Abstract
Card-based protocols are used to perform cryptographic tasks such as secure multiparty computation using a deck of physical cards. While most of the existing protocols use a two-colored deck consisting of red cards and black cards, Niemi and Renvall in 1999 constructed protocols for securely computing two-input Boolean functions (such as secure logical AND and XOR computations) using a commonly available standard deck of playing cards. Since this initial investigation, two-input protocols with fewer cards and/or shuffles have been designed, and by combining them, one can perform a secure computation of any Boolean circuit. In this paper, we directly construct a simple card-based protocol for the three-input AND computation. Our three-input AND protocol requires fewer cards and shuffles compared to that required when applying any existing two-input AND protocol twice to perform the three-input AND computation. Our protocol is unique in the sense that it is card minimal if we use two cards to encode a single bit.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
Card-based protocols perform cryptographic tasks such as secure multiparty computation using a deck of physical cards. Most existing studies in this line of research use a two-colored deck consisting of indistinguishable red
 and black
and black
 cards, whose backs have the same pattern
cards, whose backs have the same pattern
 . The Boolean values are usually encoded as follows:
. The Boolean values are usually encoded as follows:

If two face-down cards represent a bit \(x\in \{0,1\}\) according to the above encoding rule, then we call them a commitment to x and write it as follows:

Previous research has proposed many card-based protocols that are capable of securely computing Boolean functions such as the logical AND function. As mentioned above, most prior studies have used a two-colored deck of cards (e.g., [1, 2, 4, 5, 7, 16, 24]); however, there are a few protocols that use a standard deck of playing cards, as introduced below.Footnote 1
1.1 Card-Based Protocols with a Standard Deck of Cards
In 1999, Niemi and Renvall [18] proposed card-based protocols for secure two-input computations (such as computations of the logical AND and XOR) using a commonly available standard deck of playing cards for the first time. Since then, several protocols using such a standard deck have been proposed [6, 9, 10].
A typical deck of playing cards consists of 52 distinct cards excluding jokers; hence, we assume the following deck of 52 numbered cards:

where all their backs are identical
 .
.
Niemi and Renvall [18] considered, based on two cards
 and
and
 , an encoding scheme such that
, an encoding scheme such that

That is, two cards can be represented as 0 if the left number is smaller than the right one; otherwise, they are represented as 1. In this way, similar to the two-colored case, we can consider a commitment to a bit \(x\in \{0,1\}\) with two numbered cards
 and
and
 , denoted by
, denoted by

Here, the set \(\{i,j\}\) is called a base of the commitment. We sometimes write

without the description of a base if it is clear from context or there are multiple possibilities for the base. Note that, swapping the two face-down cards of a given commitment to \(x\in \{0,1\}\) converts it into a commitment to the negation \(\bar{x}\) while keeping the value of x secret; thus, a secure NOT computation is easy.
Based on this encoding, Niemi and Renvall [18] designed card-based protocols. They were followed by a couple of research groups [6, 10], whose advancements will be detailed in the next subsection.
1.2 Existing Protocols
Table 1 presents the existing protocols for the secure computation of the two-input AND function with a standard deck of cards. A protocol that terminates in a finite number of steps is said to be finite, while a protocol with a runtime that is finite in expectation is said to be Las Vegas; the fourth column of Table 1 indicates this.
Niemi and Renvall [18] proposed a Las Vegas two-input AND protocol using five cards; four cards are used to represent input commitments and the remaining card is an auxiliary one.Footnote 2 In other words, given two commitments to bits \(a,b\in \{0,1\}\) along with one additional card, their protocol produces a commitment to \(a\wedge b\) without leaking (revealing) any information about a and b:

In the (original) Niemi–Renvall protocol [18], the base of the output commitment is always \(\{1,2\}\) and the expected number of required shuffles is 9.5; however, Koch, Schrempp, and Kirsten [6] demonstrated that the expected number of shuffles can be reduced to 7.5 if we allow the base of the output commitment to be either \(\{1,4\}\), \(\{1,5\}\), or \(\{4,5\}\). In this paper, we refer this modified version as to the Niemi–Renvall protocol. As will be seen in Sect. 2.4, this protocol uses only a simple shuffle called a random cut (which is described in Sect. 2.2).
Later, Mizuki [10] proposed a finite two-input AND protocol with eight cards.Footnote 3 This protocol uses only a shuffle action called a random bisection cut (which is described in Sect. 2.3), and the number of required shuffles is four.
In 2021, Koch, Schrempp, and Kirsten [6] proposed a Las Vegas two-input AND protocol with four cards. This protocol uses only a random cut, and its expected number of shuffles is six.
1.3 Contribution
Let us consider how to securely compute the three-input AND function:

Computation of the three-input AND function can be performed by repeatedly applying one of the three existing protocols [6, 10, 18] twice: First, one must obtain a commitment to \(a\wedge b\) by applying a two-input protocol, and then apply the protocol to the commitments to \(a\wedge b\) and c. To perform this, the numbers of required cards and shuffles by Mizuki’s protocol [10] or Koch et al.’s protocol [6] are listed in Table 2.
In this study, we solicit a more efficient computation of the three-input AND. The main contribution of this paper is the novelty of our protocol that directly performs a secure three-input AND computation in a single application. Our protocol is partly based on Niemi and Renvall’s two-input AND protocol [18]. Our protocol uses only six cards, which are necessary for three input commitments; therefore, it uses the same number of cards as two runs of Koch et al.’s protocol [6]. The expected number of shuffles required for our protocol is 8.5, which is 3.5 fewer than the previous best six-card computation (see Table 2).
Overall, our proposed three-input AND protocol is “card-minimal” in the sense that only six cards are necessary under the encoding rule (1). Additionally, our protocol is simple because it uses only random cuts and random bisection cuts as shuffles.
1.4 Outline
This paper is organized as follows: Sect. 2 describes basic terminology in card-based cryptography and introduces the Niemi–Renvall protocol [18]. In Sect. 3, we describe our three-input AND protocol. We conclude this paper in Sect. 4.
2 Preliminaries
In this section, we introduce the actions involved in card-based protocols as well as practical shuffles, specifically the random cut and the random bisection cut, which will be used in our proposed protocol. Additionally, we explain the two-input AND protocol constructed by Niemi and Renvall [18].
2.1 Actions
In card-based protocols, as they have been formalized in [7, 13, 15], there are the following three main actions to be applied to a sequence of n cards.
-
Rearrangement. Apply some permutation \(\pi \in S_n\) to a sequence of n cards, where \(S_n\) denotes the symmetric group of degree n. We write this action as \((\mathsf {perm},{\pi })\):

-
Turn. Turn over the t-th card (from the left) for \(t\in \{1,\ldots ,n\}\) in a sequence to check the number of the card. We write this action as \((\mathsf {turn},{\{t\}})\):

In this example, the numbered card displaying a 1 was revealed.
-
Shuffle. Apply a permutation \(\pi \in \varPi \) chosen uniformly randomly from a permutation set \(\varPi \subseteq S_n\). We write this action as \((\mathsf {shuf},{\varPi })\):

Note that it is not possible for an observer to know which permutation in \(\varPi \) was applied.
2.2 Random Cut
A random cut is a shuffling action (denoted by \(\langle \cdot \rangle \)) that shifts a sequence of cards cyclically and randomly. If a random cut is applied to a sequence of n cards, then the resulting sequence becomes one of the following n sequences, each of which occurs with a probability of 1/n:

This random cut can be written, using a cyclic permutation \(\sigma = (1\,2\,3\,\cdots \,n)\), as
where \(\mathsf {id}\) denotes the identity permutation. Hereinafter, we use \(\mathsf {RC}_{1,2,\ldots ,n}\) to represent \(\{\mathsf {id}, \sigma , \sigma ^2\,,\ldots ,\sigma ^{n-1}\}\).
A random cut can be easily performed by human hands, and a secure implementation called the Hindu cut is well known [31, 32].
2.3 Random Bisection Cut
A random bisection cut is a shuffling action invented by Mizuki and Sone [16] in 2009. This shuffle (denoted by \(\left[ \, \cdot \, | \, \cdot \, \right] \)) bisects a sequence of 2n cards and randomly swaps the two halves; the resulting sequence becomes one of the following two sequences:

That is, the resulting sequence either remains the same as the original one or becomes a sequence where the two halves are swapped with a probability of 1/2. This random bisection cut can be written as follows:
Secure implementations using familiar tools were shown in [31, 32]. The random bisection cut has brought many efficient protocols (e.g., [11, 12, 14, 19,20,21]).
2.4 The Niemi–Renvall Protocol
Given two commitments to \(a,b\in \{0,1\}\) along with an additional card, the Niemi–Renvall protocol [18] outputs a commitment to \(a\wedge b\). The procedure is as follows.
-
1.
Place the two input commitments and an additional card
 and turn it over:
and turn it over: 
-
2.
Rearrange the third and fourth cards:
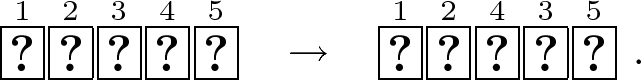
Now, let us consider the order of
 ,
,
 , and
, and
 in the rearranged sequence; the order is
in the rearranged sequence; the order is
 (apart from cyclic rotation) if and only if \((a,b)=(1,1)\), i.e., \(a\wedge b=1\) (whereas the order is
(apart from cyclic rotation) if and only if \((a,b)=(1,1)\), i.e., \(a\wedge b=1\) (whereas the order is
 if and only if \(a\wedge b =0\)). Therefore, we try to remove
if and only if \(a\wedge b =0\)). Therefore, we try to remove
 and
and
 in Steps 3 and 4.
in Steps 3 and 4. -
3.
Apply a random cut to the sequence of all cards:

-
4.
Turn over the first card; if it is
 or
or
 , then remove it. Otherwise, turn it over. If there is still a
, then remove it. Otherwise, turn it over. If there is still a
 or
or
 in the sequence, then return to Step 3.
in the sequence, then return to Step 3. -
5.
The resulting sequence after removing
 and
and
 becomes one as presented in Table 3. Apply a random cut to the sequence and then reveal the first card to obtain the output commitment. (This step was developed by Koch et al. [6].)
becomes one as presented in Table 3. Apply a random cut to the sequence and then reveal the first card to obtain the output commitment. (This step was developed by Koch et al. [6].) 
If the first card is
 , then we obtain a commitment to the negation of \(a\wedge b\). In this case, we apply the NOT computation to obtain a commitment to \(a \wedge b\).
, then we obtain a commitment to the negation of \(a\wedge b\). In this case, we apply the NOT computation to obtain a commitment to \(a \wedge b\).
 and
and

Correctness of this protocol is clear from the above description. Regarding security, since a random cut is applied to the sequence in Step 3, the revealed card in Step 4 is chosen randomly from the sequence. Therefore, no information about the input is leaked. For example, if the number of cards in Step 3 is five, the revealed card in Step 4 should be one in
 with an equal probability regardless of the input values. In the same manner, no information about the input is leaked when the first card is revealed in Step 5. To summarize, this protocol is correct and secure.
with an equal probability regardless of the input values. In the same manner, no information about the input is leaked when the first card is revealed in Step 5. To summarize, this protocol is correct and secure.
3 Our Three-Input AND Protocol
In this section, we present a three-input AND protocol that requires no additional card, i.e., is card-minimal and uses fewer shuffles as compared to the applications of previous protocols:

We begin by describing the idea behind our proposed protocol.
3.1 Idea
Observe the following simple fact about \(a\wedge b\wedge c\):
In other words, to construct a three-input AND protocol, it suffices to simulate a two-input AND protocol if \(c=1\) and to always output 0 if \(c=0\). For this, we borrow the idea behind the Niemi–Renvall protocol [18] introduced in Sect. 2.4.
Remember that their protocol swaps the third and fourth cards in Step 2; this action reverses the order of
 and
and
 if and only if \((a,b)=(1,1)\), i.e., the output is 1. That is, if we skip this step and perform the remaining steps, then the output should be always 0. From this observation, it suffices to swap the third and fourth cards if and only if \(c=1\) and then perform the remaining steps of the protocol. Therefore, in the next subsection, we will describe how to swap two cards according to the value of c (without knowing it).
if and only if \((a,b)=(1,1)\), i.e., the output is 1. That is, if we skip this step and perform the remaining steps, then the output should be always 0. From this observation, it suffices to swap the third and fourth cards if and only if \(c=1\) and then perform the remaining steps of the protocol. Therefore, in the next subsection, we will describe how to swap two cards according to the value of c (without knowing it).
3.2 Swapping by Value of Commitment
For a sequence of two cards along with a commitment to \(c\in \{0,1\}\) whose base is \(\{i,j\}\), we want to swap the cards if \(c=1\) and we want to keep them unchanged if \(c=0\), without leaking the value of c:

We call this the swap operation by the commitment to c. The swap operation proceeds as follows (whose procedure is similar to the Mizuki XOR protocol [10]).
-
1.
Assume a target sequence of two cards and a commitment to c (with \(i<j\)):

-
2.
Rearrange the second and third cards:
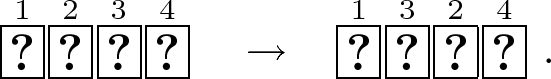
-
3.
Apply a random bisection cut to the sequence of all cards:

-
4.
Rearrange the second and third cards:

Observe that, depending on the value of c, the current sequence satisfies the followings:


-
5.
Turn over the third and fourth cards;
 or
or
 should appear with a probability of 1/2.
should appear with a probability of 1/2.-
(a)
If
 appear, then output the first and second cards.
appear, then output the first and second cards. -
(b)
If
 appear, then swap the first and second cards and then output them.
appear, then swap the first and second cards and then output them.
-
(a)
3.3 Description of Our Protocol
We now present our three-input AND protocol.
-
1.
Assume three input commitments to \(a,b,c\in \{0,1\}\):

-
2.
Apply the swap operation by the commitment to c shown in Sect. 3.2 to the second and third cards, as follows.
-
(a)
Rearrange the sequence:

-
(b)
Apply a random bisection cut to the last four cards:

-
(c)
Apply the inverse rearrangement of Step 2(a):

-
(d)
Turn over the fifth and sixth cards: If
 appear, then do nothing. If
appear, then do nothing. If
 appear, then swap the second and third cards.
appear, then swap the second and third cards.
-
(a)
-
3.
Rearrange the sequence so that the first card becomes
 appeared in the previous step and then turn it over. Subsequently, apply Steps 3, 4, and 5 of the Niemi–Renvall protocol [18] to the first five cards.
appeared in the previous step and then turn it over. Subsequently, apply Steps 3, 4, and 5 of the Niemi–Renvall protocol [18] to the first five cards.
3.4 Correctness and Security
Here, we prove the correctness and security of our three-input AND protocol. Observe that, in the sequence after Step 2 as listed in Table 4, the order of
 is
is
 if and only if \(a\wedge b\wedge c=1\) (whereas it is
if and only if \(a\wedge b\wedge c=1\) (whereas it is
 if and only if \(a\wedge b\wedge c=0\)). From this, it suffices to remove
if and only if \(a\wedge b\wedge c=0\)). From this, it suffices to remove
 and
and
 in the same manner as the Niemi–Renvall protocol [18]. Therefore, our protocol can always output a commitment to \(a\wedge b\wedge c\) by applying Steps 3, 4, and 5 of the Niemi–Renvall protocol [18].
in the same manner as the Niemi–Renvall protocol [18]. Therefore, our protocol can always output a commitment to \(a\wedge b\wedge c\) by applying Steps 3, 4, and 5 of the Niemi–Renvall protocol [18].
More formally, we prove this by using the KWH-tree [7] as in Figs. 1 and 2. The KWH-tree is a tree-like diagram that shows the transitions of possible sequences of cards along with their respective polynomials in a box, where actions to be applied to the sequence are appended to an edge. In the figure, the probability of \((a,b,c)=(x,y,z)\) is denoted by \(X_{xyz}\). A polynomial annotating a sequence in a box such as \(1/2X_{000}\) represents the conditional probability that the current sequence is the one next to the polynomial, given what can be observed so far on the table.
If the sum of all the polynomials in each box is equal to
then it is guaranteed that no information about the input is leaked. The KWH-tree of our protocol for Steps 1 and 2 is shown in Fig. 1. The KWH-tree for Step 3 is shown in Fig. 2. From the figures, it can be easily confirmed that the aforementioned condition is satisfied in each box, i.e., our protocol is secure.
4 Conclusion
In this study, we designed a simple three-input AND protocol using playing cards by only using six cards; in other words, we do not need any additional cards (aside from three input commitments). To the best of our knowledge, this is the first type of protocol that can be used for directly computing a three-input Boolean function with a standard deck of cards.
A natural open problem that presents itself from our research is the construction of efficient AND protocols for more than three inputs. It would also be interesting to investigate whether a finite AND protocol can be constructed using only random cuts even for two inputs. Making use of a standard deck in the “private permutation” setting (e.g., [8, 17, 22, 33]) would be another interesting topic. In addition, it would be worthwhile to construct zero-knowledge proof protocols working only on a standard deck for pencil puzzles, cf. [3, 23, 25, 26].
Notes
References
Abe, Y., Hayashi, Y., Mizuki, T., Sone, H.: Five-card AND computations in committed format using only uniform cyclic shuffles. New Gener. Comput. 39(1), 97–114 (2021). https://doi.org/10.1007/s00354-020-00110-2
Boer, B.: More efficient match-making and satisfiability the five card trick. In: Quisquater, J.-J., Vandewalle, J. (eds.) EUROCRYPT 1989. LNCS, vol. 434, pp. 208–217. Springer, Heidelberg (1990). https://doi.org/10.1007/3-540-46885-4_23
Bultel, X., Dreier, J., Dumas, J.G., Lafourcade, P.: Physical zero-knowledge proofs for Akari, Takuzu, Kakuro and KenKen. In: Demaine, E.D., Grandoni, F. (eds.) 8th International Conference on Fun with Algorithms (FUN 2016). Leibniz International Proceedings in Informatics (LIPIcs), vol. 49, pp. 8:1–8:20. Schloss Dagstuhl-Leibniz-Zentrum fuer Informatik, Dagstuhl, Germany (2016). https://doi.org/10.4230/LIPIcs.FUN.2016.8
Crépeau, C., Kilian, J.: Discreet solitary games. In: Stinson, D.R. (ed.) CRYPTO 1993. LNCS, vol. 773, pp. 319–330. Springer, Heidelberg (1994). https://doi.org/10.1007/3-540-48329-2_27
Kastner, J., et al.: The minimum number of cards in practical card-based protocols. In: Takagi, T., Peyrin, T. (eds.) ASIACRYPT 2017. LNCS, vol. 10626, pp. 126–155. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-70700-6_5
Koch, A., Schrempp, M., Kirsten, M.: Card-based cryptography meets formal verification. New Gener. Comput. 39(1), 115–158 (2021). https://doi.org/10.1007/s00354-020-00120-0
Koch, A., Walzer, S., Härtel, K.: Card-based cryptographic protocols using a minimal number of cards. In: Iwata, T., Cheon, J.H. (eds.) ASIACRYPT 2015. LNCS, vol. 9452, pp. 783–807. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-48797-6_32
Manabe, Y., Ono, H.: Secure card-based cryptographic protocols using private operations against malicious players. In: Maimut, D., Oprina, A.-G., Sauveron, D. (eds.) SecITC 2020. LNCS, vol. 12596, pp. 55–70. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-69255-1_5
Miyahara, D., Hayashi, Y., Mizuki, T., Sone, H.: Practical card-based implementations of Yao’s millionaire protocol. Theor. Comput. Sci. 803, 207–221 (2020). https://doi.org/10.1016/j.tcs.2019.11.005
Mizuki, T.: Efficient and secure multiparty computations using a standard deck of playing cards. In: Foresti, S., Persiano, G. (eds.) CANS 2016. LNCS, vol. 10052, pp. 484–499. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-48965-0_29
Mizuki, T., Asiedu, I.K., Sone, H.: Voting with a logarithmic number of cards. In: Mauri, G., Dennunzio, A., Manzoni, L., Porreca, A.E. (eds.) UCNC 2013. LNCS, vol. 7956, pp. 162–173. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-39074-6_16
Mizuki, T., Komano, Y.: Analysis of information leakage due to operative errors in card-based protocols. In: Iliopoulos, C., Leong, H.W., Sung, W.-K. (eds.) IWOCA 2018. LNCS, vol. 10979, pp. 250–262. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-94667-2_21
Mizuki, T., Shizuya, H.: A formalization of card-based cryptographic protocols via abstract machine. Int. J. Inf. Secur. 13(1), 15–23 (2014). https://doi.org/10.1007/s10207-013-0219-4
Mizuki, T., Shizuya, H.: Practical card-based cryptography. In: Ferro, A., Luccio, F., Widmayer, P. (eds.) Fun with Algorithms. LNCS, vol. 8496, pp. 313–324. Springer, Cham (2014). https://doi.org/10.1007/978-3-319-07890-8_27
Mizuki, T., Shizuya, H.: Computational model of card-based cryptographic protocols and its applications. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 100(1), 3–11 (2017). https://doi.org/10.1587/transfun.E100.A.3
Mizuki, T., Sone, H.: Six-card secure AND and four-card secure XOR. In: Deng, X., Hopcroft, J.E., Xue, J. (eds.) Frontiers in Algorithmics. LNCS, vol. 5598, pp. 358–369. Springer, Berlin, Heidelberg (2009). https://doi.org/10.1007/978-3-642-02270-8_36
Nakai, T., Misawa, Y., Tokushige, Y., Iwamoto, M., Ohta, K.: How to solve millionaires’ problem with two kinds of cards. New Gener. Comput. 39(1), 73–96 (2021). https://doi.org/10.1007/s00354-020-00118-8
Niemi, V., Renvall, A.: Solitaire zero-knowledge. Fundam. Inf. 38(1,2), 181–188 (1999). https://doi.org/10.3233/FI-1999-381214
Nishida, T., Hayashi, Y., Mizuki, T., Sone, H.: Card-based protocols for any Boolean function. In: Jain, R., Jain, S., Stephan, F. (eds.) TAMC 2015. LNCS, vol. 9076, pp. 110–121. Springer, Cham (2015). https://doi.org/10.1007/978-3-319-17142-5_11
Nishida, T., Hayashi, Y., Mizuki, T., Sone, H.: Securely computing three-input functions with eight cards. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 98(6), 1145–1152 (2015). https://doi.org/10.1587/transfun.E98.A.1145
Nishida, T., Mizuki, T., Sone, H.: Securely computing the three-input majority function with eight cards. In: Dediu, A.-H., Martín-Vide, C., Truthe, B., Vega-Rodríguez, M.A. (eds.) TPNC 2013. LNCS, vol. 8273, pp. 193–204. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-45008-2_16
Ono, H., Manabe, Y.: Card-based cryptographic logical computations using private operations. New Gener. Comput. 39(1), 19–40 (2020). https://doi.org/10.1007/s00354-020-00113-z
Robert, L., Miyahara, D., Lafourcade, P., Mizuki, T.: Physical zero-knowledge proof for Suguru puzzle. In: Devismes, S., Mittal, N. (eds.) SSS 2020. LNCS, vol. 12514, pp. 235–247. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-64348-5_19
Ruangwises, S., Itoh, T.: AND protocols using only uniform shuffles. In: van Bevern, R., Kucherov, G. (eds.) CSR 2019. LNCS, vol. 11532, pp. 349–358. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-19955-5_30
Ruangwises, S., Itoh, T.: Physical zero-knowledge proof for numberlink puzzle and k vertex-disjoint paths problem. New Gener. Comput. 39(1), 3–17 (2020). https://doi.org/10.1007/s00354-020-00114-y
Ruangwises, S., Itoh, T.: Physical zero-knowledge proof for ripple effect. In: Uehara, R., Hong, S.-H., Nandy, S.C. (eds.) WALCOM 2021. LNCS, vol. 12635, pp. 296–307. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-68211-8_24
Shinagawa, K.: Card-based cryptography with dihedral symmetry. New Gener. Comput. 39(1), 41–71 (2021). https://doi.org/10.1007/s00354-020-00117-9
Shinagawa, K., Mizuki, T.: Card-based protocols using triangle cards. In: Ito, H., Leonardi, S., Pagli, L., Prencipe, G. (eds.) 9th International Conference on Fun with Algorithms (FUN 2018). Leibniz International Proceedings in Informatics (LIPIcs), vol. 100, pp. 31:1–31:13. Schloss Dagstuhl-Leibniz-Zentrum fuer Informatik, Dagstuhl, Germany (2018). https://doi.org/10.4230/LIPIcs.FUN.2018.31
Shinagawa, K., et al.: Secure computation protocols using polarizing cards. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 99(6), 1122–1131 (2016)
Shinagawa, K., et al.: Card-based protocols using regular polygon cards. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 100(9), 1900–1909 (2017)
Ueda, I., Miyahara, D., Nishimura, A., Hayashi, Y., Mizuki, T., Sone, H.: Secure implementations of a random bisection cut. Int. J. Inf. Secur. 19, 445–452 (2020). https://doi.org/10.1007/s10207-019-00463-w
Ueda, I., Nishimura, A., Hayashi, Y., Mizuki, T., Sone, H.: How to implement a random bisection cut. In: Martín-Vide, C., Mizuki, T., Vega-Rodríguez, M.A. (eds.) TPNC 2016. LNCS, vol. 10071, pp. 58–69. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-49001-4_5
Yasunaga, K.: Practical card-based protocol for three-input majority. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 103(11), 1296–1298 (2020). https://doi.org/10.1587/transfun.2020EAL2025
Acknowledgements
We thank the anonymous referees, whose comments have helped us to improve the presentation of the paper. This work was supported in part by JSPS KAKENHI Grant Number JP19J21153.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 Springer Nature Switzerland AG
About this paper
Cite this paper
Koyama, H., Miyahara, D., Mizuki, T., Sone, H. (2021). A Secure Three-Input AND Protocol with a Standard Deck of Minimal Cards. In: Santhanam, R., Musatov, D. (eds) Computer Science – Theory and Applications. CSR 2021. Lecture Notes in Computer Science(), vol 12730. Springer, Cham. https://doi.org/10.1007/978-3-030-79416-3_14
Download citation
DOI: https://doi.org/10.1007/978-3-030-79416-3_14
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-79415-6
Online ISBN: 978-3-030-79416-3
eBook Packages: Computer ScienceComputer Science (R0)








 and turn it over:
and turn it over: 

 ,
,
 , and
, and
 in the rearranged sequence; the order is
in the rearranged sequence; the order is
 (apart from cyclic rotation) if and only if
(apart from cyclic rotation) if and only if  if and only if
if and only if  and
and
 in Steps 3 and 4.
in Steps 3 and 4.
 or
or
 , then remove it. Otherwise, turn it over. If there is still a
, then remove it. Otherwise, turn it over. If there is still a
 or
or
 in the sequence, then return to Step 3.
in the sequence, then return to Step 3. and
and
 becomes one as presented in Table
becomes one as presented in Table 
 , then we obtain a commitment to the negation of
, then we obtain a commitment to the negation of 





 or
or
 should appear with a probability of 1/2.
should appear with a probability of 1/2. appear, then output the first and second cards.
appear, then output the first and second cards. appear, then swap the first and second cards and then output them.
appear, then swap the first and second cards and then output them.



 appear, then do nothing. If
appear, then do nothing. If
 appear, then swap the second and third cards.
appear, then swap the second and third cards. appeared in the previous step and then turn it over. Subsequently, apply Steps 3, 4, and 5 of the Niemi–Renvall protocol [
appeared in the previous step and then turn it over. Subsequently, apply Steps 3, 4, and 5 of the Niemi–Renvall protocol [
