Abstract
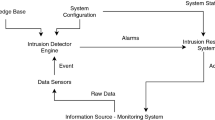
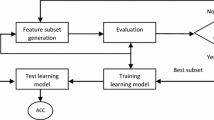
A Network Intrusion Detection System (NIDS) is a mechanism that detects illegal and malicious activity inside a network. Anomaly based Intrusion detection systems use machine learning techniques to detect novel attacks. Classifiers are predictors that estimate the class label of an attack based on prior training and learning models. While it can be seen that DoS (Denial of Service) and probe attacks are filtered with reasonable accuracy, the detection rate fails miserably for R2L (Remote-to-Local) and U2R (User-to-Root) attacks. This paper aims to improve the accuracy of the above-mentioned attacks by proposing a two-stage classifier with feature selection used in the second stage of classification. The first stage uses a simple NB classifier with all the trained features. The proposed feature selection technique is based on Genetic Algorithm with entropy-based weights used for giving importance to each feature in the fitness function. Experiments were conducted on the NSL-KDD dataset using the WEKA machine learning tool. It can be seen that the detection rate of R2L and U2R improves significantly with 86.2% and 95% enhancement in the second stage of classification. This paper also compares the proposed feature selection technique with the existing filter methods and inspects the accuracies of other classifiers.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Liao, H., Lin, R.C., et al.: Intrusion detection system: a comprehensive review. J. Netw. Comput. Appl. 36, 16–24 (2013)
Cano, J.: Cyberattacks-the instability of security and control knowledge. ISACA J. 5, 1–5 (2016)
Hollingsworth, C.: Auditing from FISMA and HIPAA: lessons learned performing an in-house cybersecurity audit. ISACA J. 5, 1–6 (2016)
Singh, K., Agrawal, S., Sohi, B.S.: A near real-time IP traffic classification using machine learning. Int. J. Intell. Syst. Appl. 5(3), 83–93 (2013)
Limthong, K., Tawsook, T.: Network traffic anomaly detection using machine learning approaches. In: IEEE Network Operations and Management Symposium, Maui, HI, pp. 542–545 (2012)
Anon: Decision Trees – C4.5. https://octaviansima.wordpress.com/2011/03/25/decision-trees-c4-5/
Li, W., Moore, A.W.: A machine learning approach for efficient traffic classification. In: 15th International Symposium on Modeling, Analysis, and Simulation of Computer and Telecommunication Systems, Istanbul, pp. 310–317 (2007)
Casas, P., Fiadino, P., D’Alconzo, A.: Machine-learning based approaches for anomaly detection and classification in cellular networks. In: Network Traffic Measurement and Analysis Conference, TMA (2016)
Benaicha, S.E., Saoudi, L., et al.: Intrusion detection system using genetic algorithm. In: Science and Information Conference, pp. 564–568, London, UK (2014)
Pal, D., Parashar, A.: Improved genetic algorithm for ıntrusion detection system. In: Internationl Conference on Computational Intelligence and Communication Networks (CICN), USA, pp. 835–839 (2014)
Guo, Y., Wang, B., et al.: Feature selection based on rough set and modified genetic algorithm for ıntrusion detection. In: 5th International Conference on Computer Science & Education, China, pp. 1441–1446 (2010)
Hu, Y.J., Ling, Z.H.: DBN-based spectral feature representation for statistical parametric speech synthesis. IEEE Signal Process. Lett. 23(3), 21–325 (2016)
NSL-KDD Dataset. http://nsl.cs.unb.ca/NSL-KDD/
Ibrahim, L.M., Basheer, D.T., Mahmood, M.S.: A comparison study for intrusion database (KDD99, NSL-KDD) based on Self-Organization Map (SOM) Artificial Neural Network. J. Eng. Sci. Technol. 8, 1107–1119 (2013)
WEKA machine learning tool. http://www.cs.waikato.ac.nz/ml/weka/
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2020 Springer Nature Switzerland AG
About this paper
Cite this paper
Devakunchari, Sourabh, Malik, P. (2020). Network Intrusion Detection System Using Two Stage Classifier. In: Smys, S., Bestak, R., Rocha, Á. (eds) Inventive Computation Technologies. ICICIT 2019. Lecture Notes in Networks and Systems, vol 98. Springer, Cham. https://doi.org/10.1007/978-3-030-33846-6_81
Download citation
DOI: https://doi.org/10.1007/978-3-030-33846-6_81
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-33845-9
Online ISBN: 978-3-030-33846-6
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)