Abstract
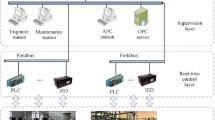
Recently, cybercrime attacking the national network has increased. National infrastructure such as water purification plants, power plants, and substations are operated by using programmable logic controllers (PLC). PLC controls through the Industrial Control Systems/Supervisory Control And Data Acquisition (ICS/SCADA), which receives operational commands and sends operational states by communication means such as Ethernet and Modbus. However, the environment of ICS/SCADA, called Industrial IoT, is vulnerable to security attacks unlike recently developed technologies such as IoT devices, systems, and networks. Therefore, this study proposes a new security system to strengthen industrial firewalls. We developed an interface, unauthorized access blocking algorithm, and real-time defense system for system access control. The performance of the proposed system was verified by external organizations. Five performance indicators were measured to validate the proposed system. All indexes were achieved to 100%. We hope that this study and results will help block and defend against cyberattacks.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Wu, H., Geng, Y., Liu, K., Liu, W.: Research on programmable logic controller security. In: IOP Conference Series: Materials Science and Engineering. IOP Publishing (2019)
Yılmaz, E.N., Gönen, S.: Attack detection/prevention system against cyber attack in industrial control systems. Comput. Secur. 77, 94–105 (2018)
CAP, R.L., CSSL, C.: Analytic of China cyberattack. Int. J. Multimedia Appl. 4(3), 37 (2012)
Ramana, M., Kurando, M.: Cyberattacks on Russia—the nation with the most nuclear weapons—pose a global threat. Bull. Atomic Scient. 75(1), 44–50 (2019)
Noguchi, M., Ueda, H.: An analysis of the actual status of recent cyberattacks on critical infrastructures. NEC Tech. J. Spec. Issue Cybersecur. 12(2), 19–24 (2019)
Kshetri, N., Voas, J.: Hacking power grids: a current problem. Computer 50(12), 91–95 (2017)
Hwang, J., Choi, K.-S.: North Korean cyber attacks and policy responses: an interdisciplinary theoretical framework. Int. J. Cybersecur. Intell. Cybercrime 4(2), 4–24 (2021)
Chun, H., Lee, H., Kim, D.: The integrated model of smartphone adoption: hedonic and utilitarian value perceptions of smartphones among Korean college students. Cyberpsychol. Behav. Soc. Netw. 15(9), 473–479 (2012)
Sadeeq, M.A., Zeebaree, S.: Energy management for internet of things via distributed systems. J. Appl. Sci. Technol. Trends 2(2), 59–71 (2021)
Li, D., Guo, H., Zhou, J., Zhou, L., Wong, J.W.: SCADAWall: a CPI-enabled firewall model for SCADA security. Comput. Secur. 80, 134–154 (2019)
Sundararajan, A., Chavan, A., Saleem, D., Sarwat, A.I.: A survey of protocol-level challenges and solutions for distributed energy resource cyber-physical security. Energies 11(9), 2360 (2018)
Maglaras, L.A., Jiang, J., Cruz, T.J.: Combining ensemble methods and social network metrics for improving accuracy of OCSVM on intrusion detection in SCADA systems. J. Inf. Secur. Appl. 30, 15–26 (2016)
El Mrabet, Z., Kaabouch, N., El Ghazi, H., El Ghazi, H.: Cyber-security in smart grid: survey and challenges. Comput. Electr. Eng. 67, 469–482 (2018)
Sun, C.-C., Hahn, A., Liu, C.-C.: Cyber security of a power grid: state-of-the-art. Int. J. Electr. Power Energy Syst. 99, 45–56 (2018)
Radoglou-Grammatikis, P., Sarigiannidis, P., Efstathopoulos, G., Karypidis, P.-A., Sarigiannidis, A.: Diderot: an intrusion detection and prevention system for dnp3-based scada systems. In: Proceedings of the 15th International Conference on Availability, Reliability and Security (2020)
Rosborough, C., Gordon, C., Waldron, B.: All about eve: comparing dnp3 secure authentication with standard security technologies for scada communications. In: 13th Australasian Information Security Conference (2019)
de Toledo, T.R., Torrisi, N.M.: Encrypted DNP3 traffic classification using supervised machine learning algorithms. Mach. Learn. Knowl. Extr. 1(1), 384–399 (2019)
Lu, Y., Ou, W.-B.: Exploitation of the distributed network protocol in ICS with improved DY model based on petri net. Int. J. Netw. Secur. 23(5), 58–768 (2021)
Marian, M., Cusman, A., Stîngă, F., Ionică, D., Popescu, D.: Experimenting with digital signatures over a dnp3 protocol in a multitenant cloud-based scada architecture. IEEE Access 8, 156484–156503 (2020)
Acknowledgments
This work is the result of the technology development of the SME technology development support project implemented by the Ministry of SMEs and Startups, Republic of Korea.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Park, W.Y., Kim, S.H., Vu, DS., Song, C.H., Jung, H.S., Jo, H. (2022). A Security System for National Network. In: Arai, K. (eds) Intelligent Computing. SAI 2022. Lecture Notes in Networks and Systems, vol 508. Springer, Cham. https://doi.org/10.1007/978-3-031-10467-1_48
Download citation
DOI: https://doi.org/10.1007/978-3-031-10467-1_48
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-10466-4
Online ISBN: 978-3-031-10467-1
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)