Abstract
Smart healthcare plays a vital role in contemporary society while its security and privacy issues remain critical challenges. With the aim of resolving problems related to the integrity and confidentiality of information transmitted in the smart healthcare, Wang et al. designed a certificateless authenticated key agreement (CL-AKA) scheme recently. However, we analyze their protocol and prove that theirs did not satisfy forward security. Further, this paper proposes an improved authenticated key agreement (AKA) scheme based on the certificateless cryptography. The proposed CL-AKA scheme does not only satisfy the security requirements in smart healthcare networks but also performs more efficient. The performance comparison shows our scheme has comparable efficiency in terms of computation cost.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
More and more attention has been paid on the medical infrastructure since people ask for higher medical quality and more convenient service. As one of the most promising applications based on the Internet of Things (IoT), smart healthcare system, a self-organizing network realizes the interaction among patients, medical staff, hospitals and medical equipment. However, its communications are conducted through open wireless channels which makes the networks vulnerable to various attacks, such as man-in-the-middle attacks and ephemeral key leakage attacks.
Since users may outsource their sensitive information to servers to alleviate the heavy overheads, secure communications over the public channel are important. Aiming at secure data storage, Chenam and Ali [1] proposed an encryption scheme based on certificateless public key authentication to resist keyword guessing attacks. Besides, to aid security and efficiency, Shiraly et al. [2] first designed a security model facing multi-servers and then proposed a certificateless public key encryption scheme with keyword search proved secure under the security model they described. To tackle the problem of mutual authentication in the process of data transmission, Turkanović et al. [3] designed a user authentication and key agreement scheme focusing on the wireless sensor networks. However, Farash et al. [4] pointed out that the scheme of Turkanović et al. was susceptible to several shortcomings mainly threatening the identities of users. Further, they [4] proposed an improved protocol tackling and eliminating the security shortcomings of the previous one.
Because of the high bandwidth of mobile communication, lightweight cryptography was proposed to satisfy the urgent requirement of high communication efficiency. In 2016, Gope et al. [5] proposed a realistic lightweight anonymous user authentication protocol in wireless networks. However, in 2019, Adavoudi-Jolfaei et al. [6] showed that in Gope et al.’s scheme the adversary could obtain the session key under the Dolev-Yao model [7]. Further, they designed a lightweight and anonymous three-factor authentication and access control scheme for real-time applications. But one year later, Ryu et al. [8] found the weaknesses of Adavoudi et al.’s protocol including insider attacks, user impersonation attacks, and session key attacks. To address these problems, they proposed a three-factor authentication scheme based on hash function and XOR.
AI-Riyami and Paterson [9] firstly introduced certificateless public key cryptography (CL-PKC) in 2003. Once the concept was proposed, adopted widely has it been to expand authenticated key agreement (AKA) protocols because of the two advantages this scheme possesses. First, CL-PKC is capable of static private key leakage resistance since the full private key is composed of two parts, one generated by key generation center (KGC) and the other generated by the user. Second, few computation resource is needed by CL-PKC which is required urgently in the Internet of Things.
Mandt et al. [10] improved the efficiency of AI-Riyami et al.’s scheme based on the bilinear Diffie-Hellman problem. Wang et al. [11] also pointed out that the efficiency of AI-Riyami et al.’s scheme was low since it at least required a paring evaluation computed on-line. Thus, Wang et al. proposed a certificateless authenticated key agreement (CL-AKA) protocol for Web client/server setting. Later, Hou and Xu [12] found that the scheme could not resist key compromised impersonation attacks, man-in-the-middle attacks and key replicating attacks.
Because of the advantages of CL-PKC, it has been applied in various environments. Asari et al. [13] utilized CL-PKC in automatic dependent surveillance-broadcast (ADS-B) systems and designed a certificateless authentication protocol resolving the privacy problem. In vehicular ad hoc networks (VANETs), both privacy and efficiency are necessary. A certificateless conditional anonymous authentication scheme was investigated by Samra et al. [14] for softwares in VANETs. Also, patients’ diagnosis information plays a vital role in wireless body area network (WBAN) which motivates designers to find resolutions. Cheng et al. [15] designed a CL-AKA for cloud-enabled WBAN based on ECDL assumption.
Recently, considering the drawbacks of existing AKA protocols, Wang et al. [17] designed a computation-transferable AKA scheme without an online registration center for smart healthcare networks. Nevertheless, in this paper, the shortcomings of Wang et al.’s scheme will be illustrated, proving that theirs could not satisfy the forward security.
The main contributions of this paper are summarized specifically as follows.
-
Recently, Wang et al. [17] proposed an AKA protocol, denoted as WHX protocol, for smart healthcare and claimed that it satisfied security and privacy protection requirements. However, an effective attack on WHX protocol is presented, which proves that WHX protocol does not satisfy the forward security.
-
To remedy the shortcoming we point out, a secure and efficient CL-AKA scheme is designed which can resist common attacks and achieve mutual authentication as well as key agreement.
-
Security analysis claims that the proposed scheme can satisfy security properties required urgently in smart healthcare environment. Performance evaluation and comparison demonstrated in Sect. 6 shows that the design scheme can behave better than other related schemes.
The arrangement of this paper is following. The security model is presented in Sect. 2. In Sect. 3, a brief review of the WHX protocol is presented. Then a specific security analysis of WHX protocol is presented in this section as well. In Sect. 4, the detailed procedures of the proposed scheme are illustrated. Following is the security analysis in Sect. 5. Performance evaluation and comparison are presented in Sect. 6. Finally, Sect. 7 provides some concluding remarks.
2 Security Model
For discussing the security of the proposed scheme, here, we introduce a security model suitable for the CL-AKA setting based on [16]. In particular, let \(\mathcal {A}\) and \(\varPi _{\varGamma }^{\varphi }\) be a probabilistic polynomial time adversary and \(\varphi \)th instance of a participant \(\varGamma \), respectively. There exist two types of adversaries, denoted as \(\mathcal {A}_{1}\) and \(\mathcal {A}_{2}\). The main difference between them is that \(\mathcal {A}_{1}\) does not have the ability of knowing the master key but can replace the public keys of any participant with selected values while \(\mathcal {A}_{2}\) has the ability of learning the master key but can not replace the public keys of participants.
The security of the proposed scheme is defined based on a game executed between \(\mathcal {A}\) and a challenger \(\mathcal {C}\). In the game, the abilities of \(\mathcal {A}\) are described by several kinds of queries answered by \(\mathcal {C}\) shown in Table 1.
After making a Test-query towards an instance \(\varPi _{\varGamma }^{\varphi }\), \(\mathcal {A}\) can also make queries towards \(\varPi _{\varGamma }^{\varphi }\) or to the matching session (if it exists) except Reveal-query and Corrupt-query towards the potential partner. Finally, \(\mathcal {A}\) should output a guess result \(c^{\prime }\). If \(c^{\prime }=c\), then \(\mathcal {A}\) wins the game.
Definition. A CL-AKA protocol is secure if any session instance \(\varPi _{\varGamma }^{\varphi }\) satisfies:
-
achieving the same session key with its matching session.
-
making sure that the advantage \(Advantage_{\mathcal {A}}(\varPi _{\varGamma }^{\varphi })=|2P[c^{\prime }=c]-1|\) is negligible for any \(\mathcal {A}\).
3 Review and Cryptanalysis of WHX AKA Protocol
In this section, we review the process of WHX AKA protocol [17] briefly, including initialization, registration, and authentication and key agreement three phases. The notations used in this paper are listed in Table 2.
3.1 Review of WHX AKA Protocol
Let q be a large prime number. The system is initialized by RC. First, it chooses a non-singular elliptic curve \(E(F_{q})\) and an additive group \(\mathbb {G}\) over it. The generator of \(\mathbb {G}\) is P whose order is q. RC then chooses s randomly in \(Z_{q}^{*}\), computes \(P_{pub}=sP\) and selects eight hash functions \(H_{i}:\{0,1\}^{*}\rightarrow \{0,1\}^{l}\), \((i=0,1,...,7)\). Finally, it keeps the master key s as a secret and publishes the system parameters \(\{q,P,\mathbb {G},P_{pub},H_{i}(i=0,1,...,7)\}\).
Before communicating, users and edge servers need to register with RC through a secure channel to get their static private key and corresponding public key. For a comprehensive process, readers can refer to the original paper [17].
After registering successfully with RC, \(U_{i}\) and ES can start to authenticate each other and negotiate about the session key. The detailed steps are as follows:
-
\(U_{i}\) selects \(a\in Z_{q}^{*}\) randomly and computes \(u, A, \eta \). Then \(U_{i}\) sends the message \(M_{1}=\{u,A,\eta ,T_{i}\}\) to ES where \(T_{i}\) is the current timestamp.
-
ES checks the freshness of \(T_{i}\) and the validation of \(\eta \). If holds, ES chooses \(b\in E_{q}^{*}\) randomly and calculates \(v, V, K_{ES}, SK_{ES}\) and \(\omega \), where the timestamp is denoted as \(T_{j}\). Next, ES sends the message \(M_{2}=\{V,\omega ,T_{j}\}\) to \(U_{i}\).
-
\(U_{i}\) verifies whether \(T_{i}\) is fresh. If successes, \(U_{i}\) computes \(K_{U},SK_{U}\). Further, \(U_{i}\) checks \(\omega \). If holds, it calculates \(\lambda \) and sends the message \(M_{3}=\{\lambda \}\) to ES.
-
Finally, ES tests the correctness of \(\lambda \).
3.2 Cryptanalysis of WHX AKA Protocol
In this subsection, we present that WHX protocol can not satisfy the requirement of forward security. If the private key of user \(U_{i}\) is compromised, the adversary \(\mathcal {A}\) will recover the session key easily through the steps below:
-
Step 1. In the authentication and key agreement phase, \(\mathcal {A}\) eavesdrops the message sent from \(U_{i}\) to ES, \(M_{1}=\{u,A,\eta ,T_{i}\}\).
-
Step 2. \(\mathcal {A}\) eavesdrops the message sent from ES to \(U_{i}\), \(M_{2}=\{V,\omega ,T_{j}\}\).
-
Step 3. After the session is completed, \(\mathcal {A}\) launches Reveal-query towards the user \(U_{i}\) to gain its private secret keys \((s_{U},x_{U})\).
-
Step 4. After obtaining the parameters above, \(\mathcal {A}\) can easily compute \(a=u-x_{U}\), \(PID^{\prime }_{U}=A\oplus H_{3}(u\cdot X_{ES})\). Then, \(\mathcal {A}\) can extract \(K^{\prime }_{U}\) by \(K^{\prime }_{U}=s_{U}\cdot (V-X_{ES})+a\cdot [R_{ES}+H_{2}(ID_{ES}\Vert R_{ES})P_{pub}]\), where \(X_{ES}, R_{ES}, P_{pub}\) are the public keys. Finally, \(\mathcal {A}\) can compute the session key according to the way generating \(SK_{U}=H_{5}(K^{\prime }_{U}\Vert ID_{ES}\Vert PID^{\prime }_{U}\Vert X_{U}\Vert X_{ES})\).
Thus, in this way, adversary \(\mathcal {A}\) can recover the session key. According to the steps above, we can see that the adversary merely gets the private keys of user, which is accordant with the definition of weak forward security. Besides, although the real identity of the patients is unknown to the public, the \(PID_{U}\) can still be accessed easily, which means that WHX protocol can not resist traceability.
4 The Improved Scheme
We present a detailed description of the improved AKA scheme in this section. There are three phases involved in our scheme, which are the initialization phase, the registration phase, the authentication and key agreement phase, respectively. The details are described as follows.
4.1 Initialization Phase
Let l represent the length of the session key. RC, responsible for the initialization of the system, acts as the following steps:
-
Selects an additive cyclic group \(\mathbb {G}\) over a non-singular elliptic curve \(E(F_{p})\). The order of \(\mathbb {G}\) is q, a large prime number, and the generator is P.
-
Chooses a random number \(s\in Z_{q}^{*}\) as its master key and calculates \(P_{pub}=sP\).
-
Selects five one-way hash functions \(H_{i} (i=1,2,...,5)\).
-
Keeps the master key s as a secret while publishes the system parameters \(\{\mathbb {G}, q, P, P_{pub}, H_{i}\}\).
4.2 Registration Phase
Before beginning the authentication and key agreement, both the user and the edge server need to register with the RC in the off-line channel. A user \(U_{i}\) with its unique identity \(ID_{U}\) can register with RC according to the steps below:
-
Selects \(x_{U}\in Z_{q}^{*}\) randomly as the secret key and computes \(X_{U}=x_{U}P\) and sends \(\{ID_{U}, X_{U}\}\) to RC through a secure channel.
-
On receiving \(\{ID_{U}, X_{U}\}\), RC extracts \(PID_{U}=H_{1}(ID_{U}\parallel s)\). Then it randomly selects \(r_{U}\in Z_{q}^{*}\) and computes \(R_{U}=r_{U}P\), \(h_{U}=H_{2}(X_{U}\parallel R_{U}\parallel PID_{U})\), \(s_{U}=r_{U}+s\cdot h_{U}\). Then RC sends \(\{R_{U}, s_{U}, PID_{U}\}\) to \(U_{i}\), where \(s_{U}\) is the partial private key of \(U_{i}\).
-
\(U_{i}\) checks if \(s_{U}P=R_{U}+H_{2}(X_{U}\parallel R_{U}\parallel PID_{U})P_{pub}\) is true. If so, \(U_{i}\) securely stores \((s_{U}, x_{U})\) as its full private key and publishes \((R_{U}, X_{U})\).
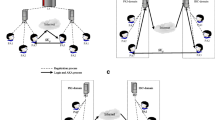
Similarly, ES registers with RC, illustrated in Fig. 1.
4.3 Authentication and Key Agreement Phase
User \(U_{i}\) and ES authenticate mutually and agree on a session key for a secure communication. Figure 1 shows the authentication and key agreement phase in detail and the specific process is presented below:
-
User \(U_{i}\) selects a random value \(a\in Z_{q}^{*}\), then computes \(u=x_{U}+a\), \(U=u\cdot P\), \(A=PID_{U}\oplus H_{3}(u\cdot X_{ES})\), and \(\eta =H_{4}(U\parallel PID_{U}\parallel T_{i})\), where \(T_{i}\) is the current timestamp. Then \(U_{i}\) sends \(M_{1}=\{U,A,\eta ,T_{i}\}\) to ES.
-
Upon receiving the message from \(U_{i}\), ES first checks the validation of timestamp \(T_{i}\). Then calculates \(PID^{\prime }_{U}=A\oplus H_{3}(x_{ES}\cdot U)\), \(\eta ^{\prime }=H_{4}(U\parallel PID^{\prime }_{U}\parallel T_{i})\). Therefore, ES can validate the user’s identity through \(\eta ^{\prime }\). If the equation holds, ES chooses a random value \(b\in Z_{q}^{*}\), then calculates \(v=x_{ES}+b\), \(V=v\cdot P\), \(K_{ES}=s_{ES}\cdot [R_{U}+H_{1}(X_{U}\parallel R_{U}\parallel PID_{U})P_{pub}]\), \(SK_{ES}=H_{5}(K_{ES}\parallel ID_{ES}\parallel PID_{U}\parallel b\cdot (U-X_{U})\parallel T_{j})\), \(\omega =E_{x_{ES}U}(ID_{ES})\). Then ES sends the message \(M_{2}=\{V,\omega ,T_{j}\}\) to the patient user \(U_{i}\), where \(T_{j}\) is the current timestamp.
-
After receiving \(M_{2}\), \(U_{i}\) first checks whether \(T_{j}\) has expired. Then \(U_{i}\) computes \((ID_{ES})=D_{uX_{ES}}(\omega )\) and checks the identity of server. If it holds, then \(U_{i}\) continues to calculates \(K_{U}=s_{U}\cdot [R_{ES}+H_{2}(ID_{ES}\parallel R_{ES})P_{pub}]\), \(SK_{U}=H_{5}(K_{U}\parallel ID_{ES}\parallel PID_{U}\parallel a\cdot (V-X_{ES})\parallel T_{j})\). Consequently, \(U_{i}\) and ES complete the authentication and key agreement phase.
Finally, \(U_{i}\) and ES successfully achieve the same session key since:
Therefore, the proposed scheme is provably correct.
5 Security Analysis of the Proposed Scheme
In this section, we analyze the security of the proposed scheme. First, we prove that the proposed scheme is secure against two types of adversaries. Then, we present the analysis result of Scyther tool claiming that our scheme is secure against common attacks.
Theorem 1
Assume that the Computational Diffie-Hellman (CDH) problem is intractable. Let \(\mathcal {A}_{1}\) be a probabilistic polynomial time adversary against the proposed scheme \(\varPi \), the advantage of \(\mathcal {A}_{1}\) against our scheme is negligible.
Proof
Suppose there exists a probabilistic polynomial time adversary \(\mathcal {A}_{1}\) who can win the game with a non-negligible advantage in polynomial time t. Then, we can design an algorithm \(\mathcal {C}\) to solve the CDH problem using the ability of \(\mathcal {A}_{1}\).
Suppose \(\mathcal {C}\) is given an instance (aP, bP) of the CDH problem whose subject is to compute \(Q=abP\). Suppose \(\mathcal {A}_{1}\) makes at most \(q_{H_{i}}\) times \(H_{i}\)-query and creates at most \(q_{c}\) participants and \(q_{s}\) be the maximal number of sessions each participant may be involved in.
\(\mathcal {C}\) sets \(P_{0}\) as the system public key \(P_{pub}\), selects the system parameter \(params=\{F_{p}, E/F_{p},G, P, P_{pub}, H_{i}\}\) and sends the public parameters to \(\mathcal {A}_{1}\). \(\mathcal {C}\) chooses at random \(I\in [1,q_{H_{2}}]\), \(J \in [1,q_{H_{2}}]\), \(T\in [1,q_{s}]\), \(s_{J}, x_{J},h_{J} \in Z_{q}^{*}\), then \(\mathcal {C}\) computes \(R_{J}=s_{J}P-h_{J}P_{pub}\), \(X_{J}=x_{J}P\). \(\mathcal {C}\) answers \(\mathcal {A}_{1}\)’s queries as follows.
-
Create\((ID_{j})\): \(\mathcal {C}\) keeps an empty list \(L_{C}\) consisting of tuples \((ID_{j}, (s_{j}, x_{j}), (R_{j},\) \(X_{j}))\). If \(ID_{j} = ID_{J}\), \(\mathcal {C}\) lets j’s private key and public key be \((s_{J},x_{J})\), and \((R_{J},X_{J})\) respectively. \(\mathcal {C}\) also lets \(H_{2}(ID_{J},R_{J})\leftarrow h_{J}\), where \(R_{J}\), \(x_{J}\), and \(h_{J}\) are the variables mentioned above. Otherwise, \(\mathcal {C}\) chooses a random \(x_{j},s_{j},h_{j}\in Z_{q}^{*}\) and computes \(R_{j}=s_{j}P-h_{j}P_{pub}\) and \(X_{j}=x_{j}P\). Thus, \(ID_{j}\)’s private key is the tuple \((s_{j}, x_{j})\) and its public key is \((R_{j},X_{j})\). At last, \(\mathcal {C}\) adds the tuple \((ID_{j},R_{j},h_{j})\) and \((ID_{j}, (s_{j}, x_{j}), (R_{j}, X{j}))\) to the list \(L_{H_{2}}\) and \(L_{C}\), separately.
-
Send\((\varPi _{i,j}^{n}, M)\): \(\mathcal {C}\) keeps an empty list \(L_{S}\) in the form of a tuple \((\varPi _{i,j}^{n}, path_{i,j}^{n},\) \(r_{i,j}^{n})\), in which \(path_{i,j}^{n}\) is a record of session message \(\varPi _{i,j}^{n}\) and \(r_{i,j}^{n}\) is defined as below.
-
If \(n=T, ID_{i}=ID_{I}, ID_{j}=ID_{J}\), \(\mathcal {C}\) returns aP as U and updates the tuple \(r_{i,j}^{n}=\bot \).
-
Else \(\mathcal {C}\) returns the corresponding answer according to the steps.
-
-
Reveal\((\varPi _{i,j}^{n})\): \(\mathcal {C}\) keeps an empty list \(L_{R}\). If \(n=T, ID_{i}=ID_{I}, ID_{j}=ID_{J}\) or \(\varPi _{i,j}^{n}\) is the matching session of \(\varPi _{I,J}^{T}\), \(\mathcal {C}\) aborts this query; otherwise, \(\mathcal {C}\) answers as follows:
-
If \(ID_{i}\ne ID_{I}\), \(\mathcal {C}\) searches for the list \(L_{C}\) and \(L_{S}\) for the detailed data and makes an \(H_{5}\) query to compute the session key \(SK_{i,j}^{n}\).
-
Else \(\mathcal {C}\) chooses a random number \(SK_{i,j}^{n}\in \{0,1\}^{l}\).
-
-
Corrupt\((ID_{i})\): If \(ID_{i}=ID_{I}\), then \(\mathcal {C}\) aborts this query; otherwise, \(\mathcal {C}\) searches for a tuple \(\{ID_{i}, (s_{i}, x_{i}), (R_{i},X_{i})\}\) in \(L_{C}\) indexed by \(ID_{i}\) and returns \((s_{i}, x_{i})\).
-
Replacement\((ID_{i},(R^{\prime }_{i},X^{\prime }_{i}))\): \(\mathcal {C}\) searches for a tuple \(\{ID_{i}, (s_{i},x_{i}), (R_{i},X_{i})\}\) in \(L_{C}\) which is indexed by \(ID_{i}\) then replaces \((R_{i},X_{i})\) with \((R^{\prime }_{i},X^{\prime }_{i})\).
-
\(H_{5}\) query: \(\mathcal {C}\) keeps an empty list \(L_{H_{5}}\) of the tuple \((\{K_{i},ID_{j},PID_{i},\lambda ,T_{j}\}, h_{u})\) where \(\lambda \) represents \(a(U_{j}-X_{j})\) or \(b(U_{i}-X{i})\) and it answers this query as below:
-
If \((\{K_{i},ID_{j},PID_{i},\lambda ,T_{j}\},h_{u})\) has been in the list \(L_{H_{5}}\), \(\mathcal {C}\) returns \(h_{u}\).
-
Else \(\mathcal {C}\) looks for \(L_{R}\). If there exists the record then \(\mathcal {C}\) returns the correspond session key \(SK_{i,j}^{n}\).
-
Else \(\mathcal {C}\) chooses a random number \(h_{u}\in \{0,1\}^{l}\) and adds the record in the list \(L_{H_{5}}\).
-
The probability is that \(\mathcal {A}_{1}\) chooses \(\varPi _{I,J}^{T}\) as the Test oracle and that \(1/q^{2}_{c}q_{s}\). In this case, \(\mathcal {A}_{1}\) would not have made Corrupt(\(ID_{I}\)), Corrupt(\(ID_{J}\)) or Reveal(\(\varPi _{I,J}^{T}\)) queries, and so \(\mathcal {C}\) would not have aborted. If \(\mathcal {A}_{1}\) can win in such a game, then \(\mathcal {A}_{1}\) must have made the corresponding \(H_{5}\) query. Therefore, \(\mathcal {C}\) can find the corresponding record in the list of \(L_{H_{5}}\) indexed by \(\{K_{i},ID_{j},PID_{i},\lambda ,T_{j}\}\) with the probability \(1/q_{H_{5}}\) and output \(\lambda \) as the result of the CDH problem. Therefore, the probability, denoted as \(\alpha \) that \(\mathcal {C}\) tackles the CDH problem satisfies \(\alpha >Adv_{\mathcal {A}_{1}}/q^{2}_{c}q_{s}q_{H_{5}}\), where \(Adv_{\mathcal {A}_{1}}\) is the advantage that \(\mathcal {A}_{1}\) wins the game.
Theorem 2
Assume that the Computational Diffie-Hellman (CDH) problem is intractable. Let \(\mathcal {A}_{2}\) be a probabilistic polynomial time adversary against the proposed scheme \(\varPi \), the advantage of \(\mathcal {A}_{2}\) against our scheme is negligible.
Proof
Suppose there exists a probabilistic polynomial time adversary \(\mathcal {A}_{2}\) who can win the game with a non-negligible advantage in polynomial time t. Then, we can design an algorithm \(\mathcal {C}\) to solve the CDH problem using the ability of \(\mathcal {A}_{2}\).
Suppose \(\mathcal {C}\) is given an instance (aP, bP) of the CDH problem whose subject is to compute \(Q=abP\). Suppose \(\mathcal {A}_{2}\) makes at most \(q_{H_{i}}\) times \(H_{i}\)-query and creates at most \(q_{c}\) participants and \(q_{s}\) be the maximal number of sessions each participation may be involved in.
\(\mathcal {C}\) sets \(P_{0}\) as the system public key \(P_{pub}\), selects the system parameter \(params=\{F_{p}, E/F_{p},G, P, P_{pub}, H_{i}\}\) and sends the public parameters to \(\mathcal {A}_{2}\). \(\mathcal {C}\) chooses at random \(I \in [1,q_{H_{2}}]\), \(J \in [1,q_{H_{2}}]\), \(T\in [1,q_{s}]\). \(\mathcal {C}\) answers \(\mathcal {A}_{2}\)’s queries as follows.
If \(\mathcal {A}_{2}\) makes Create\((ID_{i})\) query, \(\mathcal {C}\) keeps an empty list \(L_{C}\) consisting of tuples \((ID_{i}, (s_{i}, x_{i}), (R_{i}, X{i}))\). \(\mathcal {C}\) randomly selects \(s_{I}, h_{I}\in Z_{q}^{*}\) and computes \(R_{I}=r_{I}P\), \(s_{I}=r_{I}+sh_{I}\) and \(X_{I}=x_{I}P\). \(\mathcal {C}\) can answer other queries as Theorem 1.
The probability is that \(\mathcal {A}_{2}\) chooses \(\varPi _{I,J}^{T}\) as the Test oracle and that \(1/q^{2}_{c}q_{s}\). In this case, \(\mathcal {A}_{2}\) would not have made Corrupt(\(ID_{I}\)), Corrupt(\(ID_{J}\)) or Reveal(\(\varPi _{I,J}^{T}\)) queries, and so \(\mathcal {C}\) would not have aborted. If \(\mathcal {A}_{2}\) can win in such a game, then \(\mathcal {A}_{2}\) must have made the corresponding \(H_{5}\) query. Therefore, \(\mathcal {C}\) can find the corresponding record in the list of \(L_{H_{5}}\) indexed by \(\{K_{i},ID_{j},PID_{i},\lambda ,T_{j}\}\) with the probability \(1/q_{H_{5}}\) and output \(\lambda \) as the result of the ECDH problem. Therefore, the probability, denoted as \(\alpha \) that \(\mathcal {C}\) tackles the ECDH problem satisfies \(\alpha >Adv_{\mathcal {A}_{2}}/q^{2}_{c}q_{s}q_{H_{5}}\), where \(Adv_{\mathcal {A}_{2}}\) is the advantage that \(\mathcal {A}_{2}\) wins the game.
From the above two theorems, we can conclude that our scheme is secure against two types of adversaries.
Besides proving the security of the proposed scheme under the security model, we also use Scyther tool to show the proposed scheme is secure against various attacks. The result of analysis is demonstrated in the Fig. 2. According to the Fig. 2, we can clearly obtain that under the settings predefined, the scheme can achieve mutual authentication and secure session keys simultaneously.
6 Performance Analysis
This section presents the performance assessment of the proposed scheme on the security features, computation cost and communication cost.
6.1 Security Comparison
In this subsection, we compare the security features of the proposed scheme with other related schemes [17,18,19,20], and the result is shown in Table 3. We can see that our proposed scheme can resist various attacks and satisfies the security requirements from Table 3, which means that our scheme is superior to other previous schemes in terms of security features.
6.2 Computation Cost
The computation cost of the proposed scheme is compared with that of previously mentioned schemes. In terms of setting the experimental environment, we choose an additive group with the generator P and the order q, where q is 160 bits. The generator P is a base point on the Koblitz curve secp256k1: \(y^{2}=x^{3}+7\), denoted as \(E/F_{p}\) and p is 256 bits. In this paper, we mainly consider the execution time of scalar multiplication, hash function and point addition operation on an elliptic curve. Several lightweight operations, such as XOR and addition, are ignored. Table 4 shows the concrete results of these operations [17].
Mainly considering the authentication and key agreement phase, the comparison result is shown in Fig. 3. In our scheme, the computation time needed in user side for authentication and key agreement process is four hash function operations, four scalar multiplication operations, two point additions and one encryption while that of the server side is four hash function operations, five scalar multiplication operations, three point additions and one decryption. Therefore, the total execution time of our proposed scheme is 11.9204 ms. In the scheme of He et al. [18], the computation cost of user side is \(T_{mp}+3T_{sm}+4T_{h}+2T_{exp}=7.4852\) ms and server side is \(2T_{bp}+5T_{h}+2T_{a}+T_{exp}=7.2777\) ms. Similarly, the computation overheads of user side and server side in Liu et al.’s scheme [19] are \(6T_{sm}+5T_{h}+5T_{a}=7.1087\) ms and \(6T_{sm}+5T_{h}+5T_{a}=7.1887\) ms, respectively.
6.3 Communication Cost
In this subsection, the comparison of the communication cost between our proposed scheme with other related schemes is presented. We assume that the length of identity, login request and timestamp is 32 bits, marked as \(\left| ID \right| \), \(\left| L \right| \), \(\left| T \right| \), respectively. The output length of hash function is 160 bits, expressed as \(\left| H \right| \). A ciphertext block is 128 bits, expressed as \(\left| C \right| \) and the lengths of p and q are 256 bits and 160 bits, respectively. In this way, a point on elliptic curve \(G=(G_{x},G_{y})\) is 512 bits, denoted as \(\left| G \right| \). Further, assume a value in \(Z_{q}^{*}\) be 160 bits, which is denoted as \(\left| Z_{q}^{*} \right| \).
During the communication between \(U_{i}\) and ES in the proposed scheme, the message \(M_{1}\) sent by user \(U_{i}\), requires \(\left| G \right| +2\left| H \right| +\left| T \right| =864\) bits; and the message \(M_{2}\) sent by ES, employs the cost of \(\left| G \right| +\left| C \right| +\left| T \right| =672\) bits. Therefore, the addition of all the messages is 1568 bits. In the protocol [19], the communication cost needed by user side is \(\left| T \right| +2\left| G \right| +\left| H \right| +\left| Z_{q}^{*} \right| =1376\) bits while that by server require \(2\left| G \right| +\left| ID \right| +\left| Z_{q}^{*} \right| =1216\) bits, so the total cost is 2592 bits. The communication cost of the other related schemes can be computed similarly and the final result is shown in Table 5.
From comparison results in Table 5, it can be concluded that the communication cost of our proposed scheme generally has less communication cost than other related schemes. Although the communication cost of our proposed scheme is higher than that of WHX protocol, our scheme can satisfy more secure requirements.
7 Conclusion
In this paper, we point out that there exists forward security problem in WHX protocol. Aiming at remedy such potential risk, we propose an improved scheme based on the former one. The proposed scheme redesigns the generation of the session key without depending too much on the ephemeral keys. To comprehensively prove its security, formal analysis and informal analysis are used by combining theory and tools. Moreover, to evaluate the performance, we give comparisons on computation and communication cost with the former schemes. The analysis results of security and performance illustrate that our scheme is exactly security-enhanced with the forward security and outperforms WHX protocol from the perspective of computation cost.
References
Chenam, V.B., Ali, S.T.: A designated cloud server-based multi-user certificateless public key authenticated encryption with conjunctive keyword search against IKGA. Comput. Stand. Interfaces 81, 103603 (2022)
Shiraly, D., Pakniat, N., Noroozi, M., Eslami, Z.: Paring-free certificateless authenticated encryption with keyword search. J. Syst. Archit. 124, 102390 (2022)
Turkanović, M., Brumen, B., Hölbl, M.: A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 20, 96–112 (2014)
Farash, M.S., Turkanović, M., Kumari, S., Hölbl, M.: An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the Internet of Things environment. Ad Hoc Netw. 36, 152–176 (2016)
Gope, P., Hwang, T.: A realistic lightweight anonymous authentication protocol for securing real-time application data access in wireless sensor networks. IEEE Trans. Ind. Electron. 63(11), 7124–7132 (2016)
Adavoudi-Jolfaei, A.H., Ashouri-Talouki, M., Aghili, S.F.: Lightweight and anonymous three-factor authentication and access control scheme for real-time applications in wireless sensor networks. Peer Peer Netw. Appl. 12(1), 43–59 (2017). https://doi.org/10.1007/s12083-017-0627-8
Dolev, D., Yao, A.: On the security of public key protocols. IEEE Trans. Inf. Theory 29(2), 198–208 (1983)
Ryu, J., Kang, D., Lee, H., Kim, H., Won, D.: A secure and lightweight three-factor-based authentication scheme for smart healthcare systems. Sensors 20(24), 7136 (2020)
Al-Riyami, S.S., Paterson, K.G.: Certificateless public key cryptography. In: Laih, C.-S. (ed.) ASIACRYPT 2003. LNCS, vol. 2894, pp. 452–473. Springer, Heidelberg (2003). https://doi.org/10.1007/978-3-540-40061-5_29
Mandt, T.K., Tan, C.H.: Certificateless authenticated two-party key agreement protocols. In: Okada, M., Satoh, I. (eds.) ASIAN 2006. LNCS, vol. 4435, pp. 37–44. Springer, Heidelberg (2007). https://doi.org/10.1007/978-3-540-77505-8_4
Wang, S.B., Cao, Z.F., Wang, L.C.: Efficient certificateless authenticated key agreement protocol from pairings. Wuhan Univ. J. Nat. Sci. 11(5), 1278–1282 (2006)
Hou, M.B., Xu, Q.L.: On the security of certificateless authenticated key agreement protocol. In: 2009 IEEE International Symposium on IT in Medicine Education, pp. 974–979. IEEE (2009)
Asari, A., Alagheband, M.R., Bayat, M., Asaar, M.R.: A new provable hierarchical anonymous certificateless authentication protocol with aggregate verification in ADS-B systems. Comput. Netw. 185(11), 107599 (2021)
Samra, B., Fouzi, S.: New efficient certificateless scheme-based conditional privacy preservation authentication for applications in VANET. Veh. Commun. 34, 100414 (2022)
Cheng, Q.F., Li, Y.T., Shi, W.B., Li, X.H.: A certificateless authentication and key agreement scheme for secure cloud-assisted wireless body area network. Mob. Netw. Appl. 27, 346–356 (2022)
He, D.B., Chen, J.H., Hu, J.: A pairing-free certificateless authenticated key agreement protocol. Int. J. Commun. Syst. 25(2), 221 (2011)
Wang, W.M., Huang, H.P., Xiao, F., Li, Q., Xue, L.Y., Jiang, J.S.: Computation-transferable authenticated key agreement protocol for smart healthcare. J. Syst. Archit. 118, 102215 (2021)
He, D.B., Kumar, N., Khan, M.K., Wang, L.N., Shen, J.: Efficient privacy-aware authentication scheme for mobile cloud computing services. IEEE Syst. J. 12(2), 1621–1631 (2018)
Liu, X., Jin, C., Li, F.: An improved two-layer authentication scheme for wireless body area networks. J. Med. Syst. 42, 143 (2018)
Odelu, V., Das, A.K., Goswami, A.: A secure biometrics-based multi-server authentication protocol using smart cards. IEEE Trans. Inf. Forensics Secur. 10(9), 1953–1966 (2015)
Acknowledgment
This work was supported in part by National Natural Science Foundation of China (Grant No. 61872449).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Ma, Y., Ma, Y., Liu, Y., Cheng, Q. (2022). A Secure and Efficient Certificateless Authenticated Key Agreement Scheme for Smart Healthcare. In: Chen, X., Shen, J., Susilo, W. (eds) Cyberspace Safety and Security. CSS 2022. Lecture Notes in Computer Science, vol 13547. Springer, Cham. https://doi.org/10.1007/978-3-031-18067-5_2
Download citation
DOI: https://doi.org/10.1007/978-3-031-18067-5_2
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-18066-8
Online ISBN: 978-3-031-18067-5
eBook Packages: Computer ScienceComputer Science (R0)