \(h_{z}^{j}\) with \(z \in \{ 1,2,E\}\) is given by [26]
where \(\alpha_{z} = \frac{1}{{2b_{z} }}\left( {\frac{{2b_{z} m_{z} }}{{2b_{z} m_{z} + \Omega_{z} }}} \right)^{{m_{z} }}\), \(\delta_{z} = \frac{{\Omega_{z} }}{{2b_{z} \left( {2b_{z} m_{z} + \Omega_{z} } \right)}}\), \(m_{z}\) is the fading severity parameter, \(\Omega_{z}\) and \(2b_{z}\) are the average power of LOS and multipath components, respectively, and \(_{1} F_{1} (.,.,.)\) denotes the confluent hypergeometric function of the first kind [29, 9 .201.1]. Based on [27], we can simplify (8) as
where \(\zeta_{z} \left( b \right) = \left( { - 1} \right)^{b} \left( {1 - m_{z} } \right)_{b} \delta^{b} /\left( {b!} \right)^{2}\) and \((.)_{b}\) is the Pochhammer symbol [29]. Thus, with i.i.d. Shadowed-Rician fading, the PDF of \(\eta_{z}\) can be expressed by
3.1 COP of \(D_{2}\)
The COP of \(D_{2}\) is given by [25]
where \(\varepsilon_{i} = 2^{{R_{i} }} - 1\) and \(R_{i}\) denotes the target rate.
Proposition 1:
The COP of \(D_{2}\) can be obtained as
Proof:
With help (2), COP of \(D_{2}\) can be rewritten as
Substituting the PDF in (10) into (13), we obtain the following.
Based on [29, 3.351.1], the closed-form of \(D_{2}\) is given by
where \(\gamma (a,b)\) is the upper incomplete gamma functions.
The proof is completed.
3.2 COP of \(D_{1}\)
The COP of \(D_{1}\) is written as [25]
Substituting (4) into (16), (16) can be rewritten as
Similar in Proposition 1, the closed-form of COP for \(D_{1}\) is given by
3.3 SOP of \(D_{2}\)
As the main result is reported in [25], the SOP of \(D_{2}\) is expressed as
where \(\varepsilon_{i}^{S} = 2^{{R_{i} - R_{i}^{S} }} - 1\) is the secrecy rate of \(D_{i}\).
Proposition 2:
The exact closed-form SOP of \(D_{2}\) is given by.
Proof:
By (6), the SOP of \(D_{2}\) can be rewritten as.
With the help of the CDF of \(\eta_{E}\) (10), we can write (21) as
Using [29, 3.351.2], the closed-form SOP of \(D_{2}\) is given by
where \(\Gamma (a,b)\) denotes the lower incomplete gamma function.
The proof is completed.
3.4 SOP of \(D_{1}\)
As [25], the SOP of \(D_{1}\) can be expressed as.
In similar to Proposition 2, the exact closed-form of \(D_{1}\) is formulated by
4 Numerical Result And Discussions
In this section, we set \(a_{2} = 0.8\), \(a_{1} = 0.2\), \(R_{2} = 0.5\) \(R_{1} = 1\), \(R_{1}^{S} = 0.5\) and \(R_{2}^{S} = 0.1\). Moreover, we consider the Shadowed-Rician fading parameters for the satellite links is the heavy shadowing with \(m_{1} = m_{2} = m_{E} = 1\), \(b_{1} = b_{2} = b_{E} = 0.063\) and \(\Omega_{1} = \Omega_{2} = \Omega_{E} = 0.0007\).
In Fig. 2, the simulations were performed to COP versus transmit SNR to analyze the connection outage performance of the system by varying the number of antennas at the satellite. As we can observe, the performance of the system has comparatively increased when the number of antennas were increased from 1 to 2.
In Fig. 3, the simulations were performed to SOP versus transmit SNR to analyze the secrecy performance of the system. We can observe that, with the rise in the number of antennas, the SOP of the system shows better performance. We can also observe that increasing a single antenna shows a huge performance gap between the lines. Therefore, we can understand that the number of antennas plays a major role in the efficiency of the system.
5 Conclusion
In this paper, we considered a NOMA network assisting a cooperative satellite with antennas equipped at the satellite, in the presence of two legitimate users and an eavesdropper. We aimed to investigate the connection performance and the secrecy performance of the system by varying main parameters such as the number of antennas. We have derived the closed-form expressions for COP and SOP and analysed the system behaviour by changing the number of antennas and keeping the remaining parameters constant for fair comparison. We understood that the increase in the number of antennas at the satellite will help the communication links for efficient data transmission.
References
Islam, S., Avazov, N., Dobre, O., Kwak, K.: Power domain non-orthogonal multiple access (NOMA) in 5G systems: potentials and challenges. IEEE Commun. Surv. Tutor. 19(2), 721–742 (2017)
Liu, G., Jiang, D.: 5G: Vision and requirements for mobile communication system towards year 2020. Chinese J. Eng. 2016, 1–9 (2016)
Wang, Y., Ren, B., Sun, S., Kang, S., Yue, X.: Analysis of non-orthogonal multiple access for 5G. China Commun. 2, 52–66 (2016)
Khan, R., Jayakody, D.: An ultra-reliable and lowlatency communications assisted modulation based nonorthogonal multiple access scheme. Phys. Commun. 43, 101035 (2020)
Dai, L., Wang, Z., Yuan, Y.: Non-orthogonal multiple access for 5G: solutions, challenges, opportunities and future research trends. IEEE Commun. Mag. 53, 74–81 (2015)
Zhang, X., et al.: Performance analysis of NOMA-based cooperative spectrum sharing in hybrid satellite-terrestrial networks. IEEE Access 7, 172321–172329 (2019)
Balyan, V., Saini, D.S.: Called elapsed time and reduction in code blocking forWCDMA networks. In: IEEE in Proceedings of International Conference on Software Telecommunication an Computer Networks, SoftCom, pp. 141–245 (2009)
Balyan, V., Saini, D.S.: A same rate and pattern recognition search of OVSF code tree for WCDMA networks. IET Commun. 8(13), 2366–2374 (2014)
Do, D.-T., Van Nguyen, M.-S., Voznak, M., Kwasinski, A., de Souza, J.N.: Performance analysis of clustering car-following V2X system with wirelesspower transfer and massive connections. In: IEEE Internet Things J. (2021). https://doi.org/10.1109/JIOT.2021.3070744
Do, D.-T., Van Nguyen, M.-S.: Device-to-device transmission modes in NOMA network with and without Wireless Power Transfer. Comput. Commun. 139, 67–77 (2019)
Do, D.-T., Nguyen, M.-S.V., Jameel, F., Jäntti, R., Ansari, I.S.: Performance evaluation of relay-aided CR-NOMA for beyond 5G communications. IEEE Access 8, 134838–134855 (2020)
Do, D.-T., Le, C.-B., Afghah, F.: Enabling full-duplex and energy harvesting in uplink and downlink of small-cell network relying on power domain based multiple access. IEEE Access 8, 142772–142784 (2020)
Ejaz, W., Shama, S., Saadat, S., Naeem, M., Anpalagan, A., Chughtai, N.: A comprehensive survey on resource allocation for CRAN in 5G and beyong networks. J. Nerw. Comput. Appl. 160, 1–24 (2020)
Aldababsa, M., Toka, M., Gokceli, S., Kurt, G., Kucur, O.: A tutorial on nonorthogonal multiple access for 5G and beyond. Wirel. Commun. Mob. Comput. 2018. 1–24 (2018)
Petraki, D.K., Anastasopoulos, M.P., Papavassiliou, S.: Secrecy capacity for satellite networks under rain fading. IEEE Trans. Dependable Secure Comput. 8(5), 778–783 (2011)
Guo, K., An, K., Zhang, B., et al.: Physical layer security for multiuser satellite communication systems with threshold-based scheduling scheme. IEEE Trans. Veh. Technol. 69(5), 5129–5141 (2020)
Li, B., Fei, Z., Xu, X., Chu, Z.: Resource allocations for secure cognitive satellite-terrestrial networks. IEEE Wirel. Commun. Lett. 7(1), 78–81 (2018)
Li, B., Fei, Z., Chu, Z., Zhou, F., Wong, K.K., Xiao, P.: Robust chance-constrained secure transmission for cognitive satellite-terrestrial networks. IEEE Trans. Veh. Technol. 67(5), 4208–4219 (2018)
Chen, J., Yang, L.: Physical layer security for cooperative NOMA systems. IEEE Trans. Veh. Technol. 67(5), 4645–4649 (2018)
Nguyen, T.N., Duy, T.T., Luu, G.T., Tran, P.T., Voznak, M.: Energy harvesting-based spectrum access with incremental cooperation, relay selection and hardware noises. Radioengineering 26(1), 240–250 (2017)
Nguyen, T.N., Tran, M., Nguyen, T.L., Ha, D.H., Voznak, M.: Performance analysis of a user selection protocol in cooperative networks with power splitting protocol-based energy harvesting over Nakagami-m/Rayleigh channels. Electronics 8(4), 448 (2019)
Tran Tin, P., The Hung, D., Nguyen, T.N., Duy, T.T., Voznak, M.: Secrecy performance enhancement for underlay cognitive radio networks employing cooperative multi-hop transmission with and without presence of hardware impairments. Entropy 21(2), 217 (2019)
Yue, X., Liu, Y., Yao, Y., Li, X., Liu, R., Nallanathan, A.: Secure communications in a unified non-orthogonal multiple access framework. IEEE Trans. Wirel. Commun. 19(3), 2163–2178 (2020)
Do, D.-T., Le, A.-T.: NOMA based cognitive relaying: transceiver hardware impairments, relay selection policies and outage performance comparison. Comput. Commun. 146, 144–154 (2019)
Song, Y., Yang, W., Xiang, Z., Wang, B., Cai, Y.: Secure transmission in mmWave NOMA networks with cognitive power allocation. IEEE Access 7, 76104–76119 (2019)
Bhatnagar, M.R., Arti, M.K.: Performance analysis of AF based hybrid satellite-terrestrial cooperative network over generalized fading channels. IEEE Commun. Lett. 17(10), 1912–1915 (2013)
Alfano, G., De Maio, A.: Sum of squared Shadowed-Rice random variables and its application to communication systems performance prediction. IEEE Trans. Wireless Commun. 6(10), 3540–3545 (2007)
Simon, M.K., Alouini, M.-S.: Digital Communications over Fading Channels: A Unified Approach to Performance Analysis. Wiley, Hoboken (2000)
Gradshteyn, I.S., Ryzhik, I.M.: Table of Integrals, Series, and Products, 7th edn. Academic, San Diego (2007)
Acknowledgment
This research was supported by the Ministry of Education, Youth and Sports of the Czech Republic under the grant SP2022/5 and e-INFRA C.Z. (ID:90140).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Nguyen, NT., Nguyen, HN., Voznak, M. (2022). Secrecy Performance of Scenario with Multiple Antennas Cooperative Satellite Networks. In: Dziech, A., Mees, W., Niemiec, M. (eds) Multimedia Communications, Services and Security. MCSS 2022. Communications in Computer and Information Science, vol 1689. Springer, Cham. https://doi.org/10.1007/978-3-031-20215-5_1
Download citation
DOI: https://doi.org/10.1007/978-3-031-20215-5_1
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-20214-8
Online ISBN: 978-3-031-20215-5
eBook Packages: Computer ScienceComputer Science (R0)