Abstract
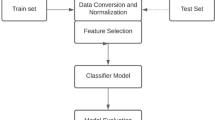
Security has been a concern in recent years, especially in the Internet of Things (IoT) system environment, where security and privacy are of great importance. Our lives have significantly transformed positively with the emergence of cutting-edge technologies like big data, edge and cloud computing, artificial intelligence (AI) with the help of the Internet, coupled with the generations of symmetric and asymmetric data distribution using highly valued real-time applications. Yet, these cut-edge technologies come with daily disastrous ever-increasing cyberattacks on sensitive data in the IoT-based environment. Hence, there is a continued need for groundbreaking strengths of AI-based models to develop and implement intrusion detection systems (IDSs) to arras and mitigate these ugly cyber-threats with IoT-based systems. Therefore, this chapter discusses the security issues within IoT-based environments and the application of AI models for security and privacy in IoT-based for a secure network. The chapter proposes a hybrid AI-model framework for intrusion detection in an IoT-based environment and a case study using CIC-IDS2017and UNSW-NB15 to test the proposmodel's performance. The model performed better with an accuracy of 99.45%, with a detection rate of 99.75%. The results from the proposed model show that the classifier performs far better when compared with existing work using the same datasets, thus prove more effective in the classification of intruders and attackers on IoT-based systems.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Awotunde JB, Ogundokun RO, Misra S (2021) Cloud and IoMT-based big data analytics system during COVID-19 pandemic. Internet Things 2021:181–201
Awotunde JB, Adeniyi AE, Ogundokun RO, Ajamu GJ, Adebayo PO (2021) MIoT-based big data analytics architecture, opportunities and challenges for enhanced telemedicine systems. In: Enhanced telemedicine and e-health: advanced IoT enabled soft computing framework, pp 199–220
Abiodun MK, Awotunde JB, Ogundokun RO, Adeniyi EA, Arowolo MO (2021) Security and information assurance for IoT-based big data. In: artificial intelligence for cyber security: methods, issues and possible horizons or opportunities. Springer, Cham, pp 189–211
Jaw E, Wang X (2021) Feature selection and ensemble-based intrusion detection system: an efficient and comprehensive approach. Symmetry 13(10):1764
Khan MA, Karim M, Kim Y (2019) A scalable and hybrid intrusion detection system based on the convolutional-LSTM network. Symmetry 11(4):583
Meryem A, Ouahidi BE (2020) Hybrid intrusion detection system using machine learning. Netw Secur 2020(5):8–19
Awotunde JB, Chakraborty C, Adeniyi AE (2021) Intrusion detection in industrial internet of things network-based on deep learning model with rule-based feature selection. Wirel Commun Mob Comput 2021:7154587
Xu C, Shen J, Du X, Zhang F (2018) An intrusion detection system using a deep neural network with gated recurrent units. IEEE Access 6:48697–48707
Sarker IH, Kayes ASM, Badsha S, Alqahtani H, Watters P, Ng A (2020) Cybersecurity data science: an overview from machine learning perspective. J Big data 7(1):1–29
Damaševičius R, Venčkauskas A, Toldinas J, Grigaliūnas Š (2021) Ensemble-based classification using neural networks and machine learning models for windows PE malware detection. Electronics 10(4):485
Dang QV (2019) Studying machine learning techniques for intrusion detection systems. In: International conference on future data and security engineering. Springer, Cham, pp 411–426
Lopez-Martin M, Sanchez-Esguevillas A, Arribas JI, Carro B (2021) Supervised contrastive learning over prototype-label embeddings for network intrusion detection. Inf Fusion
Muñoz A, Maña A, González J (2013) Dynamic security properties monitoring architecture for cloud computing. In: Security engineering for cloud computing: approaches and tools. IGI Global, pp 1–18
Kagara BN, Siraj MM (2020) A review on network intrusion detection system using machine learning. Int J Innov Comput 10(1)
Bhosale KS, Nenova M, Iliev G (2020) Intrusion detection in communication networks using different classifiers. In: Techno-societal 2018. Springer, Cham, pp 19–28
Liu H, Lang B (2019) Machine learning and deep learning methods for intrusion detection systems: a survey. Appl Sci 9(20):4396
Saleh AI, Talaat FM, Labib LM (2019) A hybrid intrusion detection system (HIDS) based on prioritized k-nearest neighbors and optimized SVM classifiers. Artif Intell Rev 51(3):403–443
Awotunde JB, Jimoh RG, Folorunso SO, Adeniyi EA, Abiodun KM, Banjo OO (2021) Privacy and security concerns in IoT-based healthcare systems. Internet Things 2021:105–134
Weber M, Boban M (2016) Security challenges of the internet of things. In: 2016 39th international convention on information and communication technology, electronics and microelectronics (MIPRO). IEEE, pp 638–643
Sfar AR, Natalizio E, Challal Y, Chtourou Z (2018) A roadmap for security challenges in the internet of things. Digit Commun Netw 4(2):118–137
Ali B, Awad AI (2018) Cyber and physical security vulnerability assessment for IoT-based smart homes. Sensors 18(3):817
Bajeh AO, Mojeed HA, Ameen AO, Abikoye OC, Salihu SA, Abdulraheem M et al (2021) Internet of robotic things: its domain, methodologies, and applications. Adv Sci Technol Innov 203–217
Granjal J, Monteiro E, Silva JS (2015) Security for the internet of things: a survey of existing protocols and open research issues. IEEE Commun Surv Tutor 17(3):1294–1312
Görmüş S, Aydın H, Ulutaş G (2018) Security for the internet of things: a survey of existing mechanisms, protocols and open research issues. J Fac Eng Archit Gazi Univ 33(4):1247–1272
Kumar SA, Vealey T, Srivastava H (2016) Security in internet of things: challenges, solutions and future directions. In: 2016 49th Hawaii international conference on system sciences (HICSS). IEEE, pp 5772–5781
Liu X, Zhao M, Li S, Zhang F, Trappe W (2017) A security framework for the internet of things in the future internet architecture. Fut Internet 9(3):27
Bhardwaj A, Mangat V, Vig R, Halder S, Conti M (2021) Distributed denial of service attacks in cloud: state-of-the-art of scientific and commercial solutions. Comput Sci Rev 39:100332
Bhati A, Bouras A, Qidwai UA, Belhi A (2020) Deep learning based identification of DDoS attacks in industrial application. In: 2020 fourth world conference on smart trends in systems, security and sustainability (WorldS4). IEEE, pp 190–196
Taha AEM, Rashwan AM, Hassanein HS (2020) Secure communications for resource-constrained IoT devices. Sensors 20(13):3637
Alaba FA, Othman M, Hashem IAT, Alotaibi F (2017) Internet of things security: a survey. J Netw Comput Appl 88:10–28
Thomasian NM, Adashi EY (2021) Cybersecurity in the internet of medical things. Health Policy Technol 100549
Alsubaei F, Abuhussein A, Shandilya V, Shiva S (2019) IoMT-SAF: internet of medical things security assessment framework. Internet Things 8:100123
Hyman WA (2018) Errors in the use of medical equipment. In: Human error in medicine. CRC Press, pp 327–347
Royce CS, Hayes MM, Schwartzstein RM (2019) Teaching critical thinking: a case for instruction in cognitive biases to reduce diagnostic errors and improve patient safety. Acad Med 94(2):187–194
National Research Council, C. O. R. P. O. R. A. T. E. (1997) Standards, conformity assessment, and trade into the 21st century. Standard View 5(3):99–102
Satyanaga A, Kim Y, Hamdany AH, Nistor MM, Sham AWL, Rahardjo H (2021) Preventive measures for rainfall-induced slope failures in Singapore. In: Climate and land use impacts on natural and artificial systems. Elsevier, pp 205–223
Hao F, Xiao Q, Chon K (2020) COVID-19 and China's hotel industry: impacts, a disaster management framework, and post-pandemic agenda. Int J Hosp Manag 90:102636
Chernyshev M, Zeadally S, Baig Z (2019) Healthcare data breaches: implications for digital forensic readiness. J Med Syst 43(1):1–12
Cappelli DM, Moore AP, Trzeciak RF (2012) The CERT guide to insider threats: how to prevent, detect, and respond to information technology crimes (Theft, Sabotage, Fraud). Addison-Wesley
Maasberg M, Zhang X, Ko M, Miller SR, Beebe NL (2020) An analysis of motive and observable behavioral indicators associated with insider cyber-sabotage and other attacks. IEEE Eng Manag Rev 48(2):151–165
Cotenescu V, Eftimie S (2017) Insider threat detection and mitigation techniques. Sci Bull “Mircea Cel Batran” Naval Acad 20(1):552
Glancy F, Biros DP, Liang N, Luse A (2020) Classification of malicious insiders and the association of the forms of attacks. J Crim Psychol
Yuan S, Wu X (2021) Deep learning for insider threat detection: review, challenges and opportunities. Comput Secur 102221
Nurse JR, Buckley O, Legg PA, Goldsmith M, Creese S, Wright GR, Whitty M (2014) Understanding insider threat: a framework for characterising attacks. In: 2014 IEEE security and privacy workshops. IEEE, pp 214–228
Sarkar KR (2010) Assessing insider threats to information security using technical, behavioural and organisational measures. Inf Secur Tech Rep 15(3):112–133
Nurse JR, Erola A, Agrafiotis I, Goldsmith M, Creese S (2015) Smart insiders: exploring the threat from insiders using the internet-of-things. In: 2015 international workshop on secure internet of things (SIoT). IEEE, pp 5–14
Altulyan M, Yao L, Kanhere SS, Wang X, Huang C (2020) A unified framework for data integrity protection in people-centric smart cities. Multimed Tools Appl 79(7):4989–5002
Abdelrahman AM, Rodrigues JJ, Mahmoud MM, Saleem K, Das AK, Korotaev V, Kozlov SA (2021) Software‐defined networking security for private data center networks and clouds: vulnerabilities, attacks, countermeasures, and solutions. Int J Commun Syst 34(4):e4706
Butt SA, Jamal T, Azad MA, Ali A, Safa NS (2019) A multivariant secure framework for smart mobile health application. Trans Emerg Telecommun Technol e3684
Ayo FE, Folorunso SO, Abayomi-Alli AA, Adekunle AO, Awotunde JB (2020) Network intrusion detection is based on deep learning model optimized with rule-based hybrid feature selection. Inf Secur J: Glob Perspect 1–17
Sivaraman V, Venkatakrishnan SB, Ruan K, Negi P, Yang L, Mittal R et al (2020) High throughput cryptocurrency routing in payment channel networks. In: 17th {USENIX} symposium on networked systems design and implementation ({NSDI} 20), pp 777–796
Zhang Q, Zhang W (2019) Accurate detection of selective forwarding attack in wireless sensor networks. Int J Distrib Sens Netw 15(1):1550147718824008
Liu A, Dong M, Ota K, Long J (2015) PHACK: an efficient scheme for selective forwarding attack detection in WSNs. Sensors 15(12):30942–30963
Rughoobur P, Nagowah, L. (2017, December). A lightweight replay attack detection framework for battery depended IoT devices designed for healthcare. In: 2017 International conference on Infocom technologies and unmanned systems (trends and future directions) (ICTUS). IEEE, pp 811–817
Liu X, Qian C, Hatcher WG, Xu H, Liao W, Yu W (2019) Secure internet of things (IoT)-based smart-world critical infrastructures: survey, case study and research opportunities. IEEE Access 7:79523–79544
Mohanta BK, Jena D, Satapathy U, Patnaik S (2020) Survey on IoT security: challenges and solution using machine learning, artificial intelligence and blockchain technology. Internet Things 11:100227
Mosteanu NR (2020) Artificial intelligence and cyber security—Face to face with cyber attack—A maltese case of risk management approach. Ecoforum J 9(2)
Singh S, Sharma PK, Yoon B, Shojafar M, Cho GH, Ra IH (2020) Convergence of blockchain and artificial intelligence in IoT network for the sustainable smart city. Sustain Cities Soc 63:102364
Ogundokun RO, Awotunde JB, Misra S, Abikoye OC, Folarin O (2021) Application of machine learning for ransomware detection in IoT devices. In: Studies in computational intelligence, vol 972, pp 393–420
Lee JH, Kim H (2017) Security and privacy challenges in the internet of things [security and privacy matters]. IEEE Consum Electron Mag 6(3):134–136
AbdulRaheem M, Balogun GB, Abiodun MK, Taofeek-Ibrahim FA, Tomori AR, Oladipo ID, Awotunde JB (2021, October) An enhanced lightweight speck system for cloud-based smart healthcare. Commun Comput Inf Sci 1455:363–376
Vorobeychik Y, Kantarcioglu M (2018) Adversarial machine learning. Synth Lect Artif Intell Mach Learn 12(3):1–169
Ghosh A, Chakraborty D, Law A (2018) Artificial intelligence in Internet of things. CAAI Trans Intell Technol 3(4):208–218
Wang S, Qiao Z (2019) Robust pervasive detection for adversarial samples of artificial intelligence in IoT environments. IEEE Access 7:88693–88704
Zolotukhin M, Hämäläinen T (2018) On artificial intelligent malware tolerant networking for IoT. In: 2018 IEEE conference on network function virtualization and software defined networks (NFV-SDN). IEEE, pp 1–6
Singh SK, Rathore S, Park JH (2020) Blockiotintelligence: a blockchain-enabled intelligent IoT architecture with artificial intelligence. Futur Gener Comput Syst 110:721–743
Linda O, Vollmer T, Manic M (2009) Neural network-based intrusion detection system for critical infrastructures. In: 2009 international joint conference on neural networks. IEEE, pp 1827–1834
Ogundokun RO, Awotunde JB, Sadiku P, Adeniyi EA, Abiodun M, Dauda OI (2021) An enhanced intrusion detection system using particle swarm optimization feature extraction technique. Procedia Comput Sci 193:504–512
Chen R, Liu CM, Chen C (2012) An artificial immune-based distributed intrusion detection model for the internet of things. In: Advanced materials research, vol 366. Trans Tech Publications Ltd., pp 165–168
Marsden T, Moustafa N, Sitnikova E, Creech G (2017) Probability risk identification based intrusion detection system for SCADA systems. In: International conference on mobile networks and management. Springer, Cham, pp 353–363
Kolias C, Kambourakis G, Stavrou A, Gritzalis S (2015) Intrusion detection in 802.11 networks: empirical evaluation of threats and a public dataset. IEEE Commun Surv Tutor 18(1):184–208
Koroniotis N, Moustafa N, Sitnikova E, Turnbull B (2019) Towards the development of realistic botnet dataset in the internet of things for network forensic analytics: bot-IoT dataset. Futur Gener Comput Syst 100:779–796
Hamza A, Gharakheili HH, Benson TA, Sivaraman V (2019) Detecting volumetric attacks on lot devices via SDN-based monitoring of mud activity. In: Proceedings of the 2019 ACM symposium on SDN research, pp 36–48
Almiani M, AbuGhazleh A, Al-Rahayfeh A, Atiewi S, Razaque A (2020) Deep recurrent neural network for IoT intrusion detection system. Simul Modell Pract Theory 101:102031
Eberhart R, Kennedy J (1995) A new optimizer using particle swarm theory. In: MHS'95. proceedings of the sixth international symposium on micro machine and human science. IEEE, pp 39–43
Hu F, Zhou M, Yan P, Li D, Lai W, Bian K, Dai R (2019) Identification of mine water inrush using laser-induced fluorescence spectroscopy combined with one-dimensional convolutional neural network. RSC Adv 9(14):7673–7679
Awotunde JB, Ogundokun RO, Jimoh RG, Misra S, Aro TO (2021) Machine learning algorithm for cryptocurrencies price prediction. Stud Comput Intell 2021(972):421–447
Sharafaldin I, Lashkari AH, Ghorbani AA (2018) Toward generating a new intrusion detection dataset and intrusion traffic characterization. ICISSp 1:108–116
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this chapter
Cite this chapter
Awotunde, J.B., Misra, S. (2022). Feature Extraction and Artificial Intelligence-Based Intrusion Detection Model for a Secure Internet of Things Networks. In: Misra, S., Arumugam, C. (eds) Illumination of Artificial Intelligence in Cybersecurity and Forensics. Lecture Notes on Data Engineering and Communications Technologies, vol 109. Springer, Cham. https://doi.org/10.1007/978-3-030-93453-8_2
Download citation
DOI: https://doi.org/10.1007/978-3-030-93453-8_2
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-93452-1
Online ISBN: 978-3-030-93453-8
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)