Abstract
Data security has been one of the critical challenges to wireless networks since their inception till date. Researchers around the globe have been gearing up for new technologies of communications, and many sophisticated techniques have been under rigorous research to pave the way for fifth-generation (5G) networks. These include massive multi-antenna systems and the use of millimeter wave (mmW) spectrum to form heterogeneous networks (HetNets) in true sense. However, data security at the physical layer has been a threat for reliable communications as malicious users/devices can intrude the link. This chapter provides a physical layer security perspective of a massive multiple-input multiple-output (MIMO)-enabled HetNet where mmW spectrum is also under utilization. The chapter provides an insight into the secrecy outage and secrecy rates of the users when their security is breached by malicious users around. Toward the end, future works in this area are provided.
Access provided by Autonomous University of Puebla. Download chapter PDF
Similar content being viewed by others
Keywords
1 Introduction
The paradigm of communication is shifting toward fifth-generation (5G) technology as the increased traffic demands cannot be met with existing conventional sub-6 GHz communication. This is because today’s era is saturated with widespread usage of smart devices and ever-increasing wireless data traffic. The 5G communication encompasses certain key enabler technologies at the physical layer that makes 5G networks plausible. This includes the massive multiple-input multiple-output (MIMO) technology and millimeter wave (mmW) communication, at 10 to 300 GHz radio frequency bands with bandwidth above 2 GHz, which are envisioned in conjunction with heterogeneous cellular networks (HetNets) [1, 2]. The HetNets provide enhanced coverage and throughput to the end users by operating in such a fashion that they create a layer of overlay deployment of small cells over the existing sub-6 GHz macro cells, thus, bringing network close to the user. Small cells consist of low-powered base stations (BS) with variable operating frequencies and communication ranges [3].
In HetNets, massive MIMO technology works by deploying a range of large-scale antenna arrays at the transmitting nodes to produce highly directional beam gains and optimal radio spectral efficiency [4]. Whereas mmW communication cells have limited coverage because of operation at smaller wavelength and higher path loss [5] due to sensitivity to blockages and severe propagation losses, however, the small wavelength of mmW communication allows placement of large array of antennas in small area; therefore, beamforming can be implemented to compensate for path losses, additional noise power, and out-of-cell interference [7]. It has been proved through measurements that there are significant differences in path loss of line-of-sight (LoS) and non-line-of-sight (NLoS) mmW propagation paths [2, 6].
Shifting the focus from coverage probability and achievable rate at the end user, in 5G communication, investigation of its secrecy and information integrity aspects has recently become an important discussion in both academia and industry. The subsequent discussion will aim to analyze the aspects of physical layer security (PLS) in massive MIMO-enabled hybrid HetNet with mmW small cells, since the physical layer security (PLS) presents an important, low complexity solution for protection of confidential information in complex networks and the aforementioned network presents a common deployment scenario for future 5G communication networks.
In this chapter, we study the PLS in three-tier hybrid HetNets with massive MIMO in macro tier and mmW frequency and sub-6 GHz small cells. Specifically, we analyze the performance of the proposed network, through analytical modeling and simulation, in terms of secrecy outage probability, secrecy spectral efficiency (SSE), and secrecy energy efficiency (SEE). The developed tractable approach of analysis of the network accounts for key features of mmW communication, massive MIMO technology, beamforming gains, number of transmitting antennas at BSs, and node densities. Secrecy outage probability modeling for each tier of the network is performed to quantify the effects of various system parameters on secrecy outage. Following it, tractable model is developed for achievable ergodic rate at the legitimate users and eavesdropper to model average achievable secrecy rate of the network. The SSE and SEE of massive MIMO-enabled three-tier hybrid HetNet are modeled and studied based on the aforementioned average achievable secrecy rate. Finally, with the help of numerical simulations, analytical models are verified, and relation between secrecy outage probability (SOP), SEE, SSE, key features of mmW communication, massive MIMO technology, beamforming gains, number of transmitting antennas at BSs, and node densities is studied.
2 Background
PLS in 5G communication networks is an emerging field of study in wireless technologies. In this respect, major research studies have been done in recent years. Liang et al. [9] and Wang et al. [10] have shown in their work the effects of fading on secrecy outage probability of the network. Wang et al. [8] and Wang et al. [11] investigated that the secrecy performance can be improved by degrading the eavesdropper channel with the help of techniques such as jamming, artificial noise, beam forming, and Wyner codes. Lv et al. [12] designed the techniques for spectrum allocation and transmit beamforming that can improve secrecy rate in two-tier HetNet. Wu et al. [13] stochastically modeled secrecy outage probability and throughout of a HetNet and studied the model for different system parameters. Wang et al. [14] proposed a mobile association policy, based on access threshold, for K-tier HetNet, and Deng et al. [15] worked on secrecy rate in massive MIMO-enabled HetNets. Wang et al. [16] investigated jamming aspects of secrecy in a network where multiple antenna-aided transmitter transmits to a single-antenna user. Xu et al. [17] studied secrecy in HetNets based on coordinated multipoint scheme, and Wang et al. [18] derived and analyzed energy efficiency and secrecy rate in massive MIMO-based heterogeneous centralized radio access network (C-RAN) and showed that secrecy improves with both centralized and distributed large-scale antenna systems in such networks. All the aforementioned works are focused on PLS in conventional sub-6 GHz networks. Sharma et al. [19] present the novel methodology for secure exchange of 3D way points between unmanned aerial vehicles (UAVs), and Sharma et al. [20] discuss a DMM scheme for secure and energy-efficient handover between the mobile nodes in 5G communication empowered fog networks. Jameel et al. [21] studied the secrecy rate outage probability at the legitimate transmitter and receiver in the presence of eavesdroppers capable of energy harvesting and information decoding.
mmW communication has different propagation properties from sub-6 GHz communication, and investigation of its PLS properties is an emerging study. For instance, Wang et al. [22] studied the secrecy properties of point-to-point mmW link and showed that mmW systems have better secrecy as compared to the conventional systems. Vuppala et al. [23] derived the effects of blockages on secrecy rate of a networks with both sub-6 GHz and mmW frequency cells. Wang et al. [24] analyzed the secrecy outage probability in a mmW communication network with omnidirectional single-antenna-assisted users and eavesdroppers. Gong et al. [25] proposed a beamforming scheme for mmW communication networks to maximize their secrecy rate. This approach has been specifically developed for two-way amplify-and-forward MIMO relaying mmW networks. Umer et al. [26] studied the coverage and rate trends of a network with mmW base stations installed in combination with massive MIMO-enabled hybrid HetNets. Umer et al. [27] used stochastic geometry to model and discuss the secrecy outage probability aspects of aforementioned network model.
The rest of the chapter is organized as follows. We first develop the system model and channel model before proceeding to derive the analytical model for the secrecy outage probability, SEE, and SSE of the network. Subsequently, the numerical results for secrecy outage probability and other parameters are discussed. Finally we draw conclusion at the end of the chapter.
3 The System Layout
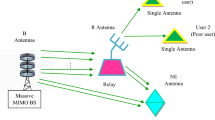
Consider a time-division duplex-based downlink transmission scenario of three-tier hybrid HetNet consisting of macro cells operating at sub-6 GHz at tier 1 and small cells operating at sub-6 GHz and mmW band at tier 2 and tier 3, respectively, as shown in Fig. 1. The BSs of each tier, legitimate users and eavesdroppers, are spatially distributed, following a two-dimensional homogeneous Poisson point process (HPPP) with intensity Φk and density λ k where k ∈{1, 2, 3}, Φu, and its density λ u and Φe with density λ e, respectively. Each BS of kth tier has transmit power P k and path loss exponent α k. Thus, the transmission from BS to the legitimate user takes place in the presence of spatially distributed eavesdroppers. The users and eavesdroppers are equipped with single omnidirectional antenna, and massive MIMO is implemented at macro cells where each macro base station (MBS) is equipped with multiple antennas forming an array, i.e., each MBS has N antennas that simultaneously transmit to U users (N ≫ U ≥ 1) with equal power distribution among all users [28]. Assume that channel state information (CSI) is known at the MBS that uses zero-forcing beamforming (ZFBF) to transmit U data streams [29]. Following Slivnyak’s theorem, we perform the analysis of the network for a typical user located at the origin. A set of parameters used in this paper are outlined in Table 1.
Since mmW frequencies suffer significant path loss, therefore, directional beamforming is implemented at the mmW small cells BSs. We employ a sectored model to define the antenna pattern at the BSs of mmW tier such that constant array gains are assumed for the main lobes as well as the side lobes. Beam direction is uniformly distributed between (0, 2π]. The effective antenna gain, G l, at a typical receiver, r, for an interferer, t, for possible directions l = {1, 2, 3, 4} is given as
where M j, θ j, m j, and p l donate the main lobe gain, beamwidth, side lobe gain, and the probability of occurrence of certain gain G l, where j = {t, r}. It is assumed that the typical transmitting BS, t, and receiver, r, are perfectly aligned; hence maximum directivity gain M r M t can be achieved.
Following the legitimate typical user, antenna gain seen at the eavesdropper e ∈ Φe from serving BS, t, is defined as
where M e is the main lobe gain, m e is the back lobe gain, and θ e is the main lobe beamwidth at the eavesdropper e, respectively.
Analysis is performed for the typical user to whom mmW BS can form line-of-sight (LoS) or non-line-of-sight (NLoS) link. Moreover, we infer that the typical user at the origin will only form the LoS link to the mmW small cell BS when there is no blockage in path of their link. Thus, to define blockage model for mmW communication in this network, in accordance with independent thinning theorem, we divide Φ3 to \(\Phi _{3}^{L}\) and \(\Phi _{3}^{N}=\Phi _{3}/\Phi _{3}^{L}\), with densities p(x)λ 3 and (1 − p(x))λ 3, using LoS probability function p(x), as independent PPPs of LoS and NLoS mmW small cells, respectively [30]. We define p(x) as a probability measure that a link of length x is LoS, i.e., 1 − p(x) is NLoS probability of a link. Based on stochastic blockage models, p(x) is given as p(x) = e −βx where β is dependent on statistics of blockages at a certain cell location and x is the measure of link distance from the serving BS to the typical user [31].
It is assumed that the small-scale fading in sub-6 GHz links is independent and identically distributed (i.i.d) and follows a Rayleigh distribution, whereas for mmW links, it is assume to be independent Nakagami fading with Nakagami fading parameter N L and N N for LoS and NLoS links, respectively. Nakagami fading parameters are considered as positive integers for ease of tractability [37].
An open access scheme for users’ connectivity to BSs is assumed where user connects with any tier BS based on the maximum average received power. Thus, the typical user will connect to tier j if
where \(\overline {P_{k}}=\dfrac { P_k}{(\frac {4\pi }{\lambda _{c}})^{2}}\) and \(L_{k}(x)=x_{k}^{-\alpha _{k}}\) are the normalized transmission power of the kth tier and path loss function. λ c is the carrier wavelength and x is the link distance from typical user to serving BS.
We define the average received power at a typical user connected with the MBS tier as
where G M = (N − U + 1) is the array gain for ZFBF transmission and \(L_{j,M}(x)=x_{3}^{-\alpha _{3}}\) is the path loss function [29]. Likewise, we define average received power at the typical user associated with small cell tier BS as
where G i is given as
For the channel modeling of considered three-tier HetNet, we model the signal-to-interference-plus-noise ratio (SINR) for the entire network. It is assumed that the transmission channels of eavesdroppers and legitimate user are independent of each other, and distortion of eavesdropper channel with interference leads to enhanced secrecy performance of overall network. We define most malicious eavesdropper for any transmission link as one with the highest received SINR; thus it dominates the secrecy rate. The SINRs discussed below are for the most malicious eavesdropper, i.e., \(\mathrm{SINR}_{i}^{e^{*}}=\underset {{e\in \Phi _{e}}} {\mathrm{max}} \{\mathrm{SINR}^{e}_{i} \} \quad \mathrm{where} \quad i\in {\{M,S,m\}}\).
We define received SINR for a typical receiver and any eavesdropper connected with the MBS b o,M as
where \(L_{s}(x_{s})=x_{s}^{-\alpha _{2}}\), \(L_{o,M}(x)=x^{-\alpha _{1}}\), and \(I_{S}={\sum _{s\in \Phi _{2}}\overline {P_{2}} h_{s}L_{s}(x_{s})}\) are the intercell interferences from sub-6 GHz small cells and h s ∼exp(1), h v,M ∼ Γ(U, 1), and h o,M ∼ Γ(N − U + 1, 1) are the small-scale fading gains at the typical user from the interfering channel, interfering MBS, and from serving MBS for U users [29]. Here, h e,M ∼exp(1) is fading gain at eavesdropper at the distance r e from the serving BS, x s and x v are the distances between the receiver and small cell BS and receiver and MBS v, and σ 2 is the noise power.
We define the SINR of a typical receiver with link distance x and an eavesdropper with link distance r e connected with the sub-6 GHz band small cell BS b o,S as
where \(L_{s,S}(x_{s})=x_{s}^{-\alpha _{2}}\), \(L_{o,S}(x)=x^{-\alpha _{2}}\), and \({I_{\overline {\mathrm {M}}}={\sum _{v\in \Phi _{1}}\frac {\overline {P_{1}}}{U} h_{v}L_{v}(x_{v})}}\) are the intercell interferences from macro cells and h s,S ∼exp(1), h o,S ∼exp(1), h e,S ∼exp(1), and h j ∼ Γ(U, 1) are the small-scale fading gains from the interfering channel. Here, x s and x v are the link distance between typical user and small cell BS s and MBS v, respectively.
The SINR for the typical receiver and an eavesdropper connected with mmW small cell b o,m is defined as
where \(L_{o,m}(x)=x^{-\alpha _{3}^{(q)}}\) is path loss, h o,m and h e,m are small-scale fading gains, and G l and G e are the directivity gains of interfering BSs, given by (1) and (2). Here, q ∈{L, N} identifies the interfering link as either LoS (L) or NLoS (N), respectively.
The power consumption model for the assumed three-tier hybrid HetNet needs to be quantified for the evaluation of SSE and SEE, respectively. We define total power consumption at MBS as
where ρ 1 and 𝜖 1 are load-independent circuit power of BD and efficiency of power amplifier, respectively. Parameters Δt and Λt are dependent on the length of transceiver chains and coding, decoding, and precoding involved in the transmission [32].
The power consumption in sub-6 GHz and mmW small cells is defined as
where i ∈{2, 3}, ρ i is load-independent circuit power, and 𝜖 i is the efficiency of power amplifier of the BS of the i-th tier.
To characterize the secure transmission scenario for the proposed network, we first assume that all tier links are eavesdropped such that eavesdroppers do not attempt attacks to change information transmitted from BS to legitimate receiver, i.e., passive non-colluding eavesdropping. A secrecy coding scheme, Wyner code, is adopted at each transmission link for the protection of confidential messages from intrusion from eavesdroppers. Under the Wyner coding scheme, each BS encodes data using this scheme before transmitting it to the legitimate user [33]. Thus, the rate of the transmitted confidential message signal R m and rate of transmitted code words R c are defined at the BS before data transmission commences. The cost of maintaining the confidential message secrecy from eavesdroppers is R c − R m [33]. It is assumed that the aforementioned rates remain fixed during transmission [34, 35]. During transmission from BS to the legitimate user, whenever the wiretapping capacity of the link from the serving BS to the eavesdropper R e is higher than the rate R c − R m, secrecy outage event occurs. Thus, the secrecy outage probability is defined as \(P_{so}^{k}(\gamma _{e})=\mathrm{Pr}(\mathrm{SINR}^{e}_{k}>\gamma _{e})\), i.e., the SINR at any eavesdropper node is higher than threshold. We quantify SSE and SEE based on secrecy outage probability where SSE is the average secrecy rate per unit bandwidth and SEE is the secrecy performance of a three-tier hybrid HetNet based on unit energy consumption.
4 System Performance Evaluation
We specify the average achievable rate associated with successful transmission of confidential information from BS to the legitimate user in proposed hybrid HetNet as secrecy transmission capacity constraint [33, 36]. Thus, the average achievable secrecy rate for the network tiers is represented as
where [y]+ = max{0, y}, \(R_{k}=\mathbb {E}[\text{log}_{2}(1+\mathrm{SINR}^{u}_{k})]\), and \(R^{e}_{k}=\mathbb {E}[\text{log}_{2}(1+\mathrm{SINR}^{e^{*}}_{k})]\) are the average achievable ergodic rates of the channel between the serving kth tier BS and the typical receiver and most malicious eavesdropper . As we are performing the analysis for the most malicious eavesdropper, therefore, the average achievable ergodic rate cannot exceed \(R^{e}_{k}\). The ergodic transmission rate of the serving BS is dependent on the CSI of the link between itself and legitimate user only as CSI of eavesdroppers is unknown at the BS because of their non-colluding nature.
4.1 Achievable Rates
Following up from (14), we derive the achievable ergodic rate at the legitimate user connected with MBS as
where \(P_C^{1}(\gamma )=\int _{0}^{\infty }P_C^{1}(\gamma ,x)f_{X_{1}}(x)dx\) is the complementary cumulative distribution function (CCDF) of \(\text{SINR}_{M}^{u}\), \(f_{X_{1}}(x)\) is the probability density function (PDF) of the distance between the MBS and typical receiver, and \(P_C^{1}(\gamma ,x)\) is the conditional coverage probability for the given distance x between the typical user and serving MBS [27]. In this scenario when the legitimate receiver is connected with MBS, the average ergodic rate on the link between serving BS and the most malicious eavesdropper is given by
where \(P^1_{so}(\gamma _{e})\) is CDF of \(\text{SINR}_{M}^{e^{*}}\). Following up from (14), we derive the achievable ergodic rate at the legitimate user connected with sub-6 GHz small cell as
where \(P_C^2(\gamma )=\int _{0}^{\infty }P_C^{2}(\gamma ,x)f_{X_{2}}(x)dx\) is the CCDF of \(\text{SINR}_{S}^{u}\), \(f_{X_{2}}(x)\) is the PDF of the distance between the serving sub-6 GHz small cell BS and typical user, and \(P_C^{2}(\gamma ,x)\) is the conditional coverage probability of the typical user.
In a scenario when the legitimate receiver is connected with sub-6 GHz small cell BS, the average ergodic rate on the link between serving BS and the most malicious eavesdropper is given by
where \(P^2_{so}(\gamma _{e})\) is the CDF of \(\text{SINR}_{S}^{e^{*}}\).
Following up from (14), we derive the achievable ergodic rate at the legitimate user connected with mmW small cell as
where \(P_C^{3}(\gamma )=\sum \limits _{q\in \{L,N\}}A_{3,q}P_C^{3,q}(\gamma )\) is the CCDF of \(\text{SINR}_{M}^{u}\) and \(P_C^{3,L}(\gamma )\) and \(P_C^{3,N}(\gamma )\) are defined as the conditional coverage probability when the typical receiver, connected with mmW small cell, connects with the BS in \(\Phi _{3}^{L}\) and \(\Phi _{3}^{N}\), respectively. A 3,q are the probabilities of typical receiver associating with LoS or NLoS link.
In a scenario when the legitimate receiver is connected with mmW small cell BS, the average ergodic rate on the link between serving BS and the most malicious eavesdropper is given by
where \(P^2_{so}(\gamma _{e})\) is the CDF of \(\text{SINR}_{M}^{e^{*}}\). By substituting (19) and (20) in (14), we obtain the average achievable secrecy rate for mmW tier.
4.2 Physical Layer Security Parameters
The secrecy outage probability, P so, for the entire network is defined as
where A k is the association probability of tier k. Similarly, a lower bound on the SSE, using the law of total expectation, is given by
where SSE1 = U × R S1 is the value of SSE for massive MIMO-enabled sub-6 GHz macro tier and SSEk = R Sk for k ∈{2, 3} is the value of SSE for sub-6 GHz and mmW small cell tiers, respectively. Average achievable secrecy rate R Sk for each tier k of the network is given by (14).
The lower bound on SEE for the proposed network is defined as [28, 38]:
where \(\text{SEE}_{1}=\frac {U\times R_{S1}}{P_{1}^{\mathrm {total}}}\) is the value of SEE for massive MIMO sub-6 GHz enabled macro tier and \(\text{SEE}_{k}=\frac {R_{Sk}}{P_{k}^{\mathrm {total}}}\) for k ∈{2, 3} is SEE for sub-6 GHz and mmW small cell tiers, respectively. Average achievable secrecy rate R Sk for each tier k of the network is given by (14).
5 Simulation Results and Performance Analysis
In this section, numerical results are shown to study and understand the impact of massive MIMO large antenna arrays and mmW channel characteristics on the secrecy outage probability, SSE, and SEE of the network. The simulation parameters are outlined in Table 2. Monte Carlo simulations are used to study the system performance.
We begin by studying the performance of the proposed network’s secrecy outage probability in terms of density of eavesdropper nodes, as shown in Fig. 2. This plot has been obtained using (21) while taking varying small cell BS densities and directional antenna gains at the eavesdroppers nodes of the network. The secrecy outage probability of the network increases with increasing eavesdropper’s density, thereby notifying that a large number of eavesdropping nodes in the network harm the network secrecy. However, there is another important observation to be noted that higher small cell BS density optimizes the secrecy of the network even though the eavesdropper’s density might be high. These results allude to the fact that higher small cell density results in the increase in interference in the network. Thus, the uncertainty at eavesdropper nodes elevates leading to their SINR falling below the threshold. This results in improvement in secrecy outage probability of the network. The reader may notice that when the small cell density in the network is kept fixed, the secrecy rate of the transmissions in the network improves with small directional antenna gains at the eavesdroppers. We conclude that lower directional gains at the eavesdroppers and higher cell density in the network are the two major settings that reduce the probability of eavesdroppers having SINR above the predefined threshold.
Now, we study the SSE behavior based on varying small cell BS density of tier 2 and tier 3 for various eavesdropper’s densities. Figure 3 plots the SSE of the network versus varying small cell densities. It can be seen that the SSE increases with the increase in small cell density and falls when the eavesdropper node’s density increases. This is because, the average cell radius decreases when small cell density is increased. Therefore, more users are offloaded to small cells so the transmission from the BS to the intended legitimate user becomes better. When the cell sizes decrease, the distance from the intended receiver to the transmitting nodes decreases that causes stronger links and enhanced secrecy rate between them. If we consider the case of mmW small cells, the LoS probability function p(R) is directly related to distance; thus, the LoS association probability increases with decrease in distance. In such scenario, low path loss LoS links between mmW BSs and legitimate users are more likely to be formed than NLoS links. Another interesting observation is that user’s association with MBSs declines in the presented scenario though they are high-power nodes but have low BS density compared to the small cells. Interference in the network increases as transmitting node density is notably high; therefore, an increase in eavesdropper’s density has little impact on SSE of the network.
Figure 4 illustrates the relationship between the SEE and the small cell density. This plot has been obtained using (23). As a preliminary observation, it may be stated that the SEE is higher for greater values of λ 2 and λ 3, respectively . This is because of the increase in SSE over the identical power consumption, shown in Fig. 3. Moreover, on increasing small cell densities, λ 2 and λ 3, more users associate with low-power small cell BSs compared to high-power macro cell BSs. This shift in association leads to a power-efficient network; however, it comes at the cost of small cell BS deployment. Here again it may be noted that the interference in the three-tier network is higher with dense transmitting BS nodes; therefore, an increase in eavesdropper’s density has little impact on SEE of the network.
Extending the previous discussion, we now vary the number of transmitting antennas on the massive MIMO-enabled MBS of the network and then observe the effects on SSE of the three-tier hybrid HetNet over different small cell densities. The results are shown in Fig. 5. It can be seen that the SSE of the network falls with the increasing number of antennas at the MBSs and shows significant increase with higher small cell density. This is because, when N increases, spectral efficiency of MBSs increases. As the MBSs are high power nodes, transmission to eavesdroppers in the network improves significantly that results in increases secrecy rate, R e. Legitimate user to BS association gets biased toward MBSs because of their high array gains at increased number of antennas. Thus, fewer portion of users connect with small cells BSs. Hence, interference in the network reduces leading to better reception at eavesdroppers.
Figure 6 illustrates the variation in SEE with increasing number of antennas at massive MIMO-enabled MBSs. Plot is based on (23). It can be seen that SEE of the network drops with increasing N. It follows from the previous result that SSE drops over the identical power consumption. In addition, users are more likely to connect to macro cell BSs with increase in transmitting nodes at their BSs, and since macro cells are higher-power-consuming entities compared to small cells, therefore, overall network setting shifts to a power-inefficient network. As a result, SEE of the network decreases with the increase in average achievable rate at eavesdroppers. The reader may notice that the interference in the network elevates with small cell density; therefore, SEE improves with drop in eavesdroppers’ secrecy rate R e.
Early on, we mentioned that mmW and massive MIMO technologies are the candidates for being the enabling technologies for 5G networks due to their higher gains and superior bandwidth as for mmW technology. We conclude the Results section by highlighting these very important points that we cannot increase the directional beamforming gains at mmW nodes neither can we increase the number of antennas at massive MIMO-enabled nodes limitlessly to have optimum coverage in the proposed network, without entertaining drop in the overall secrecy performance of the network.
6 Conclusion
In this chapter, we characterized the secure communication in massive MIMO-enabled three-tier hybrid HetNet based on the unique features of massive MIMO and mmW communication by using PLS. Particularly, we evaluated the secrecy outage probability and achievable ergodic rate at each of the three network tiers and most malicious eavesdropper node. The expressions were then used to develop a tractable approach to determine network-wide SSE and SEE. It was observed that network-wide interference elevates on high BS density that in turn dominates the secrecy performance of the network. Moreover, the secrecy performance of the networks drops at higher beamforming gains at mmW cells; therefore, a tradeoff exists between optimal coverage and secrecy in the network. The relationship between the secrecy outage probability, SSE, and SEE of the network and number of antennas at MBS, BS density, antenna gains, and eavesdropper’s density has also been studied through simulation results. Through these results, we conclude that the number of antennas at the massive MIMO-enabled macro cell BSs and beamforming directivity gains at mmW cells shall be carefully chosen for optimal secrecy performance of the network.
References
J.G. Andrews, S. Buzzi, W. Choi, S.V. Hanly, A. Lozano, A.C. Soong, J.C. Zhang, What will 5G be? IEEE J. Sel. Areas Commun. 32(6), 1065–1082 (2014)
J. Zhang, X. Ge, Q. Li, M. Guizani, Y. Zhang, 5G millimeter-wave antenna array: design and challenges. IEEE Wirel. Commun. 24(2), 106–112 (2017)
J. Ye, X. Ge, G. Mao, Y. Zhong, 5G ultra-dense networks with non-uniform distributed users. IEEE Trans. Veh. Technol. 67(3), 2660–2670 (2018)
X. Ge, R. Zi, H. Wang, J. Zhang, M. Jo, Multi-user massive MIMO communication systems based on irregular antenna arrays. IEEE Trans. Wirel. Commun. 15(8), 5287–5301 (2016)
R.W. Heath, T. Bai, R. Vaze, Analysis of blockage effects on urban cellular networks. IEEE Trans. Wirel. Commun. 13(9), 5070–5083 (2014)
E. Turgut, M.C. Gursoy, Energy efficiency in relay-assisted mmW cellular networks, in IEEE 84th Vehicular Technology Conference (VTC-Fall), Sept 2016, pp. 1–5
M. Ding, P. Wang, D. Lopez-Perez, G. Mao, Z. Lin, Performance impact of LoS and NLoS transmissions in dense cellular networks. IEEE Trans. Wirel. Commun. 15(3), 2365–2380 (2016)
H. Wang, T. Zhang, X. Xia, Secure MISO wiretap channels with multi-antenna passive eavesdropper: artificial noise vs. artificial fast fading. IEEE Trans. Wirel. Commun. 14(1), 94–106 (2015)
Y. Liang, H.V. Poor, S. Shamai, Secure communication over fading channels. IEEE Trans. Inf. Theory 54(6), 2470–2492 (2008)
L. Wang, N. Yang, M. Elkashlan, P.L. Yeoh, J. Yuan, Physical layer security of maximal ratio combining in two-wave with diffuse power fading channels. IEEE Trans. Inf. Forensics Secur. 9(2), 247–258 (2014)
H.M. Wang, M. Luo, Q. Yin, X.G. Xia, Hybrid cooperative beamforming and jamming for physical-layer security of two-way relay networks. IEEE Trans. Inf. Forensics Secur. 8(12), 2007–2020 (2013)
T. Lv, H. Gao, S. Yang, Secrecy transmit beamforming for heterogeneous networks. IEEE J. Sel. Areas Commun. 33(6), 1154–1170 (2015)
H. Wu, X. Tao, N. Li, J. Xu, Secrecy outage probability in multi-RAT heterogeneous networks. IEEE Commun. Lett. 20(1), 53–56 (2016)
H. Wang, T. Zheng, J. Yuan, D. Towsley, M.H. Lee, Physical layer security in heterogeneous cellular networks. IEEE Trans. Commun. 64(3), 1204–1219 (2016)
Y. Deng, L. Wang, K.K. Wong, A. Nallanathan, M. Elkashlan, S. Lambotharan, Safeguarding massive MIMO aided hetnets using physical layer security, in Proceedings of Wireless Communications and Signal Processing, 2015, pp. 1–5
J. Wang, J. Lee, F. Wang, T.Q.S. Quek, Jamming-aided secure communication in massive MIMO rician channels. IEEE Trans. Wirel. Commun. 14(12), 6854–6868 (2015)
M. Xu, X. Tao, F. Yang, H. Wu, Enhancing secured coverage with COMP transmission in heterogeneous cellular networks. IEEE Commun. Lett. 20(11), 2272–2275 (2016)
L. Wang, K.K. Wong, M. Elkashlan, A. Nallanathan, S. Lambotharan, Secrecy and energy efficiency in massive MIMO aided heterogeneous C-RAN: a new look at interference. IEEE J. Sel. Top. Sign. Proces. 10(8), 1375–1389 (2016)
V. Sharma, D. N. K. Jayakody, I. You, R. Kumar, J. Li, Secure and efficient context-aware localization of drones in urban scenarios. IEEE Commun. Mag. 56(4), 120–128 (2018)
V. Sharma et al., Secure and energy efficient handover in fog networks using blockchain-based DMM. IEEE Commun. Mag. 56, 22–31 (2018)
F. Jameel et al., Secure communication for separated and integrated receiver architectures in SWIPT. IEEE Wirel. Commun. Netw. Conf. 2018, 1–6 (2018)
L. Wang, M. Elkashlan, T.Q. Duong, R.W. Heath Jr., Secure communication in cellular networks: the benefits of millimeter wave mobile broadband, in IEEE 15th International Workshop on Signal Processing and Advances in Wireless Communication (SPAWC), 2014, pp. 115–119
S. Vuppala, S. Biswas, T. Ratnarajah, An analysis on secure communication in millimeter/micro-wave hybrid networks. IEEE Trans. Commun. 64(8), 3507–3519 (2016)
C. Wang, H.M. Wang, Physical layer security in millimeter wave cellular networks. IEEE Trans. Wirel. Commun. 15(8), 5569–5585 (2016)
S. Gong, C. Xing, Z. Fei, S. Ma, Millimeter-wave secrecy beamforming designs for two-way amplify-and-forward MIMO relaying networks. IEEE Trans. Veh. Technol. Early Access Articles, 66, 1–12 (2016)
A. Umer, S.A. Hassan, H. Pervaiz, Q. Ni, L. Musavian, Coverage and rate analysis for massive MIMO-enabled heterogeneous networks with millimeter wave small cells, in IEEE 85th Vehicular Technology Conference (VTC Spring), 2017, Sydney, pp. 1–5
A. Umer, S.A. Hassan, H. Pervaiz, Q. Ni, L. Musavian, S.H. Ahmed, Secrecy outage analysis for massive MIMO-enabled multi-tier 5G hybrid hetnets, in 2018 IEEE International Conference on Communications Workshops, 2018, Kansas City, pp. 1–6
Y. Hao, Q. Ni, H. Li, S. Hou, On the energy and spectral efficiency tradeoff in massive MIMO enabled hetnets with capacity-constrained Backhaul links. IEEE Trans. Commun. (2017, in press). https://doi.org/10.1109/TCOMM.2017.2730867
K. Hosseini, W. Yu, R.S. Adve, Large-scale mimo versus network mimo for multicell interference mitigation. IEEE J. Sel. Top. Sign. Proces. 8(5), 930–941 (2014)
M. Omar, M. Anjum, S.A. Hassan, H. Pervaiz, Q. Ni, Performance analysis of hybrid 5G cellular networks exploiting mmW capabilities in suburban areas, in IEEE Internation Conference on Communications, Kuala Lumpur, 2016
E. Turgut, M.C. Gursoy, Coverage in heterogeneous downlink millimeter wave cellular networks. IEEE Trans. Commun. 65, 4463–4477 (2017)
C. Yang, J. Li, Q. Ni, A. Anpalagan, M. Guizani, Interference-aware energy efficiency maximization in 5G ultra-dense networks. IEEE Trans. Commun. 65(2), 728–739 (2017)
A.D. Wyner, The wire-tap channel. Bell Labs Tech. J. 54(8), 1355–1387 (1975)
X. Zhang, X. Zhou, M.R. McKay, Enhancing secrecy with multi-antenna transmission in wireless ad hoc networks. IEEE Trans. Inf. Forensics Secur. 8(11), 1802–1814 (2013)
C. Ma, J. Liu, X. Tian, H. Yu, Y. Cui, X. Wang, Interference exploitation in D2D-enabled cellular networks: a secrecy perspective. IEEE Trans. Commun. 63(1), 229–242 (2015)
P.C. Pinto, J. Barros, M.Z. Win, Secure communication in stochastic wireless networks–part I: connectivity. IEEE Trans. Inf. Forensics Secur. 7(1), 125–138 (2012)
T. Bai, R.W. Heath, Coverage and rate analysis for millimeter-wave cellular networks. IEEE Trans. Wirel. Commun. 14(2), 1100–1114 (2015)
H. Pervaiz, L. Musavian, Q. Ni, Z. Ding, Energy and spectrum efficient transmission techniques under QoS constraints toward green heterogeneous networks. IEEE Access 3, 1655–1671 (2015)
G. Auer, V. Giannini, C. Desset, I. Godor, P. Skillermark, M. Olsson et al., How much energy is needed to run a wireless network? IEEE Wirel. Commun. 18(5), 40–49 (2011)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 Springer Nature Switzerland AG
About this chapter
Cite this chapter
Umer, A., Hassan, S.A. (2019). Physical Layer Security in 5G Hybrid Heterogeneous Networks. In: Jayakody, D., Srinivasan, K., Sharma, V. (eds) 5G Enabled Secure Wireless Networks . Springer, Cham. https://doi.org/10.1007/978-3-030-03508-2_4
Download citation
DOI: https://doi.org/10.1007/978-3-030-03508-2_4
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-03507-5
Online ISBN: 978-3-030-03508-2
eBook Packages: EngineeringEngineering (R0)