Abstract
Counter-terrorism and its preventive and response actions are crucial factors in security planning and protection of mass events, soft targets and critical infrastructures in urban environments. This paper presents a comprehensive Decision Support System developed under the umbrella of the S4AllCitites project, that can be integrated with legacy systems deployed in the Smart Cities. The system includes urban pedestrian and vehicular evacuation, considering ad-hoc predictive models of the evolution of incendiary and mass shooting attacks in conjunction with a probabilistic model for threat assessment in case of improvised explosive devices. The main objective of the system is to provide decision support to public or private security operators in the planning and real time phases in the prevention or intervention against a possible attack, providing information on evacuation strategies, the probability or expected impact of terrorist threats and the state of the traffic network in normal or unusual conditions allowing the emergency to be managed throughout its evolution.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
International terrorism has many dimensions and characteristics depending on factors such as the historical and geographical context, political links or factors related to different terrorist groups and organizations (Tuman 2009). Today security and terrorism are one of the most widespread problems that requires the attention of law enforcement agencies, policy makers and political institutions due to the social and economic impact it generates. Despite this dependence on factors, terrorist attacks have the purpose of creating great harm and consternation in the population. Cities are a spotlight as they cluster large populations in small areas susceptible to terrorist attacks. Therefore, in the field of anti-terrorist urban security, and more broadly in the context of mass events, critical infrastructures and soft targets, it is mandatory to have adequate planning and response strategies to deal with such emergencies. Hence, this paper proposes a Decision Support System (DSS) that can be used during planning and response phases anticipating terrorist threats and while helping to address emergency management issues within the context of smart cities.
According to the (Global Terrorism Database™ (GTD) 2021) more than half of the attacks worldwide are Improvised Explosive Devices (IED), mass shooting, arsons or incendiary/smoke devices attacks. The expected evolution of this kind of attacks (Martin 2016) (EUROPOL 2021) are the necessary foundation for the development of models that can help to minimize their consequences.
More specifically, between 2010 and 2019 29.4% of terrorist attacks were targeted against the population (Global Terrorism Database™ (GTD) 2021), with cities being a major attraction for the terrorists. In this context there is an increment of smart cities that use Information and Communication Technologies (ICT) to increase operational efficiency, share information with the public and improve both the quality of government services and citizen welfare. An important point is that smart cities also need to ensure a secure and safe physical and digital ecosystem for the well-being of citizens. Therefore, it is mandatory to utilize the capabilities already available in smart cities to improve security and safety. These include, for example, anomaly detection, authentication and identification of individuals, threat localisation, behavioural profiling, suspect tracking, traffic monitoring, emergency management and many other capabilities related with awareness, prevention and response (Laufs et al. 2020).
These capabilities have been studied from different perspectives leading to a wide range of results including threats and individuals detection (Chackravarthy et al. 2018) (Bellini et al. 2017), screening and tracking (Brust et al. 2017) (Anees and Kumar 2017), recognition-based authentication (Balla and Jadhao 2018; Boukerche et al. 2017) or the improvement of legacy systems deployed throughout the city endowing them with intelligence (Zingoni et al. 2017; Zhou et al. 2015). However, due to our particular approach, we must emphasise that there are hardly any studies (Dbouk et al. 2014; Bonatsos et al. 2013) that propose a comprehensive DSS involving at the same time emergency management, real-time decision support and forecasting of threats evolution and impact of most common terrorist attacks. The closest in these terms to the existing literature is focused on the management of common crimes such as vandalism and violence, both in terms of management (Fernández et al. 2013), information systems (Truntsevsky et al. 2018), unusual traffic management (Hartama et al. 2017), evacuation (Zhang et al. 2018) and to a lesser extent on the prediction of events such as robbery or homicide (Noor et al. 2013; Araujo et al. 2017).
Thus, this study jointly addresses the facets of predicting and assess the impact of terrorist attacks (IED, mass shooting and arson), together with the management of emergency situations in terms of pedestrian and vehicular intervention, evacuation and monitoring by proposing a comprehensive conceptual and computational model that implements a DSS. This system involves different data sources and computer simulations providing support to decision makers/operators to make appropriate planning, management or response decision (Turban 1995).
2 Material and Method
2.1 Conceptual Model
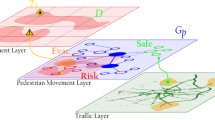
On the basis of the initial definition of a smart city, a three-layers structure can be used to formalise the mathematical model of the proposed DSS (Decision Support System), see Fig. 1.
Threat Assessment Layer:
Comprises a set of soft targets, crowded areas and infra-structures \(S=\{{s}_{0},{s}_{1},\dots ,{s}_{n}\}\) where security monitoring is desired. A soft-target can be defined as \({s}_{k}=\{B, P,A,D,O\}\), where \(B=\left\{\left({\phi }_{0},{\theta }_{0}\right),\left({\phi }_{1},{\theta }_{1}\right),\dots , \left({\phi }_{k},{\theta }_{k}\right)\right\}\) represents an enclosed and geographically defined area (longitude, latitude), \(P\) is the spatial distribution of people, \(A\) is the security assets deployed (e.g. controls, cameras or patrols) and \(D a\)nd \(O\) is the set of safe areas and obstacles inside the scenario that are defined by geographical coordinates. Threats being monitored in these areas are therefore defined as \({T}_{i}=\{L, C\}\), where \(L=\left(\phi , \theta \right)\) is the location and \(C\in \{Arson, Smoke, IED, Weapon\}\) is the category.
Pedestrian Movement Layer:
Topological definition of pedestrian transitable areas is replicated through the graph \({G}_{p}=\{N,E\}\), which is arranged by \(N=\{{n}_{0},{n}_{1},\dots ,{n}_{n}\}\) set of nodes and \(E=\{{e}_{0}, {e}_{1}, \dots , {e}_{m}\}\) set of edges. Each node \({n}_{i}=\{L,d, s\}\) is defined by its geographic location and occupant density as well as its current status \(s\in \{Passable, Impassable, Evacuate, Safe\}\). Likewise, each edge \({e}_{i}=\{d, {n}_{o},{n}_{d},f\}\) represents transitable zones and it is defined by people density, origin and destination nodes and available flow.
Traffic Layer:
Traffic network is represented through the graph \({G}_{t}=\{V,E\}\), where \(V=\left\{{v}_{0},{v}_{1},\dots ,{v}_{n}\right\}\) are the vehicular transit reference points associated with physical locations and \(E=\{{e}_{0},{e}_{1},\dots ,{e}_{m}\}\) represents the reachability associations similar to the pedestrian layer but within a traffic environment where the density and flow measurements represent vehicles instead of people. For the generation of traffic profiles, this layer considers the different usual zones \(Z\) of origin and destination of trips, which in turn are related by proximity to a node of the traffic network, generating a set of paths \(P\) between them and an origin-destination weighted matrix \(W=Z\times Z\) (Fig. 2).
Threat Assessment Layer
This layer assesses the threats and possible impacts/consequences of three type of attacks:
-
1.
Arson and Smoke Bomb: Fire Dynamics Simulator (McGrattan et al. 2017) is used for the most likely locations of this type of attacks by simulating several scenarios changing the actual combustion parameters, different wind and fire loads. The generated results providing artificial measurements \({M}_{f}({s}_{i})=\{{m}_{0},{m}_{1},\dots ,{m}_{k}\}\), (e.g. visibility, Fractional Effective Dose (FED)) are classified and stored in a structured way for further use.
-
2.
Improvise Explosive Device (IED): This approach is based on (Cuesta et al. 2019). The boundary box of each soft-target \({s}_{k}\) is calculated and subdivided into small regions shaping a fine grid of squared cells. For each cell \({c}_{ij}\) within the grid, the risk function is calculated as follows:
$$\begin{aligned} R\left( {s_k ,c_{ij} } \right) & = w_{dt} \cdot d_t \left( {c_{ij} ,E} \right) + w_{da} \cdot d_a \left( {c_{ij} ,A} \right) + w_{dr} \cdot d_r \left( {c_{ij} ,B} \right) \\ & \,\,\,+ \,w_p \cdot p\left( {c_{ij} , P} \right), \\ \end{aligned}$$where the functions studied have associated weights \(\{{w}_{dt}, {w}_{da},{w}_{dr},{w}_{p}\}\) that can be modified (e.g. to give more weight to one or another parameter) but, as a general rule, balance the risk function. The rest of the functions that are measured in the equation are:
-
\({d}_{t}\left({c}_{ij},E\right)\) → Inverse (1-p) normalized distance from cell \({c}_{ij}\) to the nearest exit (negative correlation).
-
\({d}_{a}\left({c}_{ij},A\right)\)→ Inverse normalized distance from cell \({c}_{ij}\) to the nearest asset.
-
\({d}_{r}\left({c}_{ij},B\right)\) → Normalized radial distance from cell \({c}_{ij}\) to the boundary box (positive correlation).
-
\(p({c}_{ij}, P)\) → Normalized population density inside cell \({c}_{ij}\).
-
After processing all the cells, a matrix \({M}_{r}({s}_{i})\) of risk values is provided which is associated with the threat level, resulting in a probability map with critical locations of IEDs for each soft-target.
-
3.
Mass Shooting Attack (MSA): The soft-target space \({s}_{i}\) is discretized through uniformly distributed reference points and mapped onto nodes of a reachability directed graph \(G=\{N,E\}\), \(N=\{{n}_{0},{n}_{1},\dots , {n}_{k}\}\) for pathing purposes. The optimal path (i.e. minimum distance) from each starting location \(P=\{{p}_{0},{p}_{1},\dots ,{p}_{m}\}\) is calculated, considering the location (static and/or dynamic) of the attacker(s) \({A}_{l}\), by means of Backtracking approach with associated cost function:
$$c_f \left( {n_i , n_j } \right) = \frac{{\frac{{d_{mean} \left( {n_j , E} \right)}}{{\max_n^{nghbs\left( {n_i } \right)} (d_{mean} \left( {n, E} \right)) }} + \frac{{d_{min} \left( {n_j , E} \right)}}{{{\text{max}}_n^{nghbs\left( {n_i } \right)} \left( {d_{min} \left( {n, E} \right)} \right)}} + \frac{{u\left( {n_j } \right)}}{{{\text{max}}_n^{nghbs\left( {n_i } \right)} \left( {u\left( n \right)} \right)}}}}{{\frac{{d_{mean} \left( {n_j , A_l } \right)}}{{{\text{max}}_n^{nghbs\left( {n_i } \right)} \left( {d_{mean} \left( {n_j , A_l } \right)} \right)}}}}$$where function \(nghbs\left({n}_{i}\right)\) represents the neighbours of a particular node, function \({d}_{mean/max}\left(n,S\right)\) is the mean/max distance from node \(n\) to a set \(S\) of locations and \(u\left(n\right)\) is the density of population in the surrounding of \(n\). In conclusion, this function represents three important factors: 1) the proximity of a node to an exit/safe area, 2) the spatial availability of that node, and 3) the risk associated with the location of the attacker(s). Following these paths, a microsimulation approach is used to represent the movement and behaviour of people involved considering interactions between agents and repulsion forces between terrorists, people, scenario boundaries and obstacles through a Social Force model (Helbing and Molnár 1995). A physical shooting dynamics approach is followed (Abreu et al. 2019) to represent persons hit by gunfire, where the probability of being hit is estimated and the number of casualties \({M}_{v}({s}_{i})\) are calculated through a stochastic approach.
Results generated by these methodologies can be summarised as a set of geographic locations linked to counter-terrorism security-related information enabling the lower layers to increase their level of intelligence to enable more accurate modelling results.
Pedestrian Movement Layer
This layer uses threat assessment layer inputs \(\{{M}_{f},{M}_{r}, {M}_{v}\}\) and the pedestrian movement layer the status \(s\) for each node \({n}_{i}\) in the associated graph \({G}_{p}\) to update nodes to be evacuated, safe nodes and affected nodes that are impassable. Also, the occupant densities of the different nodes and edges of the network are updated through one of the following approaches depending on the capabilities of the smart city: 1) historical-based estimates of the expected occupancy, 2) real-time monitoring of occupancy through cameras, Wi-Fi location devices, access controls or similar, and 3) random assumptions of occupancy following expected distributions. This graph is considered as an active graph and it is used to produce a preliminary calculation of shortest paths using Dijkstra's algorithm. Its subsequent optimization is carried out considering nodes availability and through a weighted Multiple Criteria Decision Analysis (MCDA) for the assessment of conflicting nodes through its score function:
where \(\{{w}_{f}, {w}_{c},{w}_{fn},{w}_{dt}\}\) are the associated weights with the MCDA and although they are generally assigned the same weight for each variable, they can be modified in each iteration of the optimisation to obtain the required results. Functions \(F\left(n\right)\) and \(C(n)\) represent the available flow for a particular node considering all the related edges and congestions per node. After this, a set of candidate graphs \({S}_{g}=\{{G}_{0},{G}_{1},\dots ,{G}_{k}\}\) solving these conflicts is generated following an iterative process and another score function is applied to choose the optimal graph considering the total estimation of evacuation time \({t}_{e}({G}_{i})\) for each graph and the sum of individual node congestions with associated weights.
Once the optimal graph has been found, it becomes the active graph again, which can be iteratively re-optimised when the model inputs change. This model provides evacuation routing, estimated egress times and mobility profiles, forecasting the number of people who will go to specific locations in a precise time period by determining and modelling the initial impact on the traffic network.
Traffic Layer
This layer provides a real time expected traffic evolution on different road sections according to date and time after a calibration of the network based on traffic historical data or data obtained through the traffic monitoring sensors deployed in the smart city. This calibration process starts from an uncalibrated network represented by the graph \({G}_{t}\) which solves for the shortest paths considering availability constraints of the road sections and updating the \(W\) origin-destination matrix via path-based (Jayakrishnan et al. 1994) and bush-bashed B algorithms (Dial 2006). Accordingly, following an iterative process for origin-destination matrix adjustment based on gradient approach (Spiess 1990) with some adjustments for large traffic models (Kolovský et al. 2018), the model optimises the set of paths \(P\) and the matrix \(W\) based on real traffic data, paying attention to discrepancies between model and reality.
2.2 System Architecture
All these methodologies have been integrated together in a comprehensive DSS that, following the architecture presented in Fig. 3, assists security decisionmakers in the planning and response phases by leveraging some of the resources and devices already deployed in the smart cities. Examples of resources and devices include cameras, monitoring Wi-Fi devices, access control sensors, etc. These devices could help to estimate the number of people in specific locations or for example traffic monitoring systems make real-time simulation of unusual traffic flow more reliable.
The architecture follows a producer-consumer approach with a centralized distributed data stream platform (Apache Kafka) for the exchange of information between layers. Each layer in turn is implemented as an independent module that has a Graphical User Interface (GUI) for configuration purposes and Application Programming Interface (API) that provides on-demand service to the rest of the layers, except for fire and smoke simulations that, due to the computational cost, must be pre-simulated and stored locally for further use in specific scenarios, if needed.
3 Case Study
After the development of the system, a comprehensive case study was performed based on data provided by Správa Informačnich Technologii Mĕsta Plznĕ, p.o. as partner of the S4AllCities project. The soft-target scenario was the Doosan Arena stadium in the city of Pilsen (Czech Republic). A detailed description of the stadium and its surrounding areas as well as the city of Pilsen itself was available, including information such as:
-
Doosan Arena 3D model obtained via Lidar and RGB scanning using DJI Zenmuse L1 and DJI Zenmuse P1 cameras.
-
Initial locations of a possible smoke bomb as well as its device-like specifications (Antari Z 3000 II fog machine).
-
One-year traffic data providing a dataset of 250 million observations
-
from 627 road built-in sensors, with a 90 s granularity in time, traffic model calibrated by the traffic data (Jedlicka et al. 2020).
-
2D map of the areas surrounding the stadium with expected attendance (11700 spectators + 3300 people), transit locations, security assets usually deployed, car parks and other minor details (Fig. 4).
The next step after the simulation, training and calibration of the models with the provided data, was the definition of four use cases to validate all the capabilities of the system listed in Table 1.
For each of these use cases, the DSS provided results, starting by retrieving the output of the smoke propagation FDS analysis (virtual smoke machine tuned on Antari Z 3000 II fog machine, North-West wind direction) followed by the simulation of threats and likely impact of attacks (Fig. 5). It is important to note that the information provided to the system operator includes the visualization of both the evolution of the different incidents and the data associated with the artificial scenario measurements (IED probability, FED, visibility and casualties). On the other hand, a simulation of pedestrian evacuation and traffic network unusual behaviour impact is also generated as shown in Fig. 5, where the operator is informed about the predicted evacuation times, routes, recognition of traffic/pedestrian congestion and the possibility of dynamically recalculating these results according to the risks deemed appropriate by, for example, cutting roads or blocking pedestrian evacuation nodes.
The simulation of our use cases showed that for the case study of the Doosan Arena stadium and the city of Pilsen the most likely dispersion of the smoke from the device would be initially south-east without affecting additional exits from the stadium (after about 5 min, smoke whirls start sticking to the outer South tribune, Fig. 5, Top-Left). In the case of explosive device threat levels and potential casualties, this would result in the blocking of the front exits of the stadium, as a two-shooter attack in this area would result in an estimated of 139 casualties (dead + wounded) considering two minutes intervention time, in addition to considering the potential locations of explosive devices, as shown in the lighter areas of the heat map in Fig. 5. As shown in Fig. 5, the pedestrian evacuation would be directed mainly to the nearest car parks by using the remaining exits available in the stadium. The effect of these pedestrian evacuation profiles would increase in approx. 700 vehicles per the first hour in the northern traffic section and 900 vehicles per the first hour in the southern section, leaving a high density of vehicles in both directions, as shown in Fig. 5.
4 Conclusions and Discussion
The emerging technologies implemented in smart cities as well as new tools and methodologies for computer simulation applied to threat analysis and citizen security are a breakthrough in the fight against terrorism. In this paper we present the methodological design based on three layers (threat, pedestrian and traffic layers) and implementation of a DSS that allows private operators, law enforcement agencies and local authorities to efficiently protect city soft-targets. Within this system, support is provided for both threat analysis and emergency management of pedestrian evacuation and its impact on the metropolitan traffic network. In addition, this paper presents a case study based on real data in the city of Pilsen where the correct functioning of the different layers that make up the system was evaluated and the benefits and characteristics of the system were presented in a more illustrative way, among which is the study of the analysis of the main terrorist threats, the complete management of an evacuation and the monitoring for decision-making of the state of the traffic network.
It must also be considered that this system has certain limitations that can be corrected in later developments. The first of these is that it does not cover all types of threats within the city. Actual reports suggest that future trends (EUROPOL 2021) in terrorism will evolve to simpler and less expensive (knife attacks) or combined attacks (cascading attacks or sabotage of critical infrastructures). Conversely, there would be an exploratory branch of the possible direct interaction of terrorist threats with the traffic network, being able to carry out developments in the field of anti-ramming measures in urban planning. From our point of view, all these limitations are not an obstacle but rather open up future branches of research and lead to the development of increasingly complete security and safety systems.
References
Abreu, O., Cuesta, A., Balboa, A., Alvear, D.: On the use of stochastic simulations to explore the impact of human parameters on mass public shooting attacks. Saf. Sci. 120, 941–949 (2019)
Anees, V., Kumar, G.: Direction estimation of crowd flow in surveillance videos. In: 2017 IEEE Region 10 Symposium (TENSYMP), pp. 1–5 (2017)
Araujo, A., Cacho, N., Thome, A., Medeiros, A., Borges, J.: A predictive policing application to support patrol planning in smart cities. In: 2017 International Smart Cities Conference (ISC2), pp. 1–6 (2017)
Balla, P.B., Jadhao, K.: IoT based facial recognition security system. In: 2018 International Conference on Smart City and Emerging Technology (ICSCET), pp. 1–4 (2018)
Bellini, P., Cenni, D., Nesi, P., Paoli, I.: Wi-Fi based city users’ behaviour analysis for smart city. J. Vis. Lang. Comput. 42, 31–45 (2017)
Bonatsos, A., Middleton, L., Melas, P., Sabeur, Z.: Crime open data aggregation and management for the design of safer spaces in urban environments. In: International Symposium on Environmental Software Systems, pp. 311–320 (2013)
Boukerche, A., Siddiqui, A., Mammeri, A.: Automated vehicle detection and classification: models, methods, and techniques. ACM Comput. Surv. (CSUR) 50(5), 1–39 (2017)
Brust, M.R., Danoy, G., Bouvry, P., Gashi, D., Pathak, H., Gonçalves, M.P.: Defending against intrusion of malicious UAVs with networked Uav defense swarms. In: 2017 IEEE 42nd Conference on Local Computer Networks Workshops (LCN Workshops), pp. 103–111 (2017)
Chackravarthy, S., Schmitt, S., Yang, L.: Intelligent crime anomaly detection in smart cities using deep learning. In: 2018 IEEE 4th International Conference on Collaboration and Internet Computing (CIC), p. 399–404 (2018)
Cuesta, A., Abreu, O., Balboa, A., Alvear, D.: A new approach to protect soft-targets from terrorist attacks. Saf. Sci. 120, 877–885 (2019)
Dbouk, M., Mcheick, H., Sbeity, I.: CityPro; an integrated city-protection collaborative platform. Procedia Comput. Sci. 37, 72–79 (2014)
Dial, R.B.: A path-based user-equilibrium traffic assignment algorithm that obviates path storage and enumeration. Transp. Res. Part B Methodol. 40(10), 917–936 (2006)
EUROPOL: European union terrorism situation and trend report (2021)
Fernández, J., et al.: An intelligent surveillance platform for large metropolitan areas with dense sensor deployment. Sensors 13(6), 7414–7442 (2013)
Global Terrorism Database™ (GTD): Obtenido de (2021). https://www.start.umd.edu/gtd/
Hartama, D., et al.: A research framework of disaster traffic management to Smart City. In: 2017 Second International Conference on Informatics and Computing (ICIC), pp. 1–5 (2017)
Helbing, D., Molnár, P.: Social force model for pedestrian dynamics. Phys. Rev. E 51(5), 4282 (1995)
Jayakrishnan, R., Tsai, W.T., Prashker, J.N., Rajadhyaksha, S.: A faster path-based algorithm for traffic assignment (1994)
Jedlicka, K., et al.: Traffic modelling for the smart city of Pilsen (2020)
Kolovský, F., Ježek, J., Kolingerová, I.: The origin-destination matrix estimation for large transportation models in an uncongested network. In: International Conference on Mathematical Applications, pp. 17–22 (2018)
Laufs, J., Borrion, H., Bradford, B.: Security and the smart city: a systematic review. Sustain. Cities Soc. 55, 102023 (2020)
Martin, R.H.: Soft targets are easy terror targets: increased frequency of attacks, practical preparation, and prevention. Forensic Res. Criminol. Int. J. 3(2), 1–7 (2016)
McGrattan, K., et al.: Fire Dynamics Simulator User’s Guide. National Institute of Standards and Technology (2017)
Noor, M., Nawawi, W., Ghazali, A.: Supporting decision making in situational crime prevention using fuzzy association rule. In: 2013 International Conference on Computer, Control, Informatics and Its Applications (IC3INA), pp. 225–229 (2013)
Spiess, H.: A gradient approach for the OD matrix adjustment problem. \({\text{a}} \in {\hat{\text{A}}}\), 1 (1990)
Truntsevsky, Y.V., Lukiny, I., Sumachev, A., Kopytova, A.: A smart city is a safe city: the current status of street crime and its victim prevention using a digital application. In: MATEC Web of Conferences, vol. 170, p. 01067 (2018)
Tuman, J.S.: Communicating Terror: The Rhetorical Dimensions of Terrorism. Sage Publications (2009)
Turban, E.: Decision Support and Expert Systems Management Support Systems. Prentice-Hall, Inc., Hoboken (1995)
Zhang, W., et al.: Agent-based modeling of a stadium evacuation in a smart city. In: 2018 Winter Simulation Conference (WSC), pp. 2803–2814 (2018)
Zhou, W., Saha, D., Rangarajan, S.: A system architecture to aggregate video surveillance data in Smart Cities. In: 2015 IEEE Global Communications Conference (GLOBECOM), pp. 1–7 (2015)
Zingoni, A., Diani, M., Corsini, G.: A flexible algorithm for detecting challenging moving objects in real-time within IR video sequences. Remote Sens. 9(11), 1128 (2017)
Acknowledgements
The project (S4AllCities) has received funding from the European Union’s H2020 research and innovation programme under grant agreement No. 883522.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
González-Villa, J. et al. (2022). Decision-Support System for Safety and Security Assessment and Management in Smart Cities. In: Mazzeo, P.L., Frontoni, E., Sclaroff, S., Distante, C. (eds) Image Analysis and Processing. ICIAP 2022 Workshops. ICIAP 2022. Lecture Notes in Computer Science, vol 13374. Springer, Cham. https://doi.org/10.1007/978-3-031-13324-4_3
Download citation
DOI: https://doi.org/10.1007/978-3-031-13324-4_3
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-13323-7
Online ISBN: 978-3-031-13324-4
eBook Packages: Computer ScienceComputer Science (R0)