Abstract
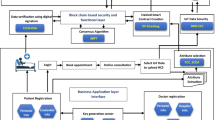
Most of the studies related to privacy-preserving linear regression training with the Internet of Medical Things (IoMT) data from various entities do not satisfy all the privacy issues of the data owner. This article proposes a secure design in order to protect privacy issues of IoMT data at the time of training a linear regression model. Blockchain is employed with a partially homomorphic cryptosystem known as Paillier to protect all participant’s data privacy. To eliminate the territory on a third-party, the proposed study unites secure building blocks in secure linear regression. Firstly, a guarded data-sharing platform is developed among various data providers, where encrypted IoMT data is registered on a shared ledger. Secondly, secure polynomial operation (SPO), and secure comparison (SC) are outlined using the homomorphic property of Paillier. Secure linear regression does not need any trusted third-party. It requires only three interplays in each iteration. Severe security inquiry proves that secure linear regression preserves sensitive data privacy for each data provider and analyst. The secure linear regression achieved 0.78, 0.066, and 0.196 adjusted \(R^{2}\) on BCWD, HDD, and DD datasets respectively. The performance of secure linear regression is nearly similar to the general linear regression.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Joyia, G.J., et al.: Internet of Medical Things (IOMT): applications, benefits and future challenges in healthcare domain. J. Commun. 12(4), 240–247 (2017)
Abadi, M., Chu, A., Goodfellow, I., McMahan, H.B., Mironov, I., Talwar, K., Zhang, L.: Deep learning with differential privacy. In: Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, pp. 308–318. ACM, New York (2016)
Bost, R., Popa, R.A., Tu, S., Goldwasser, S.: Machine learning classification over encrypted data. In: Proceedings of Network and Distributed System Security Symposium, San Diego, California, 23–26 February 2014 (2014)
Hasan, A.S.M.T., Qu, Q., Li, C., Chen, L., Jiang, Q.: An effective privacy architecture to preserve user trajectories in reward-based LBS applications. ISPRS Int. J. Geo-Inf. 7, 53 (2018)
Hasan, A.S.M.T., Jiang, Q., Chen, H., Wang, S.: A new approach to privacy-preserving multiple independent data publishing. Appl. Sci. 8, 783 (2018)
Hasan, A.S.M.T., Jiang, Q., Li, C.: An effective grouping method for privacy-preserving bike-sharing data publishing. Future Internet 9, 65 (2017)
Hasan, A.S.M.T., Jiang, Q., Luo, J., Li, C., Chen, L.: An effective value swapping method for privacy-preserving data publishing. Secur. Commun. Netw. 9, 3219–3228 (2016). https://doi.org/10.1002/sec.1527
Shen, M., Tang, X., Zhu, L., Du, X., Guizani, M.: Privacy-preserving support vector machine training over blockchain-based encrypted IoT data in smart cities. IEEE Internet Things J. 6, 7702–7712 (2019). https://doi.org/10.1109/JIOT.2019.2901840
Haque, R.U., Hasan, A.S.M.T., Jiang, Q., Qu, Q.: Privacy-preserving K-nearest neighbors training over blockchain-based encrypted health data. Electronics 9, 2096 (2020). https://doi.org/10.3390/electronics9122096
Senavirathne, N., Torra, V.: Approximating robust linear regression with an integral privacy guarantee. In: 2018 16th Annual Conference on Privacy, Security and Trust (PST), Belfast, pp. 1–10 (2018). https://doi.org/10.1109/PST.2018.8514161
Qiu, G., Gui, X., Zhao, Y.: Privacy-preserving linear regression on distributed data by homomorphic encryption and data masking. IEEE Access 8, 107601–107613 (2020). https://doi.org/10.1109/ACCESS.2020.3000764
Giacomelli, I., et al.: Privacy-preserving ridge regression with only linearly-homomorphic encryption. In: International Conference on Applied Cryptography and Network Security. Springer, Cham (2018)
Dong, X., et al.: Privacy-preserving locally weighted linear regression over encrypted millions of data. IEEE Access 8, 2247–2257 (2019)
Gascón, A., et al.: Privacy-preserving distributed linear regression on high-dimensional data. Proc. Priv. Enhanc. Technol. 2017(4), 345–364 (2017)
Katz, J., Lindell, Y.: Introduction to modern cryptography. In: CRC Cryptography and Network Security Series. CRC Press, Boca Raton (2014)
Nakamoto, S.: Bitcoin: a peer-to-peer electronic cash system (2008). https://bitcoin.org/bitcoin.pdf. Accessed 19 Dec 2020
Montgomery, D.C., Peck, E.A., Vining, G.G.: Introduction to Linear Regression Analysis, vol. 821. Wiley, Hoboken (2012)
Shokri, R., Shmatikov, V.: Privacy-preserving deep learning. In: Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, CCS 2015, pp. 1310–1321. ACM, New York (2015). https://doi.org/10.1145/2810103.2813687
Goldreich, O.: Foundations of Cryptography: Volume 2, Basic Applications. Cambridge University Press, Cambridge (2009)
Canetti, R.: Security and composition of multiparty cryptographic protocols. J. Cryptol. 13(1), 143–202 (2000). https://doi.org/10.1007/s001459910006
Dheeru, D., Karra, T.E.: UCI Machine Learning Repository. University of California, Irvine, CA, School of Information and Computer Science (2017)
Detrano, R., Janosi, A., Steinbrunn, W., Pfisterer, M., Schmid, J., Sandhu, S., Guppy, K.H., Lee, S., Froelicher, V.: International application of a new probability algorithm for the diagnosis of coronary artery disease. Am. J. Cardiol. 64, 304–310 (1989)
Acknowledgements
Authors thanks the school of computer science and technology of the University of Chinese Academy of Science, Beijing, China, and the Department of Computer Science and Engineering of University of Asia Pacific, Dhaka, Bangladesh for their support towards this study.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this chapter
Cite this chapter
Haque, R.U., Hasan, A.S.M.T. (2021). Privacy-Preserving Multivariant Regression Analysis over Blockchain-Based Encrypted IoMT Data. In: Maleh, Y., Baddi, Y., Alazab, M., Tawalbeh, L., Romdhani, I. (eds) Artificial Intelligence and Blockchain for Future Cybersecurity Applications. Studies in Big Data, vol 90. Springer, Cham. https://doi.org/10.1007/978-3-030-74575-2_3
Download citation
DOI: https://doi.org/10.1007/978-3-030-74575-2_3
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-74574-5
Online ISBN: 978-3-030-74575-2
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)