Abstract
With the development of Internet technology, a single authentication method for username and passwords can’t satisfy the basic requirements of system security. A multi-server authentication scheme is a useful authentication mechanism in which a remote user can access the services of multiple servers after registering with the registration center (RC). Biometric information is difficult to simulate, therefore biometrics is used for multi-factor authentication. Recently Reedy et al.’s proposed a three-factor authentication scheme. They claimed their schemes can resist all types of attacks. But unfortunately, after analyzing the scheme, we demonstrate their scheme cannot defend against impersonation attack and offline guessing attack. At last, we propose improved fix to overcome its deficiency.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
- Multi-factor authentication
- Password authentication scheme
- Impersonation attack
- Offline guessing attack
1 Introduction
After the emergence of Internet technology, the network-based information industry has developed rapidly and developed into multi-server ubiquitous network that starting as single point-to-point wired network. The network-based severs in our daily life, production and even military field show a broad application prospect [2]. Data has been the main part of people’s production and life. Now, the mobile terminal is pushing the application of network to another climax. However, more and more incidents of information leakage and virus spreading have also reached another climax [3]. It is for the reason that data security becomes indispensable. It’s why we need cryptography and effective encryption architecture to protect our data security.
When attacking a target, an attacker often interprets the user’s password as the beginning of the attack. As long as an attacker can guess or determine the user’s password, he can gain access to the machine or network and access any resources that the user can access. This is extremely dangerous if the user has domain administrator or root user privileges [12].
Password attack is the hacker’s favorite method of intruding into the network. Hackers obtain the passwords of system administrators or other special users, obtain the management rights of the system, steal system information, files on disk and even destroy the system.
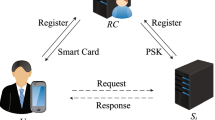
Authentication is a process of providing access authorization verification for the person who want to access or a process of giving user the identification [13]. That is applied to mutual authentication between server and user to assure each other exclusively. Apart from traditional username - password authentication method, by means of biometric authentication to establish a key also began to blossom. This process of participating in certification through biometrics is called as mutually authenticated key agreement [1].
Multi-server authentication schemes ca be divided into two main parts: password-based multi-server authentication and smartcard-based multi-server authentication schemes [19]. We can store a large secret parameters for in smartcard-based authentication [20, 21]. Smartcard-based multi-server authentication schemes prevent an adversary from successfully implementing the password-guessing attack. However, it is very inconvenient for users to carry smart cards and smart cards must participate in every process in login authentication [8]. On the contrary, password-based multi-server authentication schemes are easy to use and convenient for practical applications because they do not require a smartcard and card reader [22, 23]. However, the emergence of biometric authentication has made up for the shortcomings of the above two authentication methods and so the biometric authentication began to flourish.
Since Lamport [15] first proposed a password-based authentication in 1981, a series of single-server password-based authentication schemes are proposed. But these schemes are greatly increased burden on users because of one-on-one authentication method [15]. In 2001, Tsaur [16] proposed the smartcard-based password authentication which initiated remote user identity authentication for multi-server environment. Yoon et al. [5] demonstrated an anonymous authenticated key agreement scheme for multi-server environment by using elliptic curve cryptography [5]. Soon afterwards, he and Kim [17] pointed out that Yoon et al.’s scheme cannot resist masquerade attack, inside attack, stolen smartcards attack and offline password guessing attack and then he proposed the improved scheme. Afterwards, Chuang and Chen [18] proposed scheme that recommended using hash to meet practical application. But Mishra et al. [4] proved several weaknesses.
In 2015, Jiang et al. [23] and Odelu et al. [24] proposed biometric key agreement protocol for multi-Server applications. But in the three schemes, RC participates in the authentication stage, the registry load is too high, which is easy to cause a node failure, which not applicable to the actual situation [27, 28]. In addition, they put forward in the password update phase which has security problems and is vulnerable to masquerade attack, inside attack. There are clock synchronization problems in the protocol. As a result, they have put forward improvement plans. In 2016, Wan et al. [25] pointed out Chuang et al. ‘s [18] schemes can’t resist the masquerade attack and proposed a improvement plans. At the same time, Amin et al. [26] also pointed out that the previous schemes have various shortcomings and gave an improved authentication protocol for remote users in multi-server environment [29].
Recently, to resistant to impersonation attack, Reedy et al. [1] proposed a design of mutually authenticated key agreement scheme resistant for multi-server environment. They claimed their scheme withstand all types of known attacks. Unfortunately, we find that their scheme cannot resist offline password guessing attack, user impersonation attack and lacks user anonymity protection. We present an improved fix to overcome these deficiencies at last.
We are organized this paper as follows: (i) Firstly, our preparations introduce the attack model and elliptic curve knowledge. (ii) Next, we review Reedy et al.’s scheme and point out the drawbacks of the scheme Reedy et al.’s. That is, cryptographic analysis. (iii) We present an improved fix to overcome these deficiencies at last.
2 Preliminaries
2.1 Discrete Logarithm Problem of Elliptic Curve
The security of the entire scheme is guaranteed based on the discrete logarithm of the elliptic curve. The discrete logarithm problem is also the basis of the Reedy’s scheme. We need briefly talk about the elliptic curve involved in the scheme.
Addition definition of elliptic curve: If we delimit an elliptic curve: \( E_{\text{p}} :y^{2} = x^{3} + ax + b \) and \( 4a^{3} + 27b \ne 0 \). Assuming P and Q are the point on the elliptic curve. We define \( P + Q = R \) where R satisfies the point R is the negative point of the only intersection where the line passing through the two points P and Q intersects the elliptic curve. Additionally, \( P = Q \), the tangent to the point P is crossed to the negative point where the elliptic curve is \( R \), \( R = 2P \). However \( 3P = P + P + P = 2P + P \), we can compute the by this way. Consequently, when a point P is known, the “the number N operate the point \( NP({\text{N}} \in {\text{Z}}) \)” is not difficult, because of the nature of the addition, the operation can be faster [10]. But in turn, “the problem of knowing the point \( NP({\text{N}} \in {\text{Z}}) \) for \( N \)” is very difficult, because only each \( N \) can be traversed. This is the “discrete logarithm problem on elliptic curves” used in elliptic curve cryptography [30].
-
Which is the following parameters are known:
-
an elliptic curve: \( E_{\text{p}} :y^{2} = x^{3} + ax + b \)
-
a point P on the elliptic curve (base point)
-
\( NP({\text{N}} \in {\text{Z}}) \) on the elliptic curve \( E_{\text{p}} :y^{2} = x^{3} + ax + b \)
-
We need solve:
-
N
Because of the difficulty, the security of the elliptic curve cipher is guaranteed.
2.2 Security Model
In recent years, the adversaries model of the remote password authentication scheme has always used the classic Dolev-Yao’s model [6], that is the adversaries can arbitrarily monitor, capture, insert and delete the information on the public channel [7]. In recent years, with the development of Internet technology, the ability of adversaries are increased. Adversaries can analyze the message on the smartcards and enhance ability to attack. This paper introduce Wang et al. [7] and Huang’s [9] adversaries model.
In this mode, there are enumerated six kinds adversaries model and increments them according to their capabilities [11]. But for Three-factor Mutually Authenticated Key Agreement schemes, an adversary
 have capabilities which could obtain two of the authentication factors but have no affects to another. The details are shown as following.
have capabilities which could obtain two of the authentication factors but have no affects to another. The details are shown as following.
-
(1)
 captures the smartcards and the password, but A can’t threaten the biological factors of user.
captures the smartcards and the password, but A can’t threaten the biological factors of user. -
(2)
 have abilities to obtain password and biological factors, but have inability to get smart card parameters.
have abilities to obtain password and biological factors, but have inability to get smart card parameters. -
(3)
 get the smartcards and the biological factors, but the password is security.
get the smartcards and the biological factors, but the password is security.
In Huang et al.’s [9] schemes, the probability of success is rare in case 1 or 2. Because the biological factors are fuzzy and extremely difficult to recover. Security parameters of high information entropy are often stored in smart cards [14]. In summary, Scenario three poses a great threat because of the development of the low information entropy and dictionary attack technique.
3 Review of Reedy et al.’s Scheme
In this subsection, we will briefly review Reedy et al.’s scheme. Their scheme include six compositions: Registration Server Initialization phase, Application Server Registration phase, User Registration phase, Login phase, Mutually Authenticated Key Agreement phase, Password And Biometrics Change phase, Dynamic Addition Of Application Server phase, User Revocation/Re-Registration phase. In order to save time and space, we simply recall the central few parts.
Registration Server Initialization phase, we will not elaborate on this. This phase are ready for initialization which the registration server RS generates following parameters. RC (RC is registration server) generates an elliptic curve \( E_{p} :y^{2} = x^{3} + ax + b(\text{mod}\,{\text{p}}) \), where P is a larger prime number, private key USK, ASK and finally publishes the parameters \( \{ E_{p} ,\,{\text{p}},\,h( \cdot )\} \).
3.1 Application Server Registration Phase
-
(1)
\( S_{j} \) sends \( SID_{j} \) to RC securely.
-
(2)
RC computers \( K_{j} = h({\text{SID}}_{\text{j}} \parallel {\text{ASK}}) \) and stores them in its database.
-
(3)
RC responds to \( S_{j} \) the parameters and stores \( \{ K_{j} ,\,h({\text{ASK}}),\,{\text{P}}\} \).
3.2 User Registration Phase
A user must register with RC to become a legitimate user. \( {\text{U}}_{\text{i}} \) need do the according following steps to register with RC via a private channels.
-
(1)
\( U_{i} \) chooses \( ID_{i} \) and \( PW_{i} \) Meanwhile, users need generate a random number \( r_{i} \in Z_{p}^{*} \) and compute \( PID_{i} = h({\text{ID}}_{\text{i}} \parallel {\text{r}}_{\text{i}} ),{\text{PWD}}_{\text{i}} = h({\text{PW}}_{\text{i}} \parallel {\text{r}}_{\text{i}} ) \) and send a request messages \( \{ PID_{i} ,\,{\text{PWD}}_{\text{i}} \} \)
-
(2)
RC verifies the whether a registered user and computes \( {\text{Q}}_{\text{j}} = h({\text{PID}}_{\text{i}} \parallel {\text{K}}_{\text{j}} ) ,\,{\text{R}}_{\text{j}} = {\text{Q}}_{\text{j}} \oplus {\text{PWD}}_{\text{i}} \).
Finally, RC reserves \( \{ {\text{SID}}_{\text{i}} ,\,{\text{R}}_{\text{j}} \} \) in \( {\text{T}}_{\text{i}} \) table and \( \{ PID_{i} ,\,{\text{C}}_{\text{i}} ,\,{\text{T}}_{\text{R}} \, = \, 1\} \) in \( T_{c} \) table where \( {\text{T}}_{\text{R}} = 1 \) means \( U_{i} \) registered initially and is in active state. RC computes \( W_{j} = h({\text{PID}}_{\text{i}} \parallel {\text{USK}}) \) and personalizes \( \{ W_{j} ,\,{\text{ T}}_{\text{i}} ,\,{\text{h}}({\text{ASK}})\} \) into the smartcards to be delivered to \( U_{i} \).
-
(3)
\( U_{i} \) scans his/her \( BIO_{i} \) at the provided sensor with card reading machine, and computes \( X_{j} = W_{j} \oplus PWD_{i} \), \( C_{i} = h({\text{ID}}_{\text{i}} \parallel {\text{W}}_{\text{j}} ) \), \( (\sigma_{i} ,\theta_{i} ) = {\text{Gen}}({\text{BIO}}_{\text{i}} ) \), \( {\text{V}}_{\text{i}} = {\text{r}}_{\text{i}} \oplus {\text{h}}(\upsigma_{\text{i}} )\,U_{i} \) replaces \( W_{j} \) with \( X_{j} \) and stores \( \{ C_{i} ,\,{\text{V}}_{\text{i}} ,\,\theta_{\text{i}} \} \) on smartcards. Therefore, the smartcards finally contains \( \{ X_{j} ,\,{\text{V}}_{\text{i}} ,\,C_{i} ,\,{\text{ T}}_{\text{i}} ,\,\theta_{\text{i}} ,\,P,\,h( \cdot ),\,h({\text{ASK}})\} \).
3.3 Login Phase
User can transmit the login request by inserting smartcards and enter \( ID_{i} \), \( PW_{i} \) and \( {\text{BIO}}_{i}^{'} \) to get login privileges.
Smartcards compute \( \sigma_{i}^{'} = {\text{Re}}\,p({\text{BIO}}_{i}^{'} ,\theta_{i} ),{\text{r}}_{\text{i}} = {\text{V}}_{\text{i}} \oplus {\text{h}}(\sigma_{i}^{'} ),{\text{PID}}_{\text{i}} = {\text{h}}({\text{ID}}_{\text{i}} \parallel {\text{r}}_{\text{i}} ) \), \( {\text{PWD}}_{\text{i}} = h({\text{PW}}_{\text{i}} \parallel {\text{r}}_{\text{i}} ) \), \( W_{j} = X_{j} \oplus PWD_{i} \). Finally, smartcards need verify whether the parameter \( C_{i} \mathop = \limits^{?} h({\text{ID}}_{\text{i}} \parallel {\text{W}}_{\text{j}} ) \) are correct. If the value doesn’t correspond, the login request is terminated.
User choose the server \( S_{j} \) by assessing the list \( {\text{T}}_{\text{i}} \) and extract \( {\text{R}}_{\text{j}} \) at the same time. User compute \( {\text{Q}}_{\text{j}} = {\text{R}}_{\text{j}} \oplus {\text{PWD}}_{\text{i}} \). Smartcards generate random number \( {\text{N}}_{ 1} \in {\text{Z}}_{\text{p}}^{*} \) and compute \( B_{ij} = PID_{i} \oplus h({\text{SID}}_{\text{i}} \parallel \alpha \parallel {\text{h}}({\text{ASK}})) \), \( {\text{D}}_{\text{ij}} = {\text{h}}({\text{PID}}_{\text{i}} \parallel Q_{i} \parallel \alpha ) \), \( \alpha = N_{1} P \). Smartcard send out the login request include \( \{ B_{ij} ,\,{\text{D}}_{\text{ij}} ,\,\alpha \} \) by public channel.
3.4 Mutually Authenticated Key Agreement Phase
This phase mainly introduce the process which \( U_{i} \) and \( S_{j} \) authenticate each other and establish a secure long-term channel for further communication over public channel.
-
(1)
\( S_{j} \) computes \( PID_{i} = B_{ij} \oplus h({\text{SID}}_{\text{i}} \parallel \alpha \parallel {\text{h}}({\text{ASK}})) \) and \( {\text{Q}}_{\text{j}} = h({\text{PID}}_{\text{i}} \parallel {\text{K}}_{\text{j}} ) \) when receive the login request. Afterwards, \( S_{j} \) authenticates \( U_{i} \) only if \( {\text{D}}_{\text{ij}} \,\mathop = \limits^{?} \,{\text{h}}({\text{PID}}_{\text{i}} \parallel Q_{i} \parallel \alpha ) \) matching the condition. Otherwise, the process terminates.
-
(2)
\( S_{j} \) generates a random number \( {\text{N}}_{ 2} \in Z_{p}^{*} \) and computes \( \beta = {\text{N}}_{ 2} {\text{P}} \), \( {\text{K}}_{\text{ij}} \, = \,{\text{N}}_{ 2} \,\alpha \), \( {\text{SK}}\, = \,{\text{h}}({\text{Q}}_{\text{j}} \parallel {\text{K}}_{\text{ij}} \parallel {\text{PID}}_{\text{i}} ) \), \( {\text{E}}_{\text{ij}} \,\mathop = \limits^{{}} \,{\text{h}}({\text{SK}}\parallel {\text{SID}}_{\text{j}} \parallel \beta \parallel \alpha \parallel {\text{Q}}_{\text{j}} ) \). And then \( S_{j} \) send \( \{ {\text{E}}_{\text{ij}} ,\,\beta \} \) to smartcards by a public channel.
-
(3)
\( U_{i} \) computes \( {\text{K}}_{\text{ij}} = {\text{N}}_{ 1} \,\beta \), \( {\text{SK}}\, = \,{\text{h}}({\text{Q}}_{\text{j}} \parallel {\text{K}}_{\text{ij}} \parallel {\text{PID}}_{\text{i}} ) \) and verifies \( {\text{E}}_{\text{ij}} \,\mathop { = \,}\limits^{?} {\text{h}}({\text{SK}}\parallel {\text{SID}}_{\text{j}} \parallel \beta \parallel \alpha \parallel {\text{Q}}_{\text{j}} ) \). If the condition holds, \( U_{i} \) authenticates \( S_{j} \) and \( U_{i} \) computer \( {\text{F}}_{\text{ij}} = {\text{h}}({\text{SK}}\parallel {\text{SID}}_{\text{j}} \parallel \beta \parallel \alpha \parallel {\text{Q}}_{\text{j}} ) \) Otherwise, the process terminates. Smartcards launches \( {\text{F}}_{\text{ij}} \) to \( S_{j} \) via a public channel.
-
(4)
\( S_{j} \) verifies condition \( {\text{F}}_{\text{ij}} \,\mathop = \limits^{?} \,{\text{h}}({\text{SK}}\parallel {\text{SID}}_{\text{j}} \parallel \beta \parallel \alpha \parallel {\text{Q}}_{\text{j}} ) \) and reconfirms the authenticity of \( U_{i} \). They complete each other certification and rebuild communication channel.
4 Cryptanalysis of Reedy et al.’s Proposed Scheme
After we analyzed the Reedy et al.’s scheme and established the basic attack model, we begin to analyze the security of the scheme. We show that the scheme is not resistant to offline password guessing attack and impersonation attack. The following is a description of the Reedy et al.’s scheme.
-
(1)
We have established an adversary model in the previous section, that is, two factors are known to determine whether it can threaten the third factor. The proof of the impersonation attack is given in the scheme including user and application. In the proof a, assume
 wants to impersonate a legitimate user, he/she can performs guessing the username and the password. Apart from this,
wants to impersonate a legitimate user, he/she can performs guessing the username and the password. Apart from this,
 need build the message \( \{ {\text{B}}_{\text{ij}} ,{\text{D}}_{\text{ij}} ,\alpha \} \). And then
need build the message \( \{ {\text{B}}_{\text{ij}} ,{\text{D}}_{\text{ij}} ,\alpha \} \). And then
 compute the parameters \( \sigma_{i}^{'} \), \( {\text{r}}_{\text{i}} \) \( {\text{PID}}_{\text{i}} \), \( {\text{PWD}}_{\text{i}} \), \( W_{j} \) and test \( C_{i} \). Reedy deems the adversaries can’t correct credentials. In the proof b, Reedy consider that \( {\text{Q}}_{\text{j}} \) is unique for each \( S_{j} \). Therefore,
compute the parameters \( \sigma_{i}^{'} \), \( {\text{r}}_{\text{i}} \) \( {\text{PID}}_{\text{i}} \), \( {\text{PWD}}_{\text{i}} \), \( W_{j} \) and test \( C_{i} \). Reedy deems the adversaries can’t correct credentials. In the proof b, Reedy consider that \( {\text{Q}}_{\text{j}} \) is unique for each \( S_{j} \). Therefore,
 can’t have the session key. The scheme is considered security.
can’t have the session key. The scheme is considered security.
But in the scheme, store the long-term private key \( {\text{h(ASK)}} \) of the RC in every user’s smartcard. If A can obtain \( {\text{h(ASK)}} \), he/she will initiating an impersonation attack.
Firstly,
 can capture \( \{ {\text{B}}_{\text{ij}} ,{\text{D}}_{\text{ij}} ,\alpha \} \) and \( PID_{i} = B_{ij} \oplus h({\text{SID}}_{\text{i}} \parallel \alpha \parallel {\text{h(ASK}})) \). Then he/she computes \( Q_{j} = R_{j} \oplus PWD_{k} \) which the \( R_{j} \) is extracted from \( T_{k} \) and compute \( \alpha^{*} = N_{1}^{*} P \), \( B_{ij}^{*} = PID_{i} \oplus h({\text{SID}}_{\text{j}} \parallel \alpha^{*} \parallel {\text{h}}({\text{ASK}})) \), \( {\text{D}}_{ij}^{*} = h({\text{PID}}_{\text{i}} \parallel {\text{Q}}_{\text{j}} \parallel \alpha^{*} ) \) to \( S_{j} \), \( \text{D}_{ij}^{*} \) is successful verification.
can capture \( \{ {\text{B}}_{\text{ij}} ,{\text{D}}_{\text{ij}} ,\alpha \} \) and \( PID_{i} = B_{ij} \oplus h({\text{SID}}_{\text{i}} \parallel \alpha \parallel {\text{h(ASK}})) \). Then he/she computes \( Q_{j} = R_{j} \oplus PWD_{k} \) which the \( R_{j} \) is extracted from \( T_{k} \) and compute \( \alpha^{*} = N_{1}^{*} P \), \( B_{ij}^{*} = PID_{i} \oplus h({\text{SID}}_{\text{j}} \parallel \alpha^{*} \parallel {\text{h}}({\text{ASK}})) \), \( {\text{D}}_{ij}^{*} = h({\text{PID}}_{\text{i}} \parallel {\text{Q}}_{\text{j}} \parallel \alpha^{*} ) \) to \( S_{j} \), \( \text{D}_{ij}^{*} \) is successful verification.
-
(2)
Guessing attack means that as long as the adversaries can guess or determine the user’s password, he can gain access to the machine or network and access any resources that the user can access. The key point is the vulnerability of the user’s choice of password. If
 can obtain the message on the smartcards like \( \{ X_{j} ,{\text{V}}_{\text{i}} ,C_{i} ,{\text{ T}}_{\text{i}} ,\theta_{\text{i}} ,P,h( \cdot ),h({\text{ASK}})\} \), then he/she get the biological factors \( {\text{BIO}}_{{{\text{i}}^{{\prime }} }} \) of user.
can obtain the message on the smartcards like \( \{ X_{j} ,{\text{V}}_{\text{i}} ,C_{i} ,{\text{ T}}_{\text{i}} ,\theta_{\text{i}} ,P,h( \cdot ),h({\text{ASK}})\} \), then he/she get the biological factors \( {\text{BIO}}_{{{\text{i}}^{{\prime }} }} \) of user.
 can initiate a password guessing attack:
can initiate a password guessing attack:Firstly,
 can compute \( \sigma_{i'} = {\text{Re}}\,p({\text{BIO}}_{{{\text{i}}^{{\prime }} }} ,\theta_{i} ) \), \( {\text{r}}_{\text{i}} = {\text{V}}_{\text{i}} \oplus {\text{h}}(\sigma_{i'} ) \). And then
can compute \( \sigma_{i'} = {\text{Re}}\,p({\text{BIO}}_{{{\text{i}}^{{\prime }} }} ,\theta_{i} ) \), \( {\text{r}}_{\text{i}} = {\text{V}}_{\text{i}} \oplus {\text{h}}(\sigma_{i'} ) \). And then
 can guessing the \( {\text{ID}},{\text{PW}} \). Follow the steps to continue calculating the formula \( PWD^{*} = h({\text{PW}}\parallel {\text{r}}_{\text{i}} ) \), \( {\text{W}}_{j}^{*} = X_{j} \oplus PWD^{*} \). We can verify the \( {\text{C}}_{i}^{*} = h({\text{ID}}\parallel W_{j}^{*} )\mathop = \limits^{?} C_{i} \).
can guessing the \( {\text{ID}},{\text{PW}} \). Follow the steps to continue calculating the formula \( PWD^{*} = h({\text{PW}}\parallel {\text{r}}_{\text{i}} ) \), \( {\text{W}}_{j}^{*} = X_{j} \oplus PWD^{*} \). We can verify the \( {\text{C}}_{i}^{*} = h({\text{ID}}\parallel W_{j}^{*} )\mathop = \limits^{?} C_{i} \).
Since the actual identity and password space is very limited space (\( \left| {D_{id} } \right| \le \left| {D_{pw} } \right| \le 10^{6} \)), attacks can be completed within a limited time. Through the establishment of the attack model and the analysis of the above scheme, we show that \( C_{i} \) is the key for adversaries. The \( C_{i} \) parameter is the correctness parameter for the login verification in the smartcard. If adversaries gets the password, they can choose a random number and calculate the \( {\text{B}}_{\text{ij}} ,{\text{D}}_{\text{ij}} \) for login the \( S_{j} \). The scheme does not involve the complexity of the time space for offline guessing attack. So the solution is not safe for offline guessing attack.
The user is completely unaware of the circumstances which adversaries get messages from the channel.
 only need derive \( Q_{j} \) with \( {\text{h}}({\text{ASK}}) \). It is not difficult to find that the above attack is caused by the same security parameters from RC and \( S_{j} \) stored in the user’s smartcards. It can be seen that the analysis of this agreement proves to be incomplete.
only need derive \( Q_{j} \) with \( {\text{h}}({\text{ASK}}) \). It is not difficult to find that the above attack is caused by the same security parameters from RC and \( S_{j} \) stored in the user’s smartcards. It can be seen that the analysis of this agreement proves to be incomplete.
The user is completely unaware of the circumstances which adversary gets messages from the channel.
 only need derive \( Q_{j} \) with \( {\text{h}}({\text{ASK}}) \). It is not difficult to find that the above attack is caused by the same security parameters from RC and \( S_{j} \) stored in the user’s smartcards. It can be seen that the analysis of this agreement proved to be incomplete.
only need derive \( Q_{j} \) with \( {\text{h}}({\text{ASK}}) \). It is not difficult to find that the above attack is caused by the same security parameters from RC and \( S_{j} \) stored in the user’s smartcards. It can be seen that the analysis of this agreement proved to be incomplete.
5 Possible Fix
We put forward a solution that may figure out this problem in the light of the problems above. The critical points that the basis of the analysis above is whether the third factor of the first two factors is known to be reliability. Three factors synthesize into parameter to ensure the security of verification. We mainly modify the registration phase and the login phase. The login phase can be executed as following.
\( U_{i} \) chooses \( ID_{i} \) and \( PW_{i} \). Meanwhile, users need generate random number \( r_{i} \in Z_{p}^{*} \) and compute \( PID_{i} = h({\text{ID}}_{\text{i}} \parallel {\text{r}}_{\text{i}} ),{\text{PWD}}_{\text{i}} = h({\text{PW}}_{\text{i}} \parallel {\text{r}}_{\text{i}} ) \) and send a request messages \( \{ PID_{i} ,\,{\text{PWD}}_{\text{i}} \} \)
RC verifies the whether a registered user and computes \( {\text{Q}}_{\text{j}} = h({\text{PID}}_{\text{i}} \parallel {\text{K}}_{\text{j}} ) ,\,{\text{R}}_{\text{j}} = {\text{Q}}_{\text{j}} \oplus {\text{PWD}}_{\text{i}} \).
Finally, RC compute a random number \( IDR_{\text{i}} \) reserves \( \{ {\text{SID}}_{\text{i}} ,\,{\text{R}}_{\text{j}} ,\,IDR_{\text{i}} \} \) in \( {\text{T}}_{\text{i}} \) table and \( \{ PID_{i} ,\,{\text{C}}_{\text{i}} ,\,{\text{T}}_{\text{R}} { = 1}\} \) in \( T_{c} \) table where \( {\text{T}}_{\text{R}} \, = \, 1 \) means \( U_{i} \) registered initially and is in active state. RC computes \( W_{j} = h({\text{PID}}_{\text{i}} \parallel {\text{USK}}) \) and personalizes \( \{ W_{j} ,{\text{ T}}_{\text{i}} ,{\text{h}}({\text{ASK}}) \oplus IDR_{\text{i}} \} \) into the smartcards to be delivered to \( U_{i} \).
\( U_{i} \) scans his/her \( BIO_{i} \) at the provided sensor with card reading machine, and computes, \( (\sigma_{\text{i}} ,\theta_{\text{i}} ) = {\text{Gen}}({\text{BIO}}_{\text{i}} ) \), \( {\text{V}}_{\text{i}} = {\text{r}}_{\text{i}} \oplus {\text{h}}(\sigma_{\text{i}} ) \), \( C_{i} = {\text{h(PID}}_{\text{i}} \parallel PWD_{i} \parallel \sigma_{i} \parallel \theta_{i} ) \), \( U_{i} \) stores \( \{ C_{i} ,{\text{V}}_{\text{i}} ,\theta_{\text{i}} \} \) on smartcards. Therefore, the smartcards finally contains \( \{ W_{j} ,{\text{V}}_{\text{i}} ,C_{i} ,{\text{ T}}_{\text{i}} ,\theta_{\text{i}} ,P,h( \cdot ),h({\text{ASK}})\} \).
Next, login phase is executing as following.
Smartcards compute \( \sigma_{i}^{'} = {\text{Re}}\,p({\text{BIO}}_{i}^{'} ,\theta_{i} ),{\text{r}}_{\text{i}} = {\text{V}}_{\text{i}} \oplus {\text{h}}(\sigma_{i}^{'} ),{\text{PID}}_{\text{i}} = {\text{h}}({\text{ID}}_{\text{i}} \parallel {\text{r}}_{\text{i}} ) \), \( {\text{PWD}}_{\text{i}} = h({\text{PW}}_{\text{i}} \parallel {\text{r}}_{\text{i}} ) \). In particularity, we need proving the parameters \( C_{i} \mathop { = }\limits^{?} {\text{h(PID}}_{\text{i}} \parallel PWD_{i} \parallel \sigma_{i} \parallel \theta_{i} ) \). Finally, smartcards need verify whether the parameter are correct. If the value doesn’t correspond, the login request is terminated.
User chooses the server \( S_{j} \) by assessing the list \( {\text{T}}_{\text{i}} \) and extract \( {\text{R}}_{\text{j}} \) and \( IDR_{\text{i}} \) at the same time. User compute \( {\text{Q}}_{\text{j}} = {\text{R}}_{\text{j}} \oplus {\text{PWD}}_{\text{i}} \). Smartcards generate random number \( {\text{N}}_{1} \in Z_{p}^{*} \) and compute \( B_{ij} = PID_{i} \parallel IDR_{\text{i}} \oplus h({\text{SID}}_{\text{i}} \parallel \alpha \parallel ({\text{h}}({\text{ASK}}) \oplus IDR_{\text{i}} )) \), \( {\text{D}}_{\text{ij}} = {\text{h}}({\text{PID}}_{\text{i}} \parallel Q_{i} \parallel \alpha ) \), \( \alpha = N_{1} P \). Smartcard send out the login request include \( \{ B_{ij} ,{\text{D}}_{\text{ij}} ,\alpha \} \) by public channel.
In Mutually Authenticated Key Agreement phase, \( S_{j} \) inquiry the number \( IDR_{\text{i}} \), and then compute \( PID_{i} \parallel IDR_{\text{i}} = B_{ij} \oplus h({\text{SID}}_{\text{i}} \parallel \alpha \parallel {\text{h}}({\text{ASK}}) \oplus IDR_{\text{i}} ) \) and compute the parameter \( PID_{\text{i}} \), \( {\text{Q}}_{\text{j}} = h({\text{PID}}_{\text{i}} \parallel {\text{K}}_{\text{j}} ) \) when receive the login request. Afterwards, \( S_{j} \) authenticates \( U_{i} \) only if \( {\text{D}}_{\text{ij}} \mathop = \limits^{?} {\text{h}}({\text{PID}}_{\text{i}} \parallel Q_{i} \parallel \alpha ) \) matching the condition. Otherwise the process terminates.
6 Conclusions
In this paper, we demonstrate that Reedy et al.’s scheme can’t withstand some common attacks. More concretely, we analysis the Reedy’s proof on the basis of the Wang et al. and Huang et al.’s [9] rigorous security model. Unfortunately, we find that Reedy et al.’s scheme can’t be secure against guessing attack and impersonation attack with limited domain offline passwords. Next, we propose the improved scheme to overcome their scheme’s flaws. The proposed improved scheme can overcome the flaws of the Reedy et al.’s schemes and be more practically and secure.
References
Reddy, A.G., Yoon, E.J., Das, A.K., et al.: Design of mutually authenticated key agreement scheme resistant to impersonation attacks for multi-server environment. IEEE Access PP(99), 1 (2017)
Wang, D., Wang, P.: Two birds with one stone: two-factor authentication with security beyond conventional bound. IEEE Trans. Dependable Secur. Comput. 15(4), 708–722 (2018)
He, D., Tian, M., Chen, J.: Insecurity of an efficient certificateless aggregate signature with constant pairing computations. Inf. Sci. 268(2), 458–462 (2014)
Mishra, D., Das, A.K., Mukhopadhyay, S.: A secure user anonymity-preserving biometric-based multi-server authenticated key agreement scheme using smart cards. Expert Syst. Appl. 41(18), 8129–8143 (2014)
Yoon, E.J.: Robust biometrics-based multi-server authentication with key agreement scheme for smart cards on elliptic curve cryptosystem. J. Supercomput. 63(1), 235–255 (2013)
Dolev, D., Yao, A.C.: On the security of public key schemes. IEEE Trans. Inf. Theory 29(2), 198–208 (1981)
Wang, D., Wang, P.: On the anonymity of two-factor authentication schemes for wireless sensor networks. Comput. Netw. 73(C), 41–57 (2014)
Wang, D., He, D., Wang, P., et al.: Anonymous two-factor authentication in distributed systems: certain goals are beyond attainment. IEEE Trans. Dependable Secur. Comput. 12(4), 428–442 (2015)
Huang, X., Xiang, Y., Chonka, A., et al.: A generic framework for three-factor authentication: preserving security and privacy in distributed systems. IEEE Trans. Parallel Distrib. Syst. 22(8), 1390–1397 (2011)
Veyrat-Charvillon, N., Standaert, F.-X.: Generic side-channel distinguishers: improvements and limitations. In: Rogaway, P. (ed.) CRYPTO 2011. LNCS, vol. 6841, pp. 354–372. Springer, Heidelberg (2011). https://doi.org/10.1007/978-3-642-22792-9_20
Wang, D., Zhang, Z., Wang, P., et al.: Targeted online password guessing: an underestimated threat. In: ACM SIGSAC Conference on Computer and Communications Security, pp. 1242–1254. ACM (2016)
Wang, D., Wang, P.: On the implications of Zipf’s law in passwords. In: Askoxylakis, I., Ioannidis, S., Katsikas, S., Meadows, C. (eds.) ESORICS 2016. LNCS, vol. 9878, pp. 111–131. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-45744-4_6
Boyd, C., Mathuria, A.: Schemes for authentication and key establishment. In: Schemes for Authentication and Key Establishment, pp. 3215–3230. Springer (2003)
He, D., Wang, D.: Robust biometrics-based authentication scheme for multiserver environment. IEEE Syst. J. 9(3), 816–823 (2015)
Lamport, L.: Password authentication with insecure communication. Commun. ACM 24(24), 770–772 (1981)
Tsaur, W.-J.: A flexible user authentication scheme for multi-server internet services. In: Lorenz, P. (ed.) ICN 2001. LNCS, vol. 2093, pp. 174–183. Springer, Heidelberg (2001). https://doi.org/10.1007/3-540-47728-4_18
Kim, H., Jeon, W., Lee, K., Lee, Y., Won, D.: Cryptanalysis and improvement of a biometrics-based multi-server authentication with key agreement scheme. In: Murgante, B., Gervasi, O., Misra, S., Nedjah, N., Rocha, Ana Maria A.C., Taniar, D., Apduhan, Bernady O. (eds.) ICCSA 2012. LNCS, vol. 7335, pp. 391–406. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-31137-6_30
Chuang, M.C., Chen, M.C.: An anonymous multi-server authenticated key agreement scheme based on trust computing using smart cards and biometrics. Int. J. Netw. Secur. 18(5), 997–1000 (2014)
Tsai, J.L., Lo, N.W.: A new password-based multi-server authentication scheme robust to password guessing attacks. Wirel. Pers. Commun. 71(3), 1977–1988 (2013)
Chang, C.C., Lee, J.S.: An efficient and secure multi-server password authentication scheme using smart cards. In: International Conference on Cyberworlds (2004)
He, D.: Security flaws in a smart card based authentication scheme for multi-server environment. Wirel. Pers. Commun. 70(1), 323–329 (2013)
Juang, W.S.: Efficient multi-server password authenticated key agreement using smart cards. IEEE Trans. Consum. Electron. 50(1), 251–255 (2004)
Jiang, P., Wen, Q., et al.: An anonymous and efficient remote biometrics user authentication scheme in a multi server environment. Front. Comput. Sci. 9(1), 142–156 (2015)
Odelu, V., Das, A.K., Goswami, A.: A secure biometrics-based multi-server authentication protocol using smart cards. IEEE Trans. Inf. Forensics Secur. 10(9), 1953–1966 (2015)
Wan, T., Liu, Z.X., Ma, J.F.: Authentication and key agreement protocol for multi-server architecture. J. Comput. Res. Dev. 53(11), 2446–2453 (2016)
Khan, M.K., Kim, S.K., Alghathbar, K.: Cryptanalysis and security enhancement of a ‘more efficient & secure dynamic ID-based remote user authentication scheme’. Comput. Commun. 34(3), 305–309 (2011)
Shivraj, V.L., Rajan, M.A., Singh, M., et al.: One time password authentication scheme based on elliptic curves for Internet of Things (IoT) (2015)
Qi, X., Na, D., Wong, D.S., et al.: Cryptanalysis and security enhancement of a robust two-factor authentication and key agreement protocol. Int. J. Commun. Syst. 29(3), 478–487 (2016)
Zhong, J., Liu, Z., Xu, J.: Analysis and improvement of an efficient controlled quantum secure direct communication and authentication protocol. Comput. Mater. Contin. 57(3), 621–633 (2018)
Fong Cheang, C., Wang, Y., Cai, Z., Xu, G.: Multi-VMs intrusion detection for cloud security using Dempster-Shafer theory. Comput. Mater. Contin. 57(2), 297–306 (2018)
Acknowledgments
The work was supported in part by the National Natural Science Foundation of China under Grants 61862052 and the Science and Technology Foundation of Qinghai under Grants 2019-ZJ-7065.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 Springer Nature Switzerland AG
About this paper
Cite this paper
Zhang, S., Li, X., Xie, Y. (2019). An Analysis of a Three-Factor Authentication Scheme and Its Improved Fix. In: Sun, X., Pan, Z., Bertino, E. (eds) Artificial Intelligence and Security. ICAIS 2019. Lecture Notes in Computer Science(), vol 11633. Springer, Cham. https://doi.org/10.1007/978-3-030-24265-7_51
Download citation
DOI: https://doi.org/10.1007/978-3-030-24265-7_51
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-24264-0
Online ISBN: 978-3-030-24265-7
eBook Packages: Computer ScienceComputer Science (R0)




 captures the smartcards and the password, but A can’t threaten the biological factors of user.
captures the smartcards and the password, but A can’t threaten the biological factors of user. have abilities to obtain password and biological factors, but have inability to get smart card parameters.
have abilities to obtain password and biological factors, but have inability to get smart card parameters. get the smartcards and the biological factors, but the password is security.
get the smartcards and the biological factors, but the password is security. wants to impersonate a legitimate user, he/she can performs guessing the username and the password. Apart from this,
wants to impersonate a legitimate user, he/she can performs guessing the username and the password. Apart from this,
 need build the message
need build the message  compute the parameters
compute the parameters  can’t have the session key. The scheme is considered security.
can’t have the session key. The scheme is considered security. can obtain the message on the smartcards like
can obtain the message on the smartcards like  can initiate a password guessing attack:
can initiate a password guessing attack: can compute
can compute  can guessing the
can guessing the